Data resource authority management method based on access control list
A technology of access control list and data resources, which is applied in the direction of electronic digital data processing, digital data authentication, instruments, etc., can solve the problems of low query efficiency and bloated content of access control list, and achieve the convenience of independent development, shorten the query time, interface clear effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
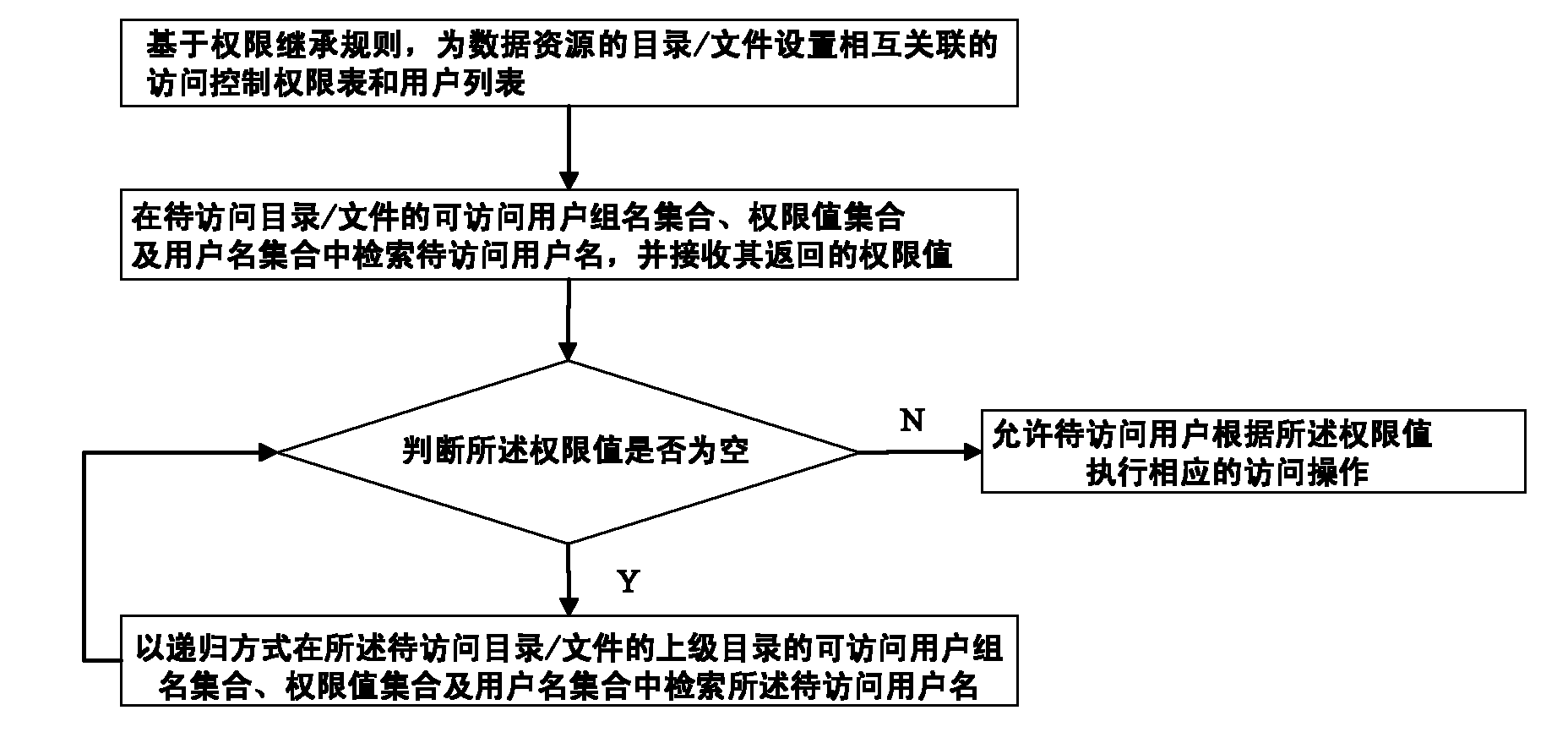
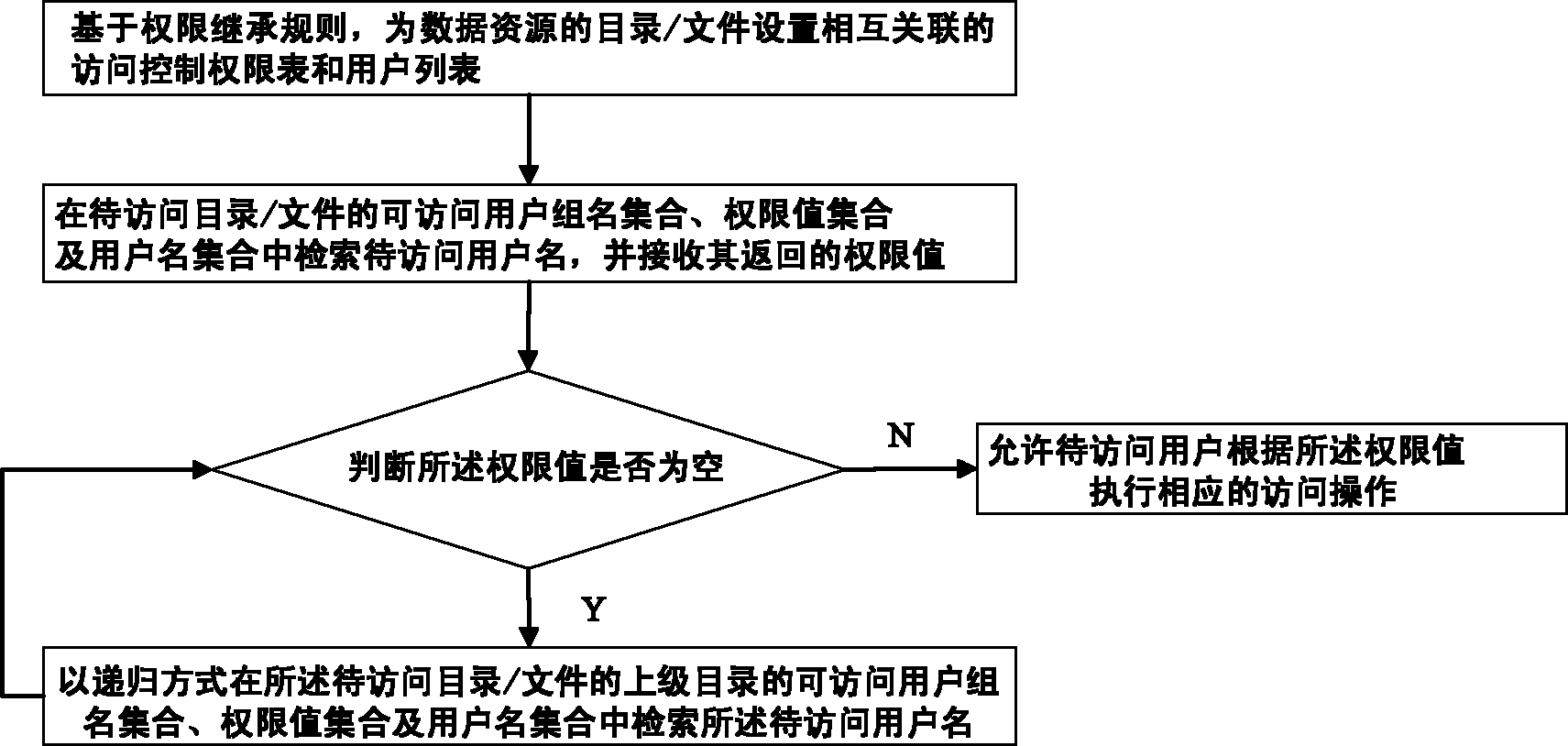
[0021] The data resource authority management method based on the access control list proposed by the present invention is described as follows in conjunction with the accompanying drawings and embodiments.
[0022] For a large-scale distributed storage system containing massive public resource data, in order to improve the response speed, the most effective measure is to reduce the number of records in the database as much as possible and shorten the single query time. The public resource data in a large-scale distributed storage system includes more than several million files, and most of the access control lists have the same value. Therefore, the core idea of the present invention is to adopt the authority inheritance strategy, so that the authority value of the parent directory is inherited when creating a new object or copying an object, thereby reducing repeated records and shortening the time for querying data as much as possible.
[0023] Such as figure 1 As shown,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com