User privacy data protection method and mobile terminal using user privacy data protection method
A mobile terminal, user privacy technology, applied in the direction of preventing unauthorized use of memory, instruments, characters and pattern recognition, etc., can solve problems such as decreased user satisfaction, affecting user convenience, and rejecting users, and achieves saving of password input. time, avoid the risk of forgetting passwords, and improve the effect of user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
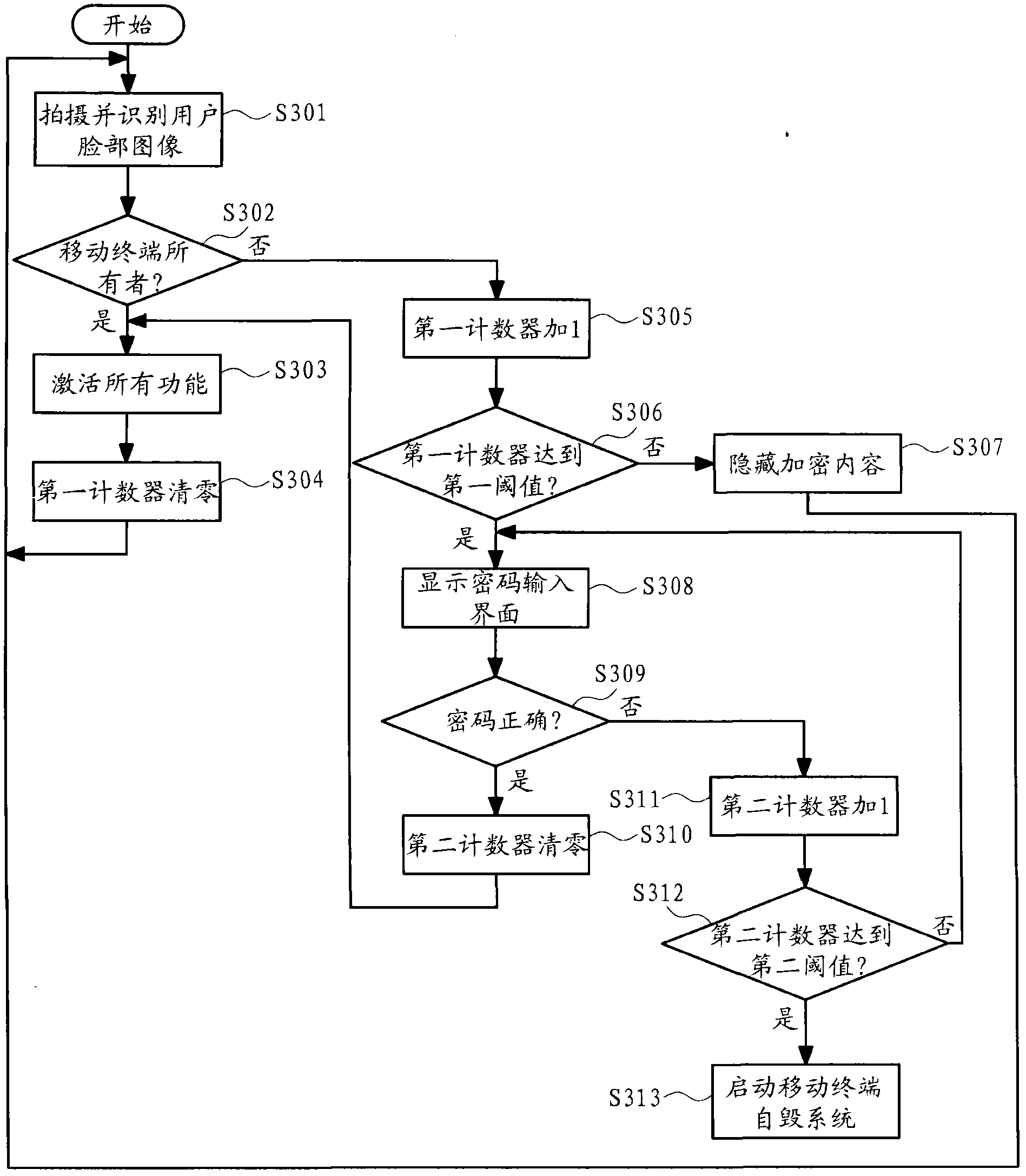
[0024] Embodiments of the invention will now be described in detail, examples of which are illustrated in the accompanying drawings, wherein like reference numerals refer to like parts throughout. The embodiments are described below in order to explain the present invention by referring to the figures.
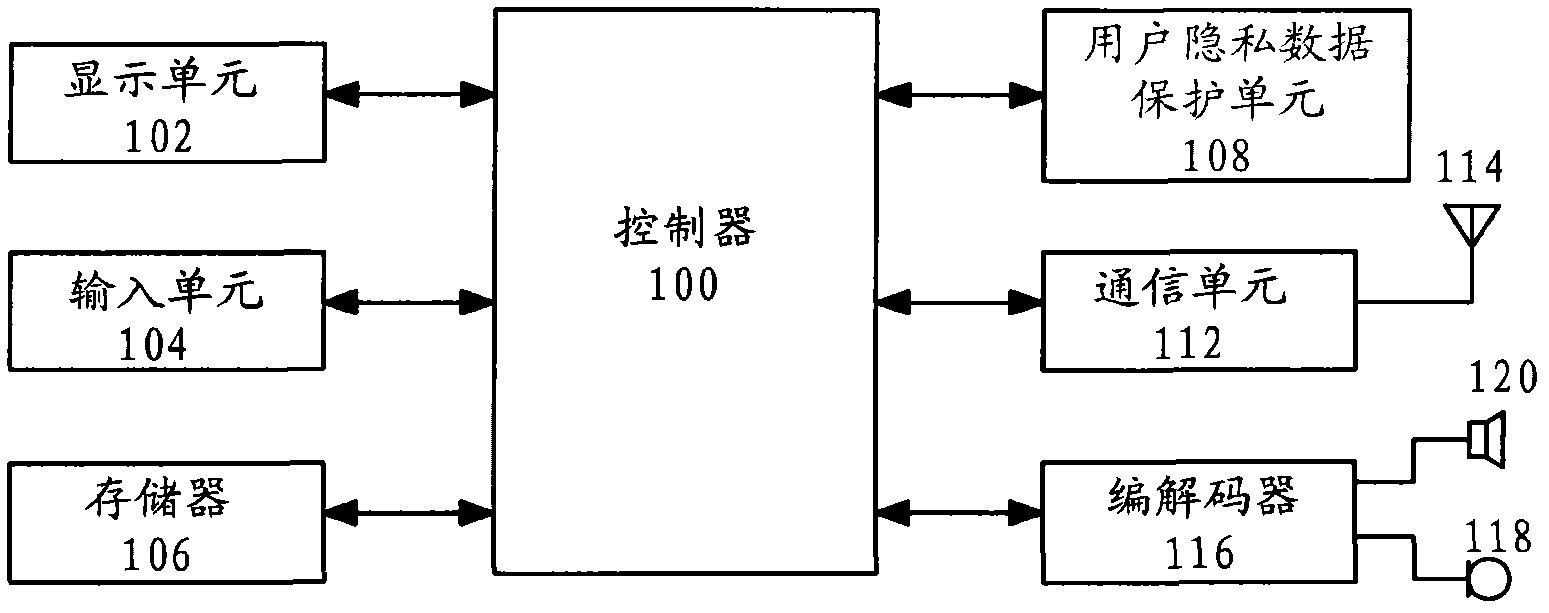
[0025] figure 1 It is a block diagram showing a mobile terminal for protecting user privacy data according to an embodiment of the present invention. According to an embodiment of the present invention, the mobile terminal may be a mobile phone. However, the present invention is not limited thereto, and the mobile terminal may also be a PDA, PMP, IPAD, etc.
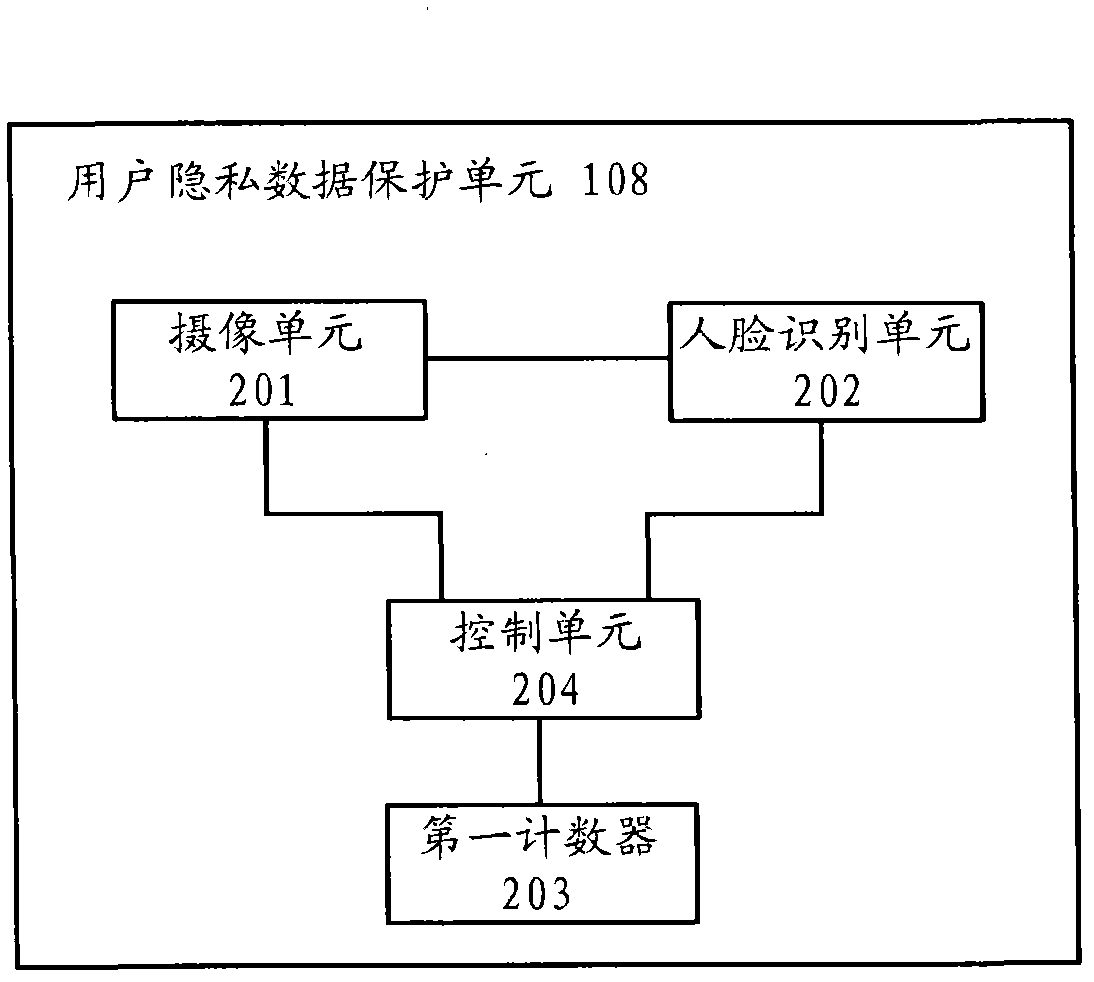
[0026] refer to figure 1 , the mobile terminal includes a controller 100 , a display unit 102 , an input unit 104 , a memory 106 , a user privacy data protection unit 108 , a communication unit 112 , an antenna 114 , a codec 116 , a microphone 118 and a speaker 120 .
[0027] The controller 100 controls the overall op...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com