Verifying authenticity of voice mail participants in telephony networks
一种语音邮件、证书的技术,应用在电话通信、电气元件、用户身份/权限验证等方向,能够解决语音邮件会话未被认证等问题
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
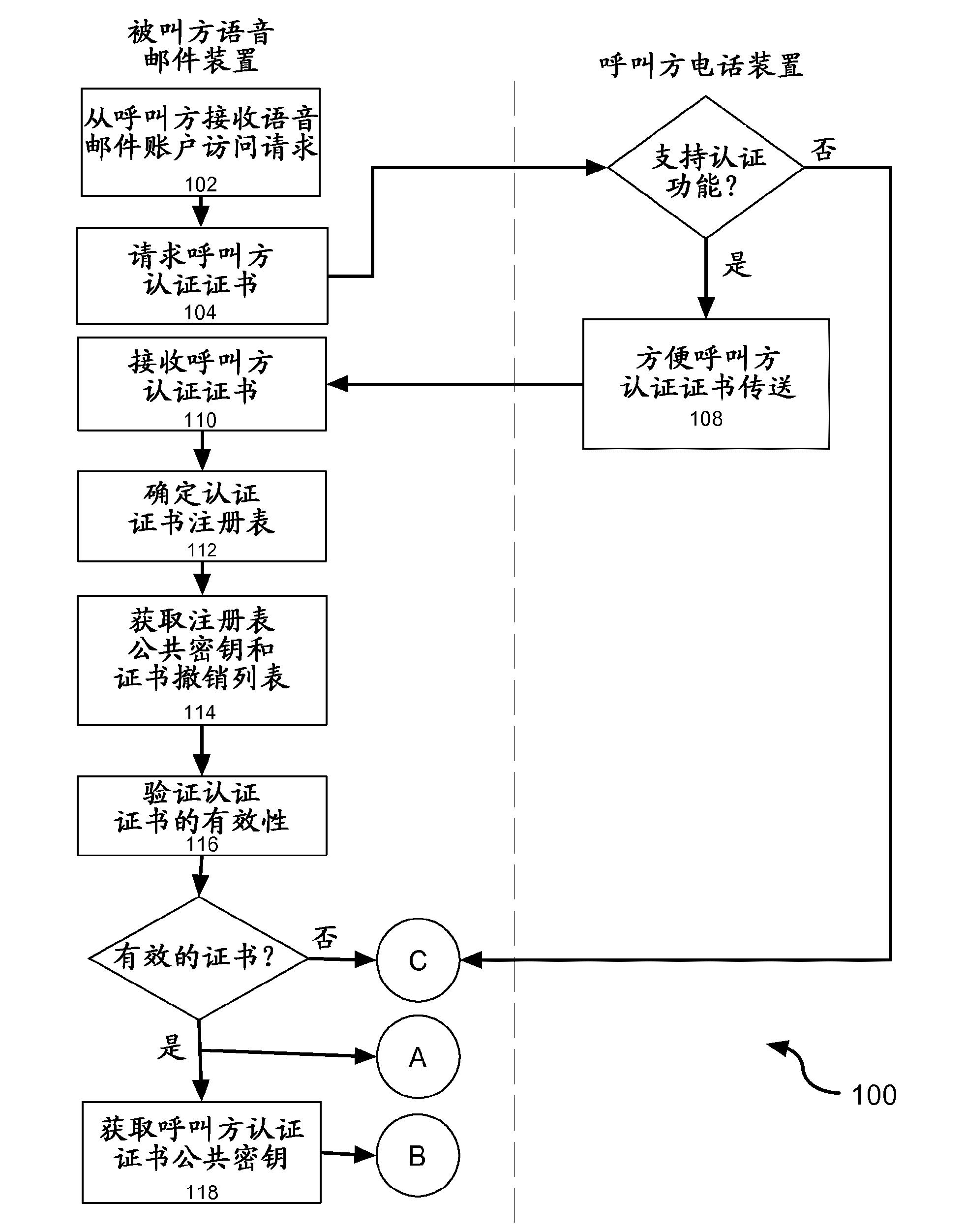
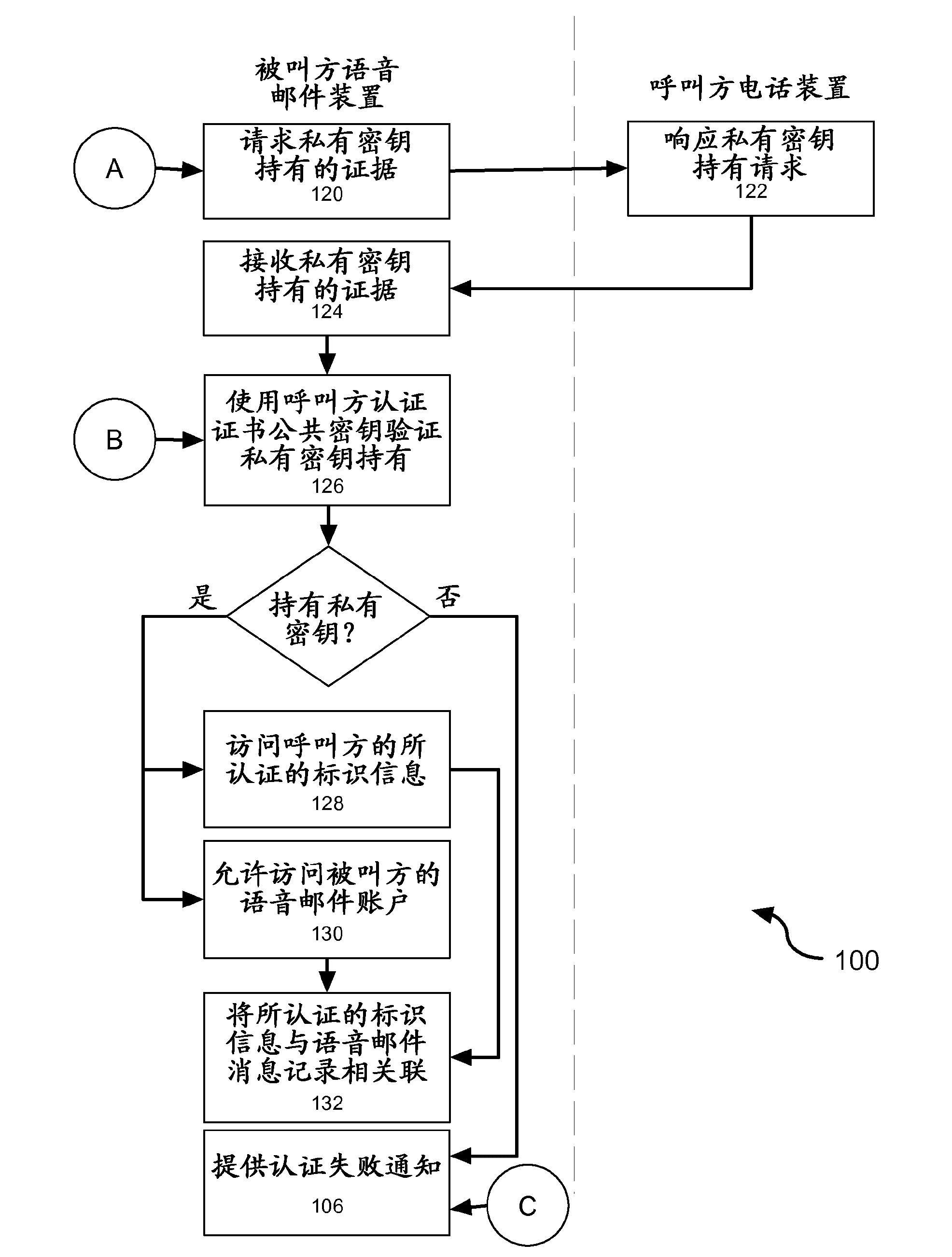
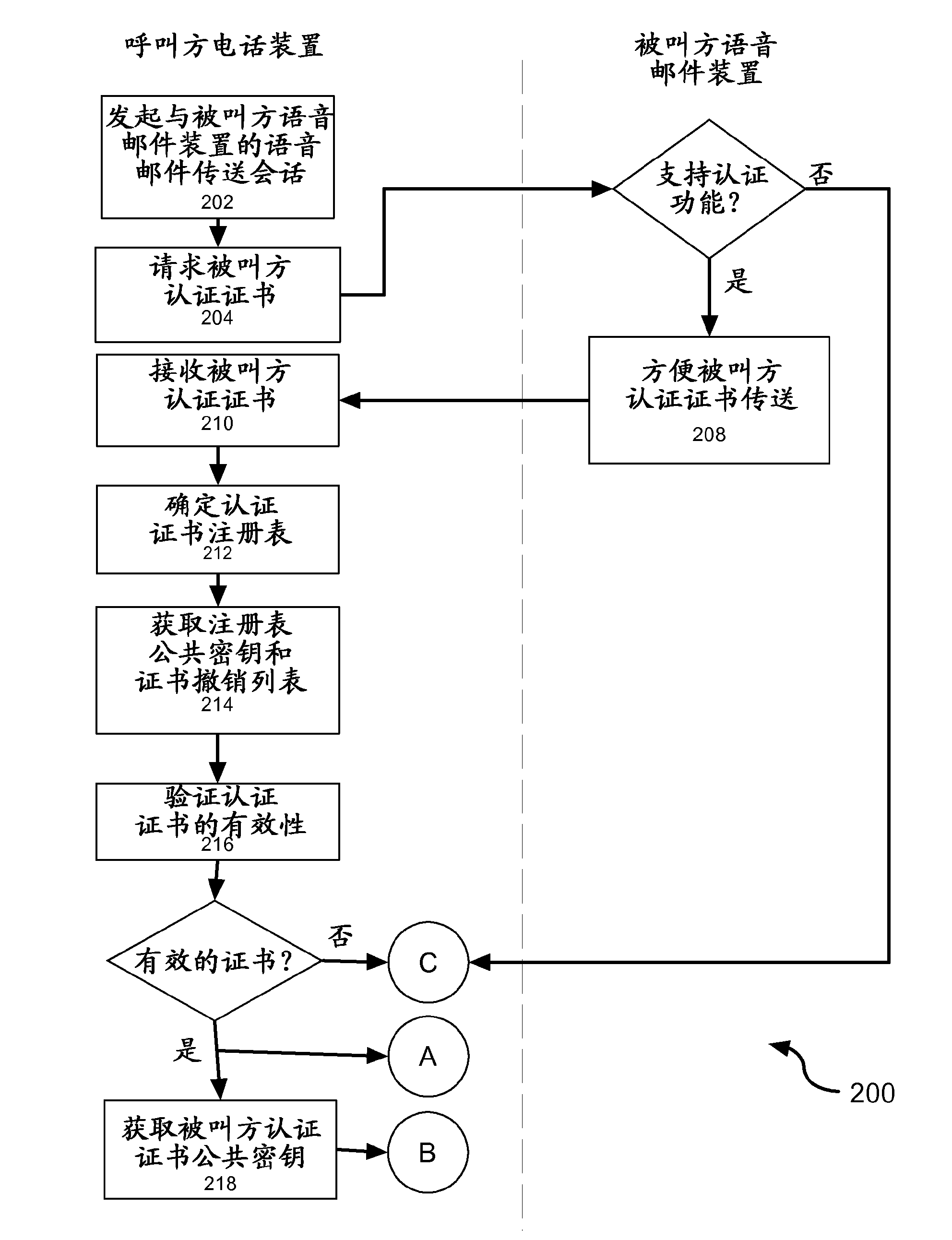
[0019] Embodiments of the present invention can be readily implemented on a variety of voicemail systems and telephony devices (eg, cell phones, PDAs, etc.). These embodiments utilize strong encryption capabilities based on X.509 certificates delivered through a trusted certificate authority registry, thereby allowing the called party's authentication to be authenticated in association with leaving a voicemail message for the called party and / or to Allows authentication of the caller before the caller leaves a voicemail message. In this way, a telephony device capable of displaying a list of voicemail messages can display authenticated identity information behind a voicemail message (i.e., when acting as an outbound messaging party) and utilize voicemail screening (i.e., when acting as an inbound messaging message participants) and conveniently incorporate this feature.
[0020]The present invention provides an enhanced level of security associated with voicemail system acces...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com