Private key safety management method based on identity public key cryptography system
A technology of identity public key and security management, applied in the direction of public key of secure communication, user identity/authority verification, etc., can solve the problem of low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
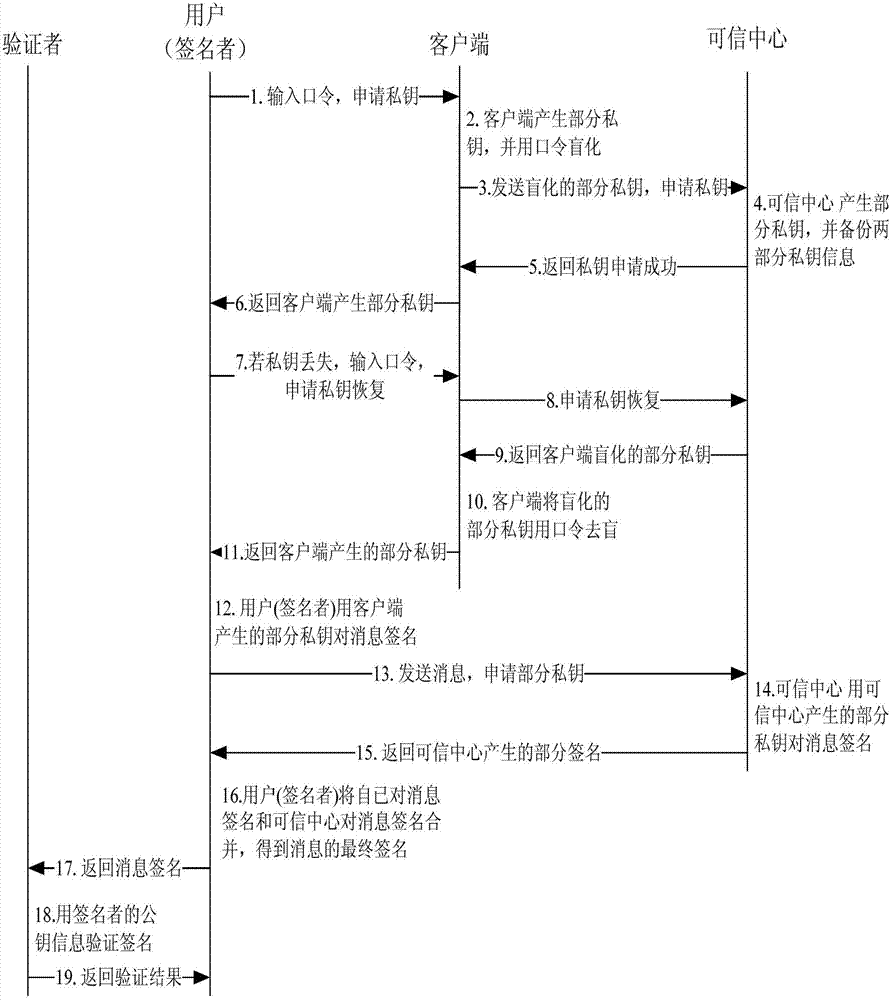
[0082] see figure 1 As shown, the system overall framework flow chart of the private key security management method based on the identity public key cryptosystem.
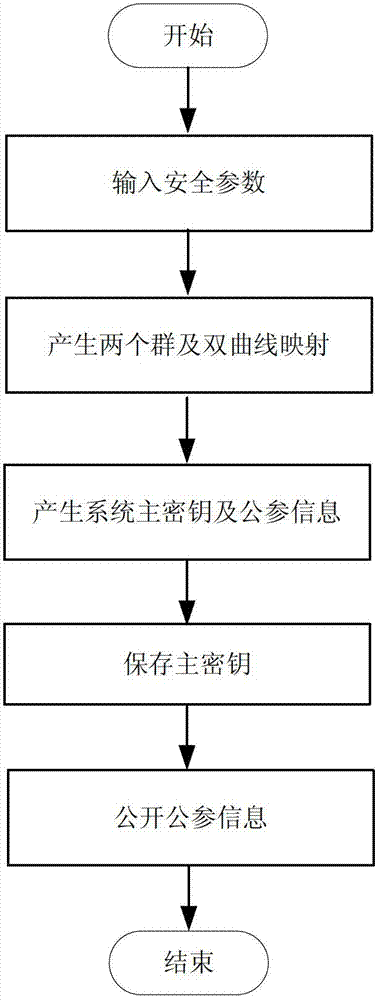
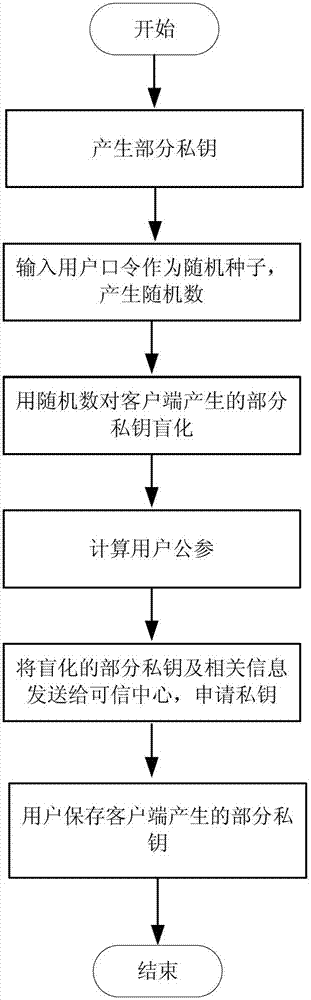
[0083] The entire framework flow chart includes trusted center, client, signer and verifier. The signer first enters the password through the client; the client generates part of the private key, and then blinds it with the password, and sends the blinded part of the private key to the trusted center to apply for a private key; the trusted center generates part of the private key and backs it up Two parts of private key information, the private key application is successfully returned to the client; the signer saves part of the private key generated by the client through the client. If the signer's private key is lost, it is necessary to apply to the trusted center for private key recovery, that is, enter the password through the client; the trusted center returns the client's blinded partial private key; the clie...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com