An analysis method and device for a data privacy protection protocol
A data privacy and analysis method technology, applied in the computer field, can solve problems such as high labor costs, low efficiency, and difficulty in updating data privacy protection projects, and achieve the effect of reducing the difficulty of updating and improving analysis efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
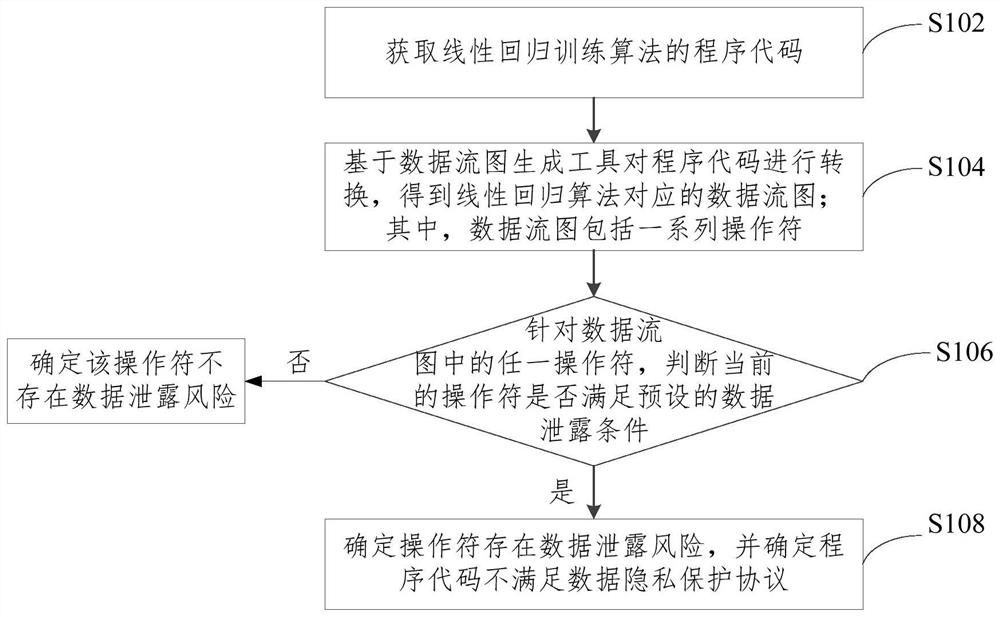
[0031] refer to figure 1 The flow chart of the analysis method of the data privacy protection agreement shown, the method mainly includes the following steps:
[0032] Step S102, acquiring the program code of the linear regression algorithm.
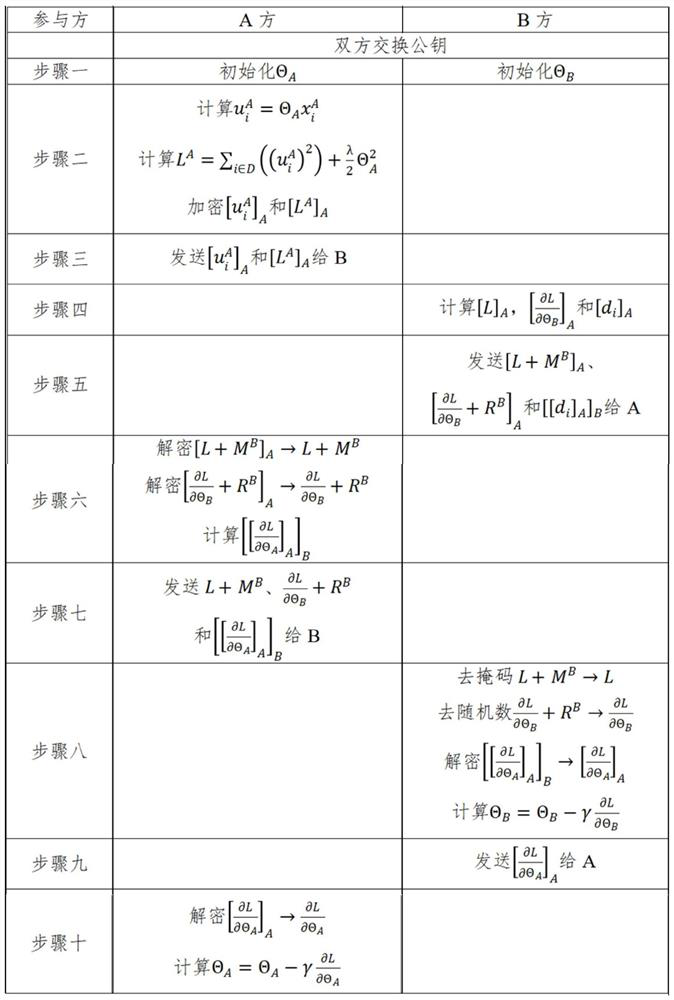
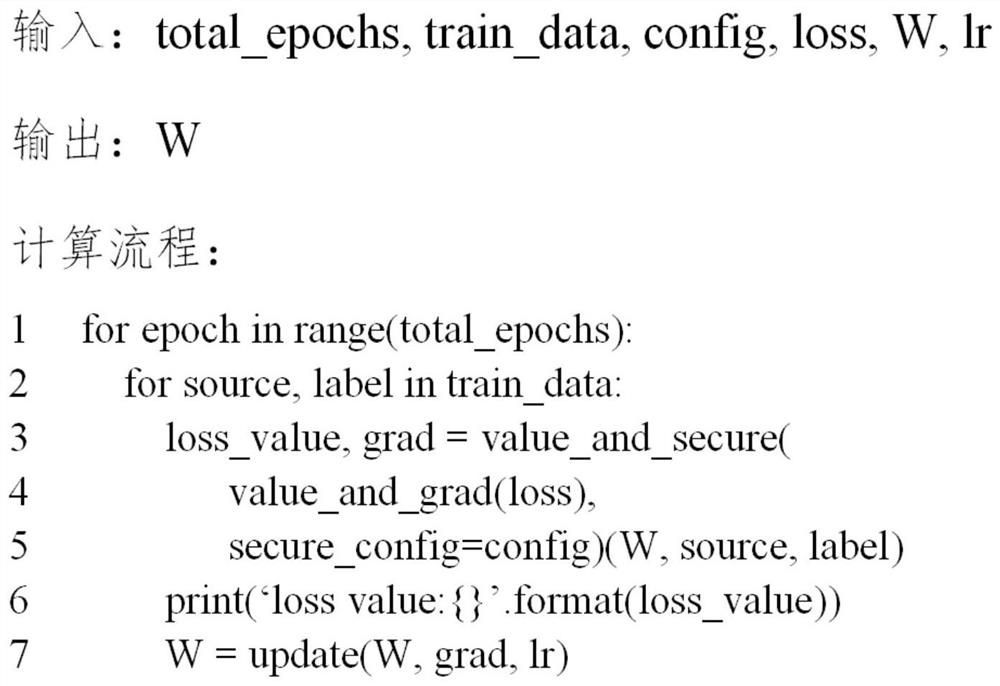
[0033] In practical applications, the program code used to train the linear regression algorithm needs to be executed by two different participants, and the program codes executed by different participants are different. Regression Algorithm Training. According to the participants, the program code can be divided into X data and Y data. The X data represents the part of the program code executed by the participant on the X side, and the Y data represents the part of the program code executed by the participant on the Y side. In this embodiment, the obtained program code of the linear regression algorithm is a complete program code including both X data and Y data.
[0034] Step S104, converting the program code based on the data flow ...
Embodiment 2
[0062] This embodiment provides an analysis device for a data privacy protection protocol, which is used to implement the analysis method for a data privacy protection protocol provided in the embodiment. refer to Figure 5 , the device consists of:
[0063] An acquisition module 502, configured to acquire the program code of the linear regression algorithm;
[0064] The conversion module 504 is used to convert the program code based on the data flow graph generation tool to obtain a data flow graph corresponding to the linear regression algorithm; wherein, the data flow graph includes a series of operators;
[0065] A judging module 506, configured to judge whether the current operator satisfies a preset data leakage condition for any operator in the data flow diagram;
[0066] The determination module 508 is configured to determine that the operator has a risk of data leakage and determine that the program code does not meet the data privacy protection agreement if it is s...
Embodiment 3
[0073] An embodiment of the present invention provides an electronic device, which includes: a processor and a storage device; a computer program is stored on the storage device, and the computer program executes the analysis of the data privacy protection protocol as described in Embodiment 1 when the computer program is run by the processor method.
[0074]An embodiment of the present invention provides a computer-readable storage medium, on which a computer program is stored. When the computer program is run by a processor, the steps of the method for analyzing the data privacy protection protocol in the first embodiment above are executed.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com