Method, client and system for software access control
An access control and client-side technology, applied in transmission systems, electrical components, instruments, etc., can solve the problems of inability to use, inconvenient to use, and increase the user's burden, so as to achieve the effect of copyright protection and convenient use.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
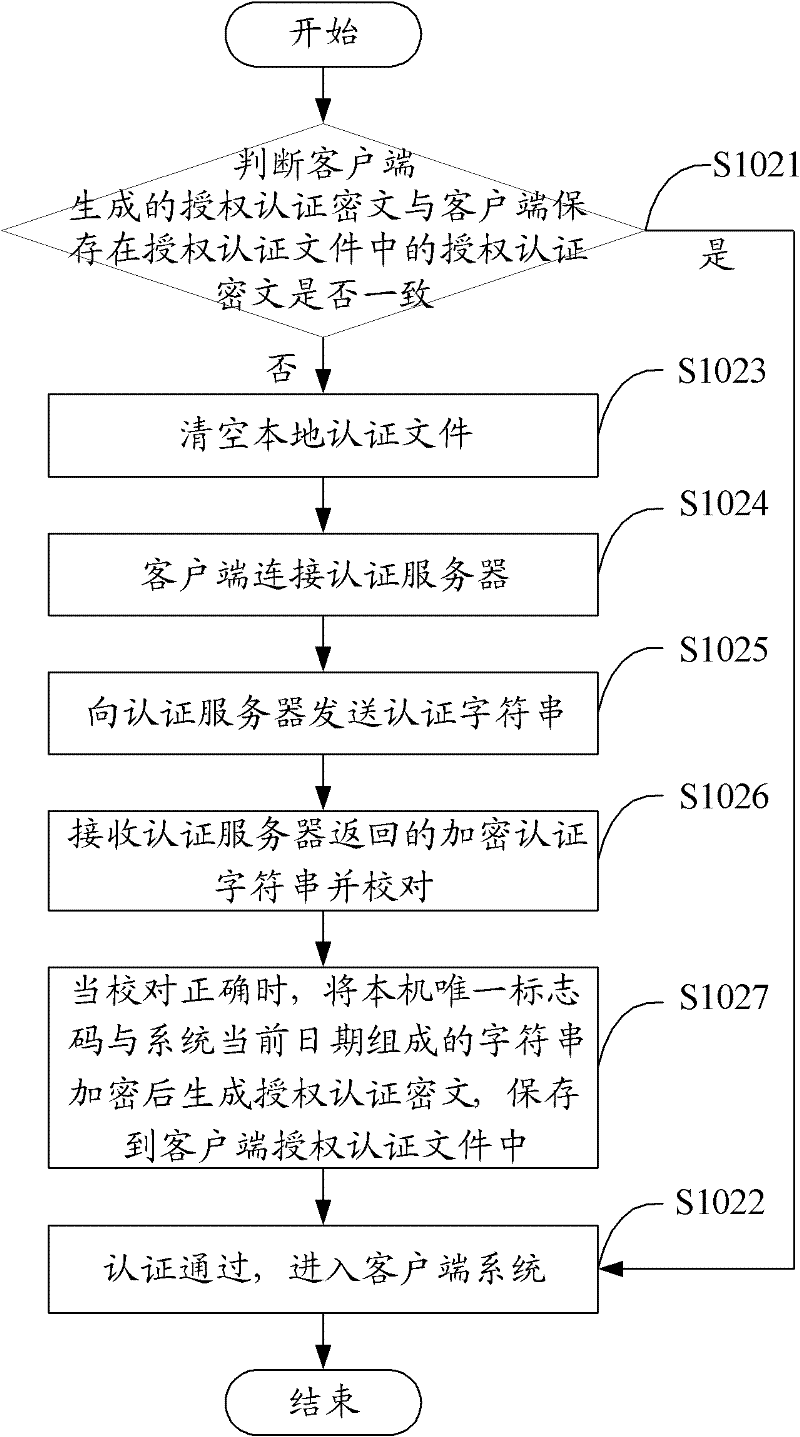
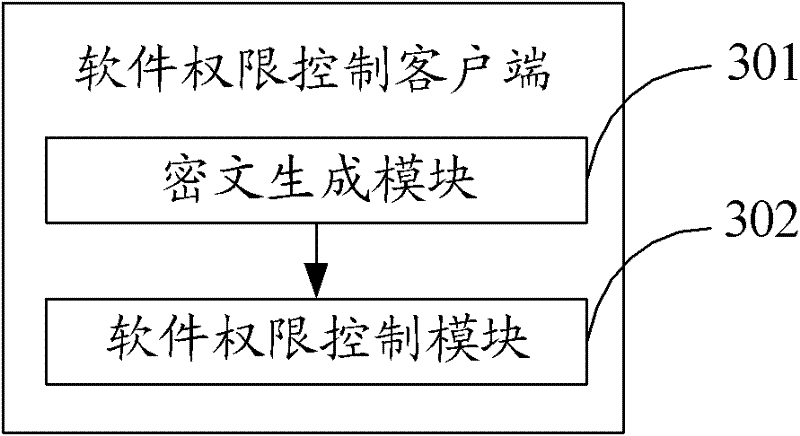
[0045] The solution of the embodiment of the present invention is mainly to combine the two authentication methods of online authentication and offline authentication, so as to improve the safety of software use and facilitate the use of authorized users.
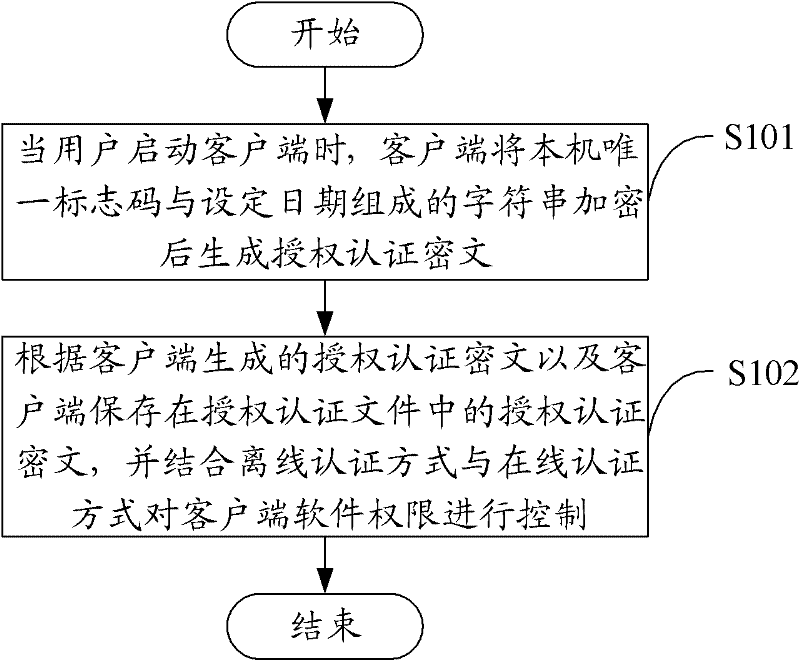
[0046] Such as figure 1 As shown, an embodiment of the present invention proposes a software permission control method, including:
[0047] Step S101, when the user starts the client, the client encrypts the string composed of the unique identification code of the machine and the set date to generate an authorization authentication ciphertext;
[0048] Wherein, the set date is generated according to the current date of the system and preset rules, wherein, the preset rule is set according to the valid authentication period after the client software is successfully authenticated in advance, and the set date can be the current date of the system or the current date of the system. The current date minus the interval between a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com