Method and device for enhancing user information input security
A technology for user information and security, applied in the field of information security, can solve problems such as increasing network bandwidth, failing to operate normally or downtime, and increasing network traffic so as to achieve the effect of strengthening security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
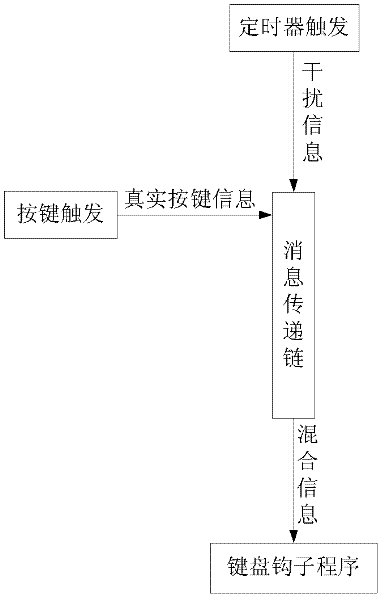
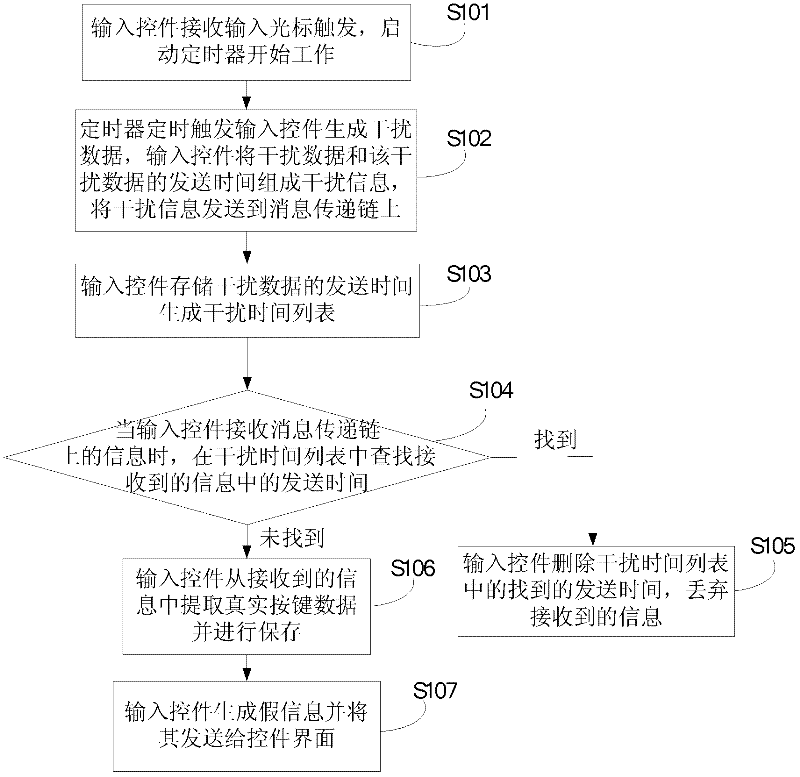
[0086] Embodiment 1 of the present invention provides a method for improving the security of user information input. In this embodiment, the information on the message delivery chain consists of data and sending time. For example, the interference information includes the interference data and the sending time of the interference data. The real key information includes the real key data and the sending time of the real key, and the input control distinguishes the interference information from the real key information by sending time, such as figure 2 shown, including:
[0087] S101: The input control receives the input cursor trigger, and starts the timer to start working;
[0088] S102: The timer regularly triggers the input control to generate interference data, the input control forms interference information from the interference data and the sending time of the interference data, and sends the interference information to the message delivery chain;
[0089] Preferably, ...
Embodiment 2
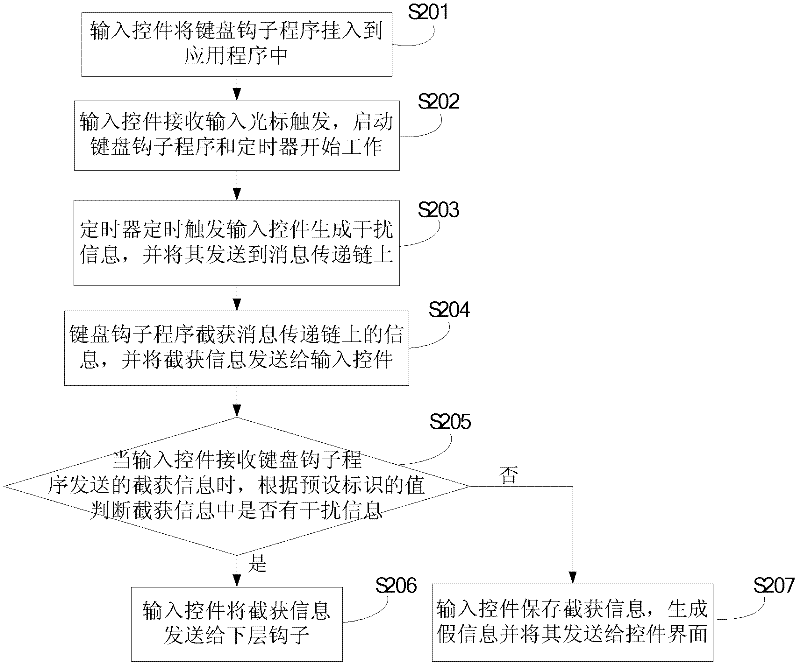
[0101] In order to prevent the data on the message transmission chain of the first embodiment from being intercepted by the hacker hook program, the second embodiment provides another method for improving the security of user information input, which is to set a keyboard hook program on the basis of the first embodiment. The keyboard hook program and the hacker hook program compete to intercept the information on the message delivery chain, and the keyboard hook program sends the intercepted information to the input control for processing. The method of this embodiment is as follows: image 3 shown, including:
[0102] S201: The input control hooks the keyboard hook program into the application program;
[0103] In this embodiment, the input control hangs the keyboard hook program into the application program by calling the HHOOK SetWindowsHookEx function of the API (Chinese name: application program interface); the keyboard hook program, the hacker hook program and other hook...
Embodiment 3
[0114] Embodiment 3 of the present invention provides another method for improving the security of user information input. In this method, multiple keyboard hook programs are set. The hook program intercepts the information from the message delivery chain and does not send it to the input control but processes it by itself, such as Figure 4 As shown, the method provided in this embodiment includes:
[0115] S301: The input control hooks multiple keyboard hook programs into the application program;
[0116]In this embodiment, the input control hooks the keyboard hook program into the application program by calling the HHOOK SetWindowsHookEx function of the API;
[0117] S302: the input control receives the input cursor trigger, starts the keyboard hook program and the timer starts to work;
[0118] Specifically, in this embodiment, the timer triggers the input control every 10 milliseconds to unload all keyboard hook programs and re-hook them into the application program, so...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com