Method for detecting broadband private connection based on open system interconnection (OSI) transmission layer timestamp
A detection method and time stamping technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve the problems of high system resource occupation, ineffective time-sharing Internet access, and narrow application scope, and achieve low system resource occupation and standardize the Internet. Market, a wide range of effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
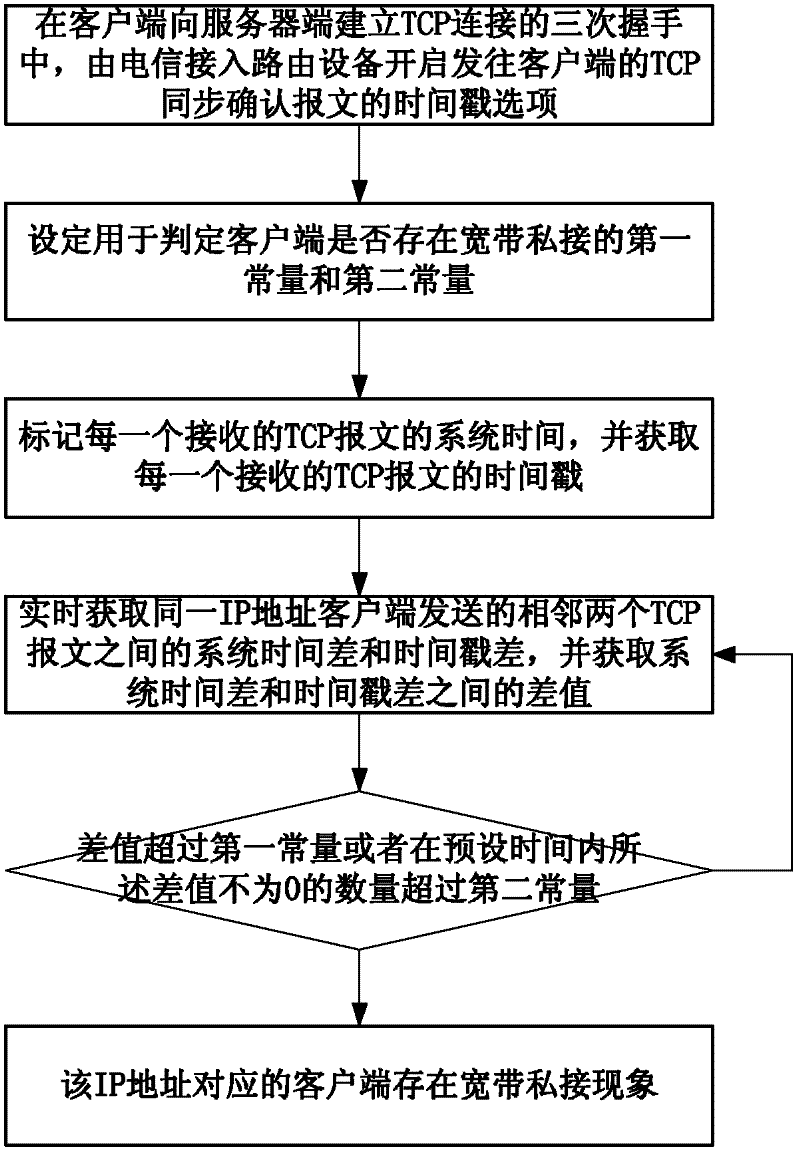
[0040] Such as figure 1 As shown, the implementation steps of the broadband private connection detection method based on the OSI transport layer timestamp in the embodiment of the present invention are as follows:
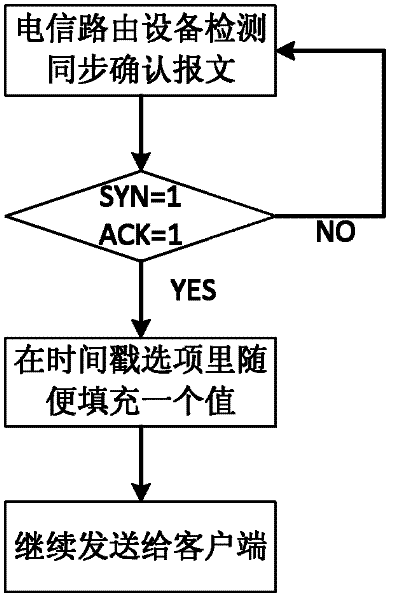
[0041] 1) When the client establishes a TCP connection to the telecommunications access routing device, the timestamp option of the client TCP message is enabled;
[0042] 2) Setting the first constant and the second constant for determining whether there is a broadband private connection in the client;
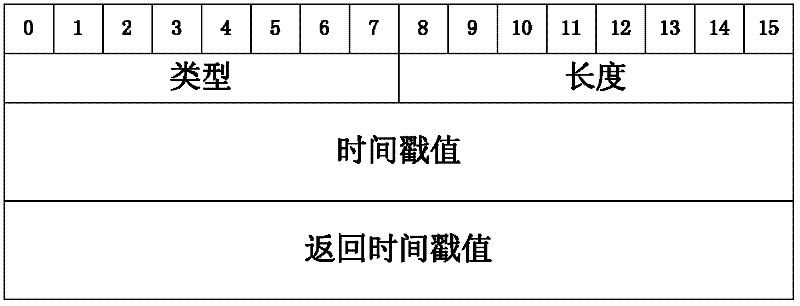
[0043] 3) mark the system time of each received TCP message, and obtain the timestamp of each received TCP message;
[0044] 4) Obtain the system time difference and timestamp difference between two adjacent TCP messages sent by the same IP address client in real time, and obtain the difference between the system time difference and the timestamp difference, if the difference exceeds the first constant or If the number of difference values that are not 0 withi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com