Dual-factor authentication method based on HASH chip or encryption chip
A two-factor authentication and encryption chip technology, applied in the field of computer application system security, can solve problems such as security damage in the authentication process, and achieve the effect of improving processing efficiency and server concurrent processing capability, improving security, and ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
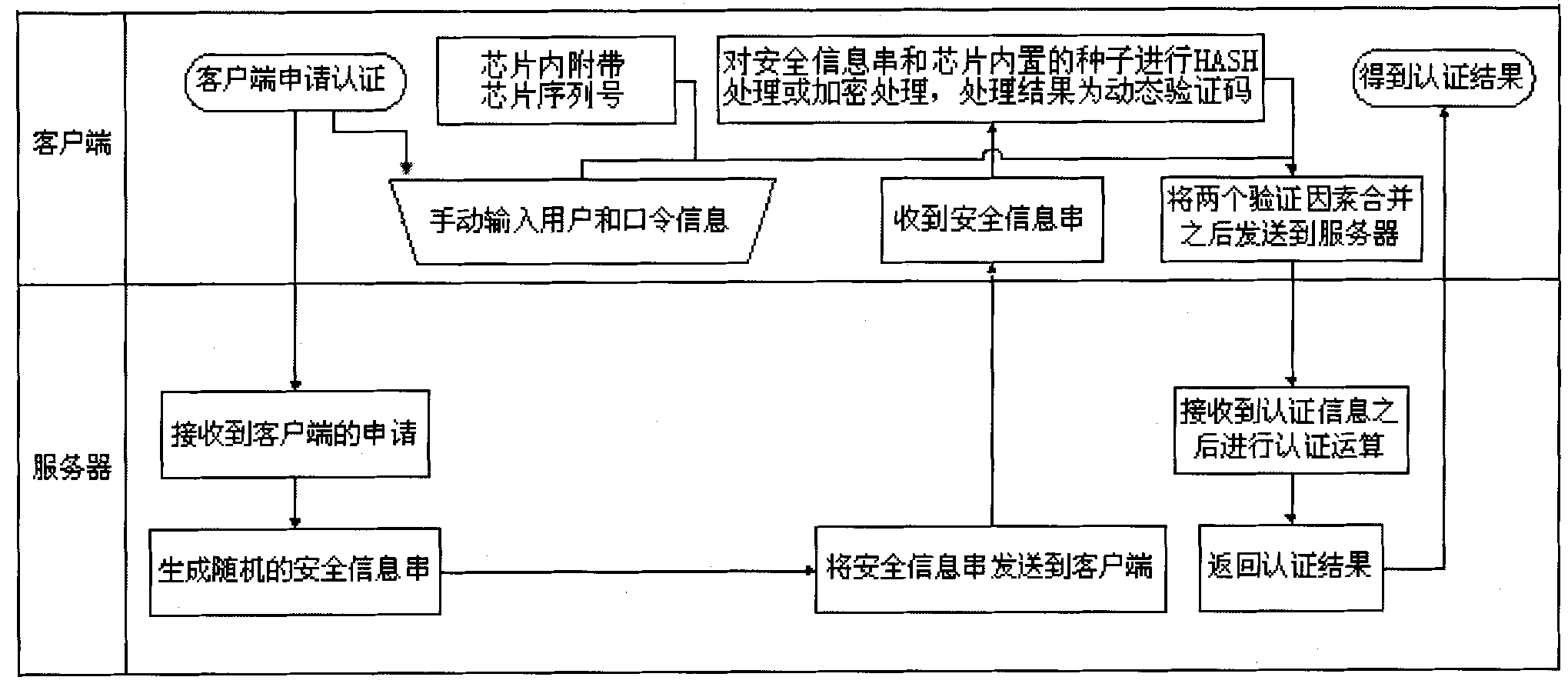
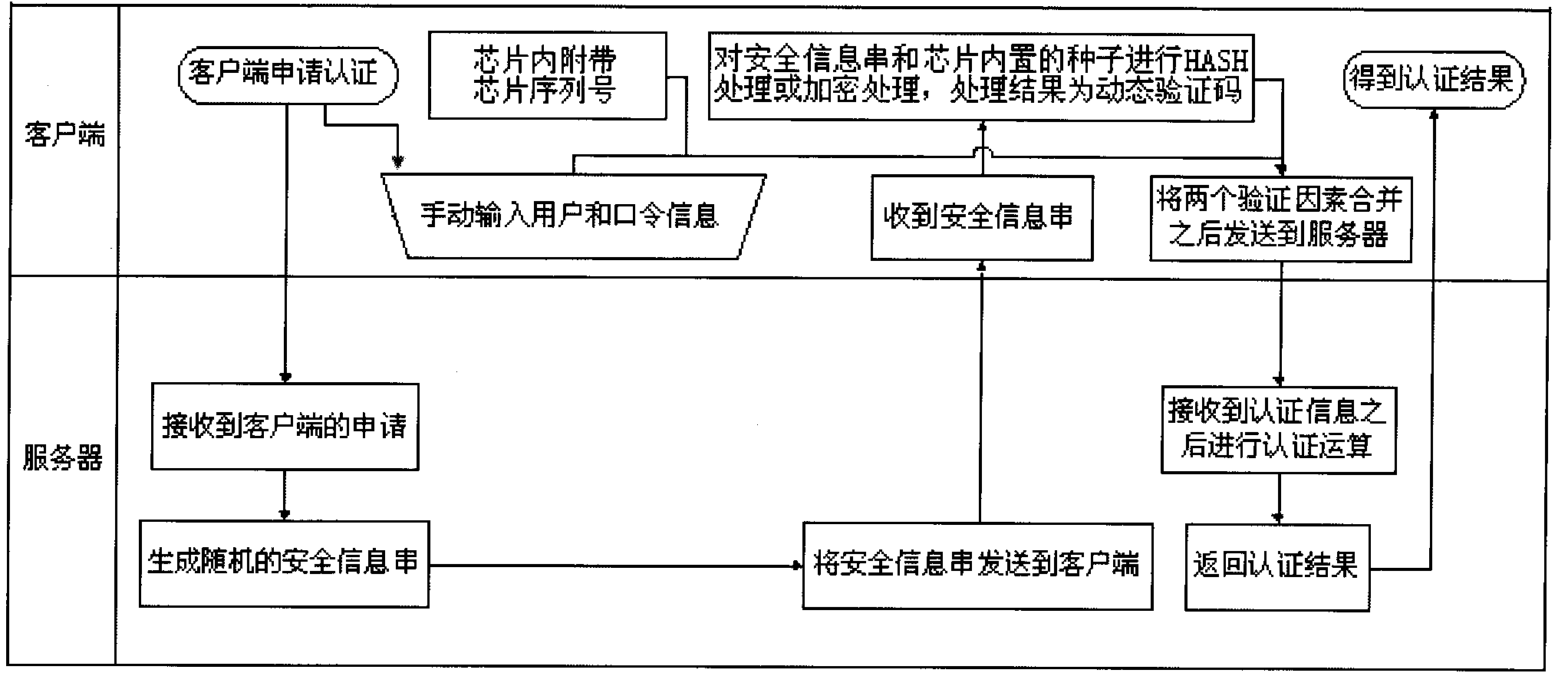
[0012] The present invention can use a cost-effective HASH chip (a chip using a HASH algorithm) or an encryption chip to perform two-factor authentication. HASH, generally translated into "hash", and also directly transliterated into "hash", is to transform an input of any length (also called pre-mapping, pre-image) into a fixed-length output through a hash algorithm. The output is the hash value. In the present invention, first, the HASH chip or encryption chip used by the client is shipped with a chip serial number and written into a randomly generated seed; when the client applies for authentication, the server sends a randomly generated seed after receiving the request. The security information is sent to the client, and the client uses a HASH chip or an encryption chip to perform HASH or encryption processing on the combination of the random security information sent by the server and the seed built into the chip. The result of the processing is a dynamic verification cod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com