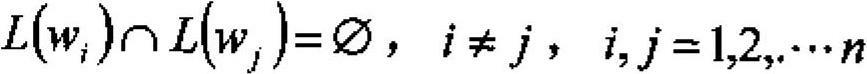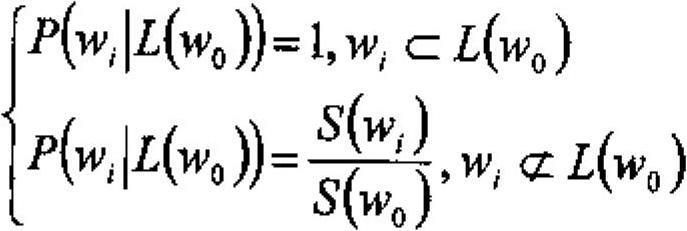Software vulnerability detection method based on behavioral characteristic automaton model
An automaton model and software vulnerability technology, applied in computer security devices, instruments, program/content distribution protection, etc., can solve problems such as fuzzy description of behavior characteristics, simple classification and quantification results, and unclear essential connection of vulnerabilities, etc., to improve Effects on Reliability and Safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
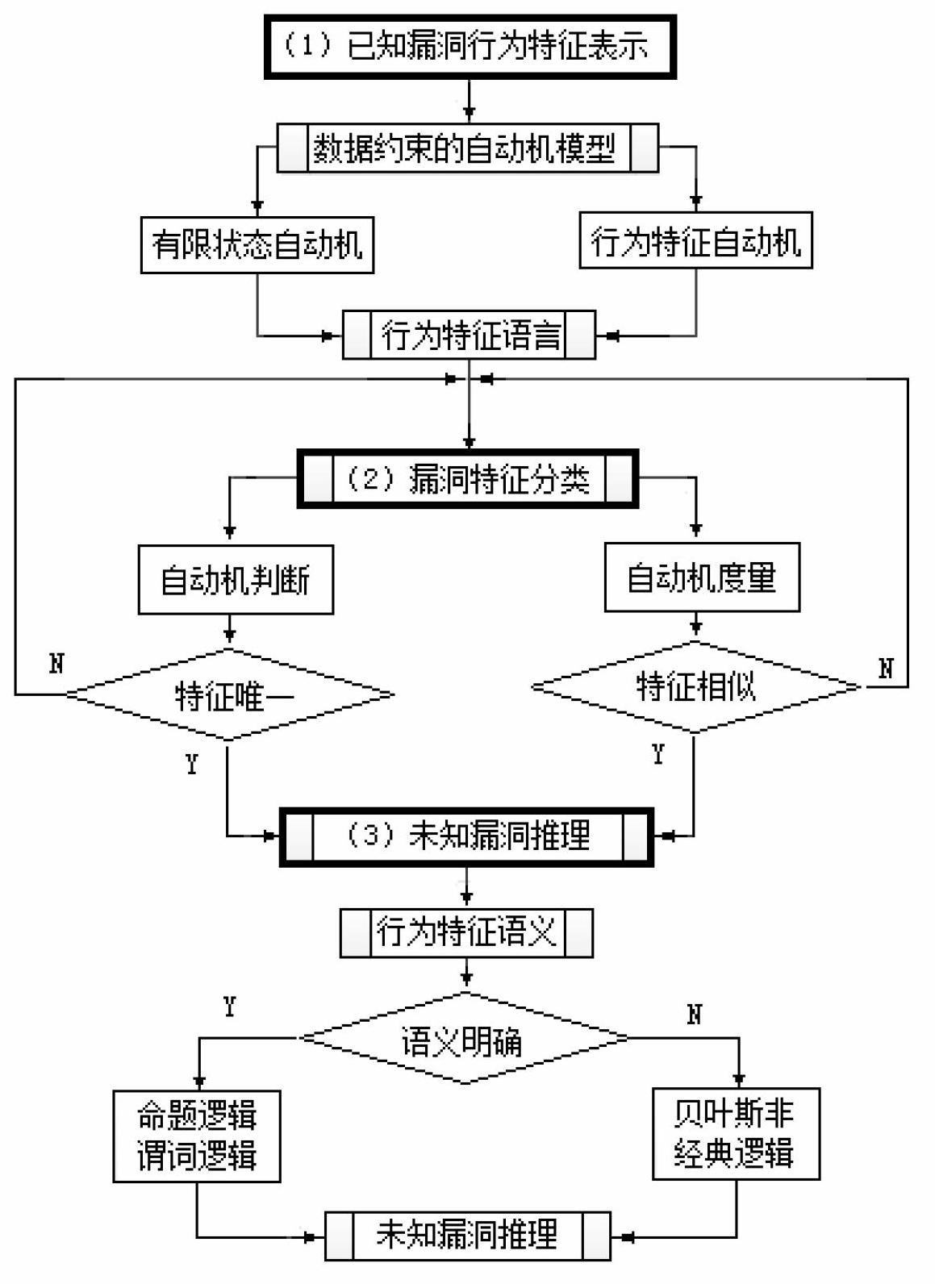
[0026] Such as figure 1 As shown, a software vulnerability detection method based on behavioral feature automaton model, the method includes the following steps:
[0027] 1) Representation of known vulnerability behavior characteristics in the vulnerability behavior characteristic database;
[0028] 11) Build an automaton model BAR with data constraints:
[0029] BAR = function(Behavior(), Automaton(), reasoning())
[0030] Behavior=B(Judge, In, Out, State, Action)
[0031] Automaton=(FSM(In, Out, State, f(In), g(s)), BM(Behavior))
[0032] Re asoning(Logic(FSM(), NoClassicalLogic(BM()))
[0033] Among them, Behavior represents the expression of behavior characteristics, Automaton represents automata, and reasoning represents reasoning; behavior characteristics are expressed as functions related to constraints Judge, input In, output Out, state State and behavior Action; automata include finite state automata FSM (In , Out, State, f(In), g(s)) and behavioral characteristi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com