Trojan-embedded website detection method based on hyper text transfer protocol (HTTP) traffic analysis
A detection method and flow analysis technology, applied in the computer field, can solve the problem of consuming large resources and achieve the effect of good detection effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
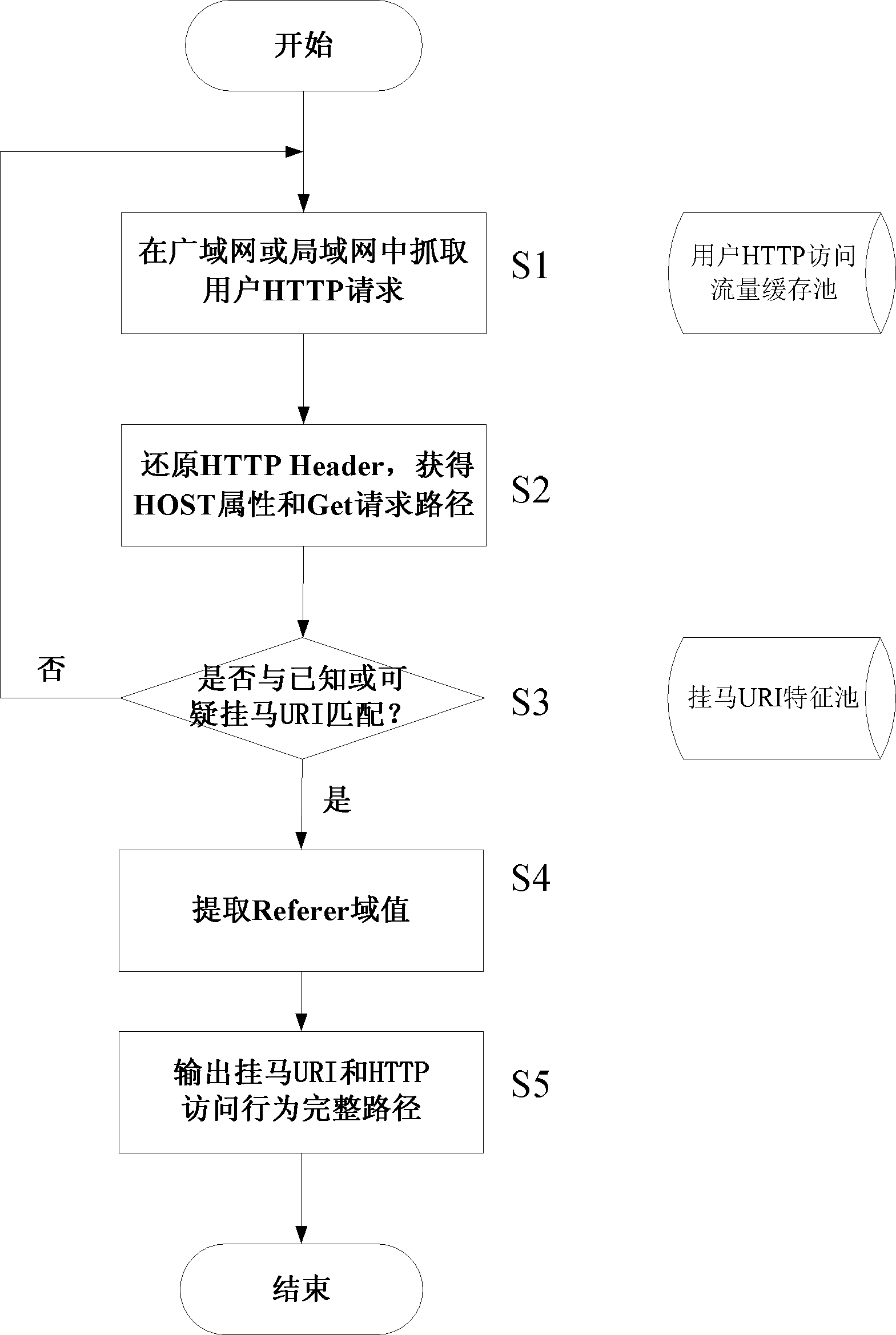
[0030] The method for detecting websites linked to horses based on HTTP traffic analysis provided by the present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0031] The inventor detects captured access requests to known or suspicious webpages that are linked to horses in the network bypass, and analyzes the Referer field of the header of the HTTP protocol data packet, so as to find those websites that have been invaded by linked horses.
[0032] After a lot of analysis and research on the characteristics of the current webpages that are linked to horses, it is found that the Referer domain value may play a special role in the detection of webpages that are linked to horses.
[0033] HTTP Referer is a part of the header. When the browser sends a request to the web server, it will usually bring the Referer to tell the server which page it is linked from, so that the server can obtain some information for pro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com