Network access control model as well as method and terminal thereof
A technology of network access control and model, applied in the field of network
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
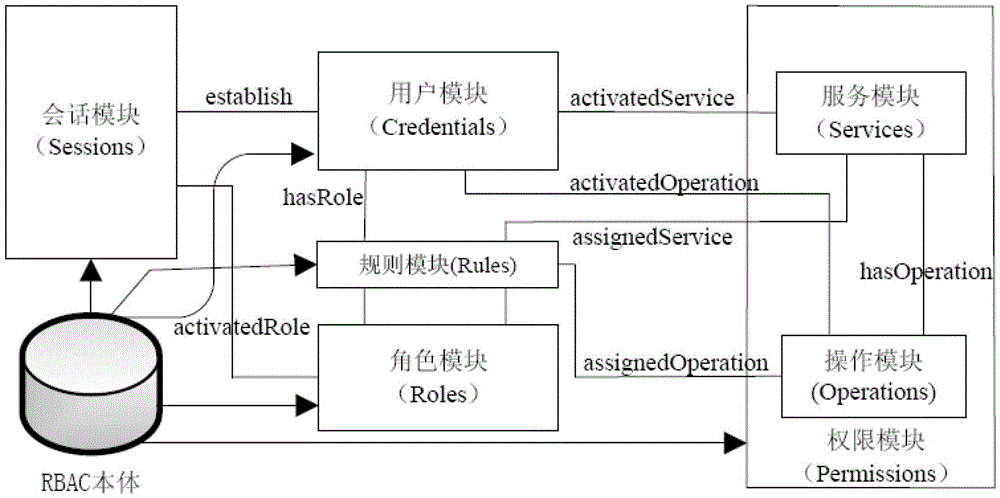
[0018] Such as figure 1 As shown, the network access control policy model proposed in the preferred embodiment of the present invention includes RBAC ontology, user module, session module, role module, authority module and rule module, wherein the rule module is used to realize user module, role module, The derivation between or within the permission modules can automatically assign the corresponding relationship between users and roles, roles and permissions, and the assignment of roles can also be restricted according to actual needs.
[0019] The modules mentioned in this embodiment can be software, hardware, firmware, or a combination thereof that independently implements a specific function, such as programs, storage media, integrated circuits, etc., and can also be stored in the same network entity or in a distributed manner. In different network entities, the present invention is not necessarily limited to specific implementation manners. Each module is described in de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com