Behavior status switching mode identification method of application program for Android-based smart phone
An application program, smartphone technology, applied in special data processing applications, telephone communications, instruments, etc., can solve the problems of inability to effectively detect security risks, detection technology can not identify whether the application is infected with viruses, etc., to achieve the detection of security risks. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
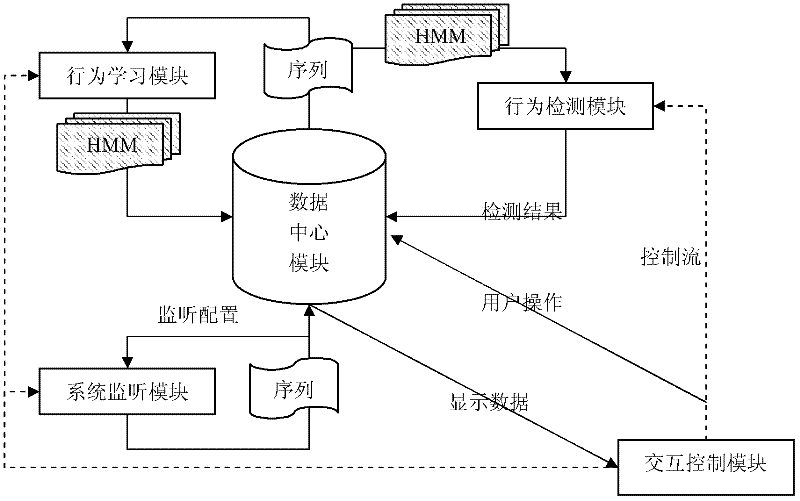
[0011] Specific implementation mode 1. Combination figure 1 Illustrate this embodiment, the application program behavior state conversion pattern recognition method based on Android smart phone, its concrete method is:
[0012] Step 1. According to the time interval, the system monitoring module intercepts the system state, filters and converts the intercepted information, and records the generated composite state sequence, and then sends the composite state sequence to the data center module;
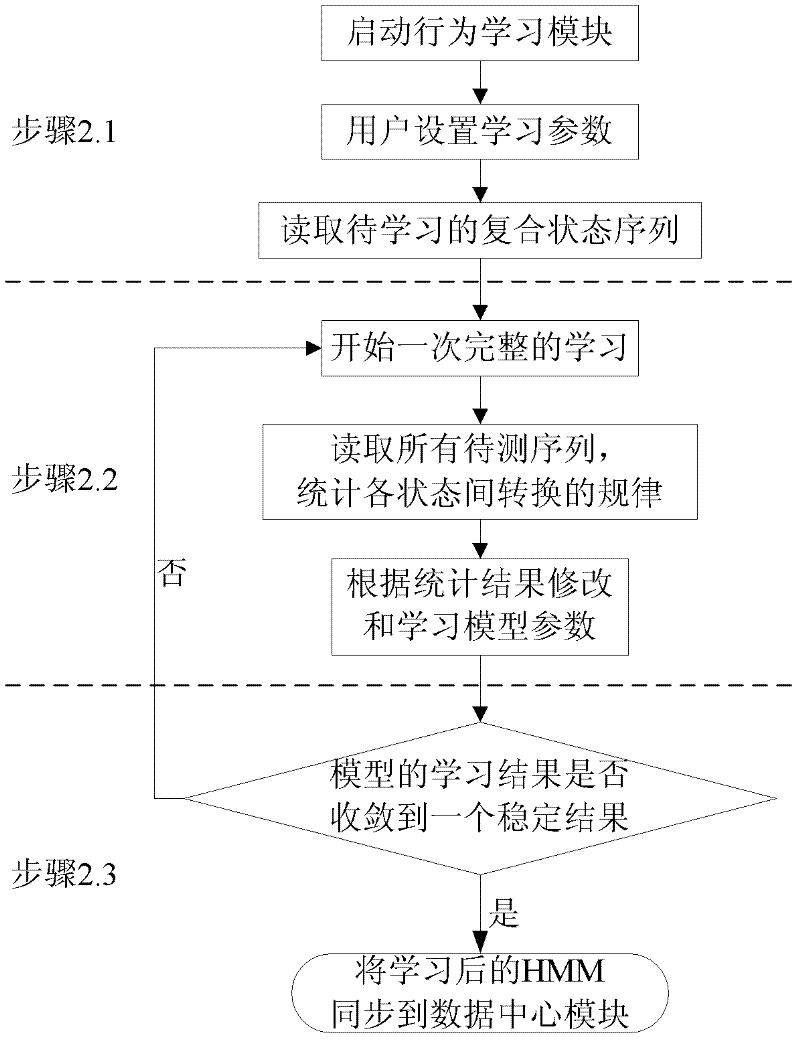
[0013] Step 2. The behavior learning module reads the sequence to be learned and the initial model from the data center module. After repeated learning, and ends with a certain convergence standard, the learning result is stored in the data center module. The learning result is the class the applied HMM;
[0014] Step 3. The behavior detection module sets the detection strategy according to the application type to be detected. If it is a known type of application, select the correspon...
specific Embodiment approach 2
[0015] Specific embodiment two, combine figure 1 This embodiment is described. The difference between this embodiment and the first embodiment is that the system monitoring module described in step 1 uses the interactive control module to configure monitoring parameters and control the operation of each module of the system.
[0016] In this embodiment, the interactive control module 5 is used to configure some monitoring parameters, and controls the operation of each module of the system, such as the user can open the SMS (Short Messaging Service) application program to perform some operations, and start the system monitoring module to intercept SMS in the background behavior status information, and combine the information to form the original composite state U. The user can also repeat this process to monitor the running behavior of multiple SMS programs. These applications must all be SMS-type applications with normal application behavior, namely They have relatively consis...
specific Embodiment approach 3
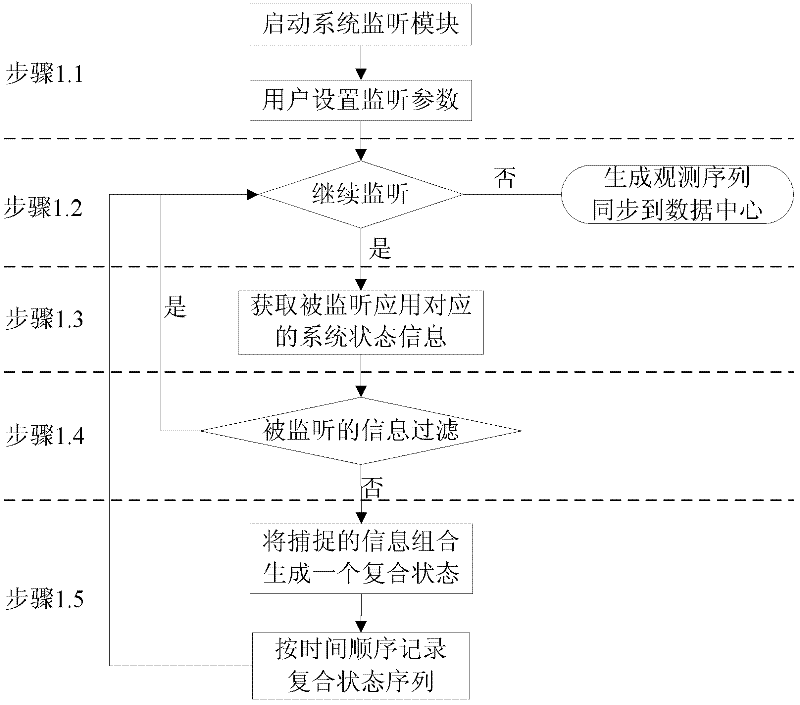
[0017] Specific embodiment three, combine figure 2 Describe this implementation mode, the difference between this implementation mode and specific implementation mode 1 is that the specific process of the step 1 is:
[0018] Step 1.1, start the system monitoring module, and the user sets the monitoring parameters: start the monitoring component, and monitor the status of the system when the monitoring application is running; set the monitoring parameters, including the time parameter of the monitoring time interval and the application name;
[0019] Step 1.2, determine whether to continue monitoring, if yes, then perform step 1.3, if not, generate an observation sequence and synchronize it to the data center module;
[0020] Step 1.3. Obtain the system state information corresponding to the monitored application: including the elements that make up the composite state, the stack top component type, the current state of the application, and the CPU and memory consumption of th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com