Method and system for processing Hash collision
A hash collision and hash technology, which is applied in the direction of electrical digital data processing, special data processing applications, instruments, etc., can solve the problems of nowhere to store table items, insufficient TCAM space, high cost, etc., to reduce hash conflicts The effect of incidence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be described in detail below in conjunction with specific embodiments shown in the accompanying drawings. But these embodiments do not limit the present invention. Based on the various embodiments of the present invention, all other embodiments obtained by those of ordinary skill in the art without creative work should be included in the protection scope of the present invention .
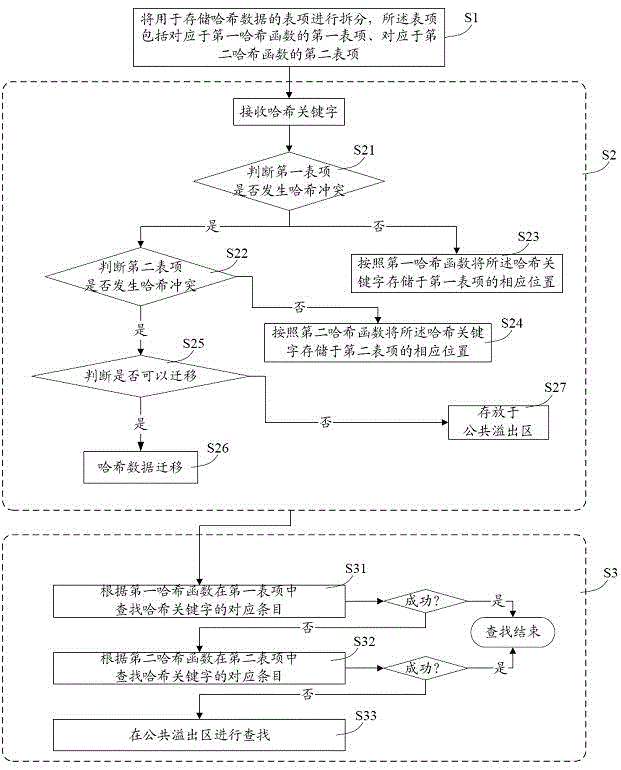
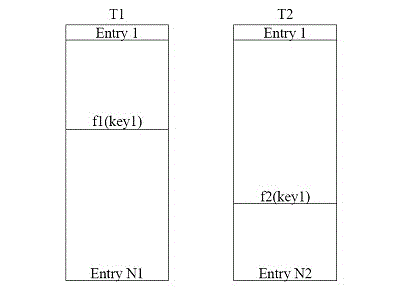
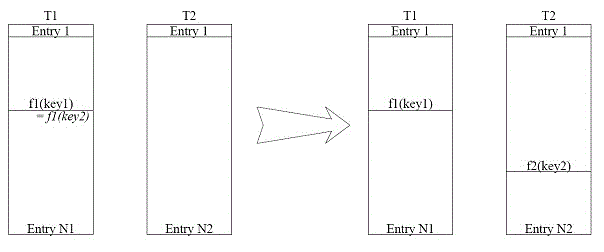
[0031] Please refer to Figure 1 to Figure 4 As shown, it describes some specific embodiments of the hash collision processing method of the present invention. Among them, such as figure 1 As shown, in one embodiment of the present invention, the method for processing hash conflicts mainly includes the step of dividing table entries (step S1), storing the hash key (step S2) and searching for hash entries (step S3). Specifically, the above steps include:
[0032] S1. Split an entry for storing hash data, where the entry includes a first entry corresponding to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com