Application layer DDOS (distributed denial of service) attack and defense method
A distributed rejection, application layer technology, applied in transmission systems, electrical components, etc., can solve the problems of difficult operation, high cost, and high time and space complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The present invention will be further described below in conjunction with the drawings and embodiments.
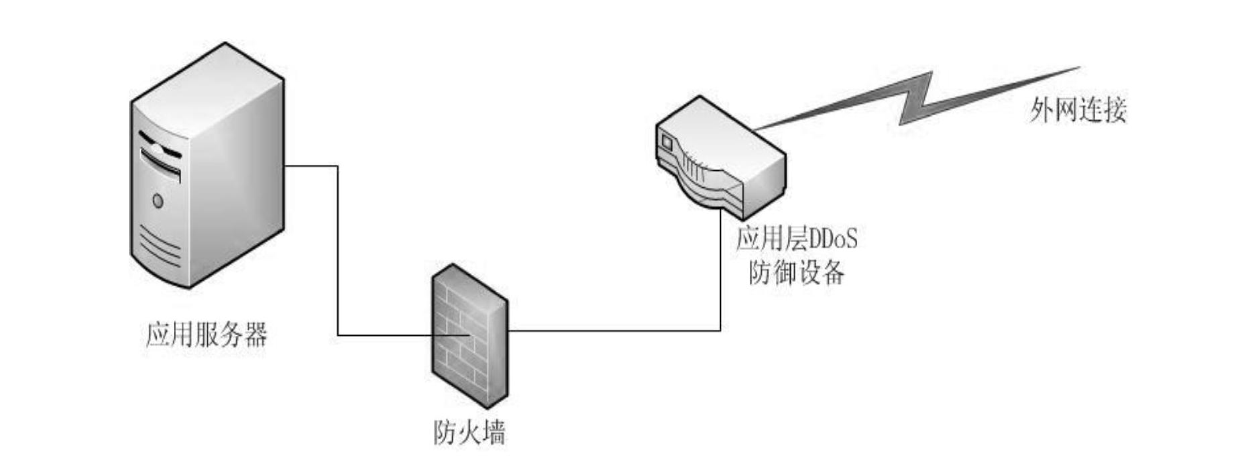
[0050] figure 2 , The application layer DDoS defense equipment is the equipment that adopts this method and is deployed at the intranet egress. Access traffic from the external network is first protected and filtered by the defense device, and then processed by the firewall or directly enters the application server.
[0051] This method can also be implemented directly in the firewall device and becomes a part of the firewall function.
[0052] The specific steps of the present invention are:
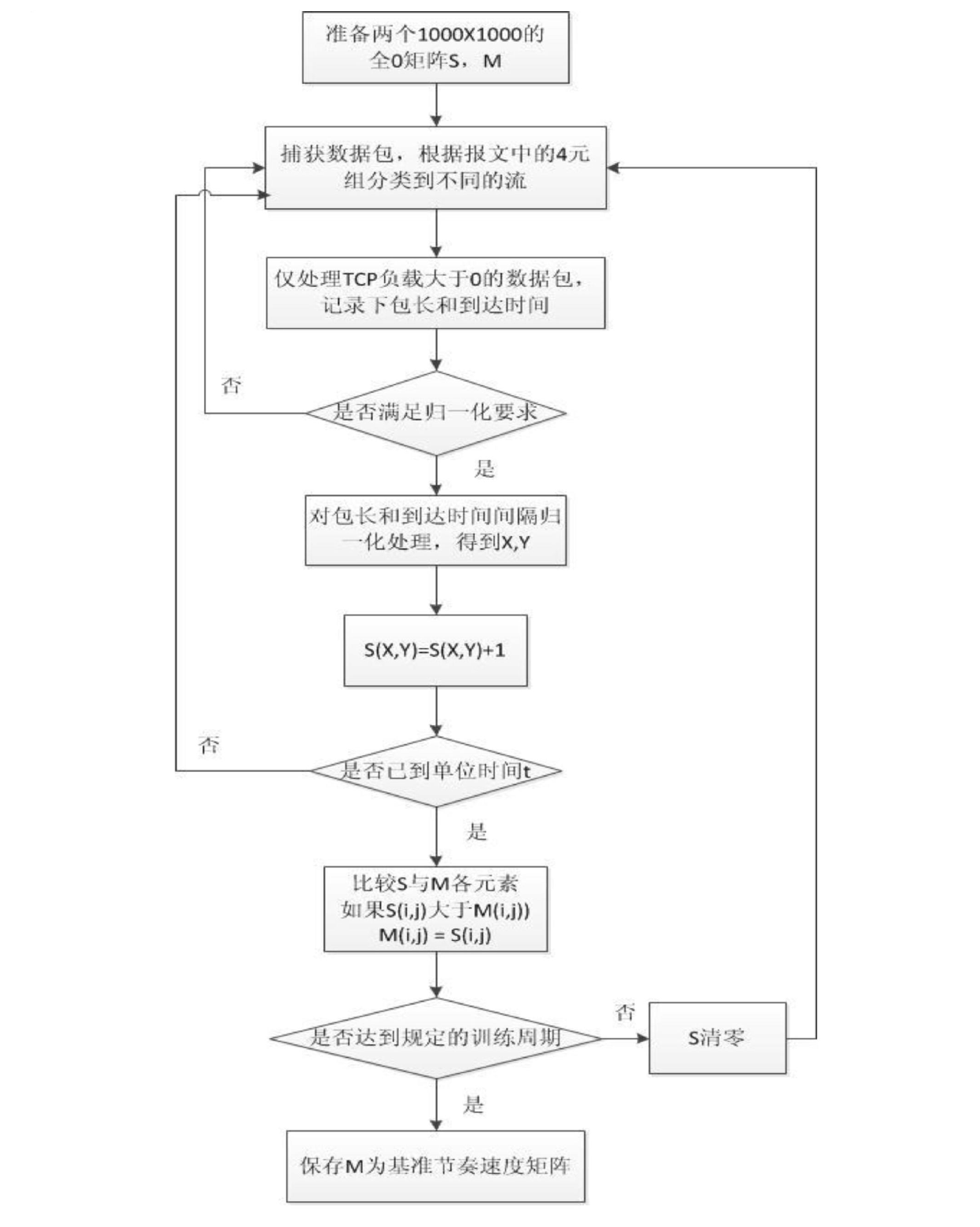
[0053] 1. Training phase
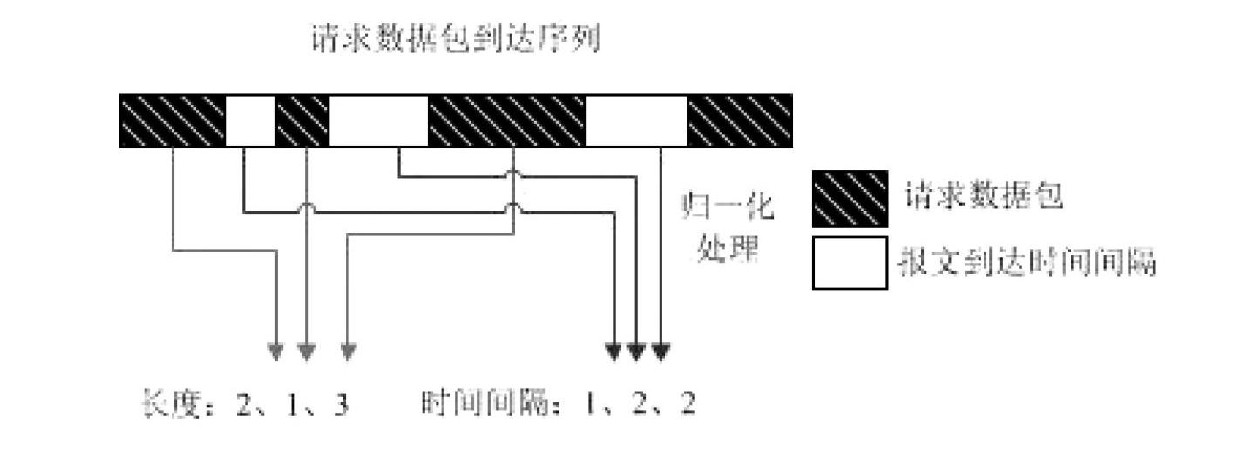
[0054] 1-1). Take the normal access traffic of the server during peak hours as training data, and only need the traffic from the client to the server. Prepare two 1000×1000 all-zero matrices S and M;
[0055] 1-2) When the incoming traffic arrives, classify the traffic according to the four-tuple (source / destination IP address, destination port, protocol nu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com