RFID-based confidential carrier intelligent monitoring system and monitoring method of the same
A secret-related carrier and secret-related technology, applied in the field of information security, can solve the problem of failure to grasp the core and essence of "civil defense" thinking, methods and strategies of "civil defense" that have not kept pace with the times, and physical carriers of secret-related information that cannot be carried out individually. monitoring and other issues to achieve the effect of enhancing reliability and safety and improving work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
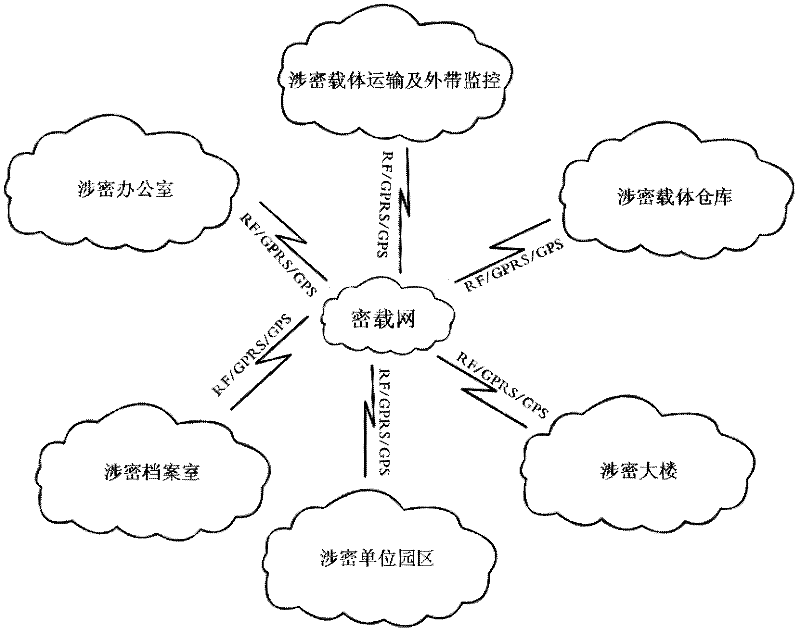
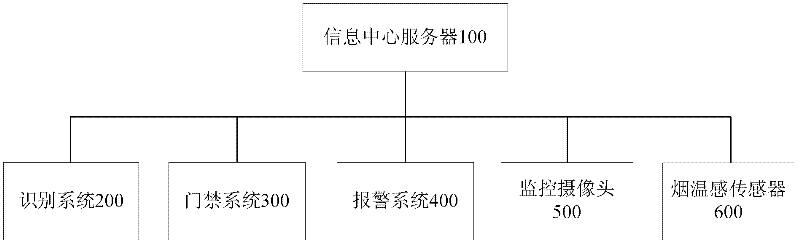
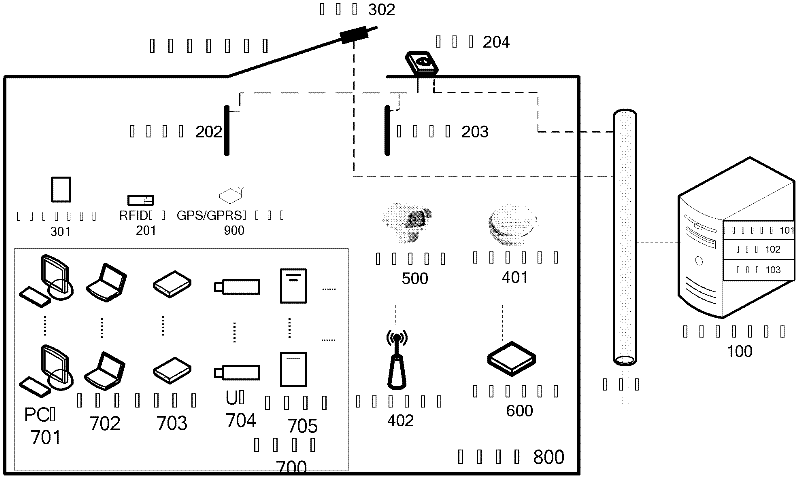
[0042] like figure 1 As shown, as a carrier of secret-related carrier information and applications, the secret network physically covers secret-related offices, secret-related archives, secret-related carrier warehouses, secret-related buildings, secret-related unit parks, and secret-related carrier transportation and external areas. The area along the way logically carries the intelligent monitoring system of secret-related carriers, including the monitoring system of secret-related offices, the monitoring system of secret-related archives, the monitoring system of secret-related buildings, the monitoring system of parks of secret-related units, the monitoring system of secret-related carrier warehouses and The application system provided around the security monitoring requirements of secret-related carriers, such as the transportation of secret-related carriers and the take-out monitoring system, realizes the procurement, distribution, transportation, warehousing, access, tak...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com