DDos (distributed denial of service) attack defensive system based on network trap
An attack defense system and network trap technology, applied in the field of distributed denial of service attack (DDoS) defense system, can solve the problem that normal users cannot access network resources, etc., and achieve the effect of fast reflection and timely response to attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
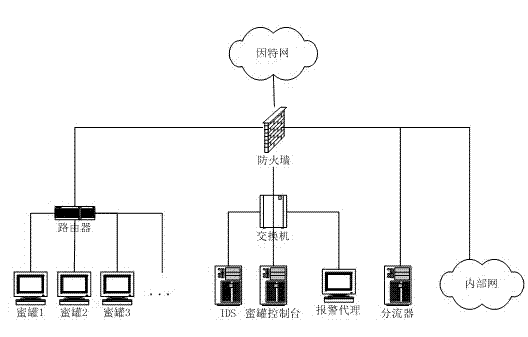
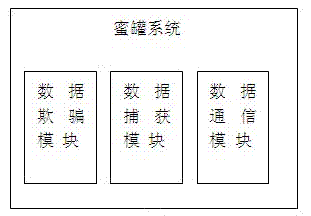
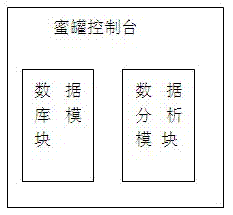
[0039] figure 1 The shown system structure diagram of the present invention is physically composed of a honeypot console, multiple honeypot systems, an alarm agent and a data distribution server. These honeypot systems deployed in the network can form a security defense system. Each honeypot system is a deceiving host, and its external characteristics can attract attackers to invade. The honeypot system can establish multiple operating system camouflage environments, and its operating system is the same as the host operating system. Attackers can enter the honeypot system in two ways. One is that the attacker finds sensitive information or system vulnerabilities on the honeypot system and enters through attack tools; The address diversion function of the SIPF diverts suspicious data into the honeypot system.
[0040] In the actual networking, the honeypot system and the honeypot console are deployed in different places and separated by a firewall. The connection between them...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com