Encryption method using random sequence on-demand and having misleading function
An encryption method and function technology, applied in the field of information security, can solve the problems of not really random, short keys, etc., to reduce redundancy and avoid synchronization.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The following are examples of the present invention, however, the present invention is not limited to the examples.
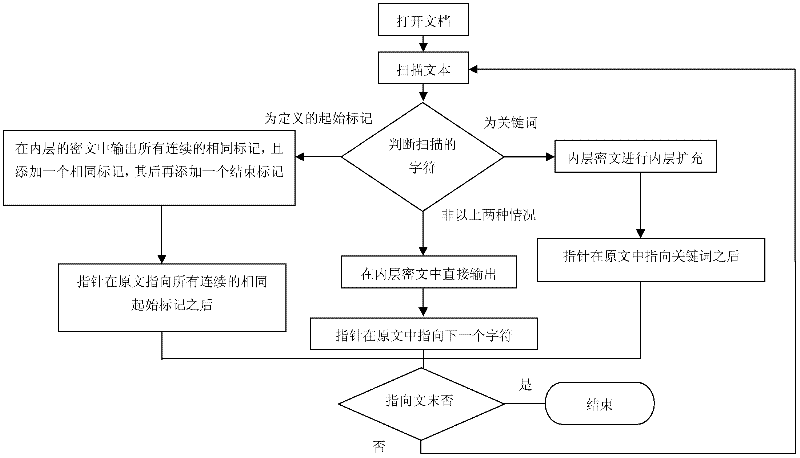
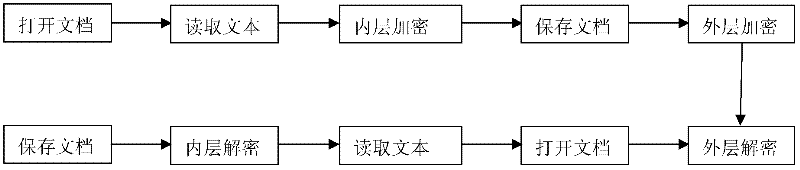
[0033] In the actual implementation, it is stipulated that different parts of the total key are used for inner and outer encryption respectively, and the outer key is a fixed length, which is determined according to the algorithm used in the outer encryption. For example, the outer encryption algorithm adopts 256-bit AES encryption. The first 256 bits of the key are outer keys, and the rest are inner keys. The inner key is intercepted with equal length. The interception length is determined according to the number N of keywords in the same group of keywords in the keyword database. The value should be greater than or equal to log 2 N.
[0034] Before encryption, the two parties share a random key sequence in a way such as QKD. The file encryption process is as follows:
[0035] 1) During the encryption process, according to the type of the file, use c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com