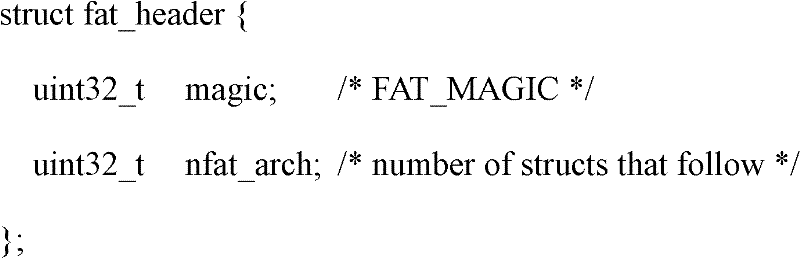Protecting method for packing executable program
A technology for executing programs and shell programs, applied in program/content distribution protection, platform integrity maintenance, instruments, etc., can solve the problems of easy software, cracking, illegal tampering, etc., to prevent disassembly cracking and illegal tampering, and increase security. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0031] This embodiment describes in detail the process of encrypting the acquired target file with reference to the accompanying drawings. The following takes the implementation method based on the Mac.OS platform as an example to describe the packing protection method proposed by the present invention in detail. The files mentioned in this embodiment appear with common file names in the Apple system.
[0032] When the acquired target file is a Flat format file, the liposuction program lipo is first run to separate the target file, and then the separated i386 or x64 file is encrypted.
[0033] The process of running lipo to separate the Flat file is specifically, judging the file type according to the file header of the Flat file, and separating the file to be separated from the specified position according to the structural information of the file to be separated contained in the Flat file header .
[0034] Specifically, the file header of the Flat file is defined as follows...
Embodiment 2
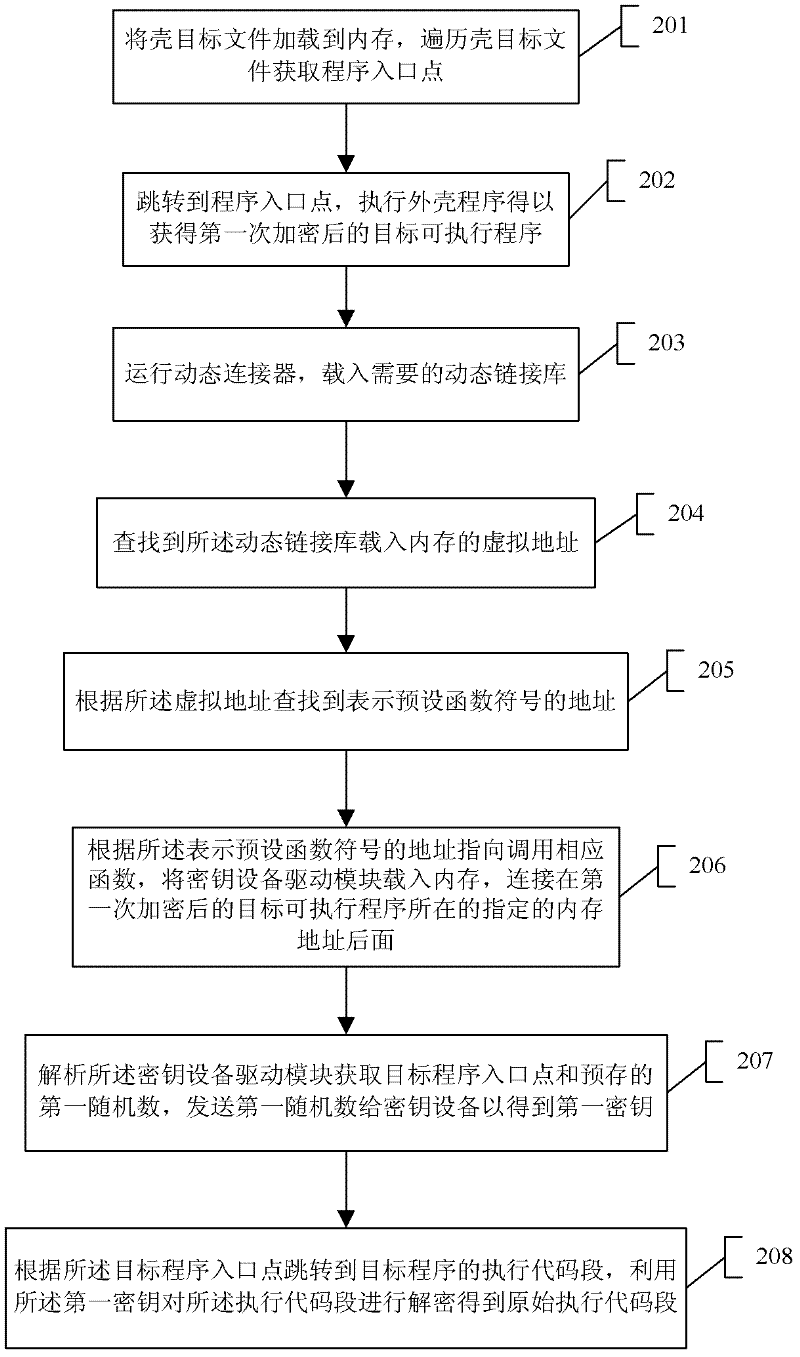
[0105] The process of executing the above shell target file includes the following steps:
[0106] Step 201: Load the shell object file into the memory, traverse the shell object file to obtain the program entry point;
[0107] Specifically, traverse the file header of the shell object file, find the thread state command LC_UNIXTHREAD, and obtain the entry address of the program entry point.
[0108] Step 202: Jump to the program entry point, execute the shell program;
[0109] Executing the shell program specifically includes obtaining a second key from the code segment of the shell program, and using the second key to decrypt the second encrypted shell program in the shell program to obtain a new first encrypted target Executable program file, releasing other contents of the code segment of the shell program; scanning the executable code segment of the target executable program file after the new encryption for the first time, and copying all command segments to the specified...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com