Access quarantine method of public file in data divulgence protection system
A technology for public files and protection systems, applied in the field of information security, can solve problems such as affecting user use, increasing the difficulty and cost of system management and maintenance, and data asynchrony, avoiding data asynchrony, reliable and efficient data isolation, and solving application programs. Effects of public documents
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
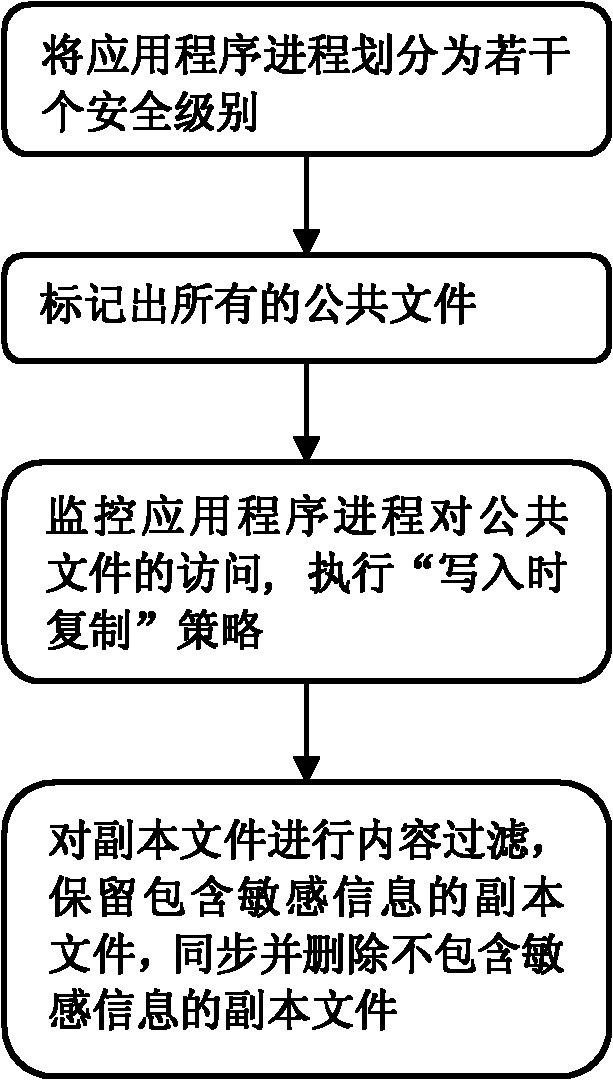
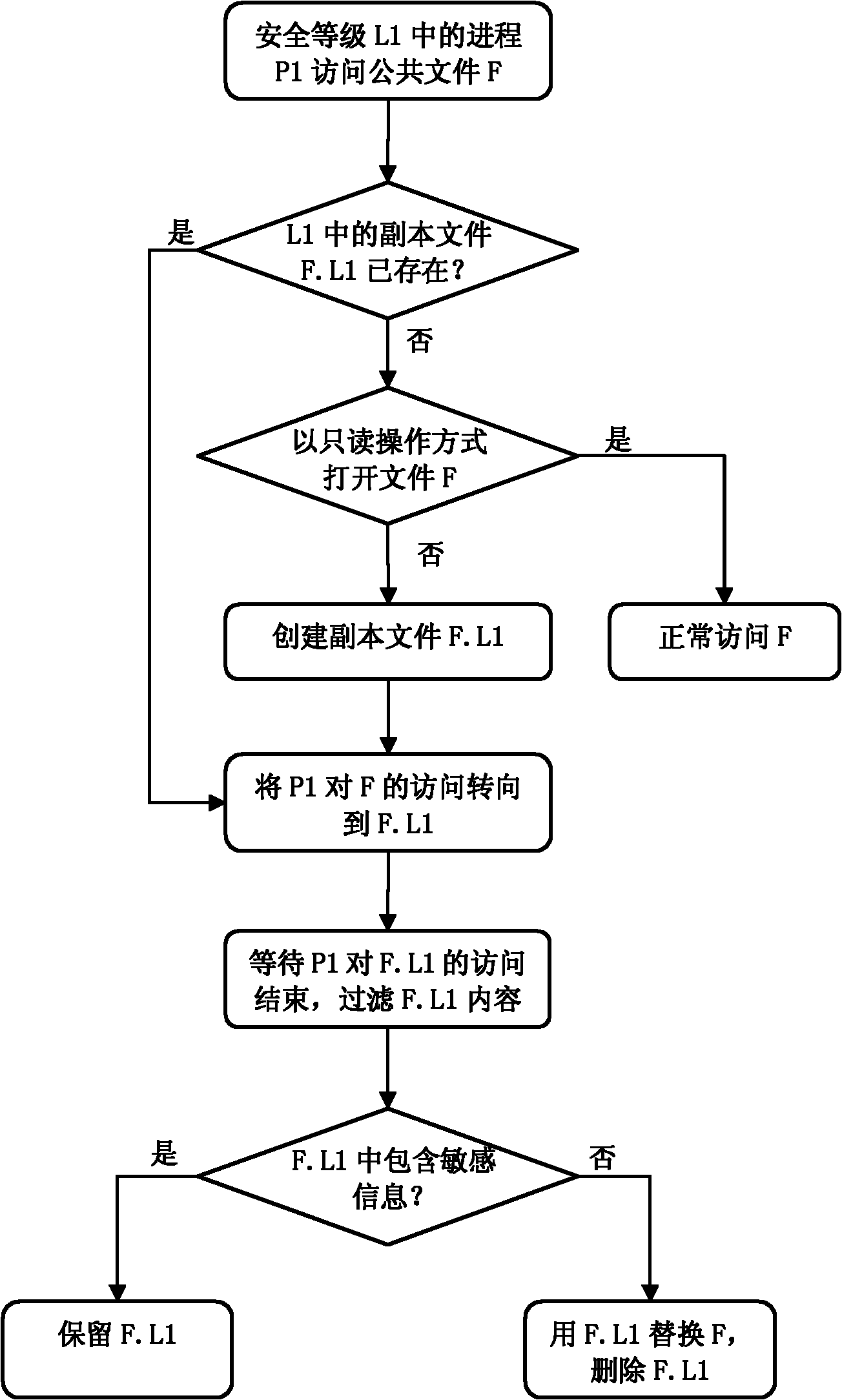
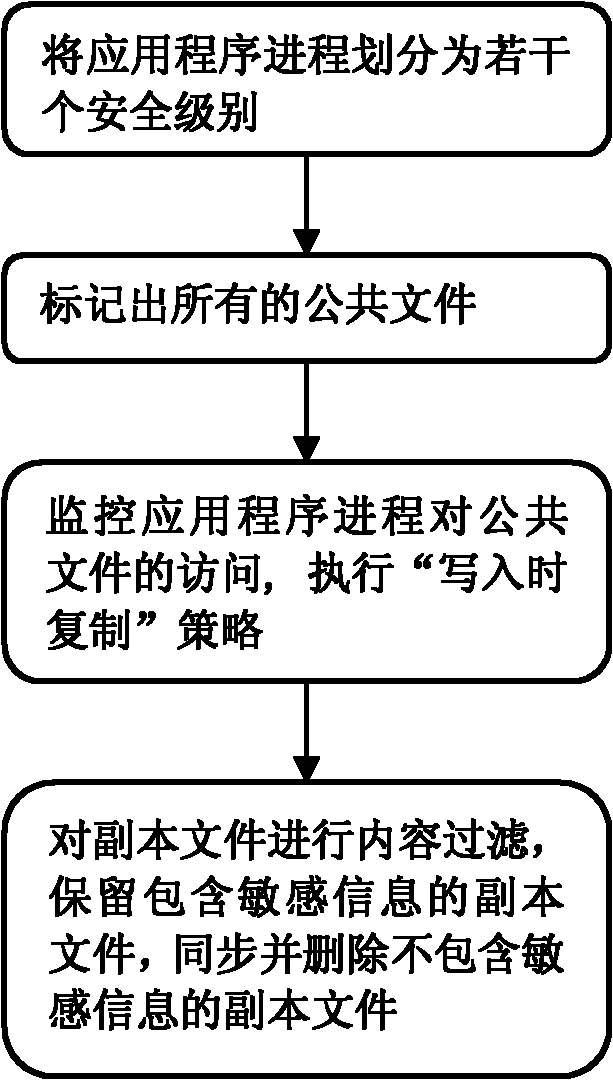
[0031] In this embodiment, the data leakage protection system divides the application process into two levels: security level and common level. The purpose of protection is that sensitive data can only be accessed by security level processes, but not by normal level processes. The following uses the Microsoft Office Word (hereinafter referred to as word) application program as an example to illustrate how to isolate Word's access to the Normal.dotm file under different security levels.
[0032] In the Word application, Normal.dotm is a Word template file, which is read and written when Word is used to edit a doc type file. This file is usually located in the program data directory of the currently logged in user, for example:
[0033] C:\Users\UserName\AppData\Roaming\Microsoft\Templates\Normal.dotm
[0034] In this embodiment, the Word process P1 in the security level L1 accesses the public file F, and the Word process P2 in the normal level L2 accesses the public file F. A...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com