Link discovery technique based network intrusion prediction method
A network intrusion and contact discovery technology, applied in data exchange networks, transmission systems, digital transmission systems, etc., can solve problems such as the inability to quickly and accurately find key network base points with high intrusion risks, and the large amount of network data, so as to improve security. The effect of protection ability, small calculation amount and fast response speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
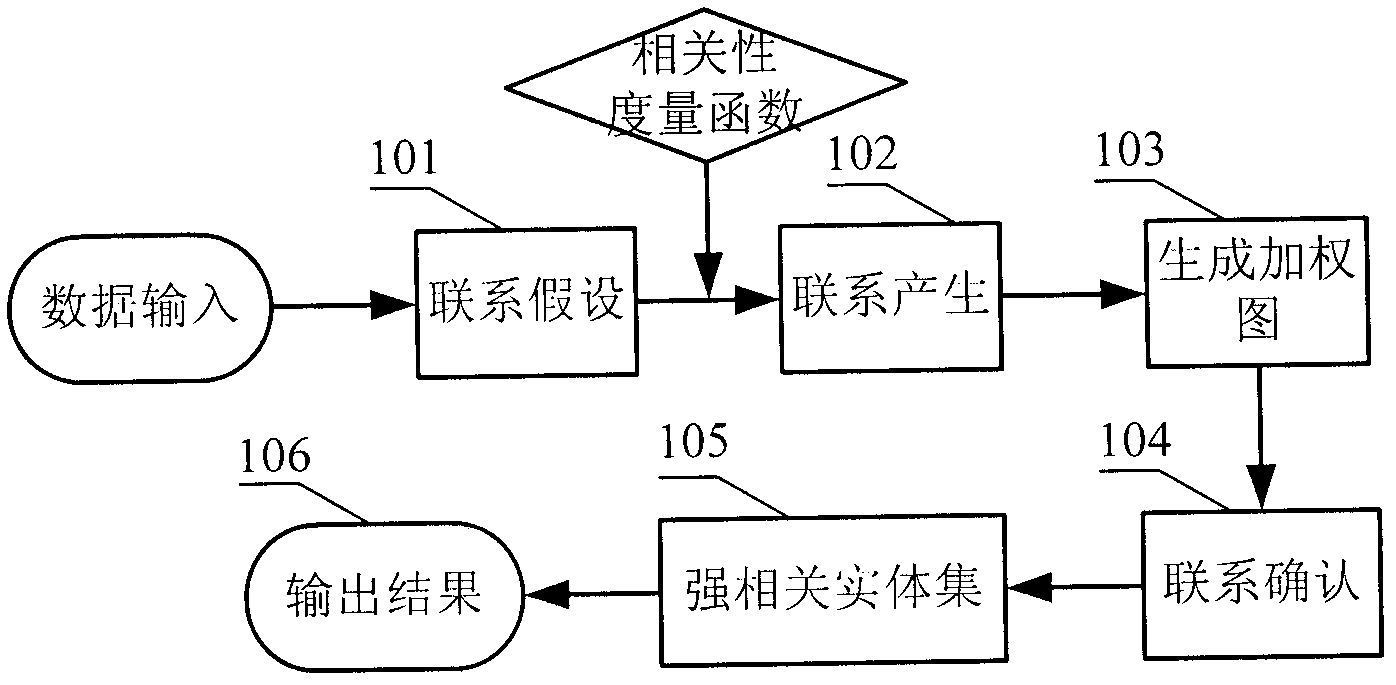
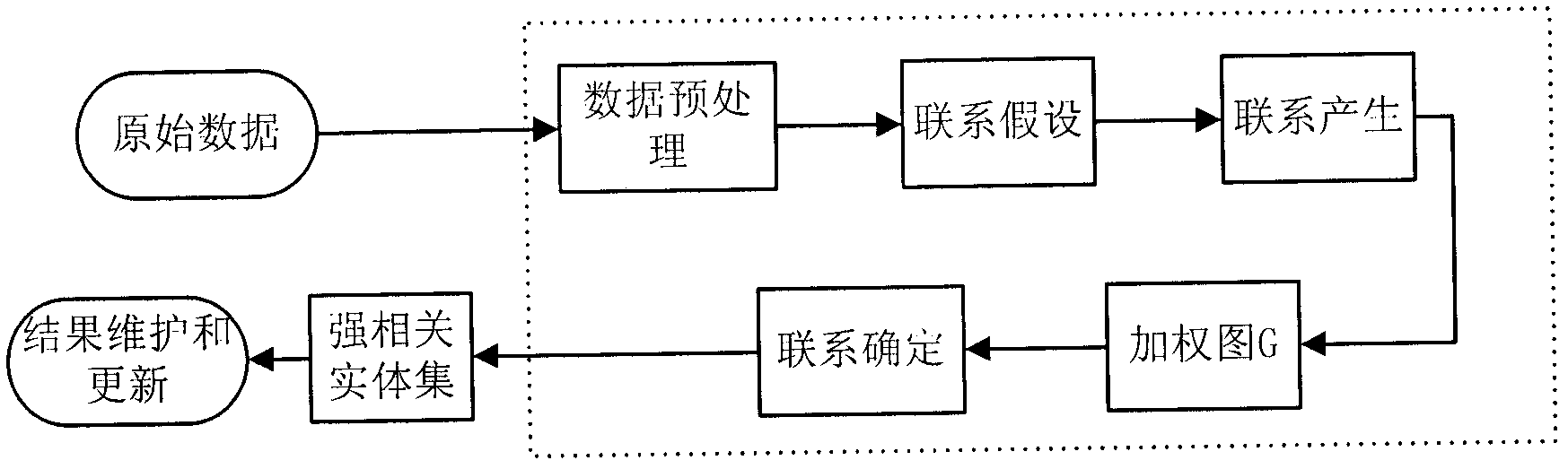
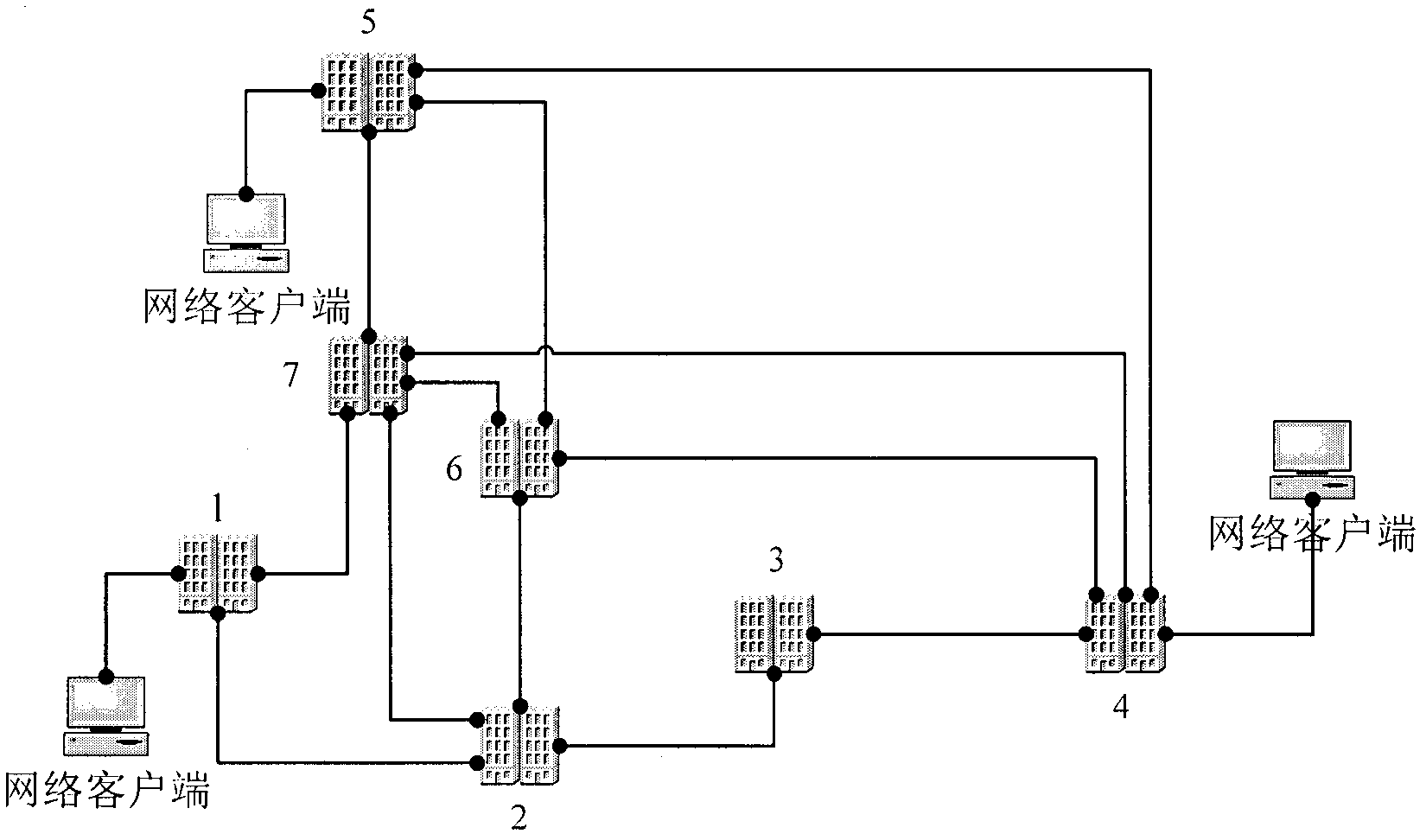
[0033] In order to make the objectives, technical solutions, and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings and preferred embodiments or implementations. It should be understood that the described specific embodiments or examples are only used to explain the present invention, and not to limit the present invention.
[0034] Several terms appearing in the present invention are given relevant definitions:
[0035] Entity: Represents any hardware or software process that can send or receive information in a computer. In this patent, it refers to a network object that contains one or more attributes. For example, the network base station described in the present invention is an entity, which contains IP addresses and more. Attributes.
[0036] Variable: Refers to the observable attributes of an entity.
[0037] In the embodiment of the present invention, N represents the number ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com