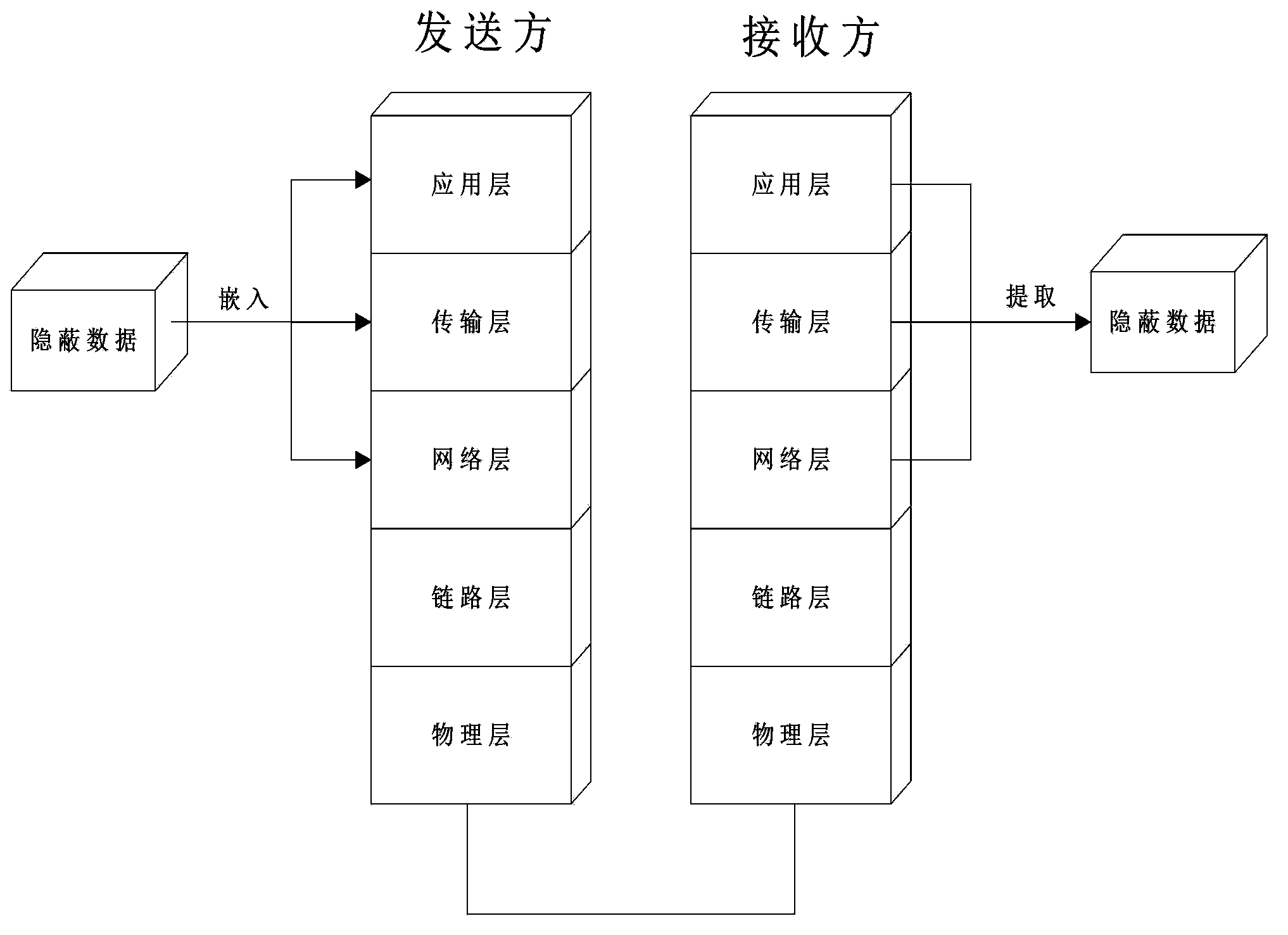
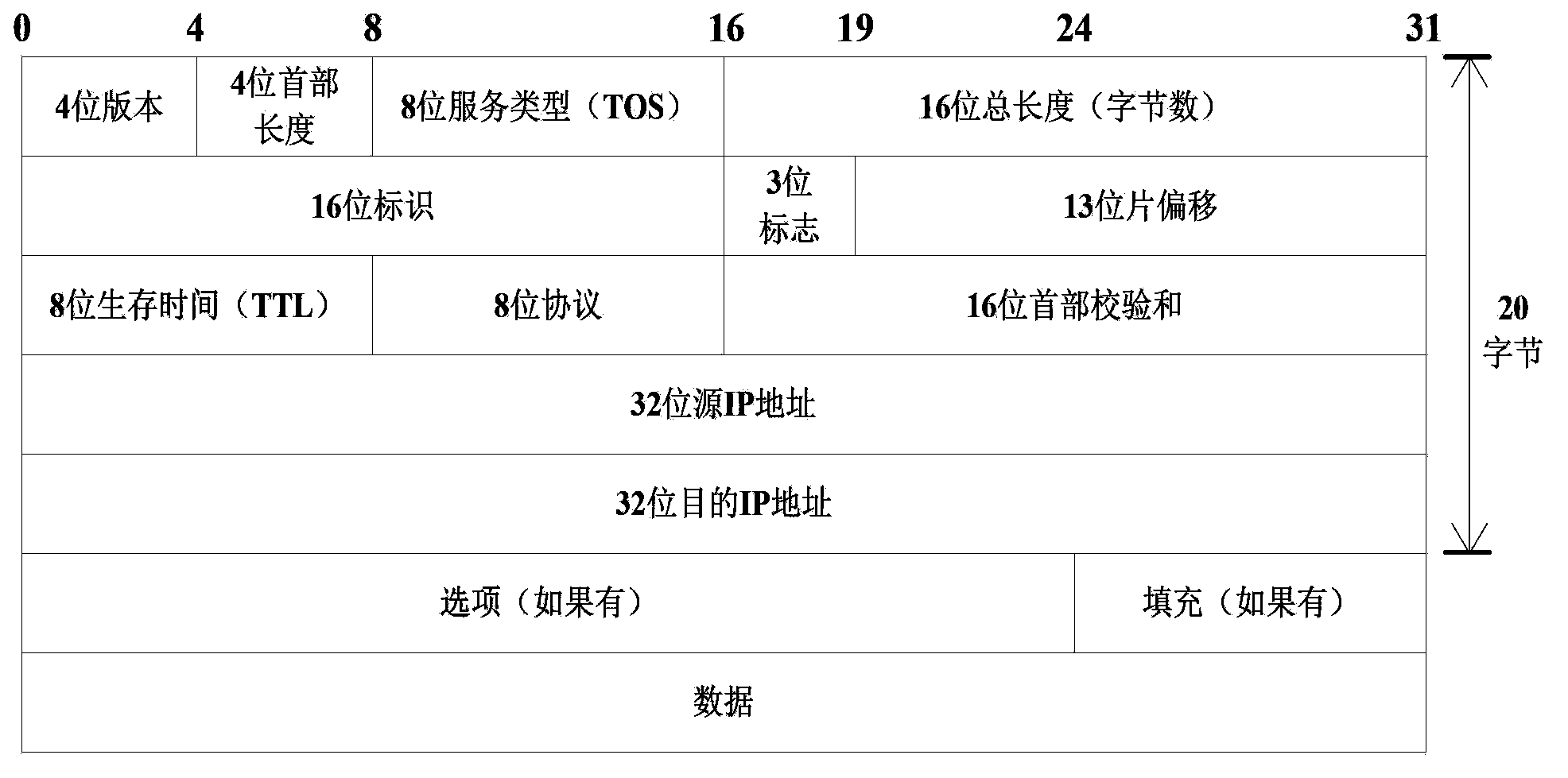
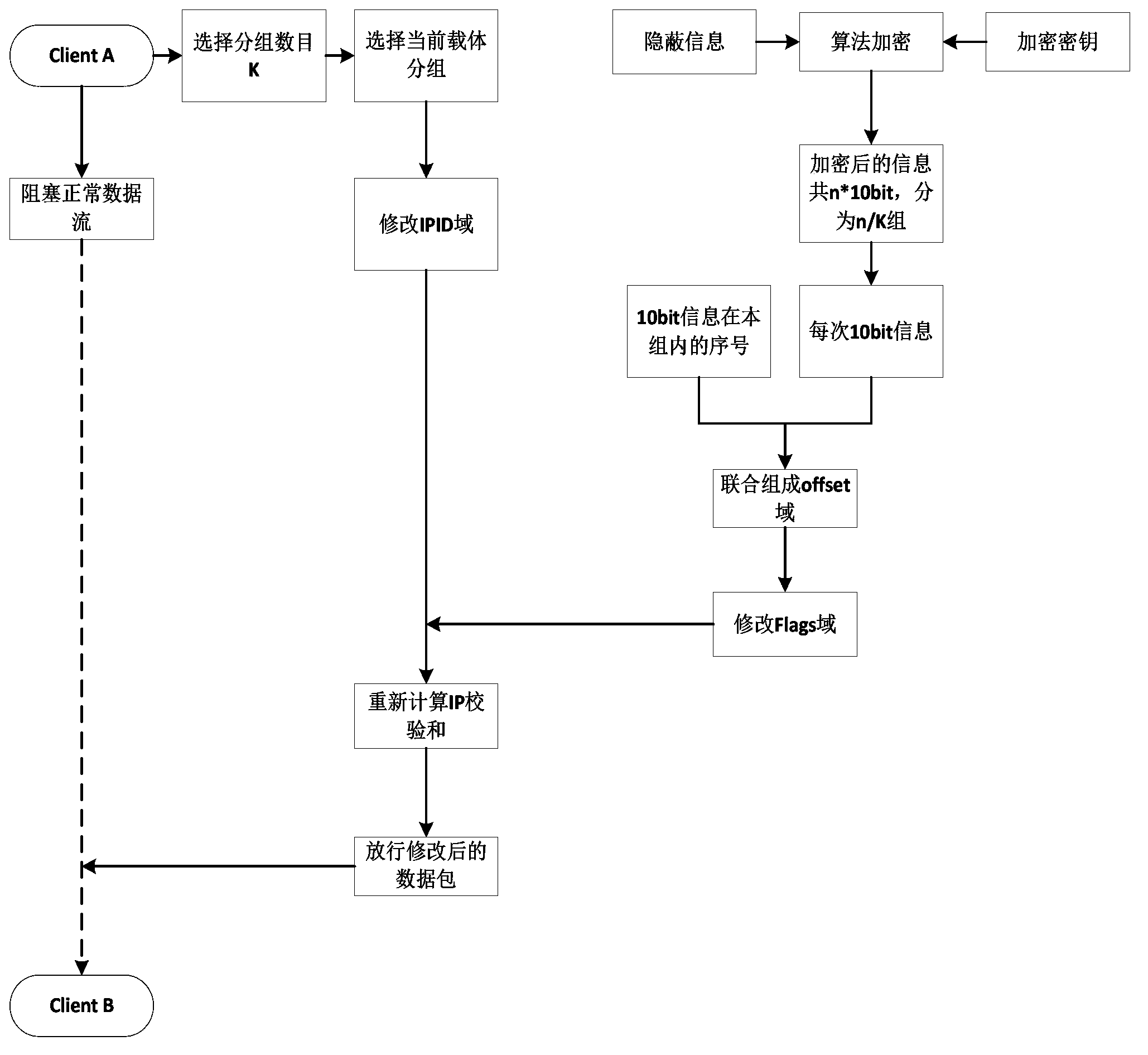
Hidden information communication method based on IP fragmentation camouflage technology
A technology for covert information and communication methods, applied in encryption devices with shift registers/memory, electrical components, transmission systems, etc., can solve the problems of unreliable and low security of covert communication, improve the embedding rate and ensure transmission. Quality, the effect of improving concealment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0042] 1. Communication of hidden information
[0043] In this embodiment, it is assumed that the original hidden information has been encrypted into a bitstream file, and the value of u is 10.
[0044] (1) The transmission process of the hidden information embedded in the sender
[0045] Such as image 3 As shown, the basic process of embedded transmission of hidden information at the sender is:
[0046] Step 1: At the beginning of sending, the sender selects the number of bit packets K to be sent this time, that is, the number of fragmented packets identified in the same IPID domain K (the maximum requirement is 8).
[0047] Step 2: After the above stage ends, the sender first sends a synchronization packet to the receiver to indicate the beginning of the transmission of concealed information. The specific method is: embed the number of fragments K in step 1 into the upper 3 bits of the Offset field, and do the remaining 10 bits specify the format or content of the flag information? ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com