Fishing mail inspection method based on text characteristic analysis
A phishing email and feature analysis technology, applied in the field of information security, can solve the problems of phishing web page creator deception, etc., and achieve a wide range of uses and applications.
Inactive Publication Date: 2011-06-15
NANJING UNIV OF POSTS & TELECOMM
View PDF3 Cites 39 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
This method expands the idea of research on the characteristics of phishing webpages, and further improves the accuracy of phishing webpage detection to a certain extent. However, this method still only uses the information of a single webpage when extracting the characteristics of phishing webpages, so it is easy to be made deceived
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
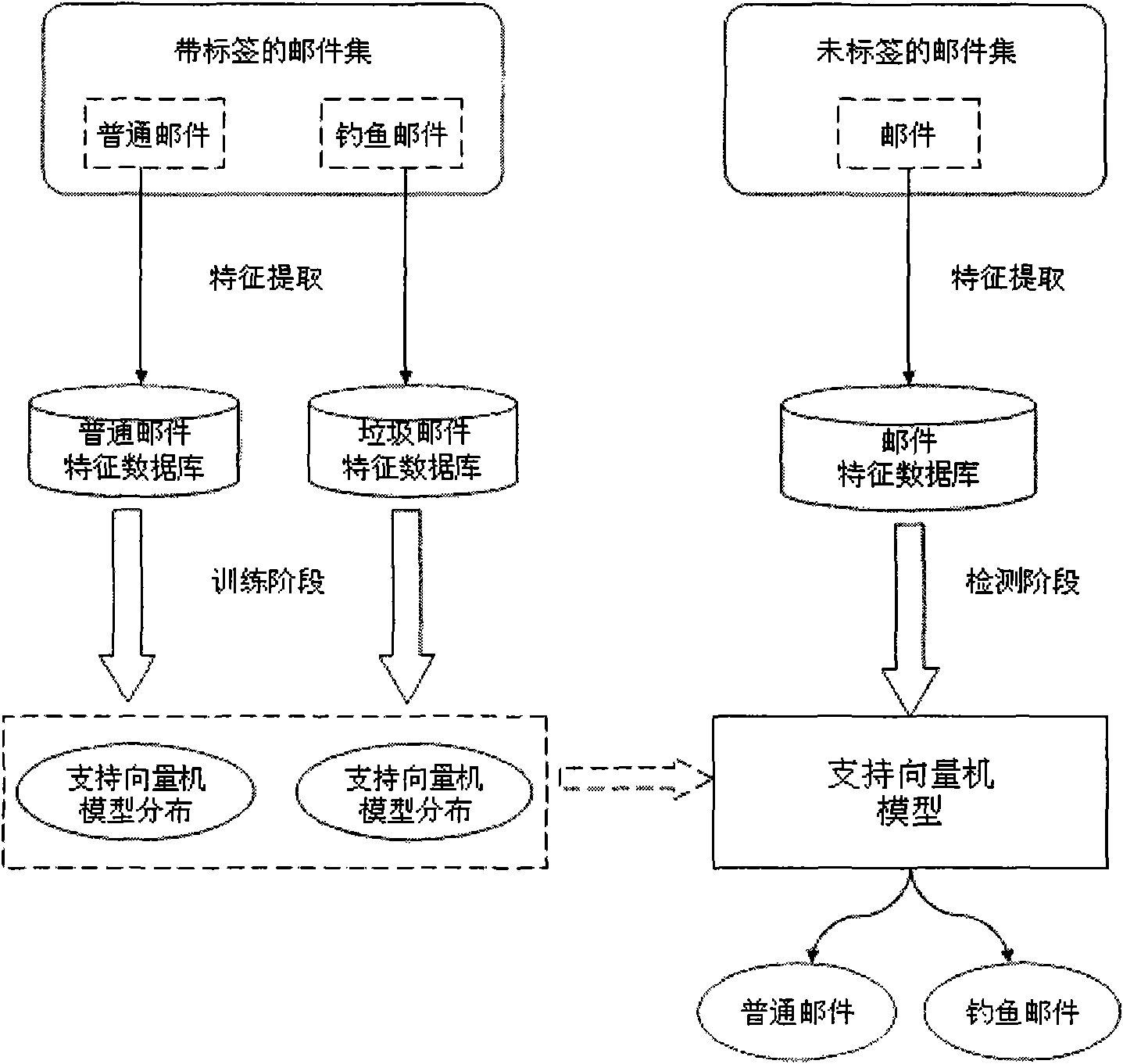
The invention provides a fishing mail inspection method based on text characteristic analysis, which is characterized by comprising the following steps: eliminating non-text contents in mails; utilizing a mail analyzer to analyze the mails; utilizing a regular expression algorithm to extract sitelinks in the mails; utilizing the regular expression algorithm to extract relevant characteristics in the sitelinks again; and using a domain name to register for a search engine to obtain the site registration date characteristics. The extracted text characteristics are the characteristic vectors of the mails. A test proves that the method is used to improve precision and recall of the fishing mails as well as save time and overhead of program operation. In the method, original text characteristics are subjected to screening, so that a plurality of characteristics with preferable effects are selected. The plurality of characteristics with preferable effects are combined with the characteristics of the fishing mails and the current research base so as to provide several new text characteristics aiming at the inspection of the fishing mails. The method is utilized to inspect suspicious mails.
Description
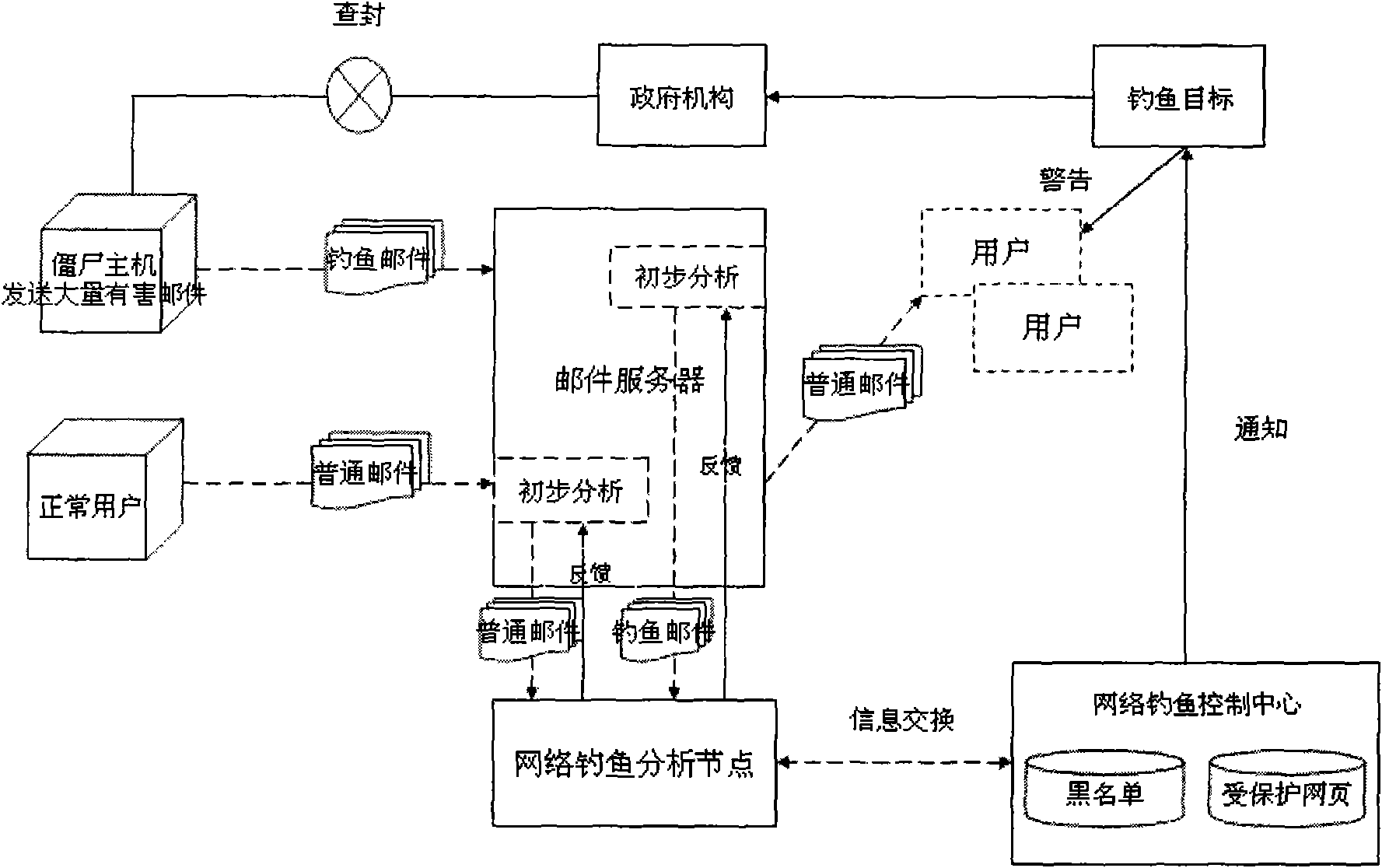
A phishing email detection method based on text feature analysis technical field The invention relates to a method for detecting phishing emails, mainly judging and identifying phishing emails from the perspective of email text feature analysis, and belongs to the field of information security. Background technique With the popularity of the Internet and the increase in online transactions, "phishing" has become extremely rampant. "Phishing websites" refer to fraudulent websites made by criminals, which are usually almost identical to bank websites or other well-known websites, thereby luring website users to submit sensitive information (such as user names, passwords, account numbers) on "phishing websites". or credit card details, etc.)[1]. And e-mail has become the best way for these criminals to spread these "phishing websites", which has led to a sharp expansion of the number of phishing e-mails. The phishing structure system is shown in Figure 1. The attack proces...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): H04L12/58H04L12/26
Inventor 张卫丰彭寅张迎周周国强陆柳敏许碧欢
Owner NANJING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com