A software security detection method for code reuse programming
A detection method and code reuse technology, applied in the field of software security detection, can solve problems such as code injection attacks are no longer effective, computer system security threats, etc., to achieve the effect of improving software security quality, increasing the success rate of generation, and eliminating side effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
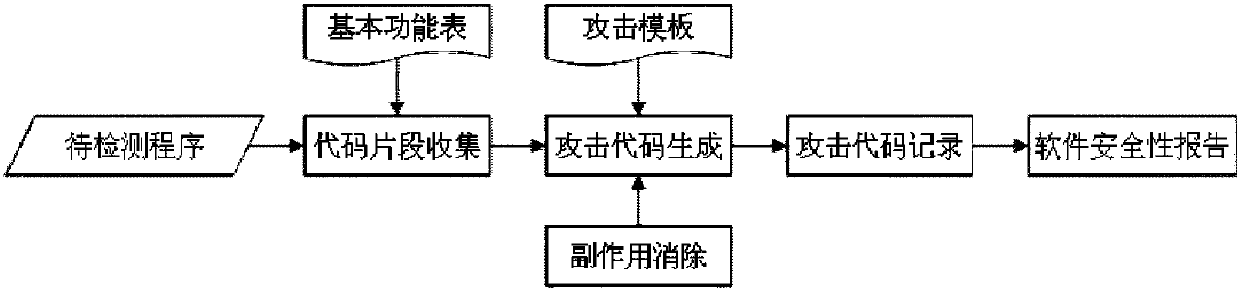
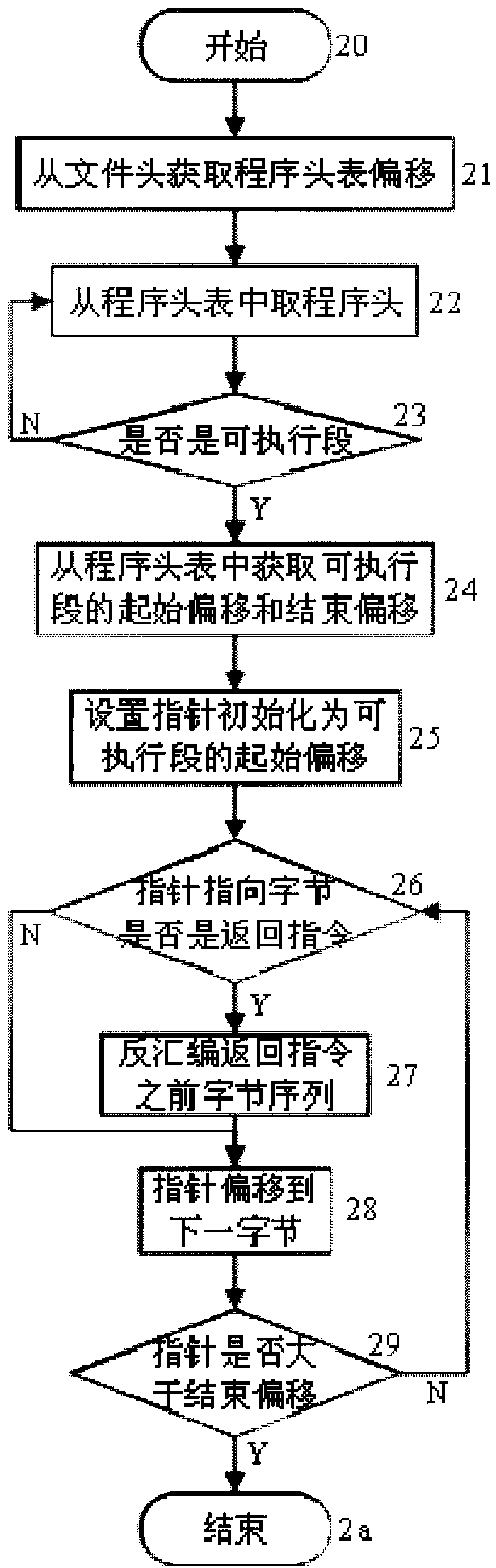
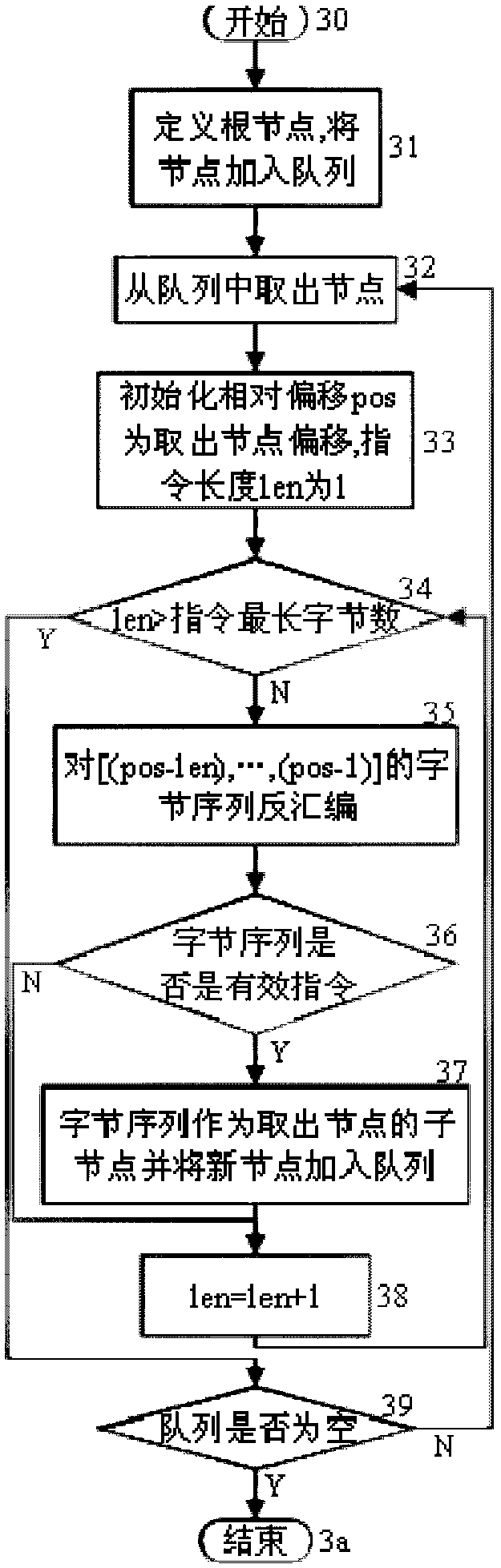
[0030] figure 1 It is an overall flow chart of the software security detection method. The input of the method is the program to be detected, and the output is the potential attack code in the program to be detected that can be utilized by an attacker. First, collect the code fragments of each basic function in the executable segment of the program to be detected; then combine the collected basic function code fragments according to the predefined attack template to generate the attack code; , so after the attack code is generated, it is necessary to use the side effect elimination strategy for the side effect code fragment in the attack code to eliminate side effects; if the side effect of the code fragment in the attack code is successfully eliminated, the attack code is available and recorded in the corresponding test result file; finally output The attack code in each test result file reports the potential security risks of reuse code programming in the program to be test...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com