Elliptic curve and bilinear pairing cryptography based direct anonymous proving method
A bilinear pairing and elliptic curve technology, applied in the computer field, can solve the problems of low protocol efficiency, destruction of anonymity of the proving party, etc., and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
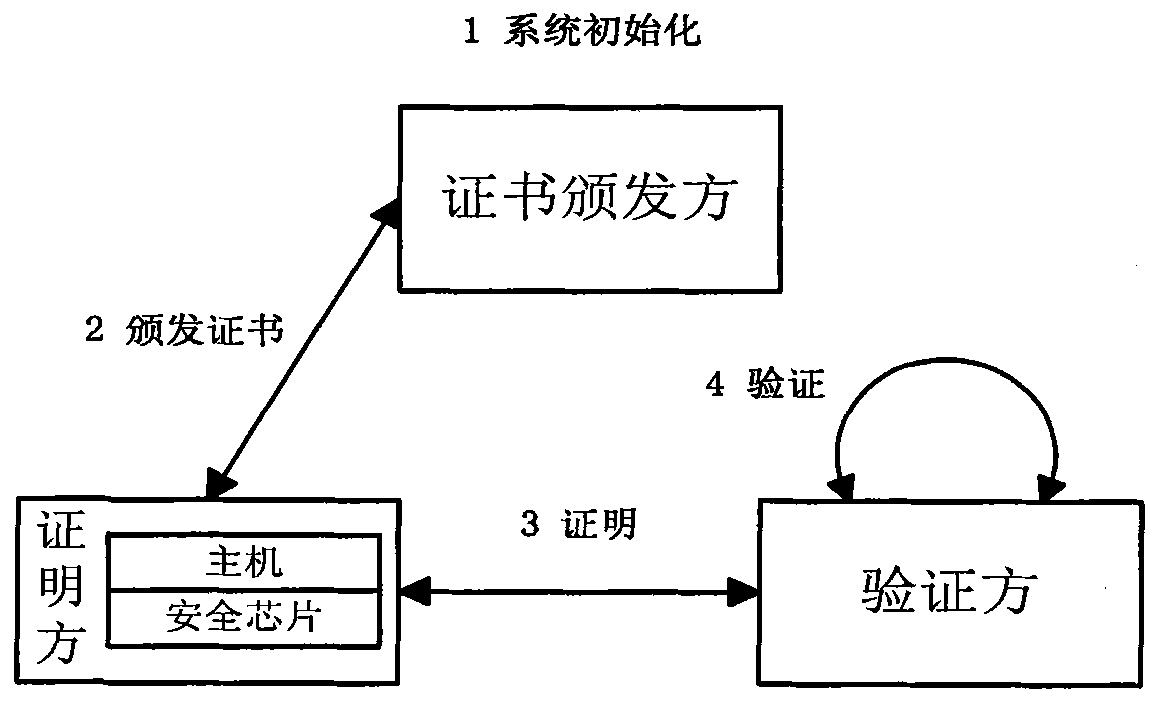
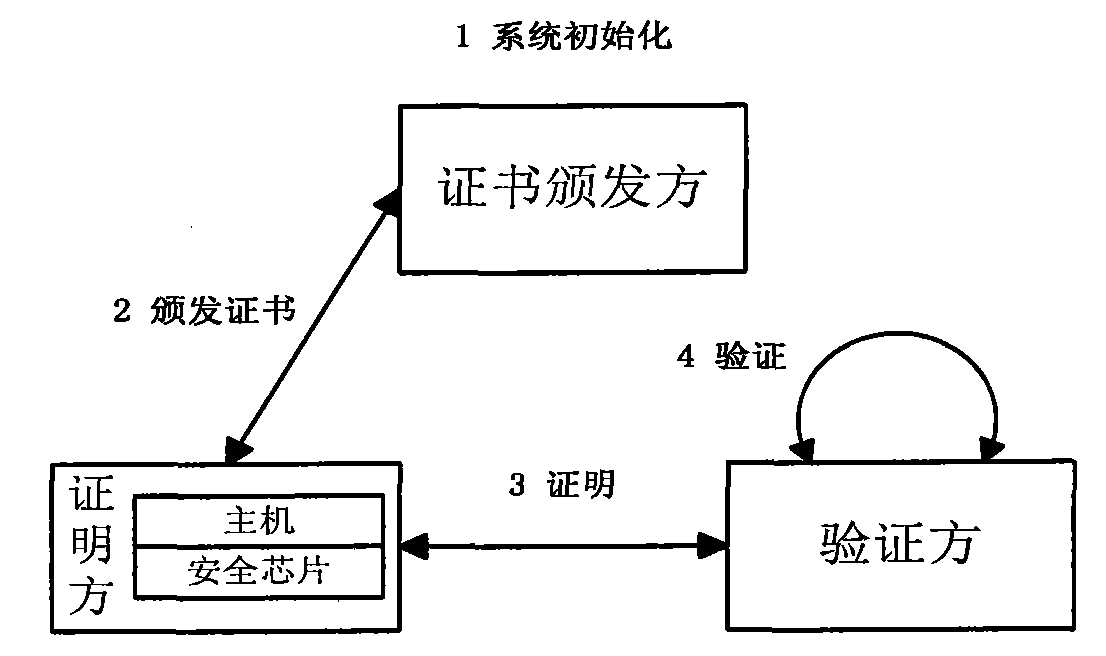
[0042] A direct anonymous proof method based on elliptic curve and bilinear pairing cryptosystem. The participating entities of the method include a certificate issuer, a prover and a verifier. The method mainly includes the following steps:
[0043] 1) Certificate issuer system initialization
[0044]A. The certificate issuer determines the blind signature method to be used; the certificate issuer can choose a suitable blind signature method according to the actual situation, for example, the CL-LRSW method (J.Camenisch, and A.Lysyanskaya.Signature schemes and anonymous credentials from bilinear maps.In: Franklin, M. (ed.) CRYPTO2004.LNCS, vol.3152, pp.56-72. Springer, Heidelberg (2004)) or the BBS+ method (M.H.Au, W.Susilo and Y. Mu. Constant-size dynamic k-TAA. In the Proceedings of 5th International Conference on Security and Cryptography for Networks (SCN 2006). LNCS, vol.4116, pp.111-125. Springer-Verlag, 2006.). The selected blind signature method requires that the own...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com