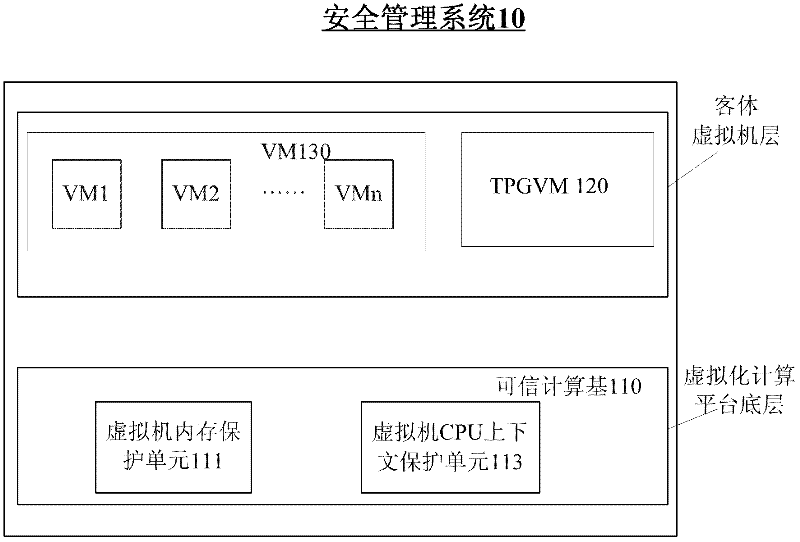
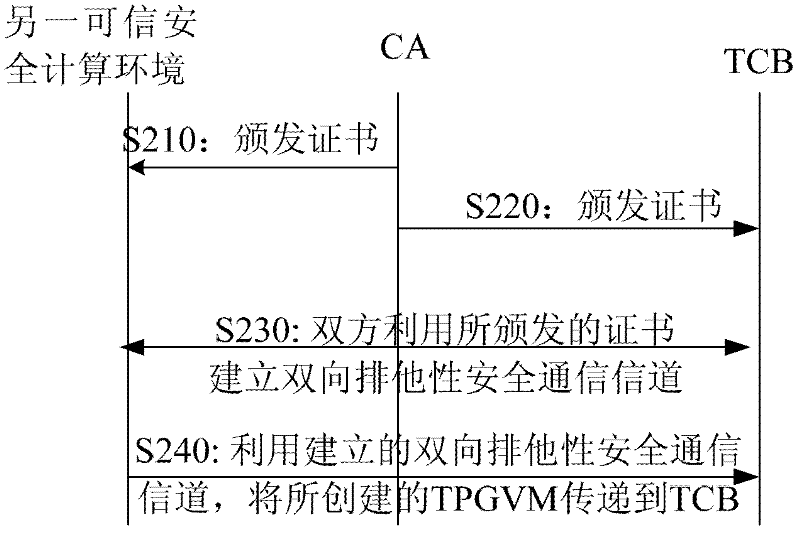
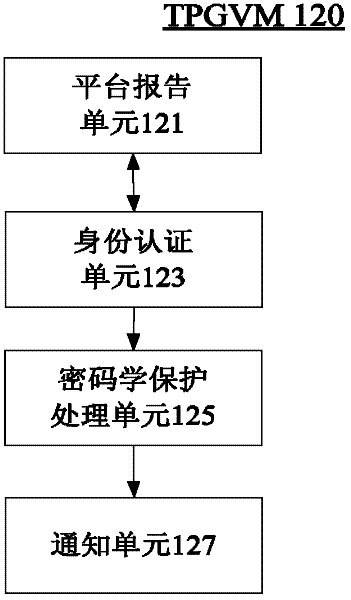
Method and system for full life cycle security management of virtual machine
A technology of full life cycle and life cycle, which is applied in the field of providing security management of virtual machine life cycle on virtualized computing platform, and can solve problems such as TCB agent malicious attack.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] Various aspects of the disclosure are described below. It should be appreciated that the teachings herein may be embodied in a wide variety of forms and that any specific structure, function, or both disclosed herein are merely representative. Based on the teachings herein one skilled in the art should appreciate that an aspect disclosed herein may be implemented independently of any other aspects and that two or more of these aspects may be combined in various ways. For example, an apparatus may be implemented or a method practiced using any number of the aspects set forth herein. In addition, such an apparatus may be implemented or such a method may be practiced with other structure, functionality, or structure and functionality in addition to or in addition to one or more of the aspects set forth herein. Additionally, any aspect described herein may comprise at least one element of a claim.
[0034] With regard to the virtualization system, the term "virtualization...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com