Running protection method for computer software product
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
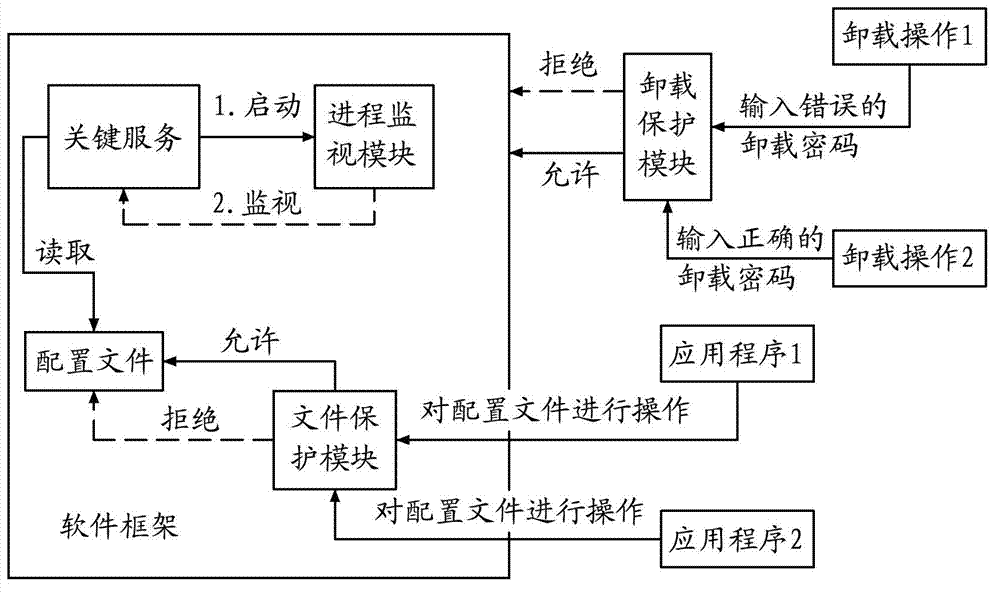
[0023] Such as figure 1 As shown, the present invention is based on the Hook technology and remote injection technology provided by Microsoft, and through the development of an independent protection framework, the respective defects of the software protection methods in the prior art are skillfully solved, and a relatively complete software self-protection can be realized. Features.
[0024] The following is a brief introduction to several technologies used:
[0025] Hook technology (Hook technology) is a means provided by the Windows operating system to allow other programs to modify the behavior of the system or applications at the binary level. Applications can use this technology to control specific behaviors of the system (such as specific API call) to intercept and insert custom actions.
[0026] Remote injection technology is a technology provided by the Windows system to inject dynamic link libraries (DLLs) into other processes. Through this technology, the behavior...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com