Method for detecting existence of virtual machine monitor (VMM) under Windows platform
A virtual machine monitor and platform technology, which is applied in the direction of platform integrity maintenance, instruments, computer security devices, etc., can solve the problems of no detection of VMM technical solutions, and the inability to distinguish the current operating system operating environment, so as to avoid malicious tampering and apply Effect of increased range, reliability and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
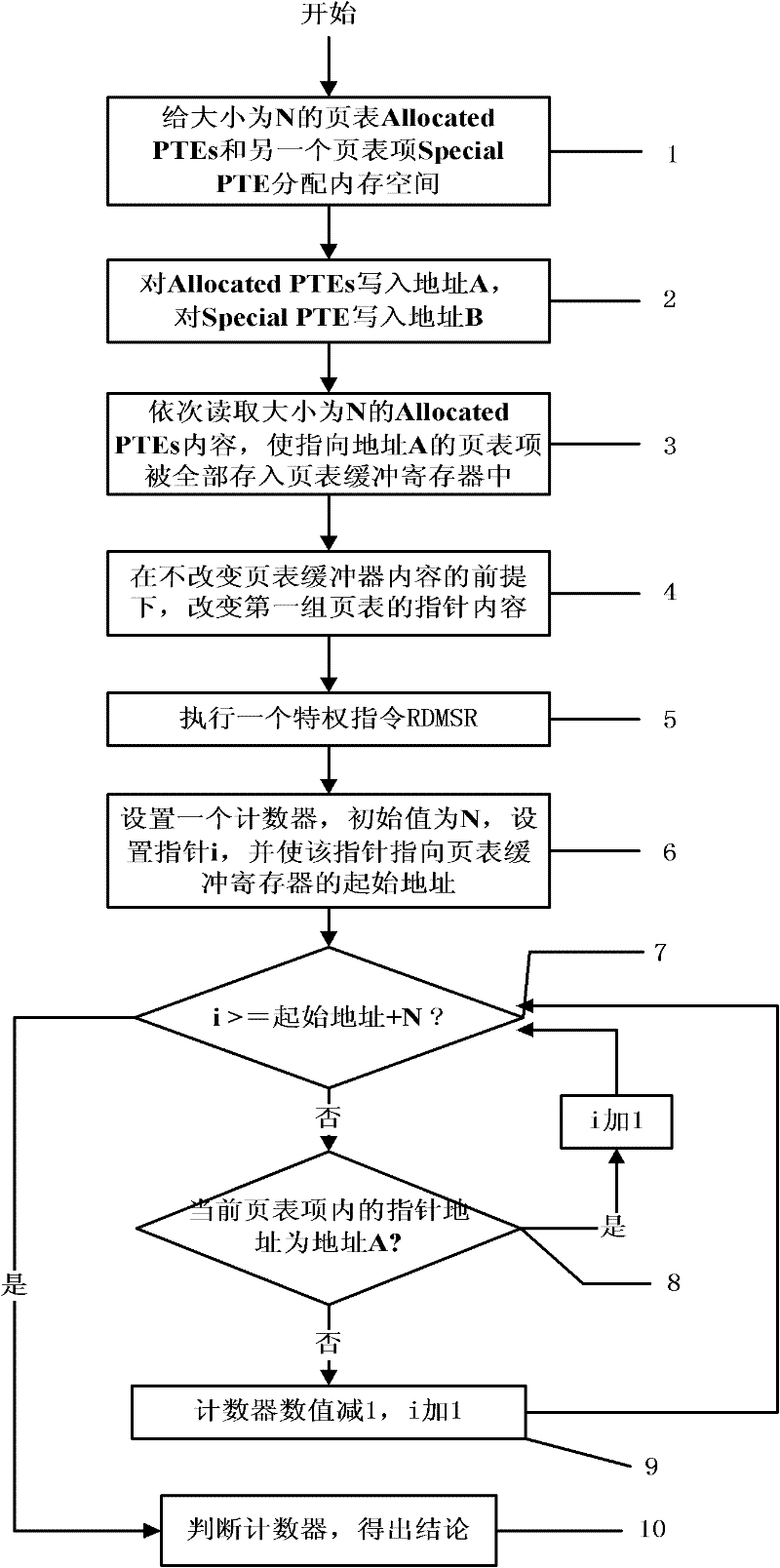
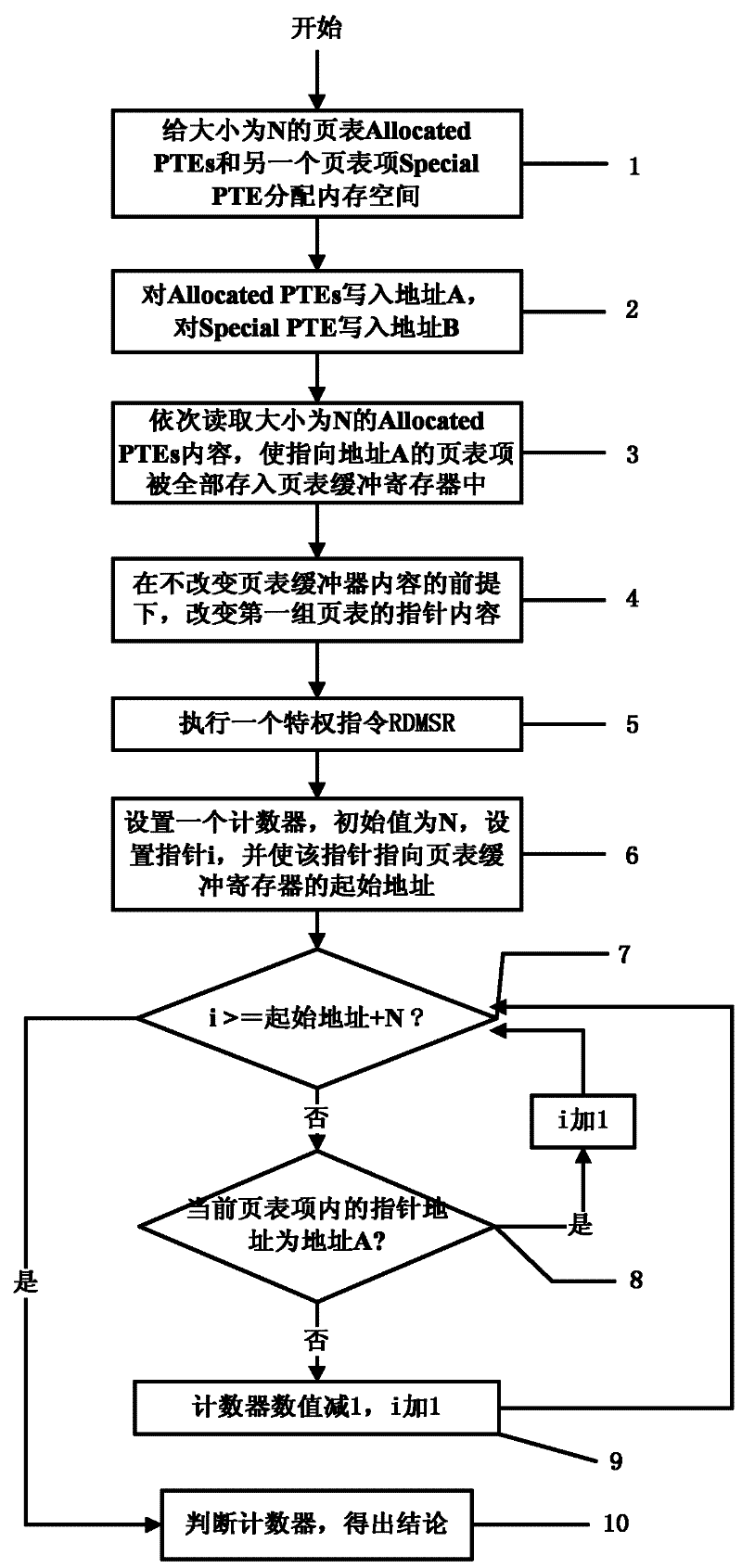
[0032] figure 1 Is the general flowchart of the present invention.
[0033] Step 1), allocate memory space to the page table Allocated PTEs of size N and another page table entry Special PTE;
[0034] Step 2), write address A for Allocated PTEs, and write address B for Special PTEs;
[0035] Step 3), sequentially read the content of Allocated PTEs with a size of N, so that all page table entries pointing to address A are stored in the page table buffer register;
[0036] Step 4), without changing the content of the page table buffer, change the content of the Allocated PTEs pointer to the address B pointed to by the Special PTE in turn;
[0037] Step 5), execute a privileged instruction RDMSR;
[0038] Step 6), set a counter, the initial value is N, set the pointer i, and make the pointer point to the starting address of the page table buffer register;
[0039] Step 7), if the pointer i has traversed all the page table entries in the page table buffer register, then execut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com