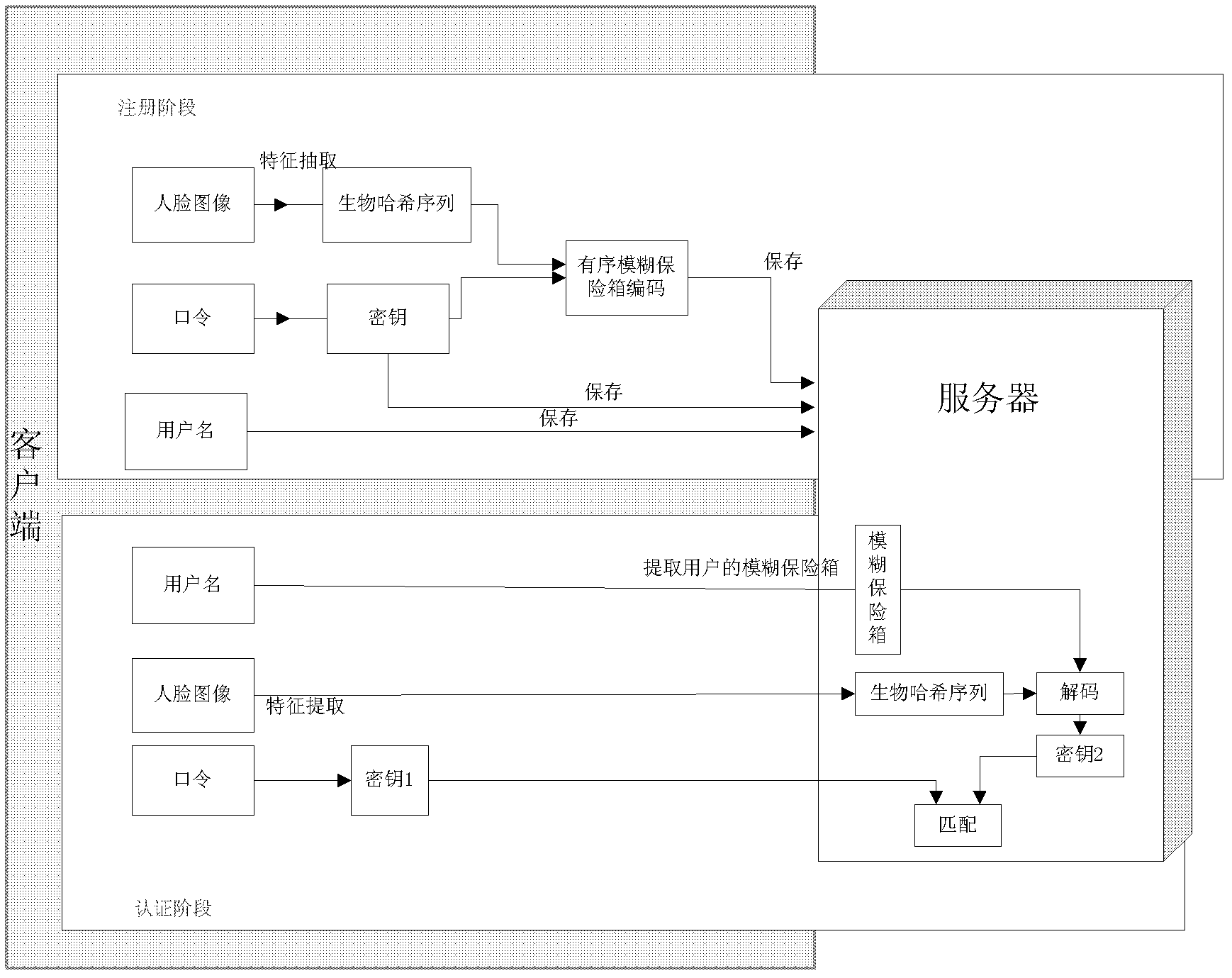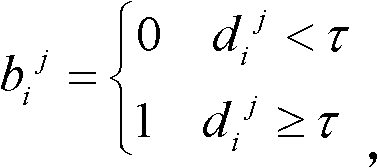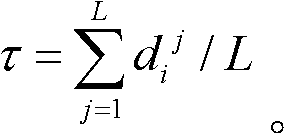Fuzzy strong box remote identity authentication method based on face feature
A technology of fuzzy safes and facial features, applied in user identity/authority verification, character and pattern recognition, instruments, etc., can solve problems such as security degradation, intolerance of intra-class changes, cross-matching, etc., and reduce FAR recognition. rate, avoid aliasing matching, and ensure the effect of security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The scheme we proposed uses face hashing to realize the randomization of facial features; furthermore, an ordered fuzzy safe encoding and decoding scheme is proposed, which makes full use of the orderliness of facial biometric features. Specific programs such as figure 1 shown.
[0047] The scheme is oriented to the client / server structure, including two stages of registration and authentication.
[0048] 1.1 Perform feature extraction on the face image to obtain an ordered sequence of face features;
[0049] 1.2 Generate multiple biological hash sequences: use the password entered by the user as a random seed to generate a series of pseudo-random numbers and form a matrix Q in a specific order, and perform random mapping on the face features, that is, multiply the face feature sequence by the matrix Q, Binarize the obtained array into a string sequence (that is, generate a biological hash sequence);
[0050] 1.3 Ordered fuzzy safe code:
[0051] 1.3.1 Generating po...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com