Chaos message authentication code realization method for wireless sensor network
A technology of message authentication codes and wireless sensors, applied in transmission systems, digital transmission systems, user identity/authority verification, etc., can solve problems such as low efficiency and poor security, and achieve broad application fields, enhanced security, and easy implementation Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The present invention will be further described below in conjunction with the accompanying drawings.
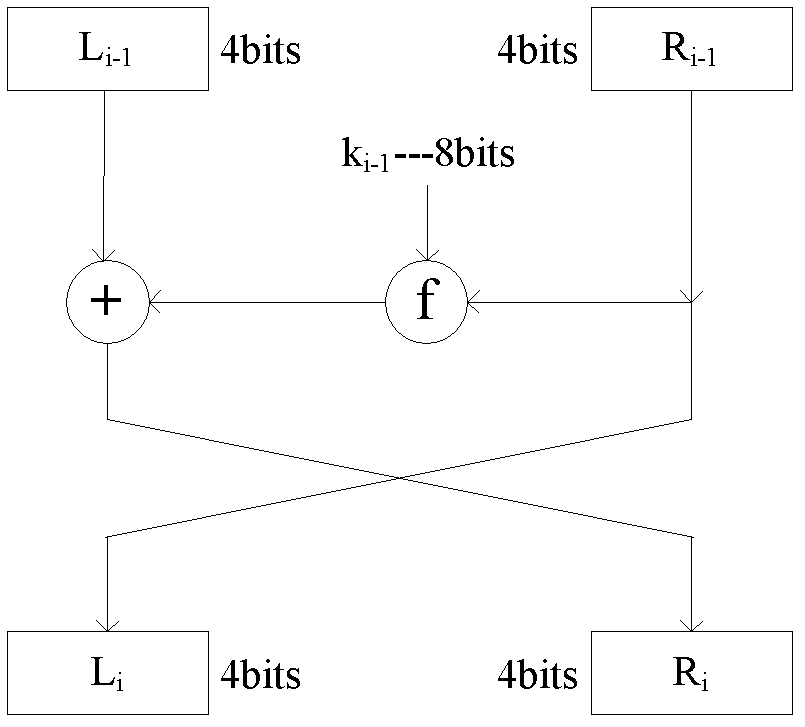
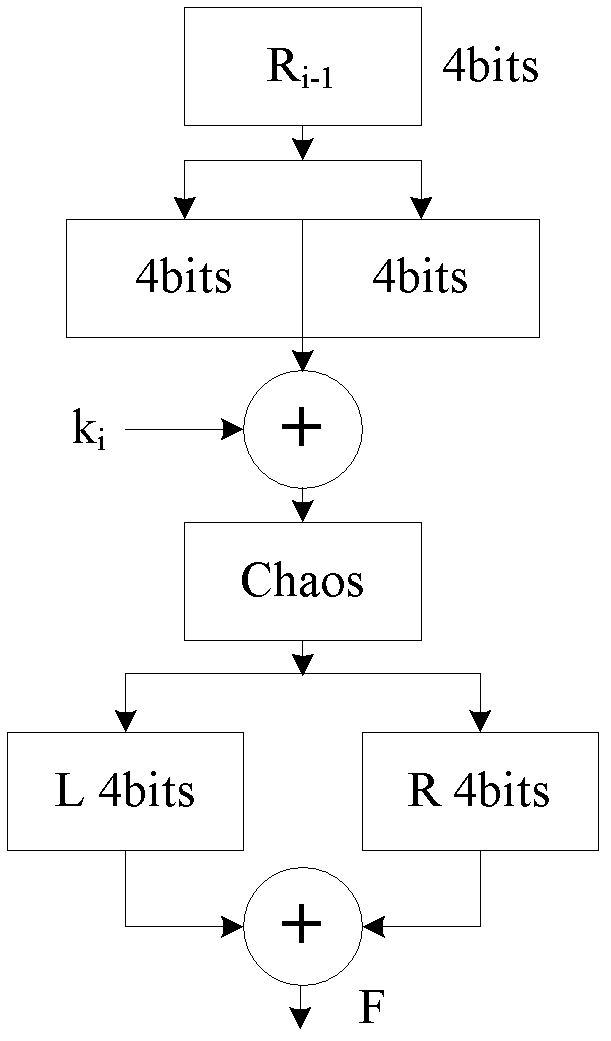
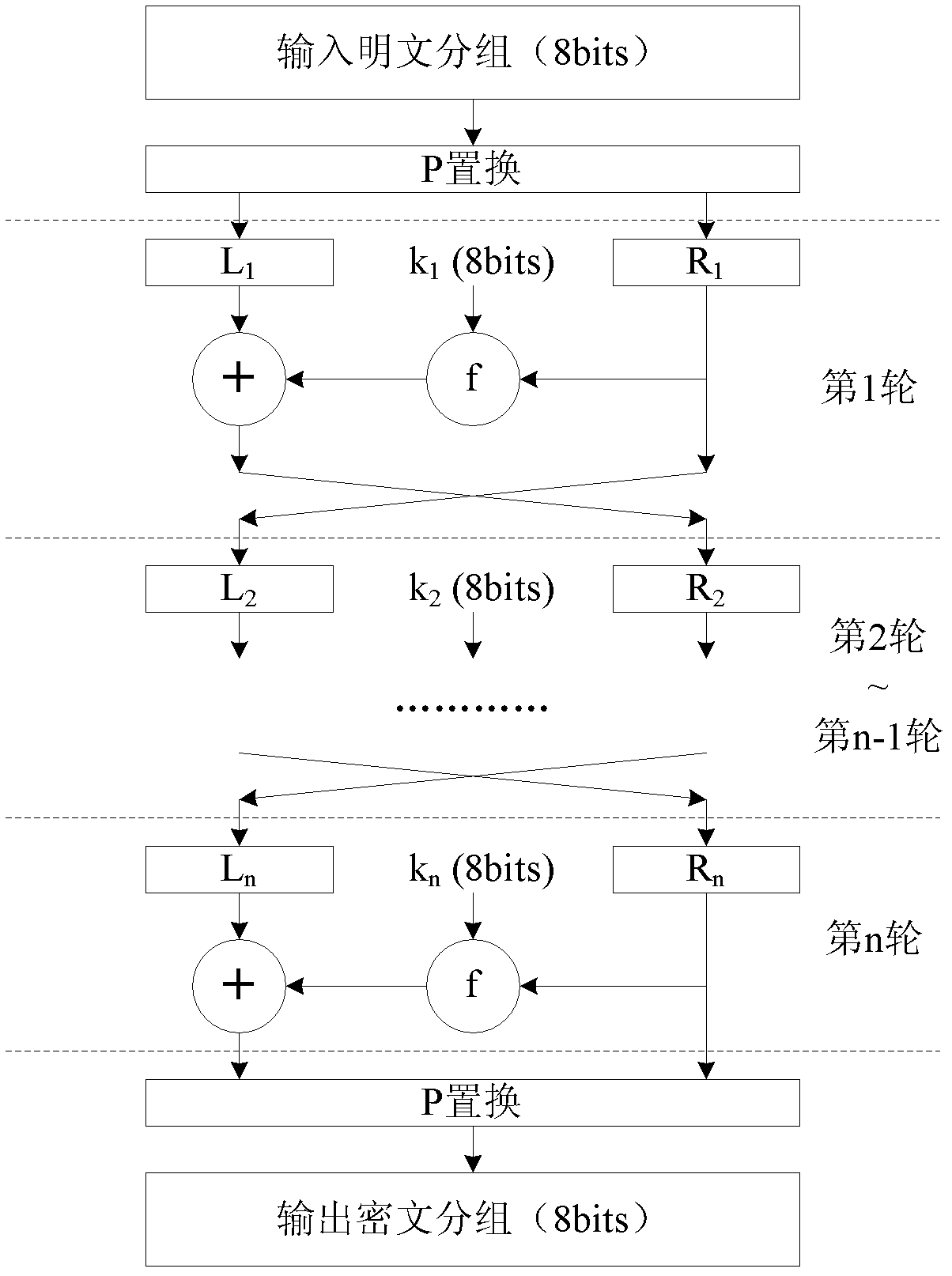
[0040] refer to Figure 1 to Figure 8 , a chaotic message authentication code implementation method for wireless sensor networks, the chaotic message authentication code implementation method includes the following steps:
[0041] 1) First, the Logistic chaotic mapping function based on integer calculation is used for wireless sensor nodes. The iterative formula of the Logistic chaotic mapping function is:
[0042] z n + 1 = z n 2 - z n 2 > > 6 - 1 - - - ( I - 10 )
[0043]Among them, z n =ax n +a, tak...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com