Method and system for protecting account, preventing order from being tampered and preventing fishing attack based on graphical two-dimensional code
A phishing attack and two-dimensional code technology, which is applied in the field of network communication, can solve the problems of easy phishing attack, phishing, tampering, etc., and achieve the effect of strong practical value, strong practical significance, and improved network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
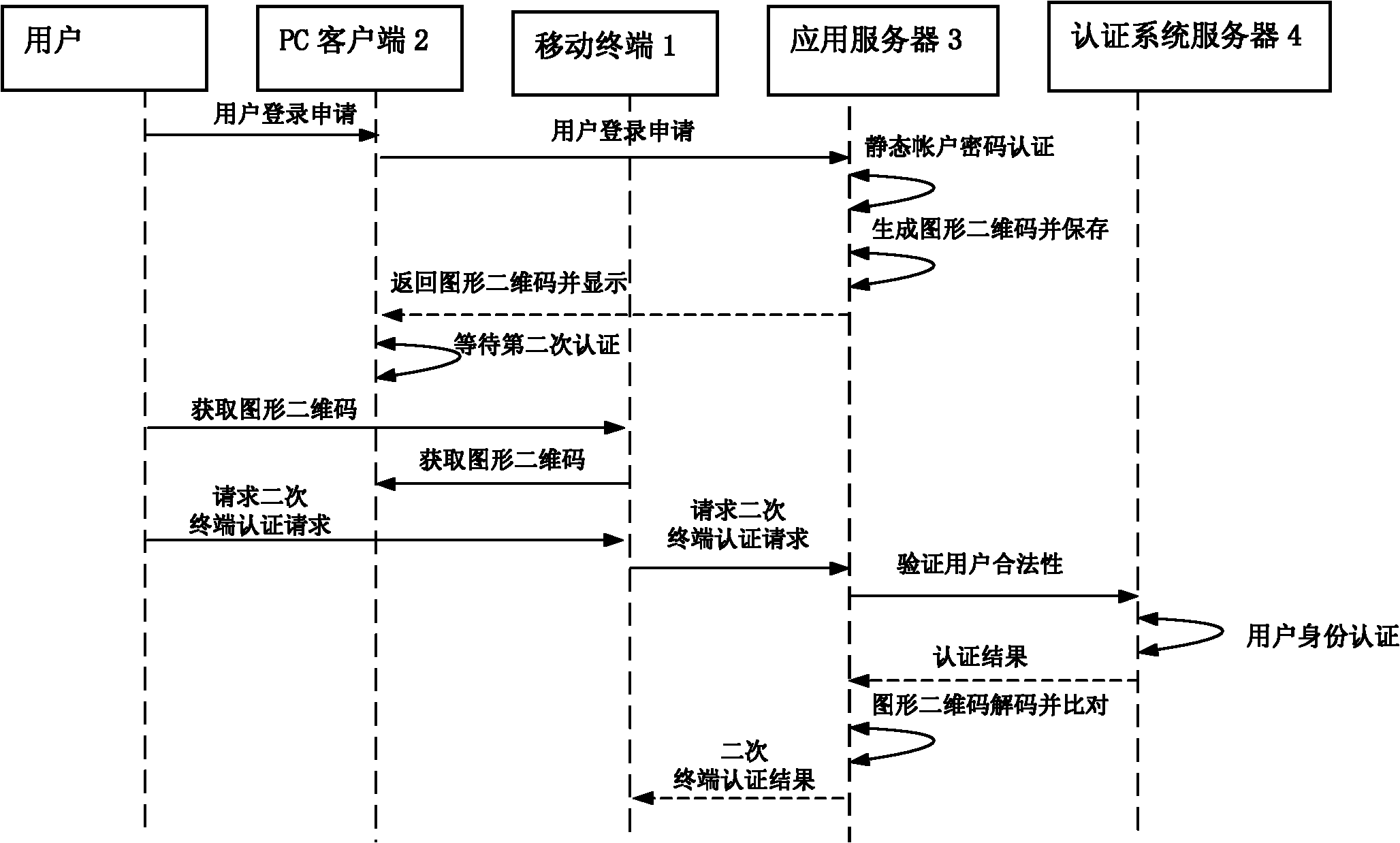
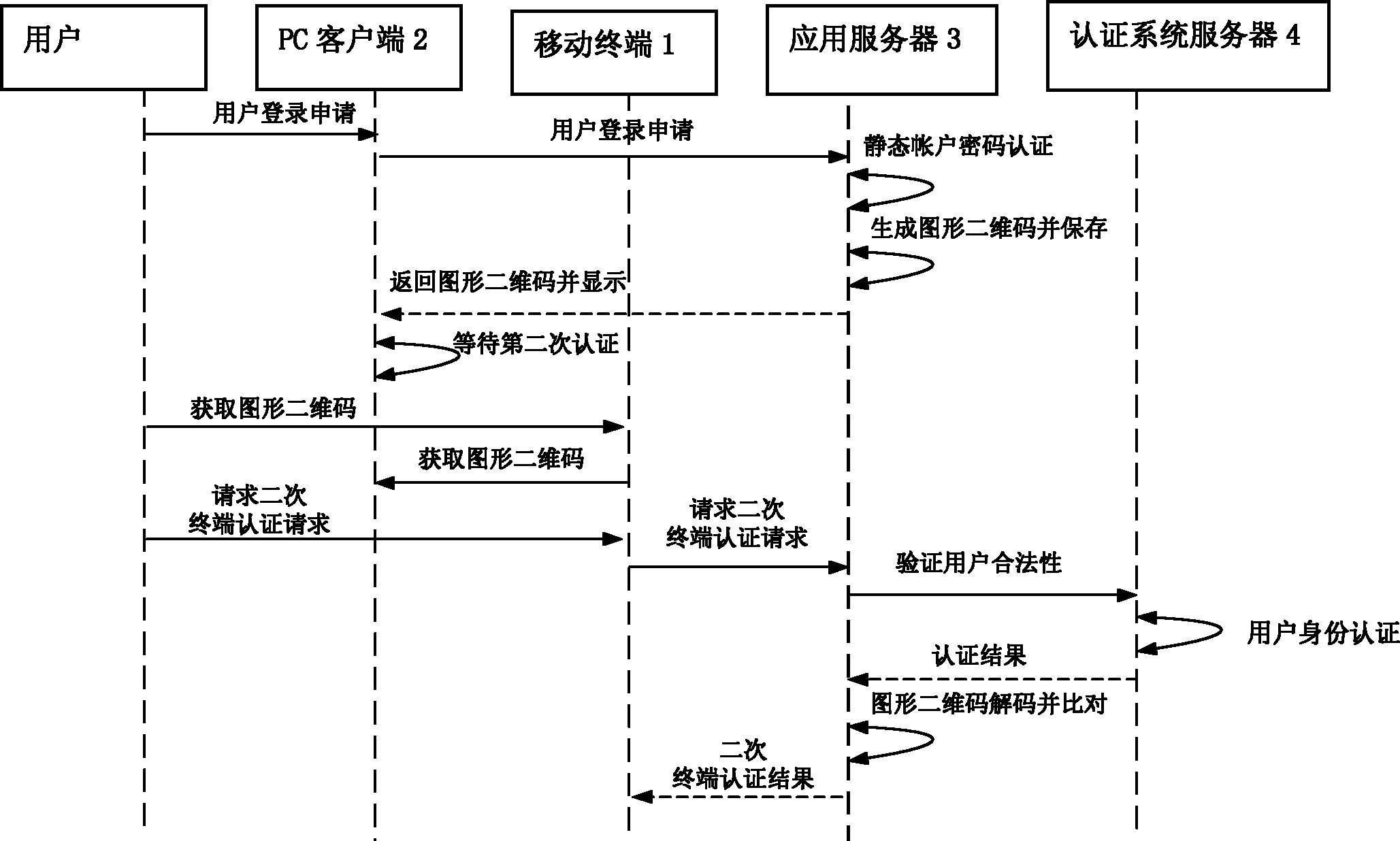
[0031] The present invention will be described in detail below in conjunction with the accompanying drawings and embodiments. The working principle of a method for protecting accounts based on graphic two-dimensional codes and preventing order tampering and phishing attacks in the present invention is as follows: figure 1 as shown,
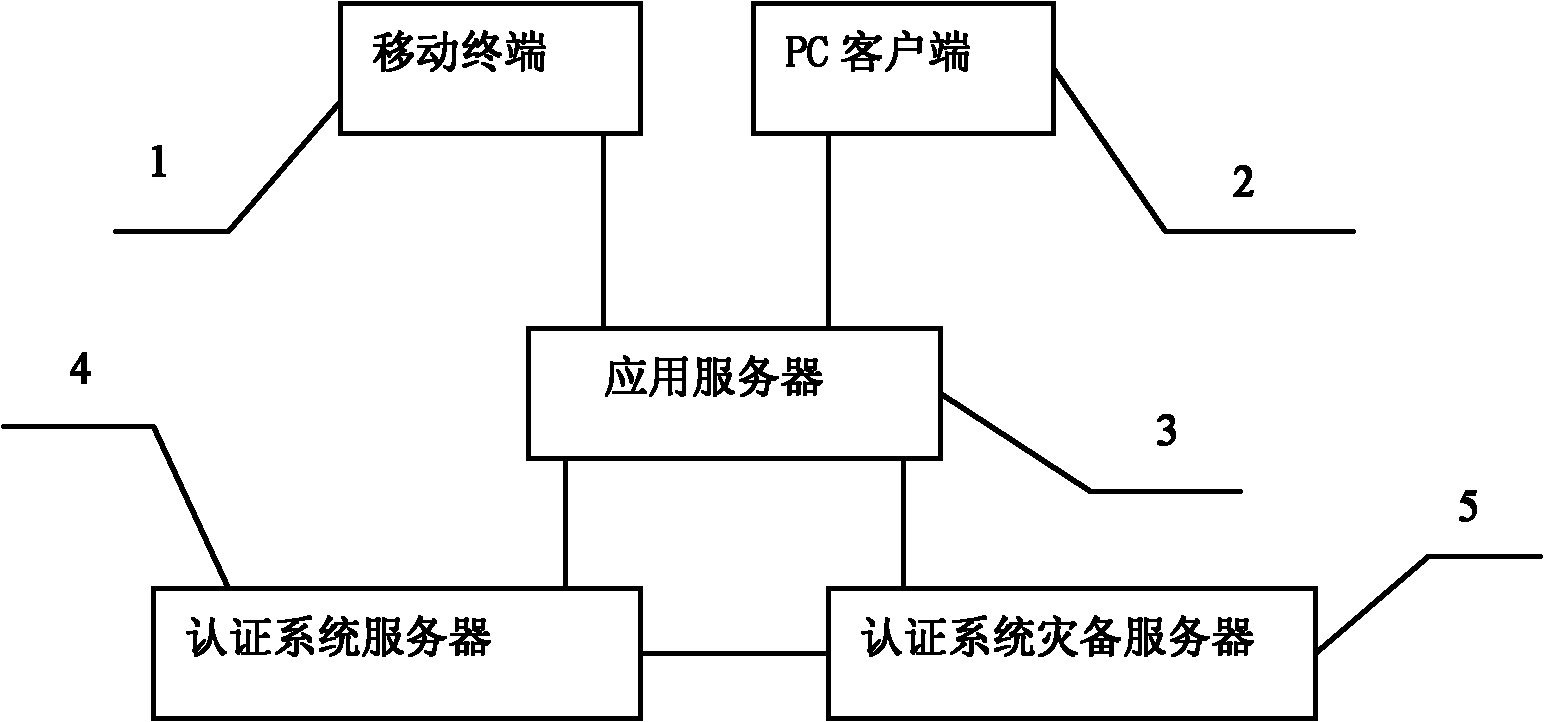
[0032] The PC client 2 accesses the application server 3 through a browser, and has a container for displaying a graphic two-dimensional code;
[0033] The application server 3 can distribute static account numbers, graphic two-dimensional code algorithm generation and decoders;
[0034] The authentication system server 4 provides support services for the account bound to the application server 3 based on the client of the mobile terminal 1, and it can distribute unique identifiers and perform identity authentication for accounts registered on the application server 3;
[0035] The client installed on the mobile terminal 1 can obtain the graphic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com