Detection method for information leakage hidden trouble in Android application log based on static state analysis
A detection method and technology for information leakage, which can be applied in the fields of instruments, electrical digital data processing, computer security devices, etc., and can solve problems such as privacy leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] The invention will be further described in detail below in conjunction with the embodiments and the accompanying drawings.
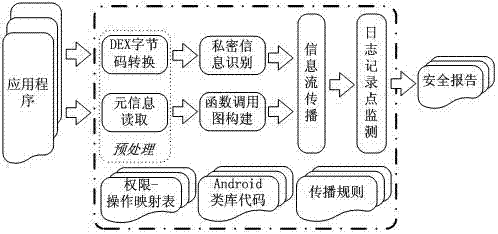
[0055] The overall schematic diagram of the detection method of the present invention is as figure 1 shown.
[0056] The present invention designs and implements the above-mentioned information leakage security detection technology based on traditional static information flow analysis. This section makes a detailed introduction to the specific implementation of the framework.
[0057] 1. Preprocessing stage
[0058] The present invention finally selects the DED tool to carry out the transformation work of decompiling DEX byte code transformation. DED is a set of conversion tools designed by Enck et al. to convert DEX bytecode into traditional Java bytecode. When DED converts DEX bytecodes into traditional Java bytecodes, there is a certain error rate. During the DEX conversion stage, correct Java bytecodes cannot be generated. However, all cu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com