Method for preventing fragment attack of IP (Internet Protocol) datagram
An IP datagram and message technology, applied in electrical components, transmission systems, etc., can solve problems such as error datagrams, fragmented message attacks of IP datagrams, and the system cannot handle them, and achieve the effect of preventing fragmentation attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
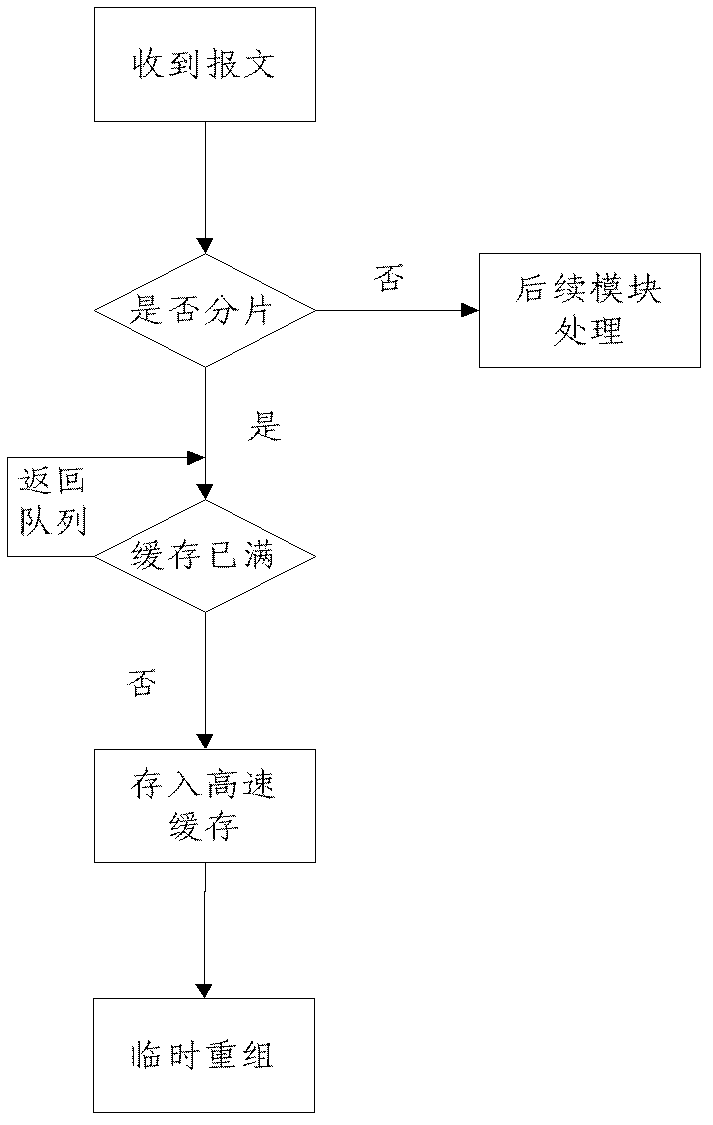
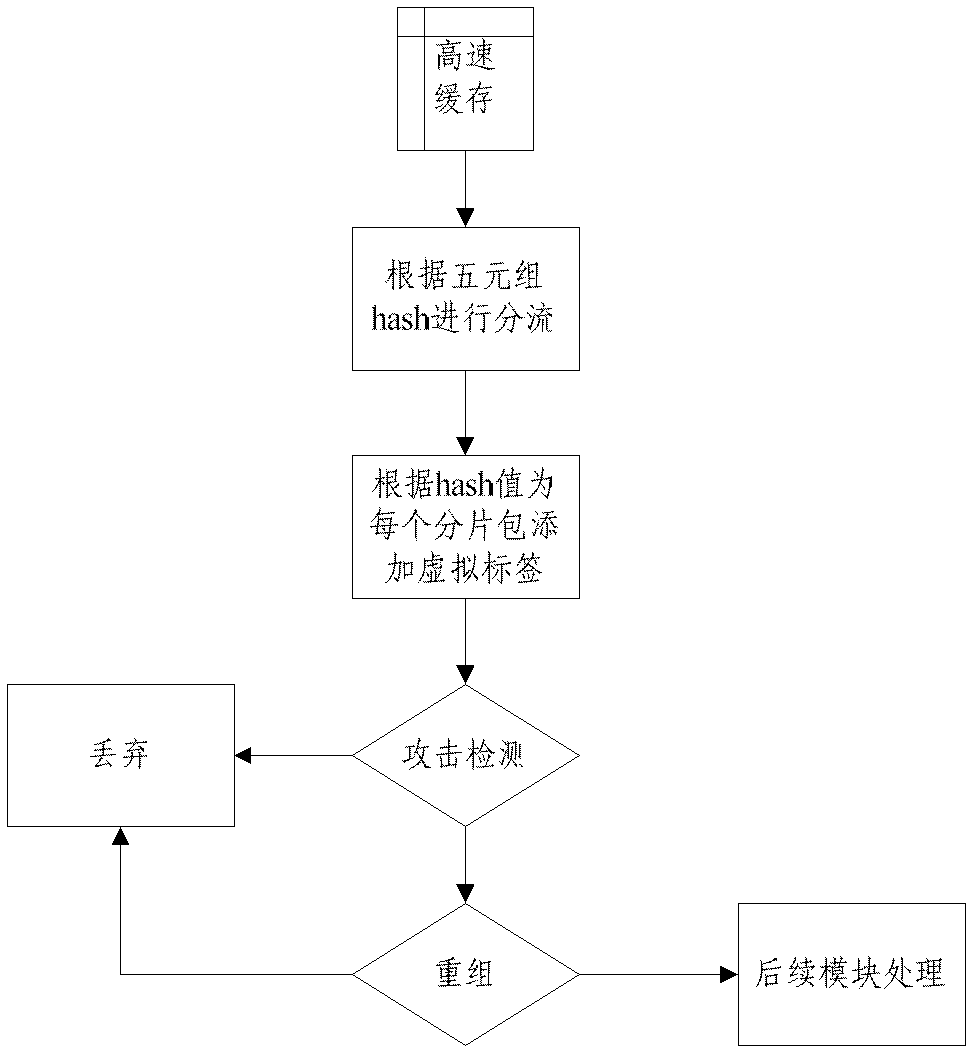
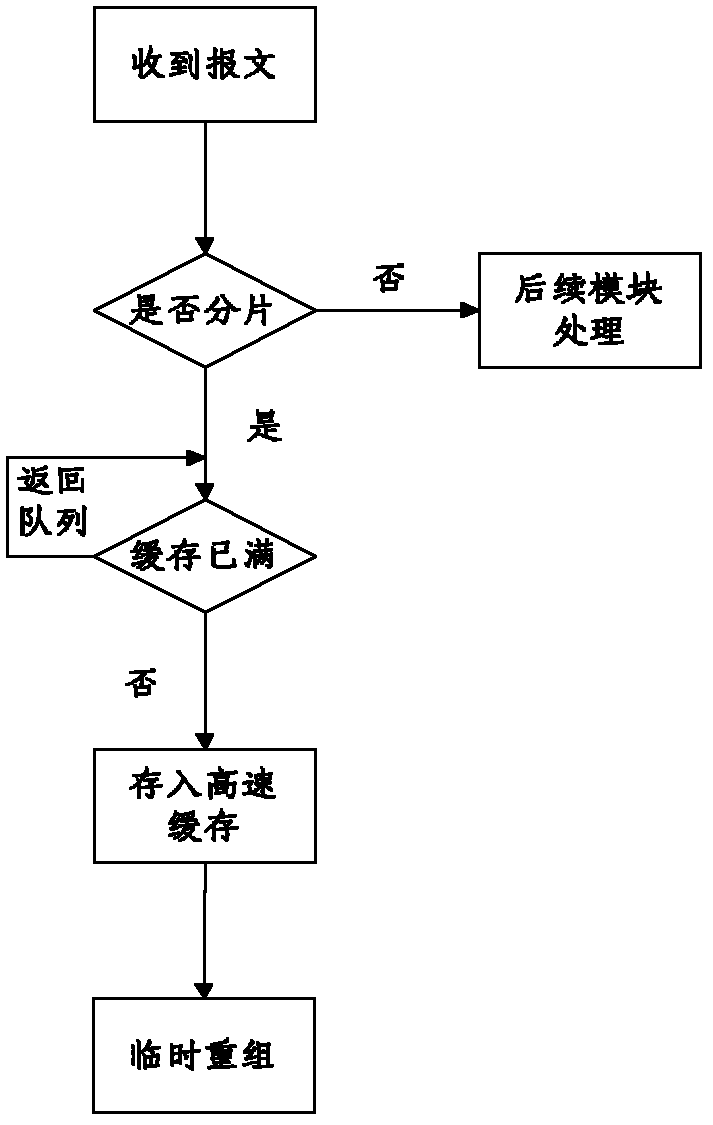
[0026] The specific embodiments of the present invention will be described in further detail below in conjunction with the drawings and embodiments. The following examples are used to illustrate the present invention, but not to limit the scope of the present invention.
[0027] In this embodiment, the firewall executes the method of the present invention as an example. In order to avoid the firewall (similar to other network devices), each service module (address translation, access control, data encryption and decryption) separately processes fragmented packets of IP datagrams. This situation leads to high complexity. The firewall temporarily reorganizes the received fragmented packets (that is, before the firewall interface receives the fragmented packet and submits it to the subsequent upper-layer business module for reorganization, each interface is defined The fragmented message is reorganized in the buffer space). During the temporary reorganization process, the fragmente...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com