Random point generation method suitable for elliptic curve cryptography (ECC) safety protection
An elliptic curve cryptography and security protection technology, which is applied in the field of random point generation suitable for elliptic curve cryptography security protection, and can solve the problem of large time cost of modular multiplication operations.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
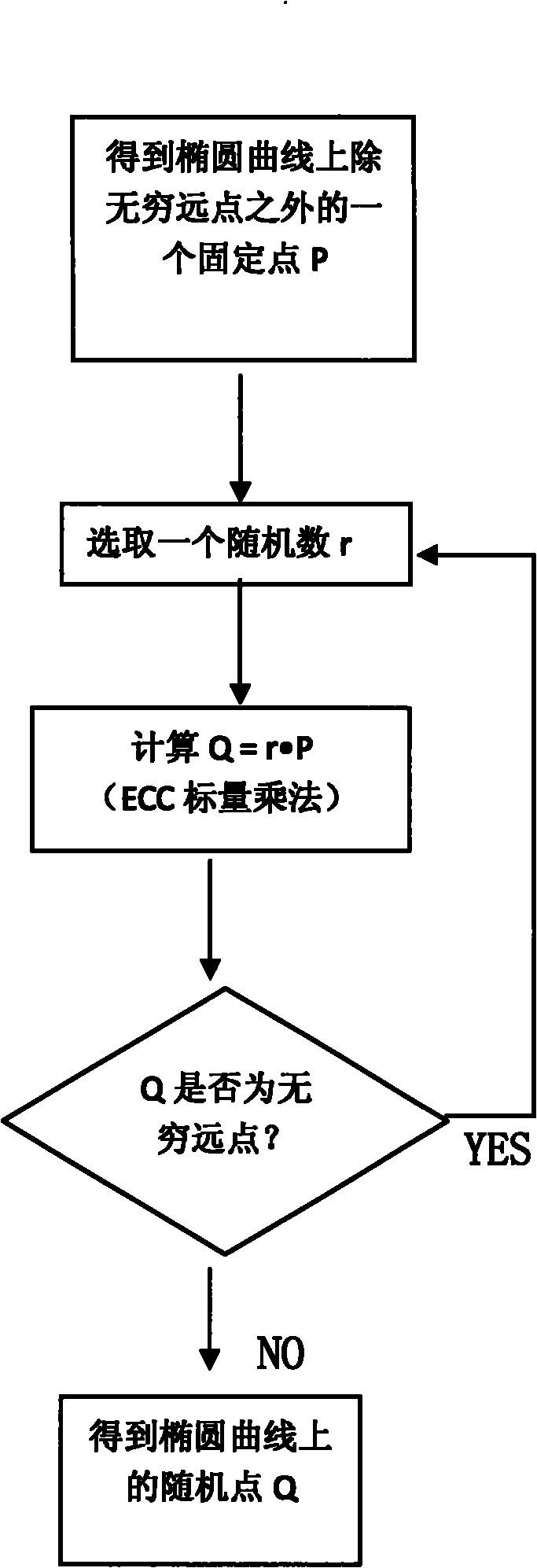
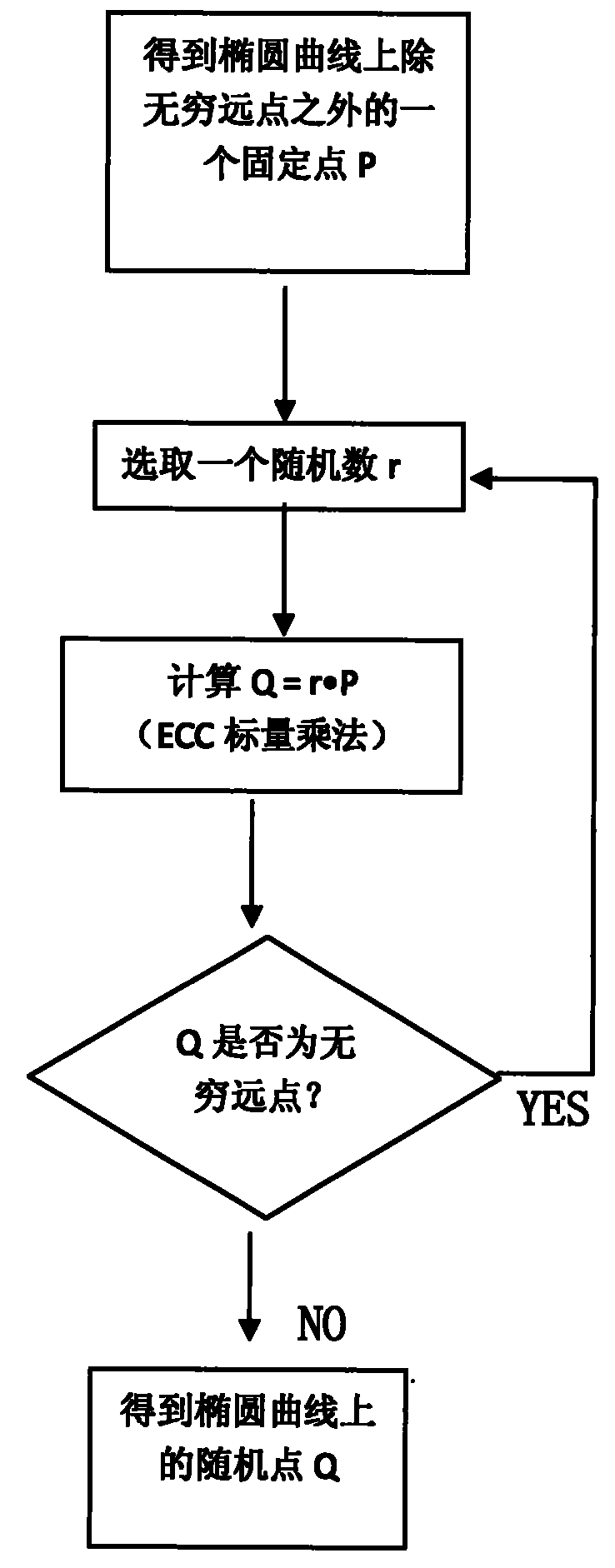
[0059] The following is an example of generating random points on an elliptic curve using the method of the present invention.
[0060] In the embodiment of the present invention, the given finite field is F p , the elliptic curve equation used is y 2 =x 3 -3x+b, the scalar multiplication coordinate system uses Jacobian projective coordinates, the scalar multiplication adopts the binary method from left to right, and the method of judging the point at infinity is whether the Z coordinate of the midpoint of the projective coordinates is 0.
[0061] Such as figure 1 As shown, the steps of generating random points on the specific elliptic curve of the present invention are as follows:
[0062] Step 1, get the elliptic curve y 2 =x 3 A fixed point P on -3x+b. The fixed point P can be any fixed point on the elliptic curve except the point at infinity.
[0063] Step 2, choose a random number r65 , a random number r of 64 bits or less can be randomly selected.
[0064] In ste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com