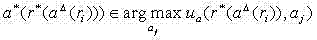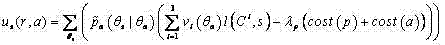Attack-graph-based intrusion response mode
An attack graph and attacker's technology, applied to electrical components, transmission systems, etc., to achieve the effect of enhancing accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] 1. Attack the subsequent attack set of p
[0034]
[0035] 2. Through the game situation Profits to Computing Systems and Profits to Attackers
[0036]
[0037]
[0038] 3. Calculation of the next attack predicted by the attack system a. The loss of the system on each security scale caused by the attack p reported by the alarm
[0039]
[0040] 4. When the attacker uses a as the next attack action, the income of the attacker and the system are respectively
[0041]
[0042]
[0043] 5. Calculate the attacker's best next attack action as
[0044]
[0045] 6. Calculate the best response of the system
[0046]
[0047] 7. After the system’s best response action, the attacker’s next best response action in the whole game process is
[0048]
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com