DoS (Denial of Service) attack defense method based on identity and location separation-and-mapping mechanism
A mapping mechanism and identity technology, applied in the field of network security, can solve the problems that StopIt cannot provide, the terminal cannot provide permission or denial capability, and the integration of StopIt and identity and location separation network system is poor.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
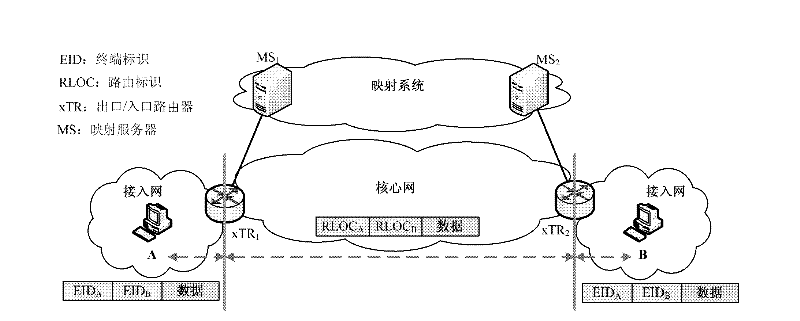
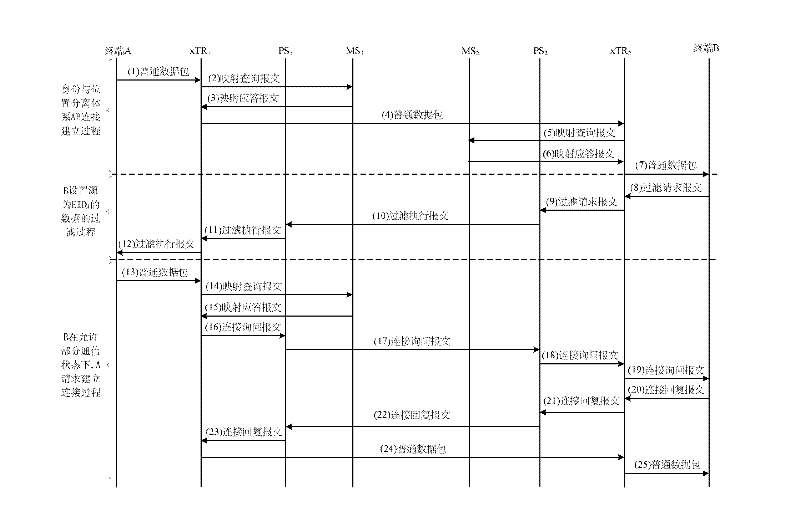
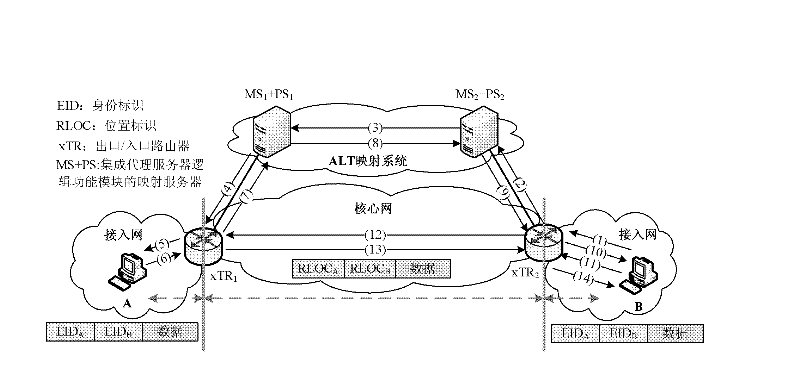
[0055] In recent years, the number of Internet users has become unprecedentedly large. Various services are carried out on the Internet, including mobility, multi-home, and traffic engineering (Traffic Engineering), which causes a huge increase in the scale of the global routing table and instability. The Internet Architecture Board (IAB) revealed that Internet routing systems face serious scalability problems. With the exhaustion of IPv4 addresses and the gradual application of IPv6, the huge address space of IPv6 may exceed the processing capacity of the routing table, affecting the normal operation of the Internet.
[0056] Therefore, the IAB commissioned the Routing Research Group (RRG) of the Internet Research Task Force (IRTF) to design a new network system to solve the problem of routing scalability. At present, researchers have proposed a variety of network architecture solutions to solve the problem of routing scalability.
[0057] In traditional networks, IP addres...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com