RFID (Radio Frequency Identification) triple safety certification method based on label ID (Identification) random division
A security authentication and labeling technology, applied to computer components, collaborative devices, instruments, etc., can solve problems such as single authentication mode and potential safety hazards
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
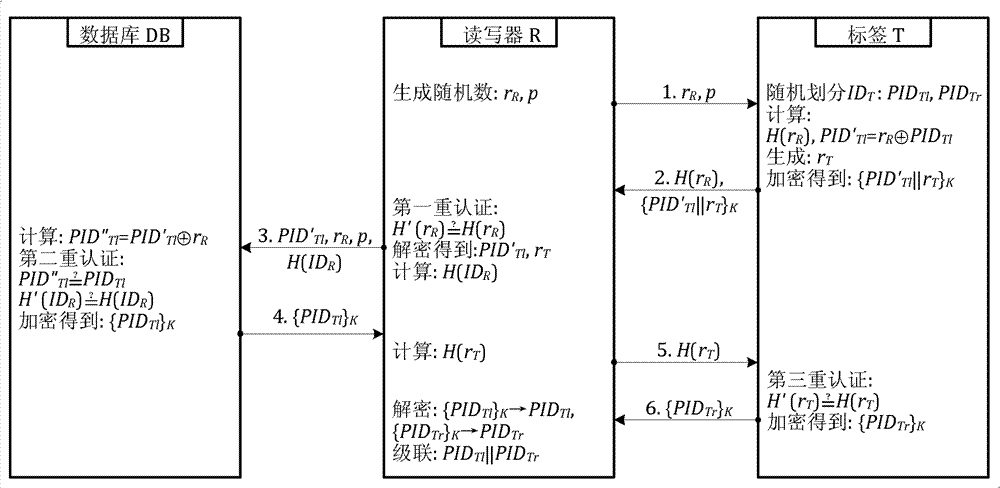
[0037] 1. RFID system initialization
[0038] When the RFID system is initialized, each tag and reader has a unique identifier ID T and ID R ; The database has all tags and identifiers of readers; tags, readers and background databases have a secret shared key K. In the described RFID system, the backward communication link from the reader to the backend database is considered secure.
[0039] 2. Certification process
[0040] The safety authentication protocol steps of the RFID system are as follows:
[0041] Step 1: The reader R first generates two random numbers r R and p, and r R and p are sent to tag T as an inquiry request;
[0042] Step 2: After tag T receives the request, it sends its own identifier ID T Randomly divide into left identifiers and the right identifier two parts; of which, and The division of is determined by p, which changes dynamically in different session periods; the label T is to r R Perform Hash operation to get H(r R ), and perfor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com