Safety management method for distributed SYSLOG (System Log) in network management system
A network management system and security management technology, applied in the field of network management system, can solve the problems of log server crash, low log performance, loss of SYSLOG log data, etc., to achieve the effect of improving performance and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
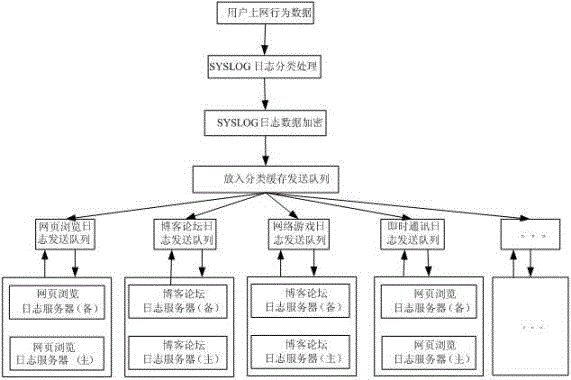
[0027] The distributed SYSLOG log security high-performance management method adopts a custom symmetric encryption algorithm to classify the SYSLOG log data according to the user's online behavior, such as web browsing, blog forum, online game, instant messaging, email, file transfer, remote login , Internet proxy, stock software, multimedia, P2P software, and according to different types of SYSLOG log data, first enter different types of cache queues, and send the SYSLOG log data in different types of cache queues to different types of log servers through sending threads. In this way, the distributed security high-performance management of the SYSLOG log is realized, so as to improve the performance of the log server for analyzing the log and improve the security of the log storage.
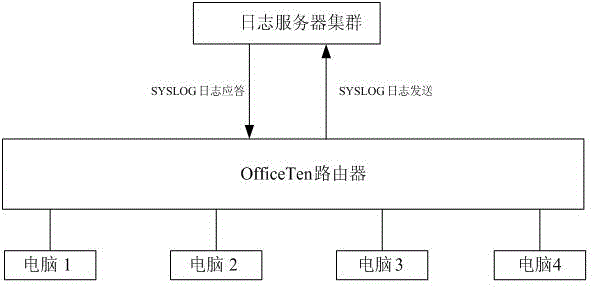
[0028] figure 1 Describes the overall example of OfficeTen routers processing SYSLOG log data. Personnel connect to OfficeTen routers on computers 1, 2, 3, and 4 through network cables, and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com