System and method for generating white-box implementations of software applications
A software application, application technology, applied in the field of cryptography, which can solve the problem of subtle errors being easily missed, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
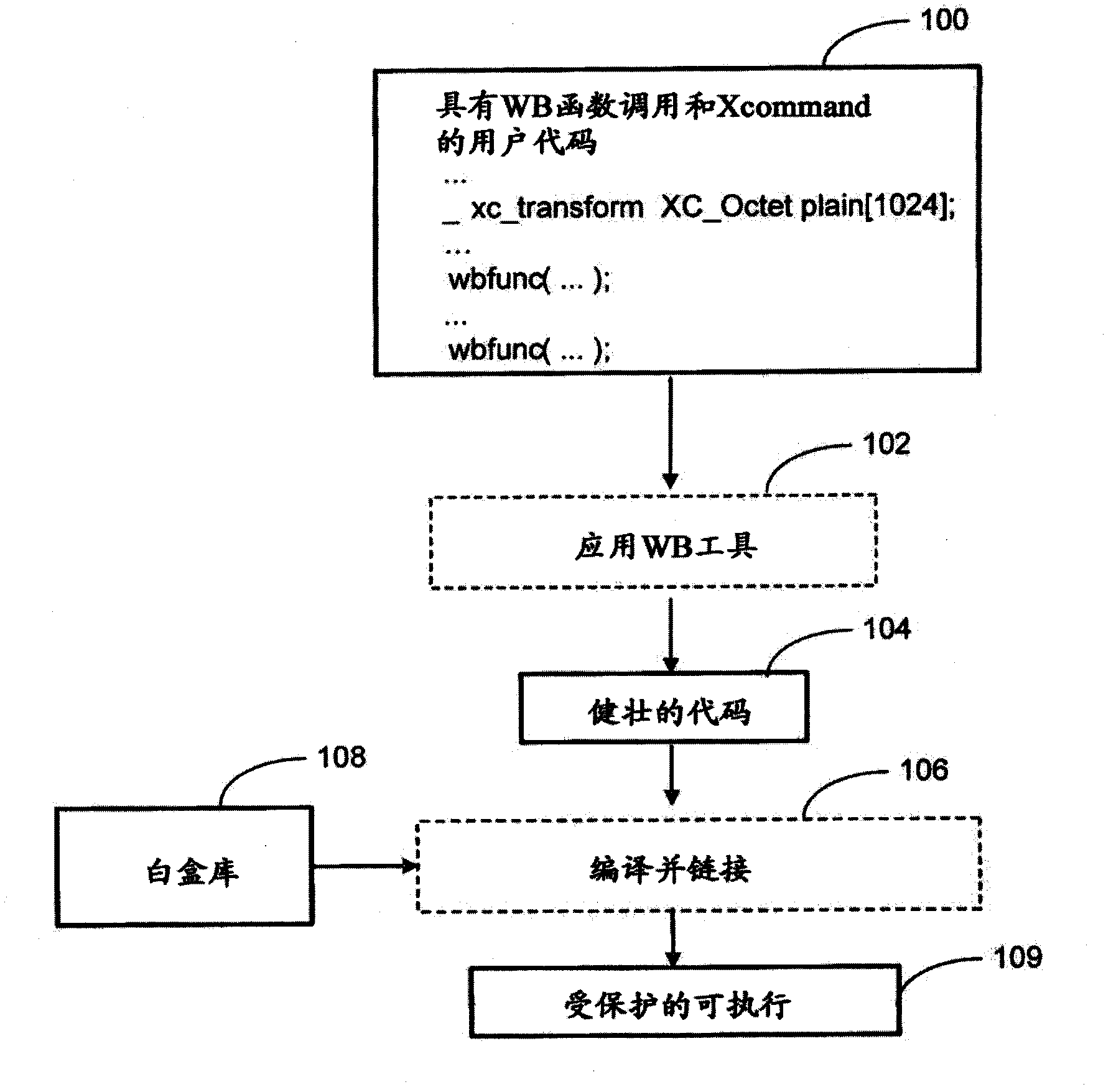
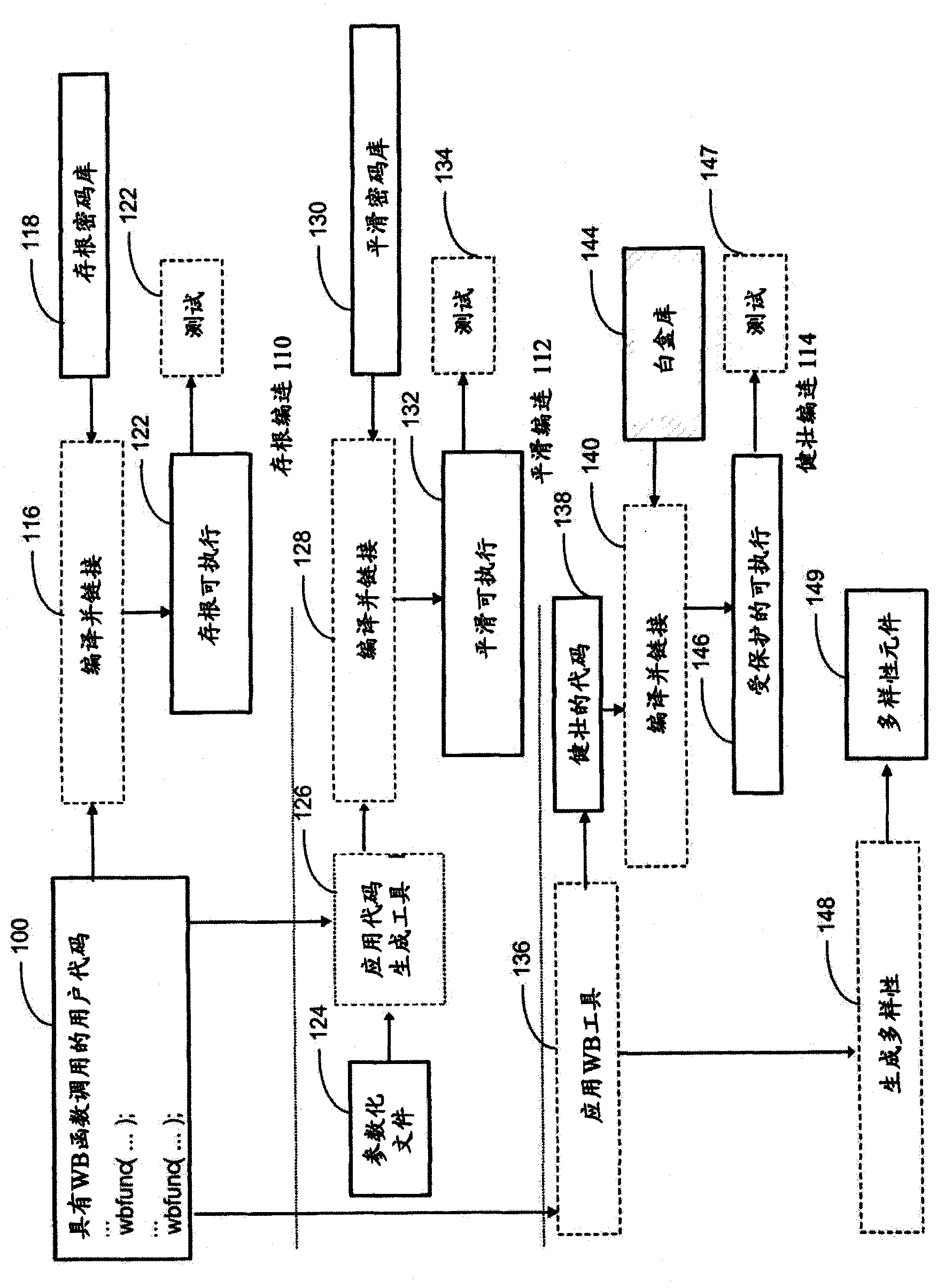
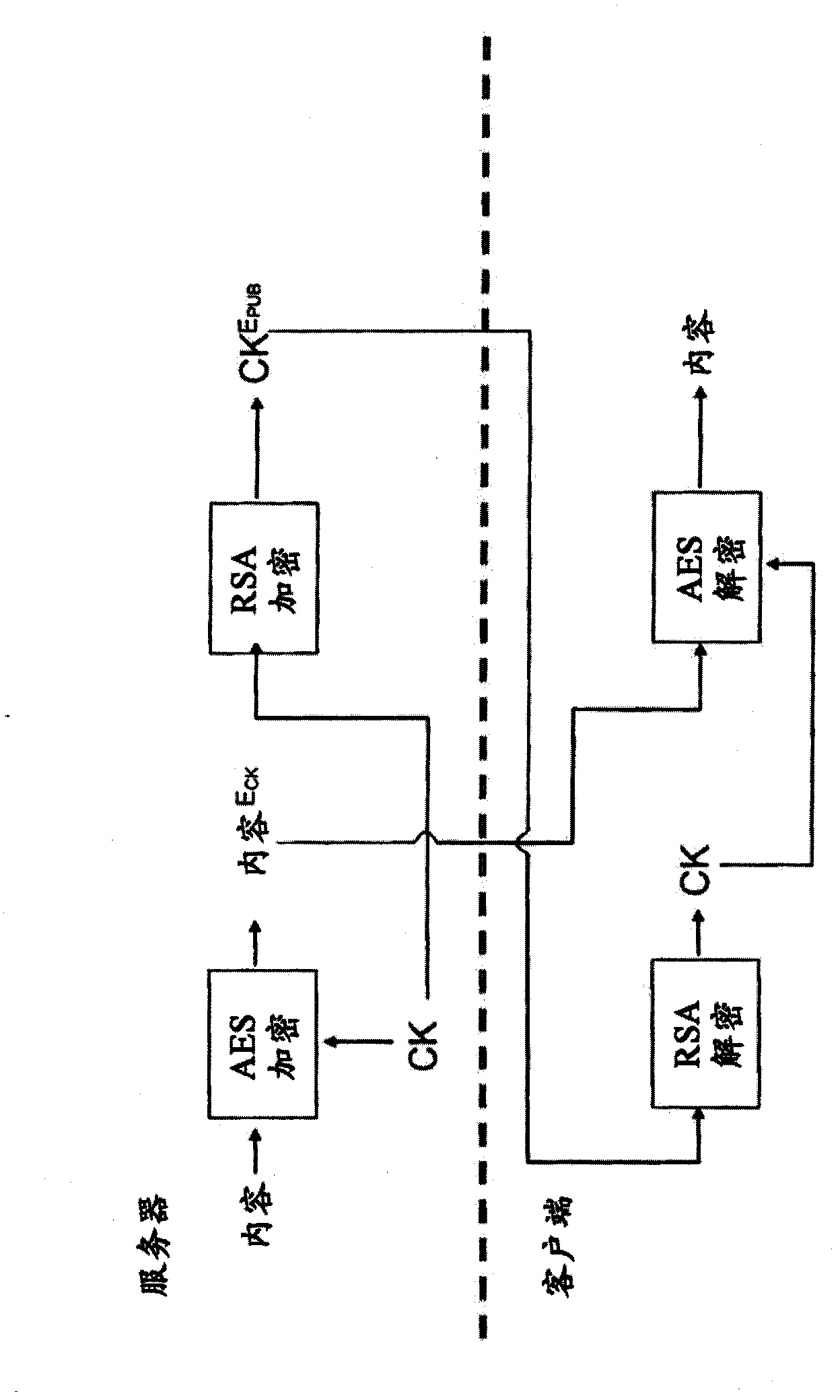
[0018] Clearly, there is a need for a method and system by which the steps of constructing surrounding implicit and mutually implicit parts of an application that uses white-box cryptography functions can be automated, making the error-prone methods currently used to construct such systems methods can be replaced by fairly reliable automated methods. To achieve this, embodiments are disclosed in which the ordinary intra-cryptic parts of the application (the parts that actually perform the white-box operations) are made more transparent than is customary for these parts. Flexible to adapt to the above mentioned automation system.
[0019] The benefits of such a system are similar to those gained by compiling code rather than writing hand-assembled code. In theory, a good programmer should be able to write applications in hand-assembled code. In practice, however, manual assembly code is extremely error-prone, and compilers make complexity never possible at the assembly code l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com