Encryption card certification and authority method adopting USB intelligent secret key and encryption card
An intelligent key, authentication and authorization technology, applied in the field of encryption cards, can solve the problems of unprotected keys in confidential cards, slow serial transmission of data, and influence of authentication speed, so as to achieve rapid completion of authentication and backup, and improve security strength and safety. Sex-enhancing effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] Specific implementation plan
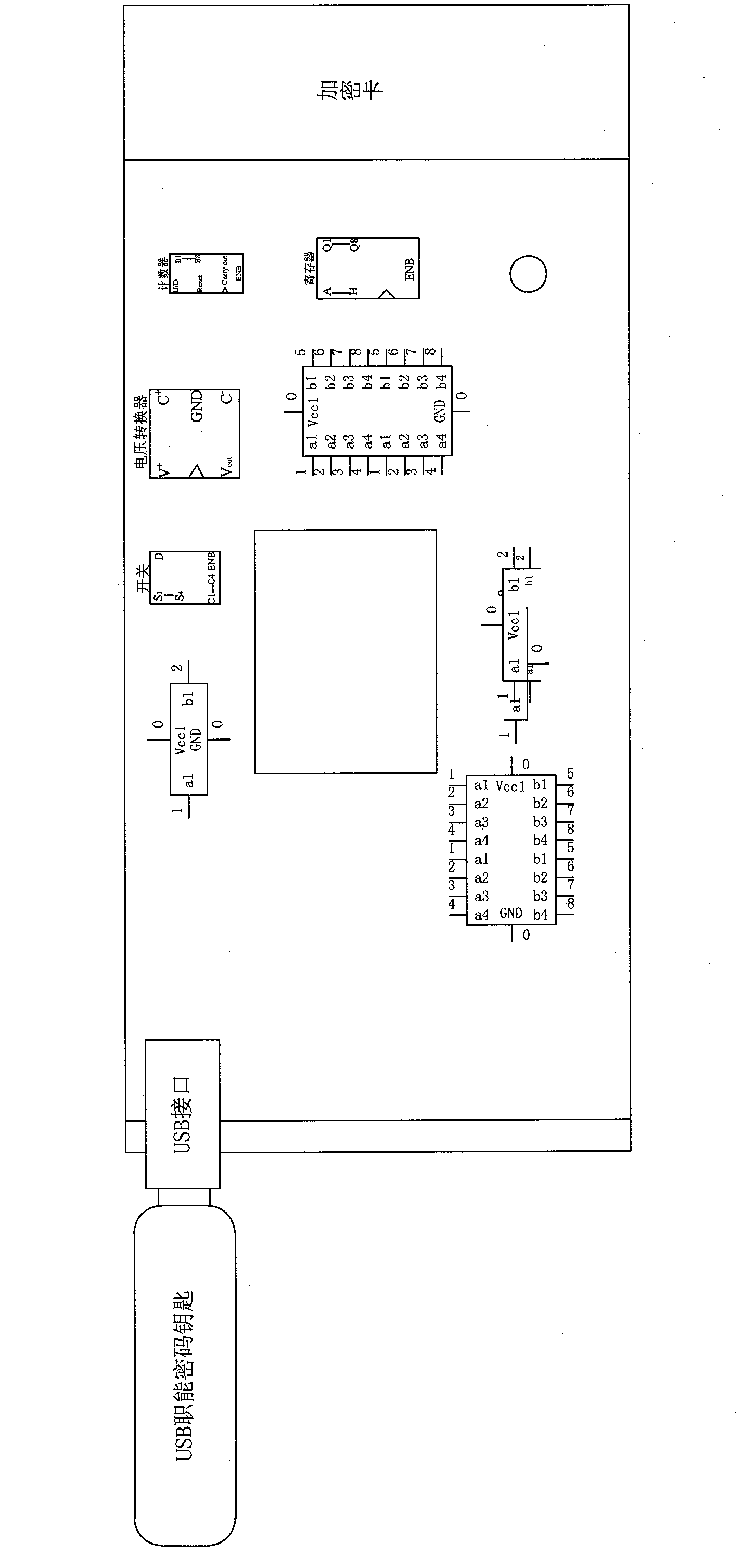
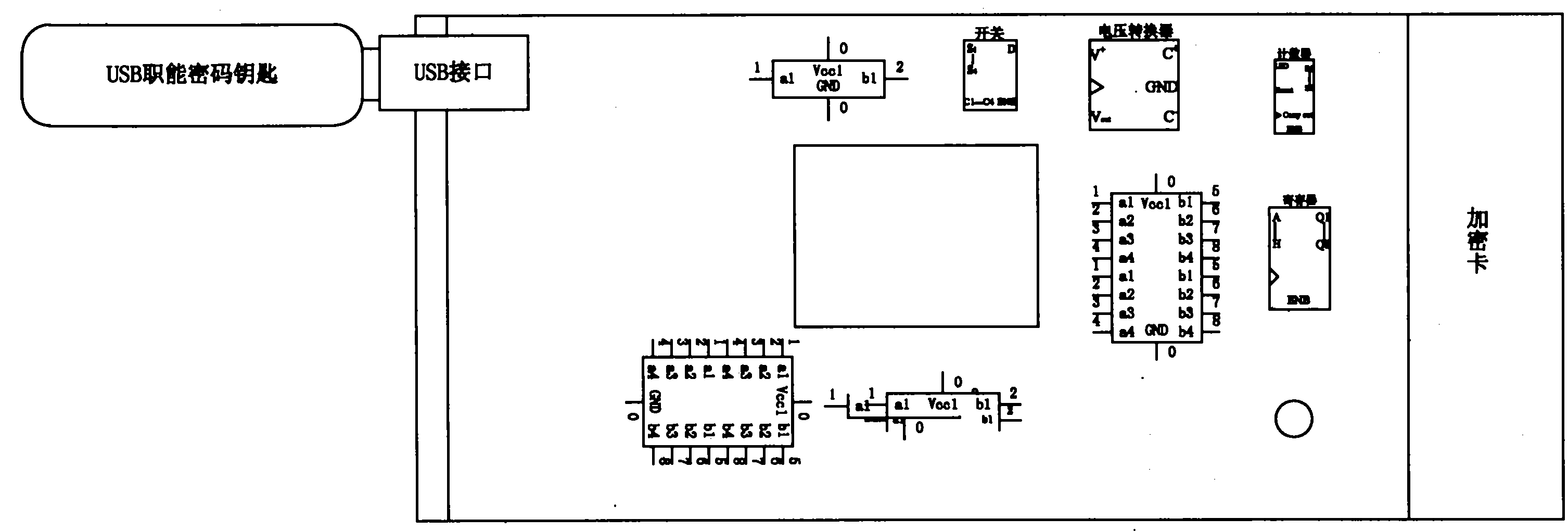
[0034] Aiming at the current problems of encryption card authentication, management and data protection, the present invention provides a safe, efficient and easily expandable solution.
[0035] Authorization:
[0036] (1). We issue a certificate (or key pair, not counting) for each USB smart cryptographic key to identify the user. Due to the physical characteristics of the USB smart cryptographic key, the private key of the certificate (or key pair) cannot be copied and exported, fundamentally eliminating the possibility of media being copied. Even if the USB smart password key is lost, it is still protected by the PIN code of the USB smart password key, and the private key cannot be used without knowing the PIN code.
[0037] (2) All data in the encryption card is encrypted and saved (this key is referred to as the protection key in this article); (3) The encryption card authorizes the USB smart password key, and the protection key of the encry...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com