Field programmable gate array-based (FPGA-based) intrusion detection system and method
An intrusion detection and input technology, applied in the field of network security, can solve the problems of high power consumption, small capacity and high price
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0070] The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments.
[0071] This embodiment adopts a development board based on Cyclone II series FPGA chips, and the system uses Quartus II9.0 as a software development tool.
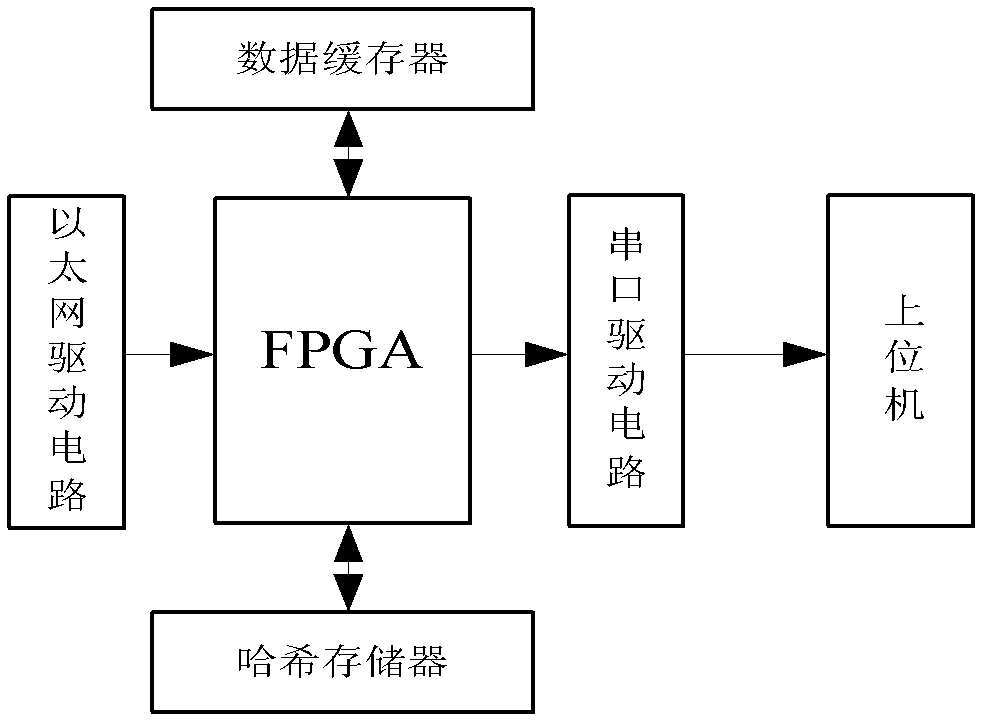
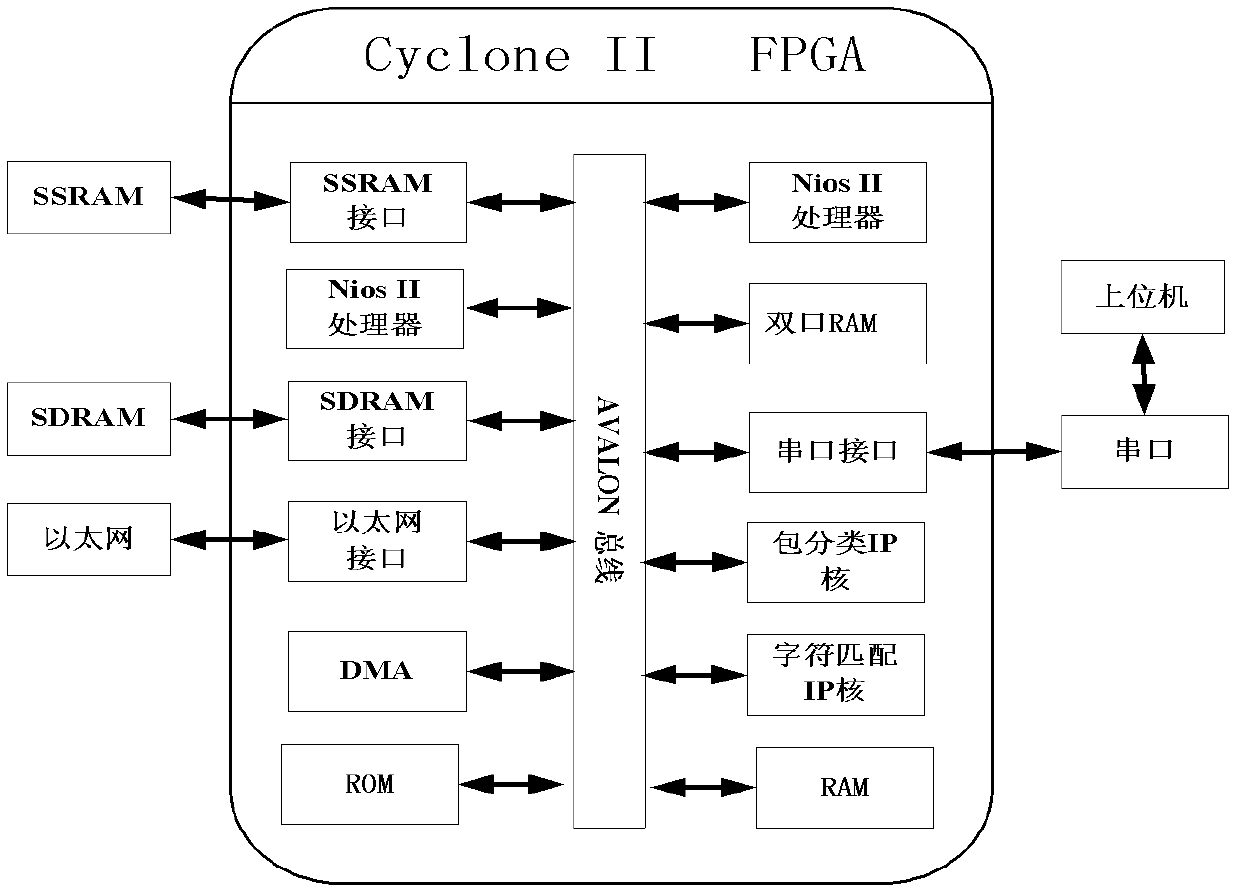
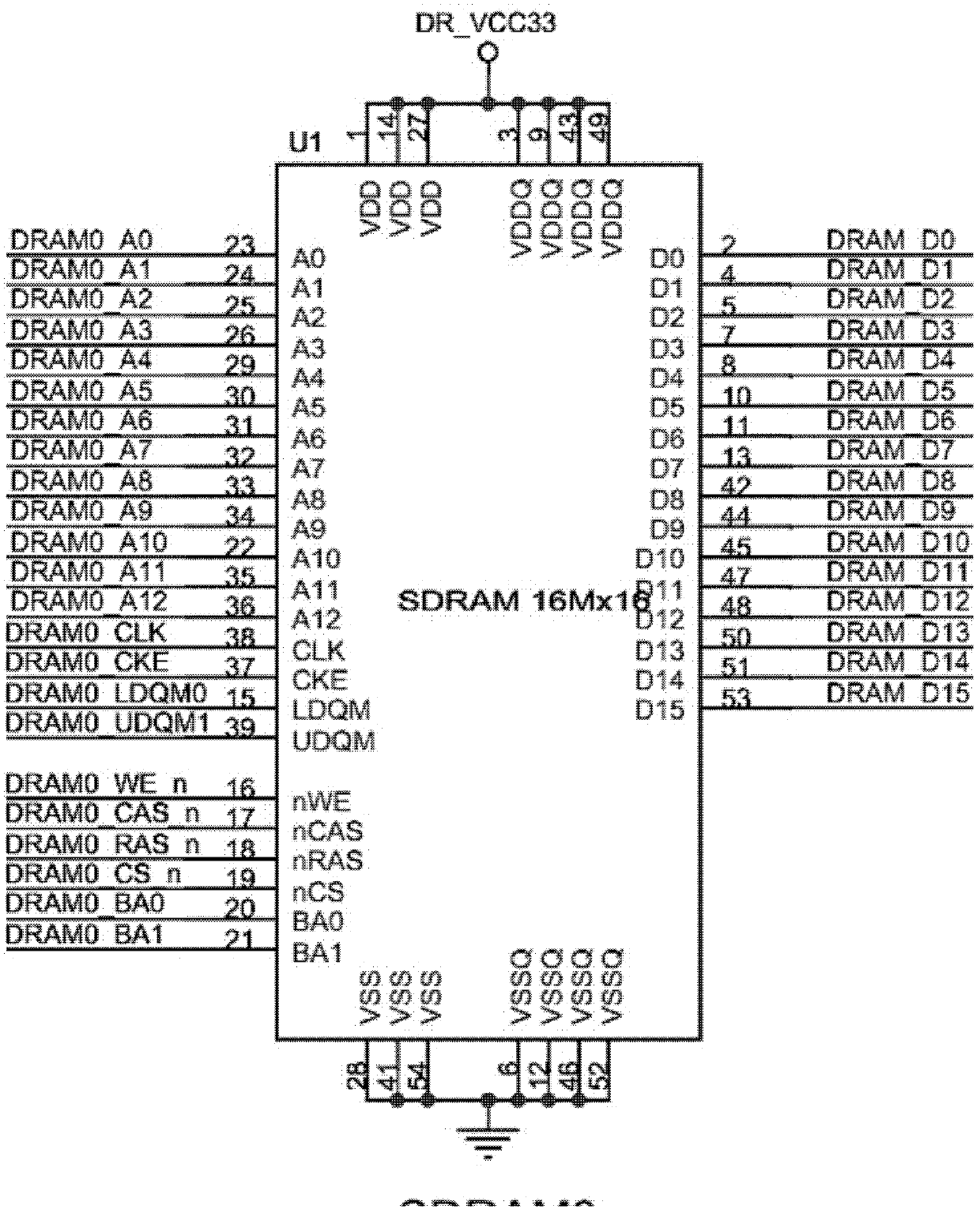
[0072] figure 1 It is a system block diagram of the present invention, including Ethernet driver circuit, FPGA, data buffer, hash memory, serial port driver circuit and host computer, wherein, the FPGA block diagram is as figure 2 As shown, the model of the FPGA chip is Cyclone II series EP2C70F896C6N, which is the controller of the system and controls the operation of the system; the Ethernet driver chip used is DM9000A, which controls the sending and receiving of system Ethernet data; the data buffer is capacity It is 512K*38 SSRAM chip IS61LPS51236A-200TQL, which stores the intermediate data of system operation; the hash memory is composed of two 16M*16 SDRAM memories, which store the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com