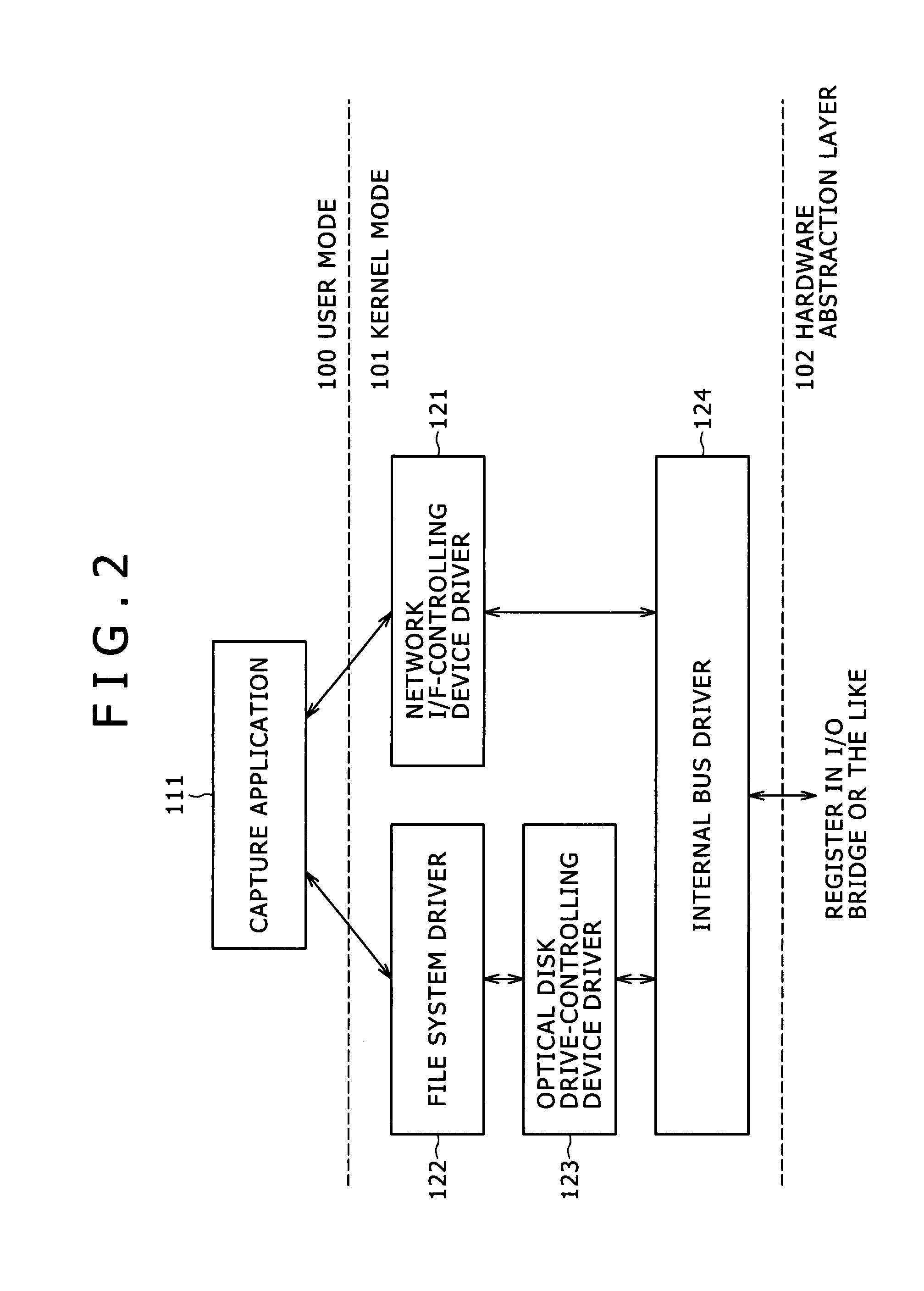
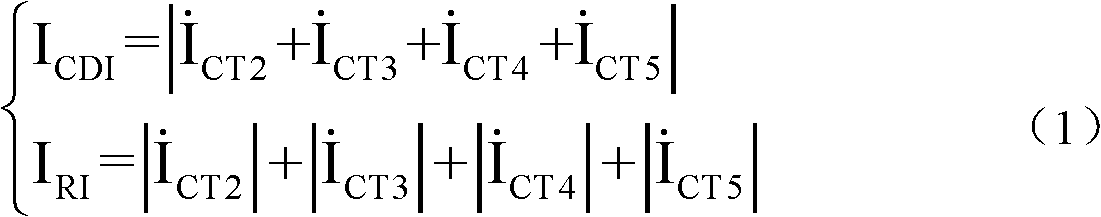Patents
Literature
80 results about "Abnormal end" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
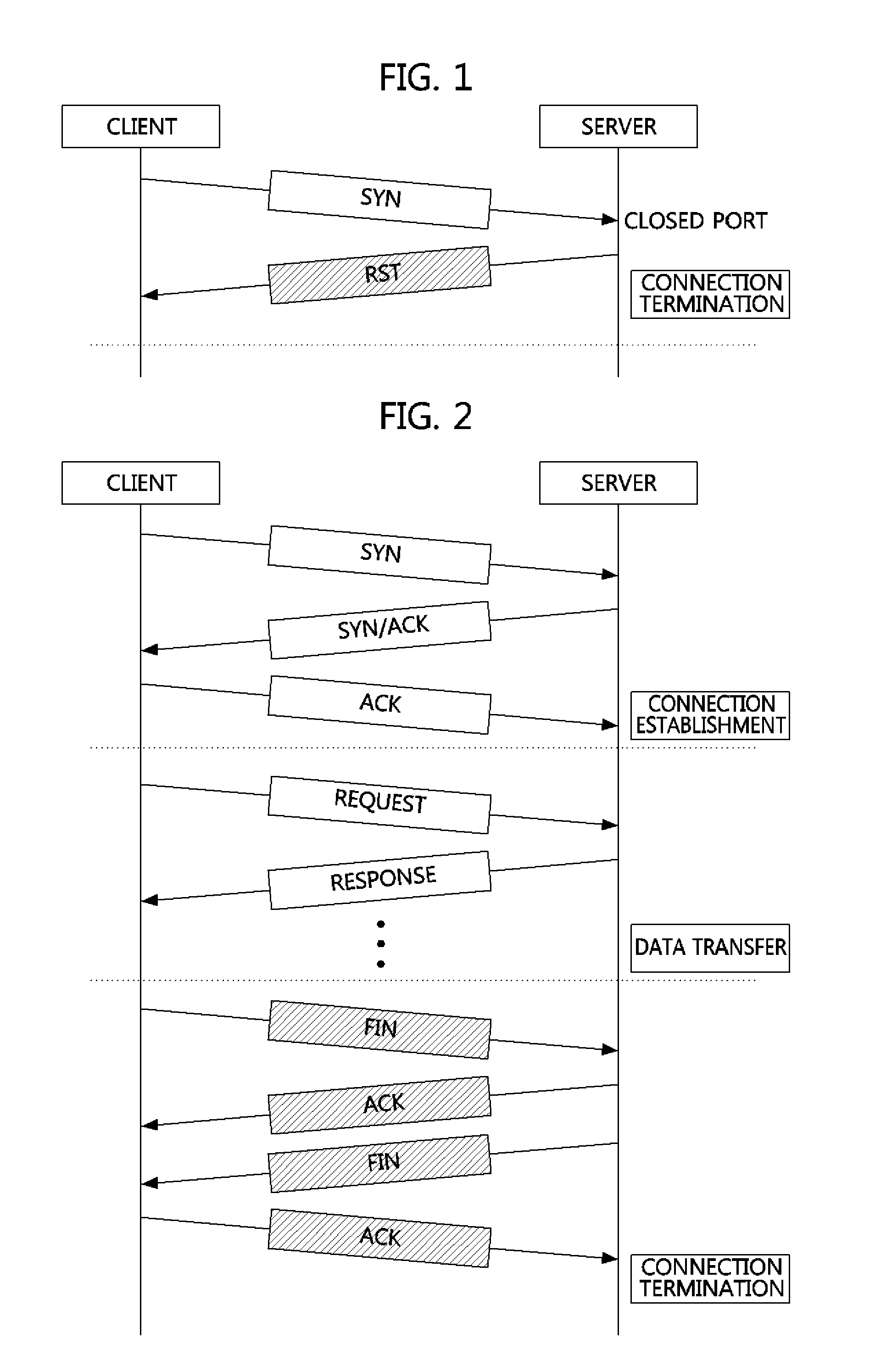
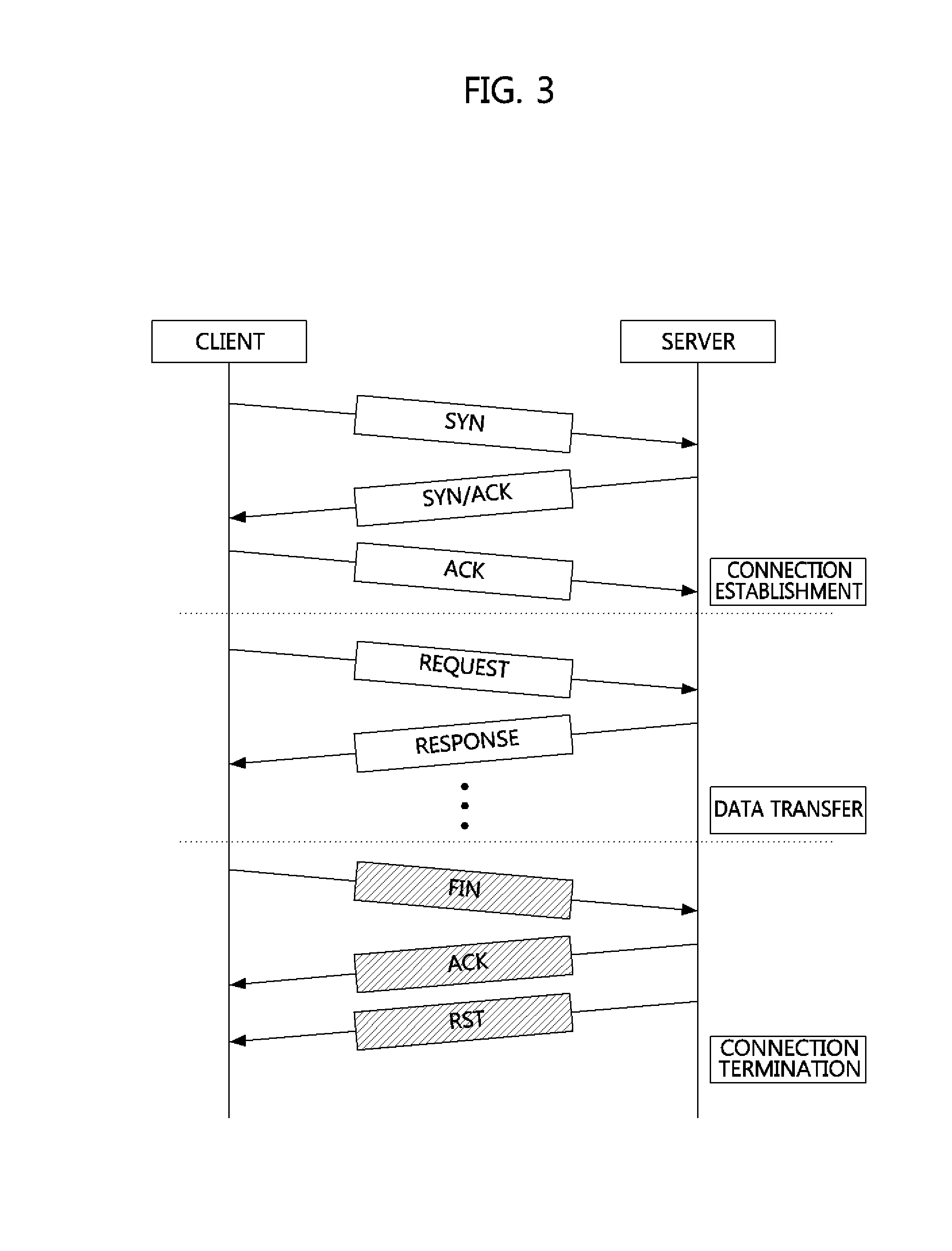
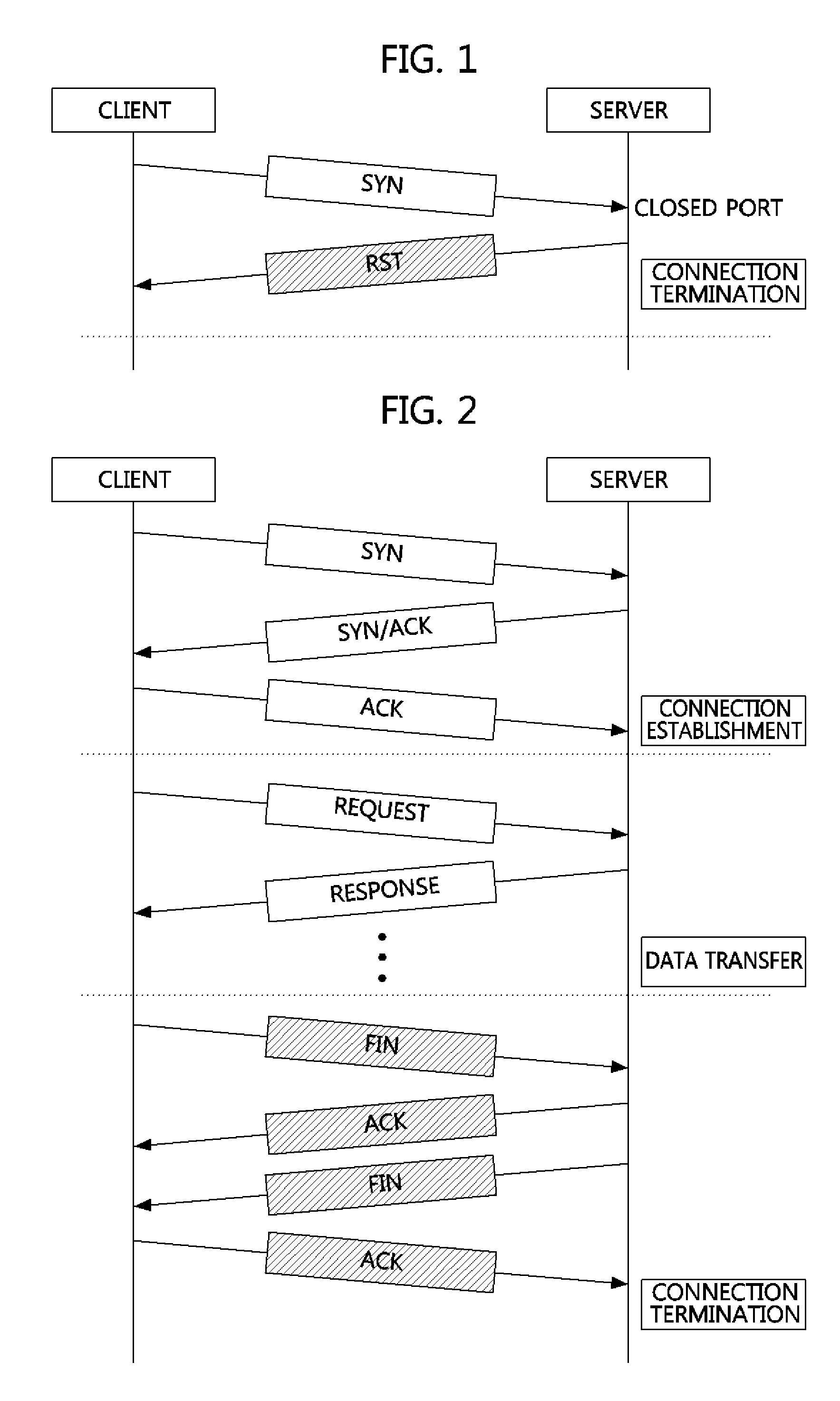
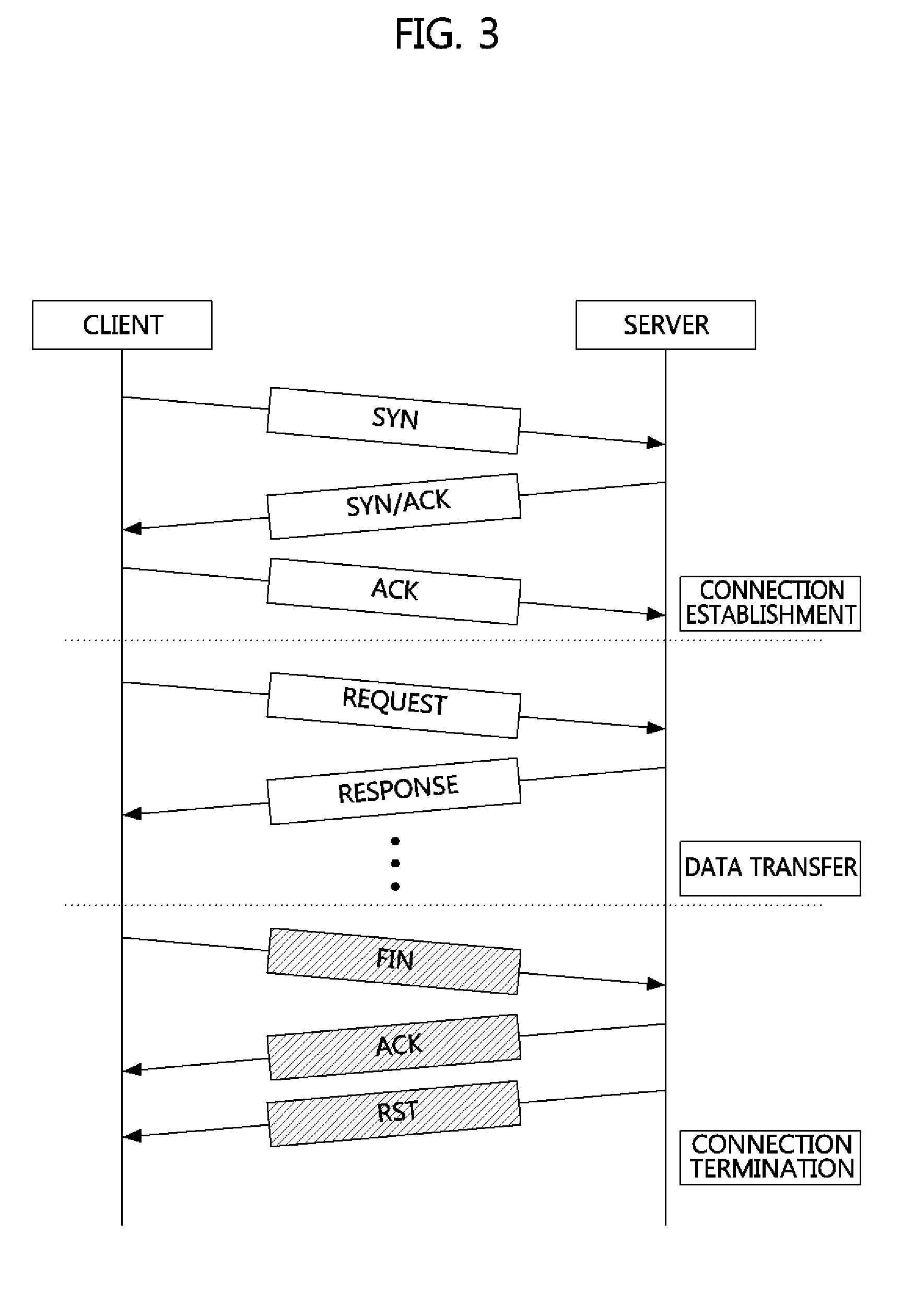
An AbEnd (also abnormal end or abend) is an abnormal termination of software, or a program crash. This usage derives from an error message from the IBM OS/360, IBM zOS operating systems. Usually capitalized, but may appear as "abend". The most common were ABEND 0C7 (Data exception) and ABEND 0CB (Division by zero). Abends could be "soft" (allowing automatic recovery) or "hard" (terminating the activity).
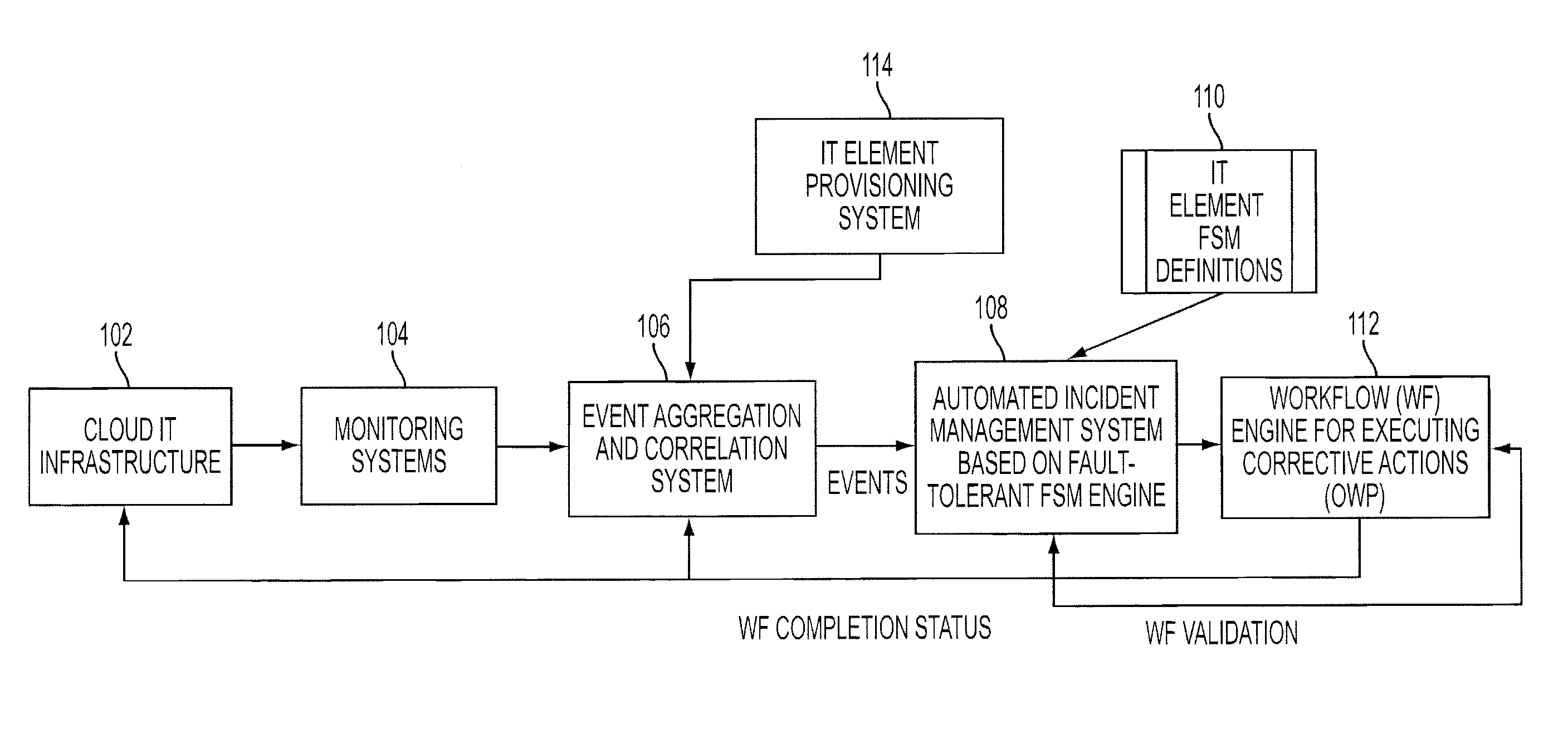
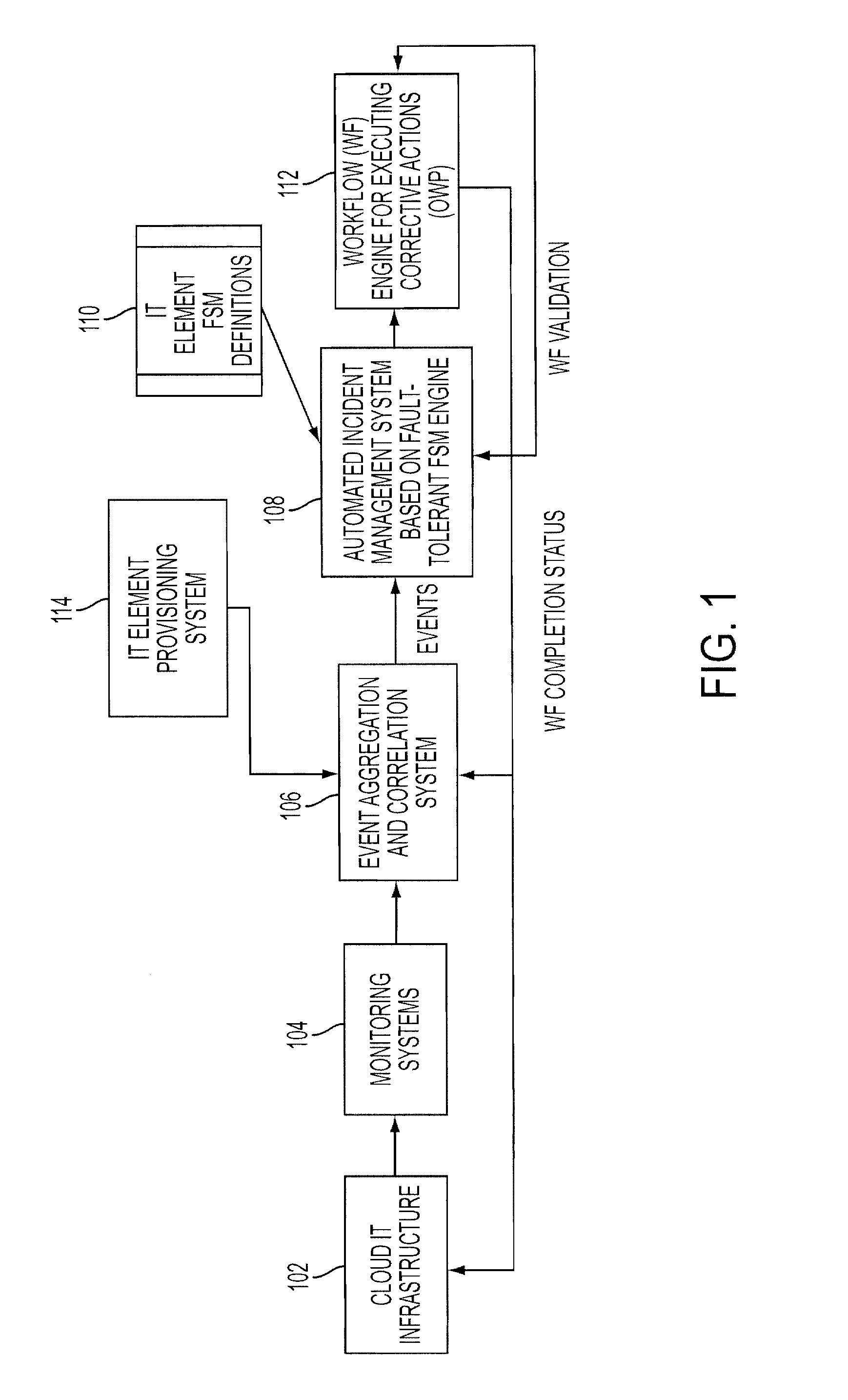
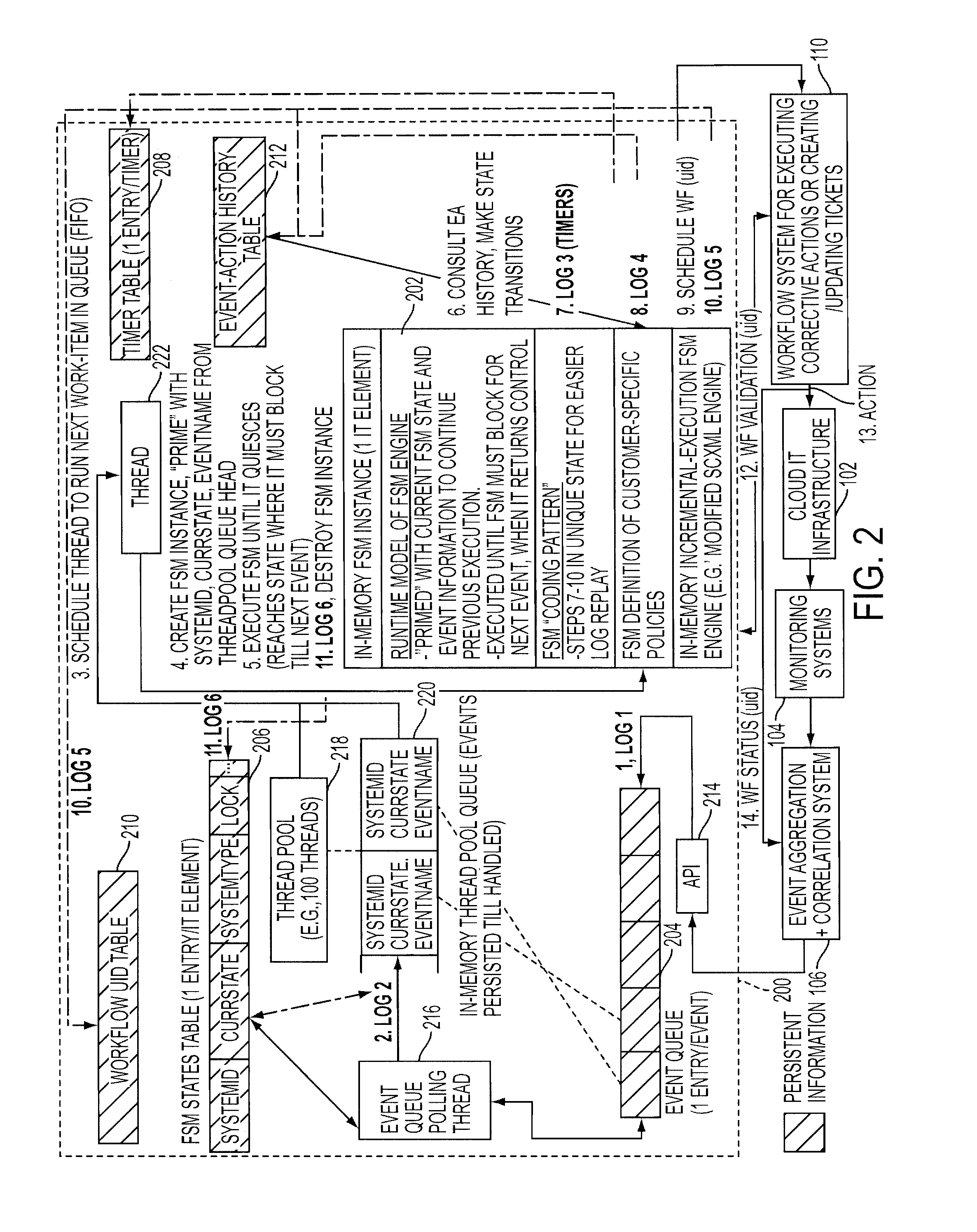
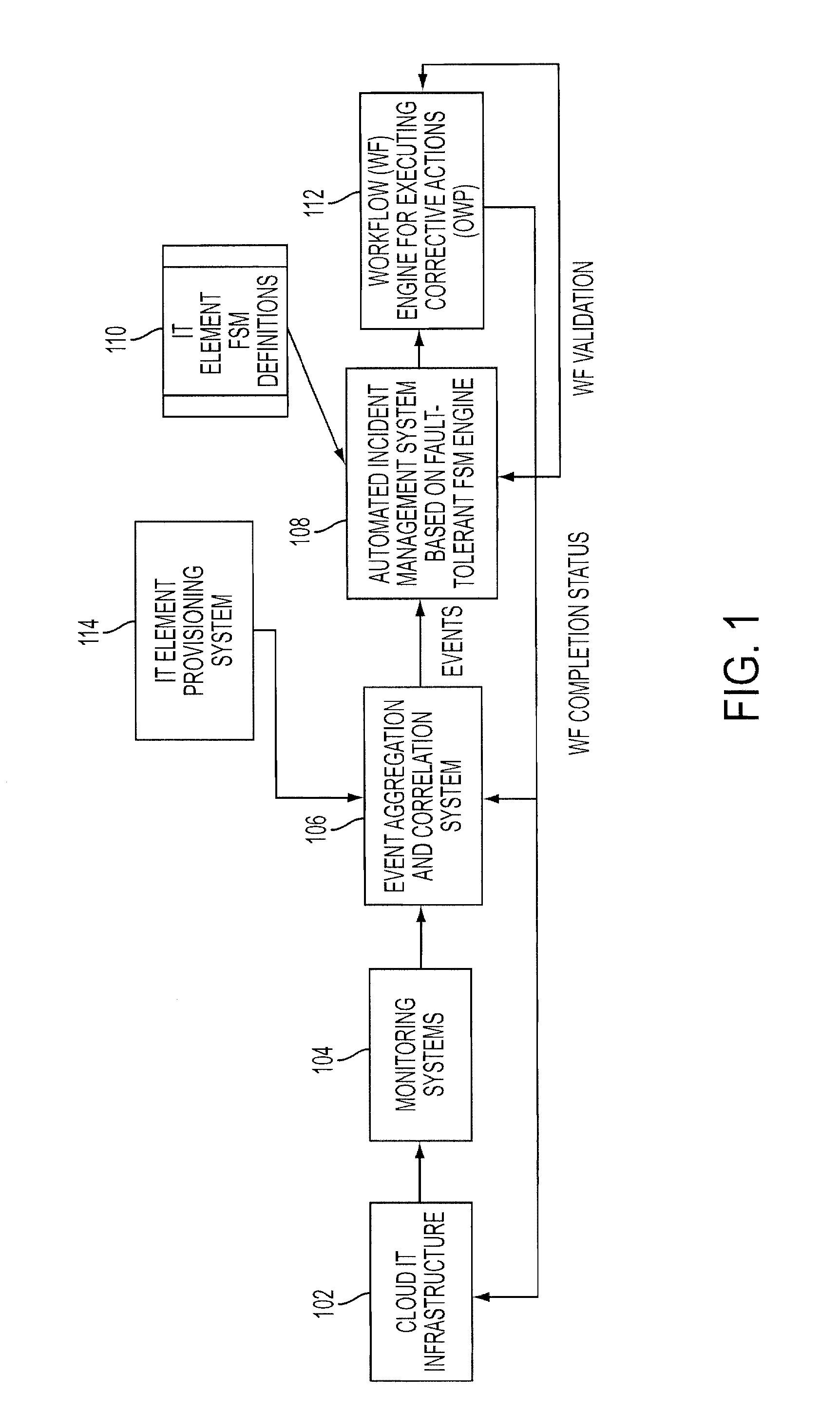
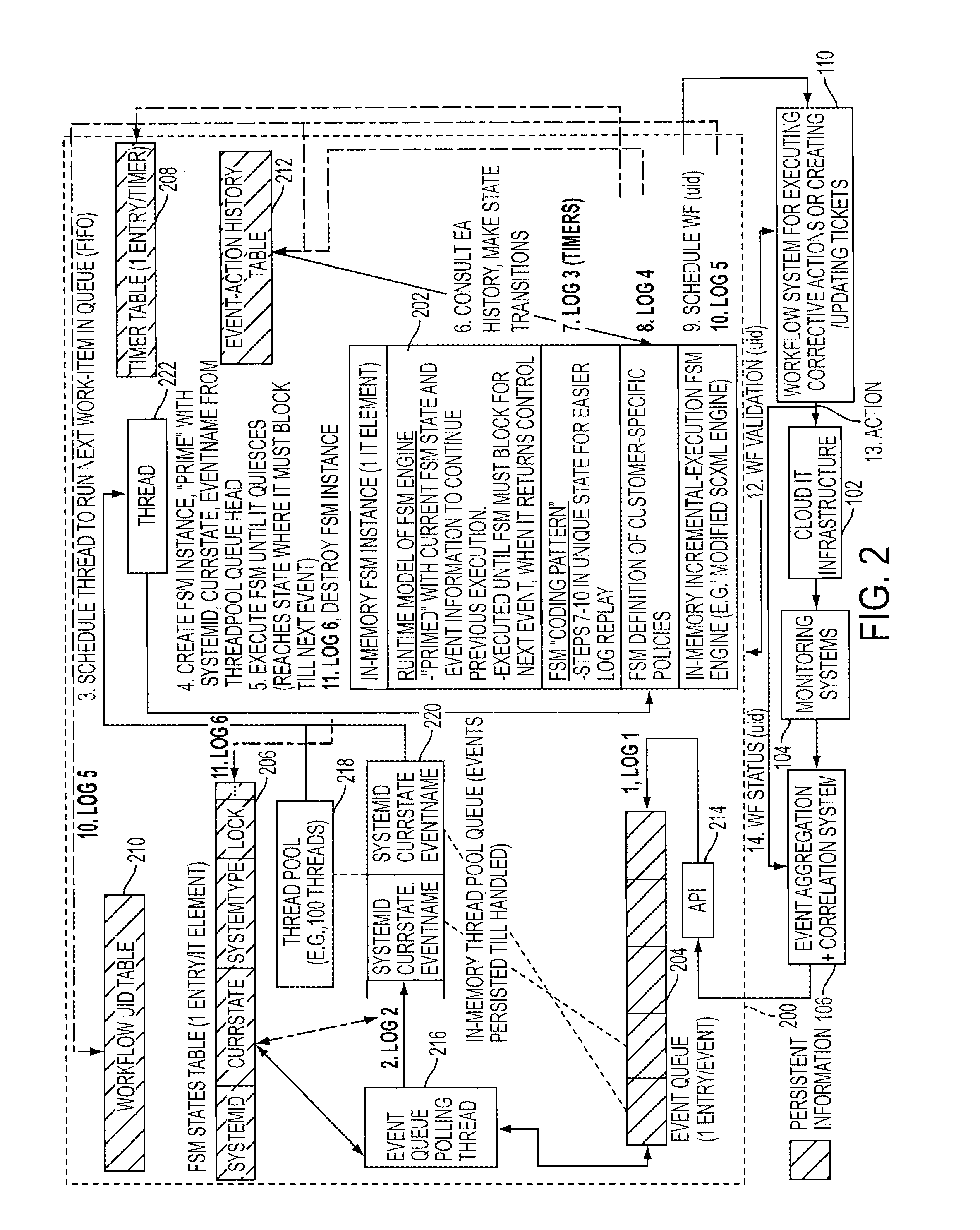
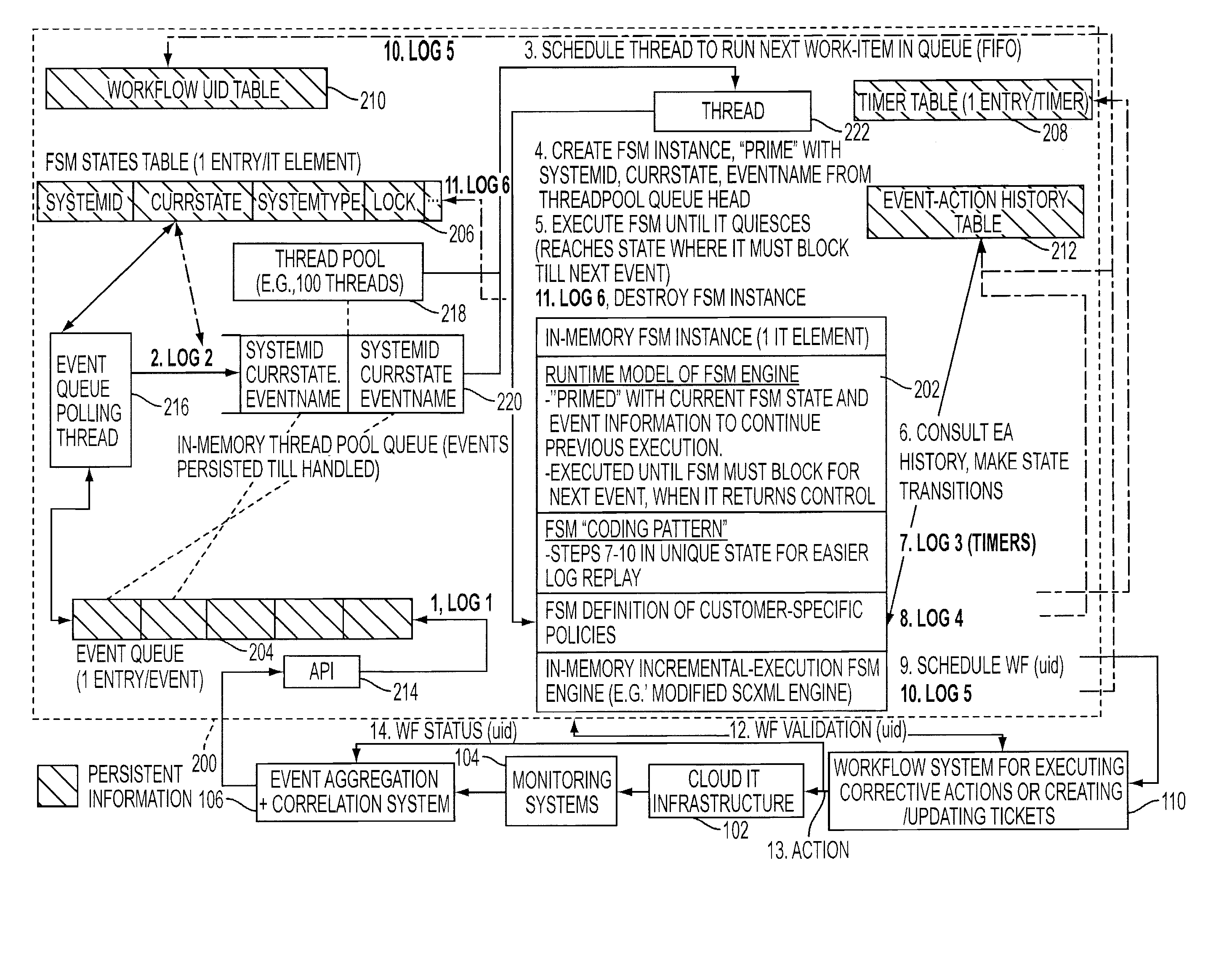
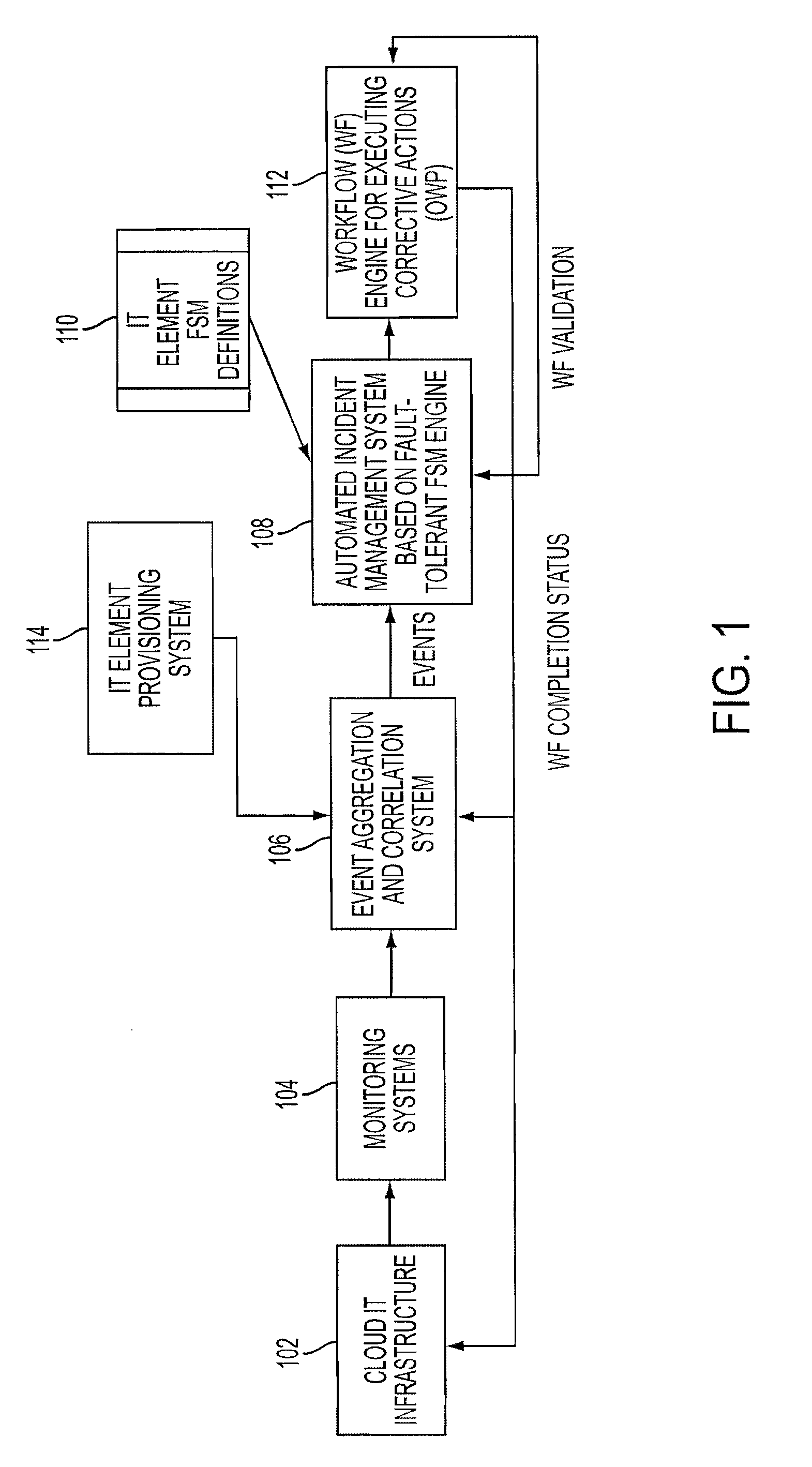
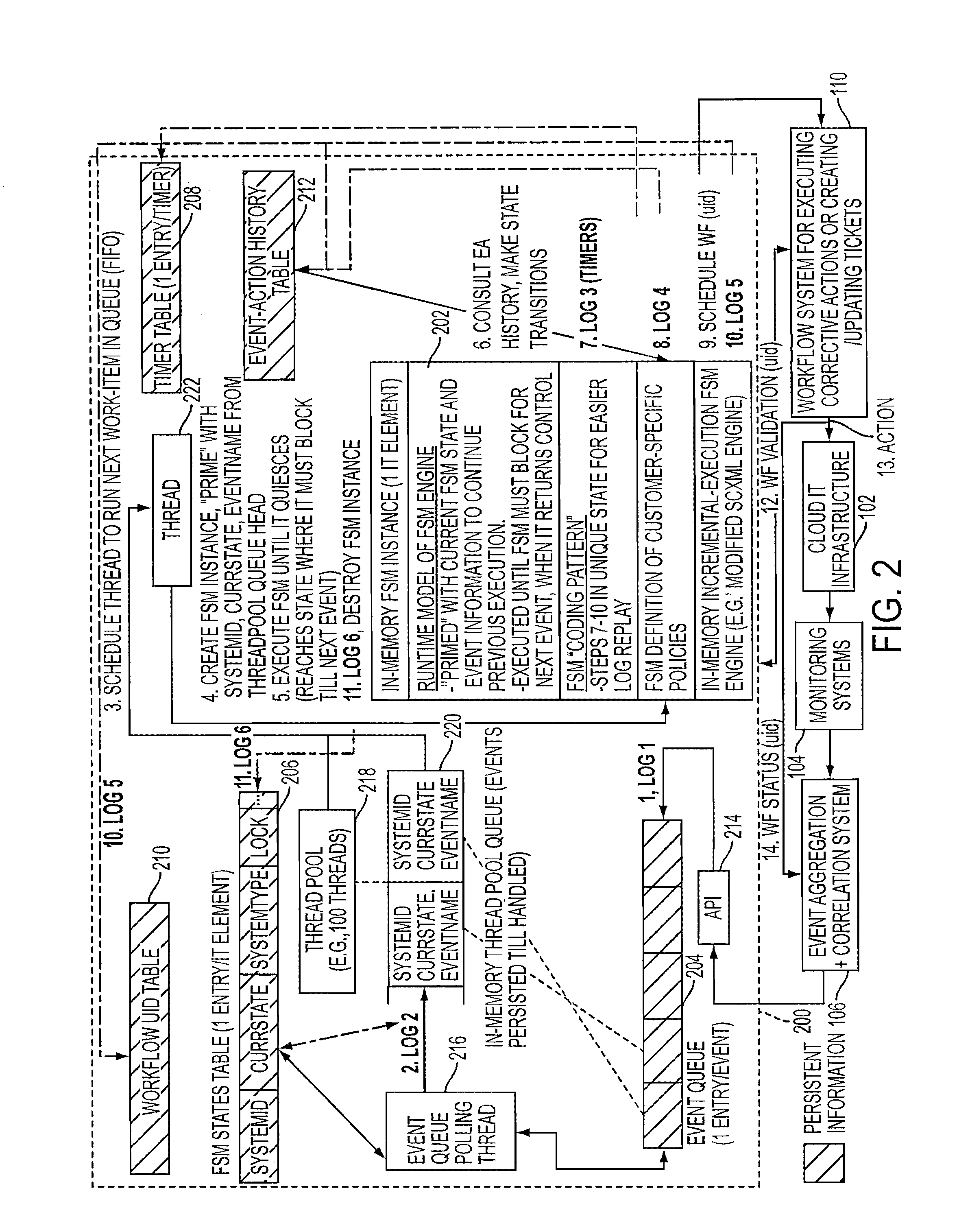
Adding scalability and fault tolerance to generic finite state machine frameworks for use in automated incident management of cloud computing infrastructures
InactiveUS20120151272A1Program controlRedundant operation error correctionFault toleranceExtensibility
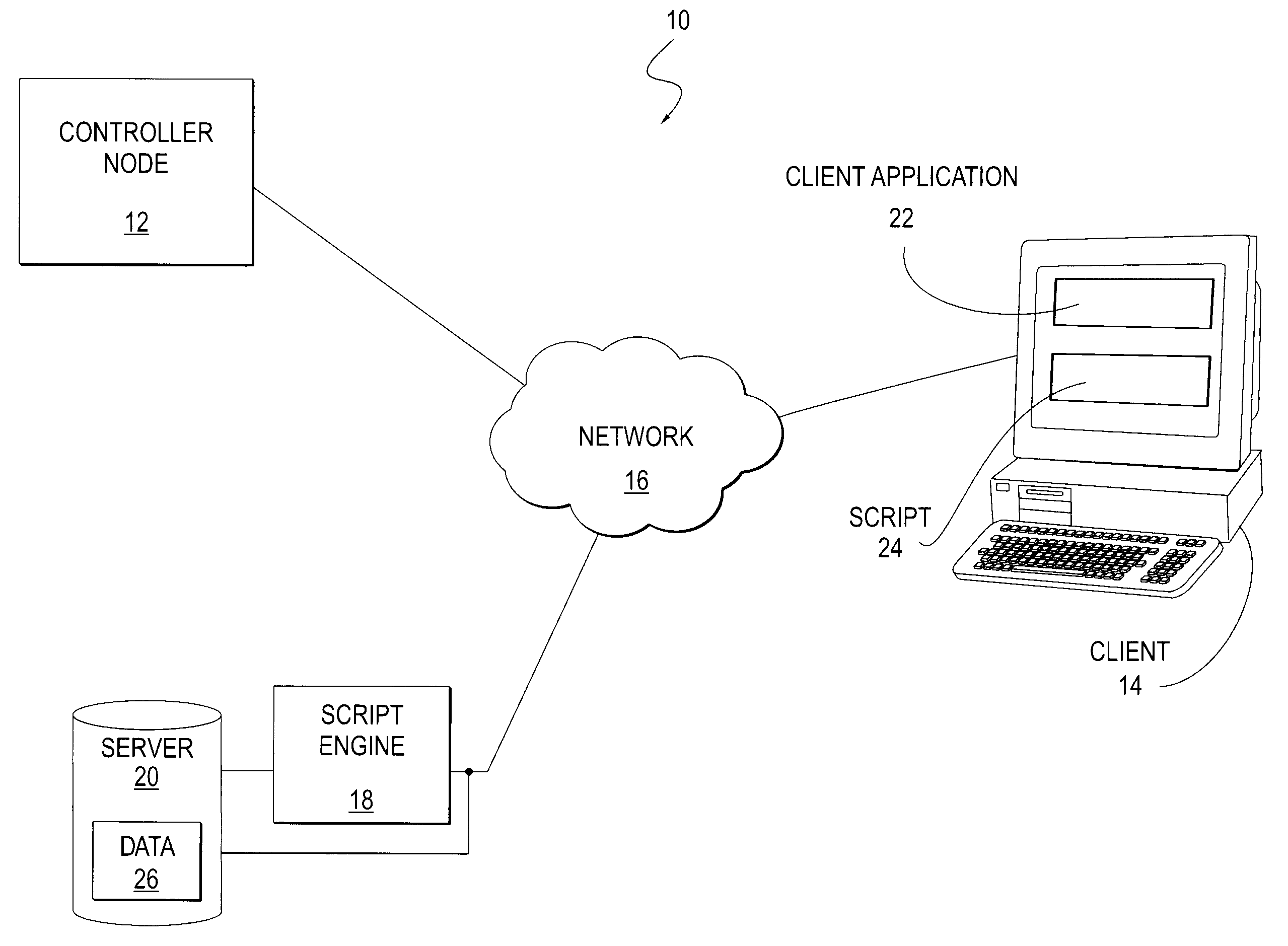
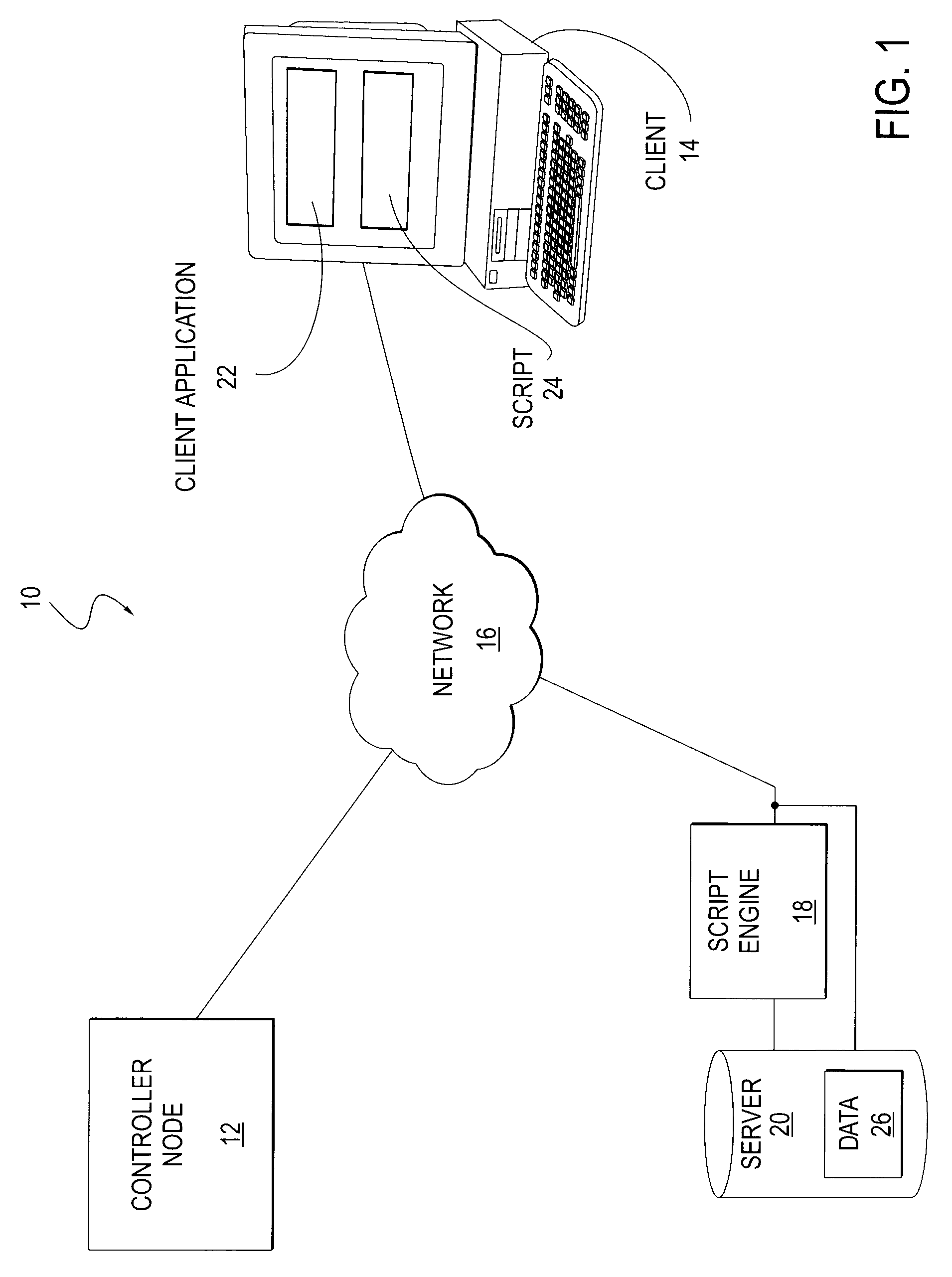
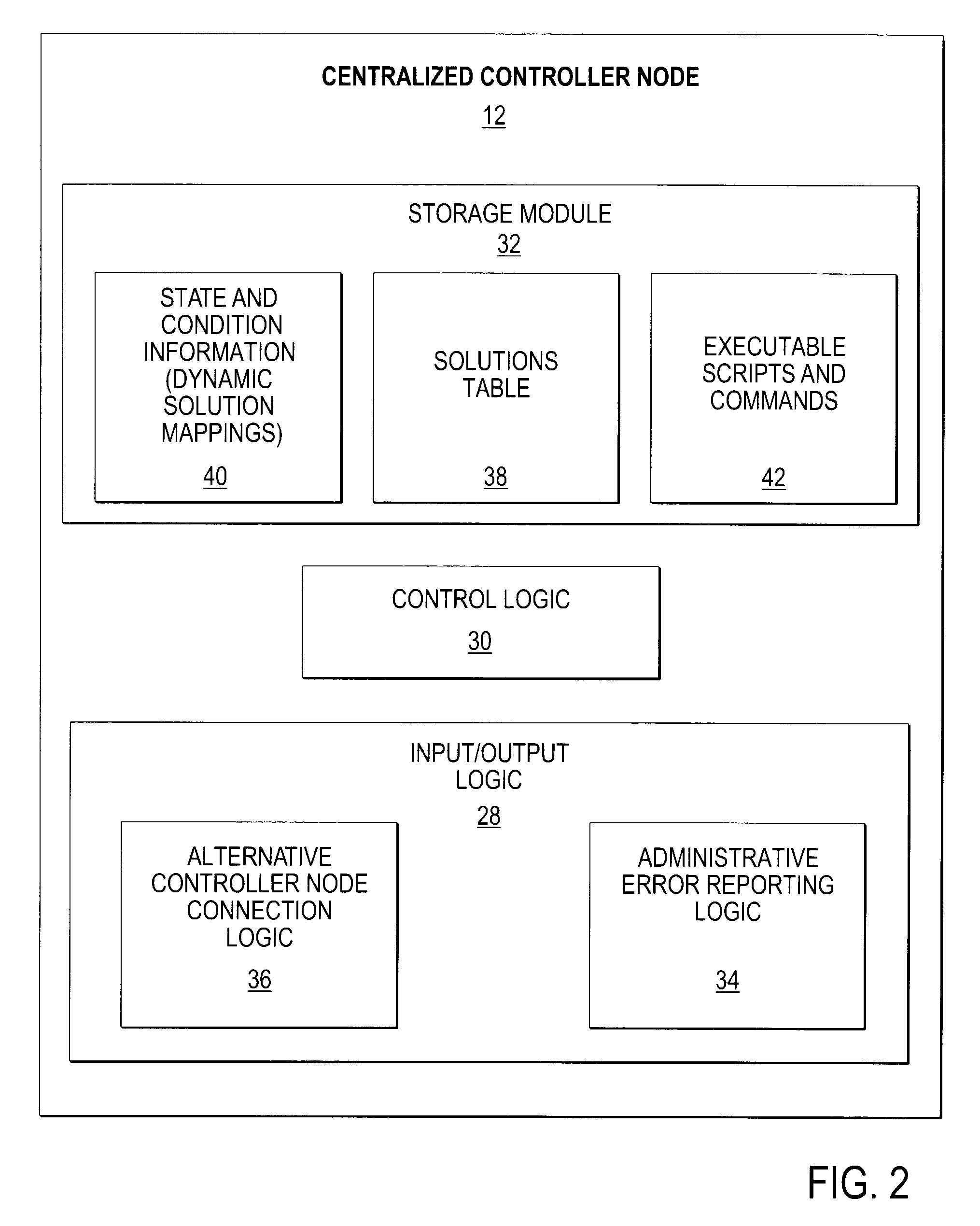
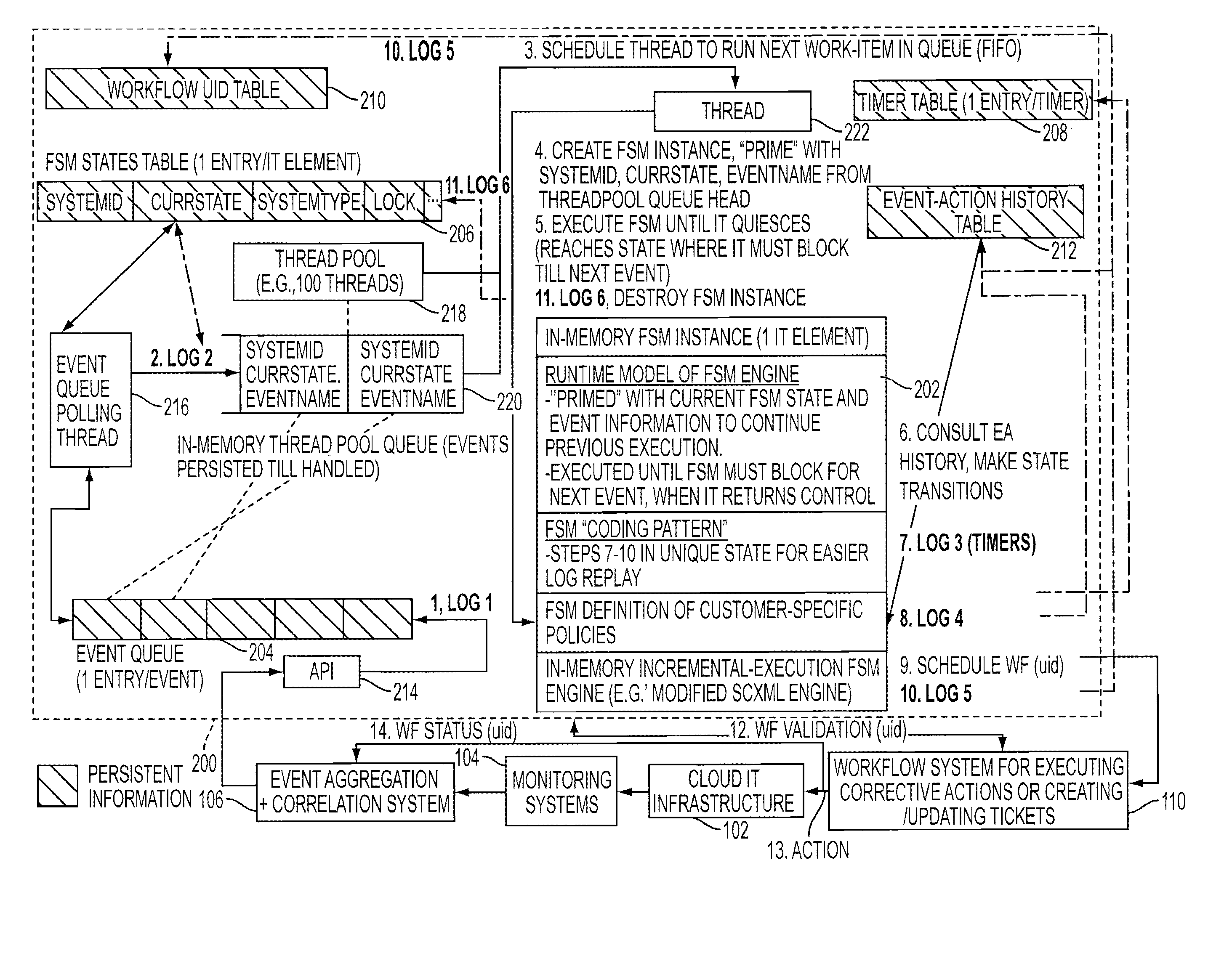
A scalable and fault tolerant finite state machine engine, for example, for use in an automated incident management system, logs or records data in persistent storage at different points or levels during various internal processing of an event associated with an information technology element, and action taken associated with the event, by executing a finite state machine instance that encodes policies for handling incidents on such types of information technology elements. In the event that the finite state machine engine is shutdown during processing, the finite state machine engine is able to pick up from where it left off when it was shutdown, for each abnormally terminated finite state machine instance, by using the data logged in the persistent storage and determining a point of processing from where it should continue its execution.
Owner:GLOBALFOUNDRIES US INC
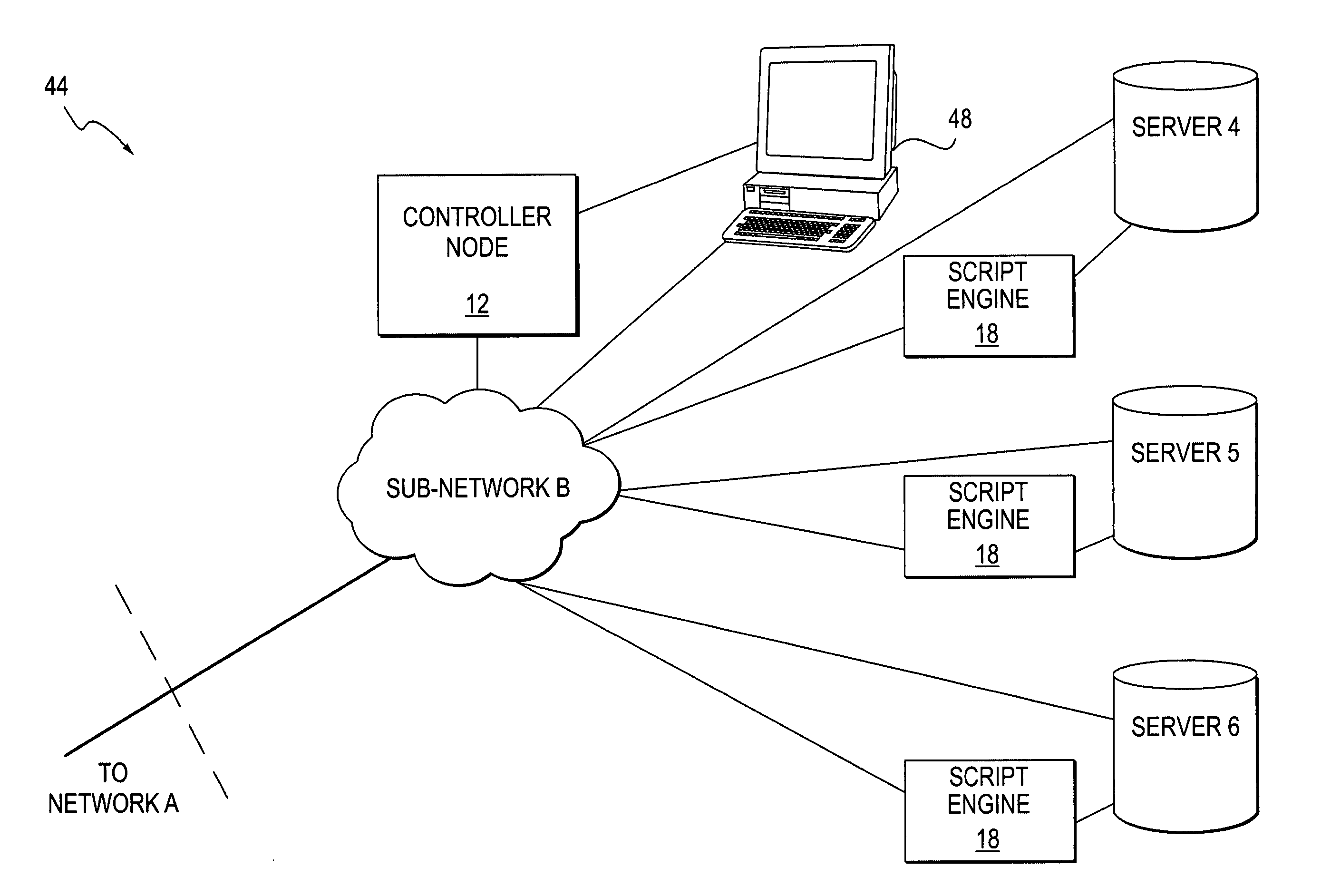
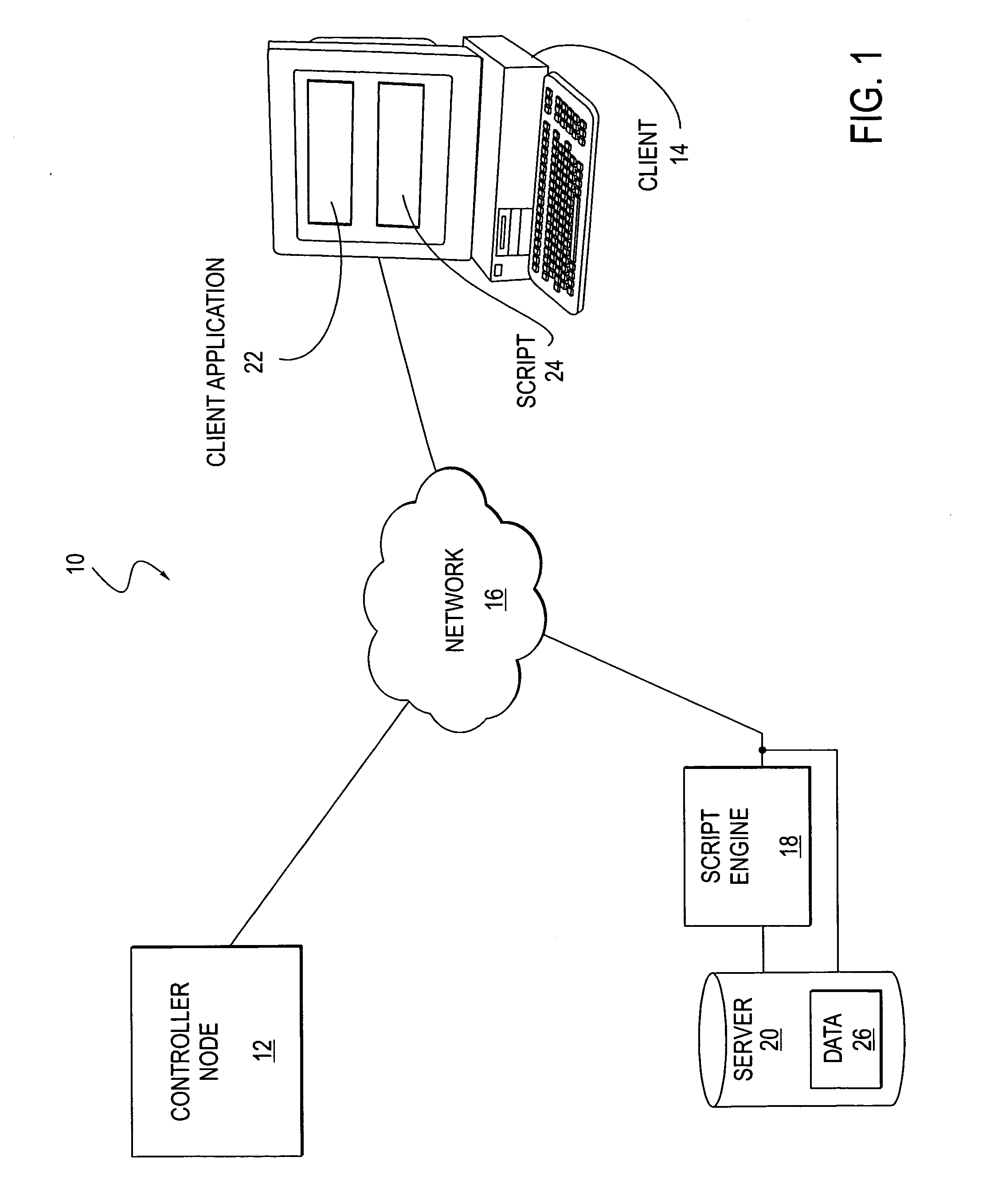
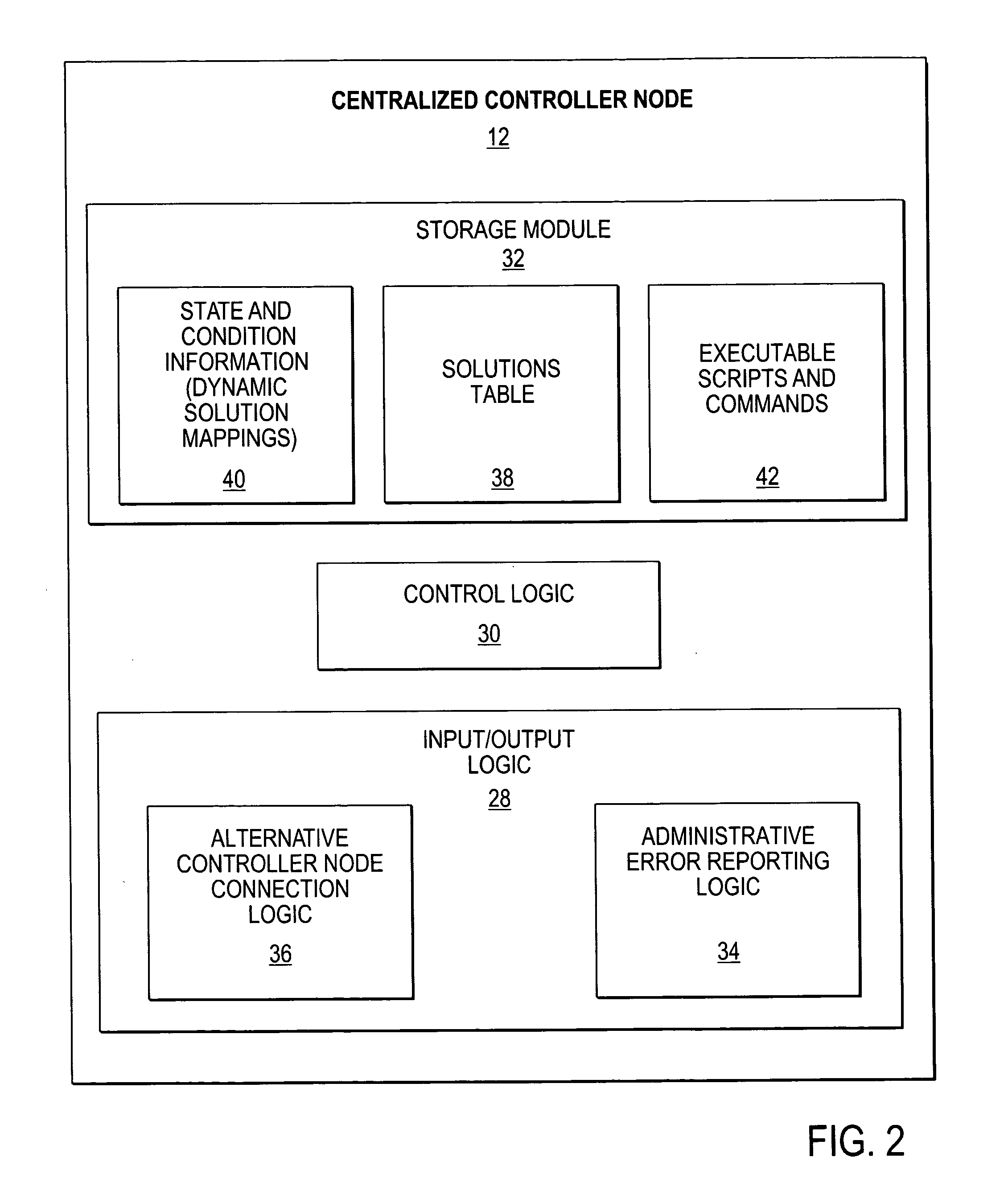
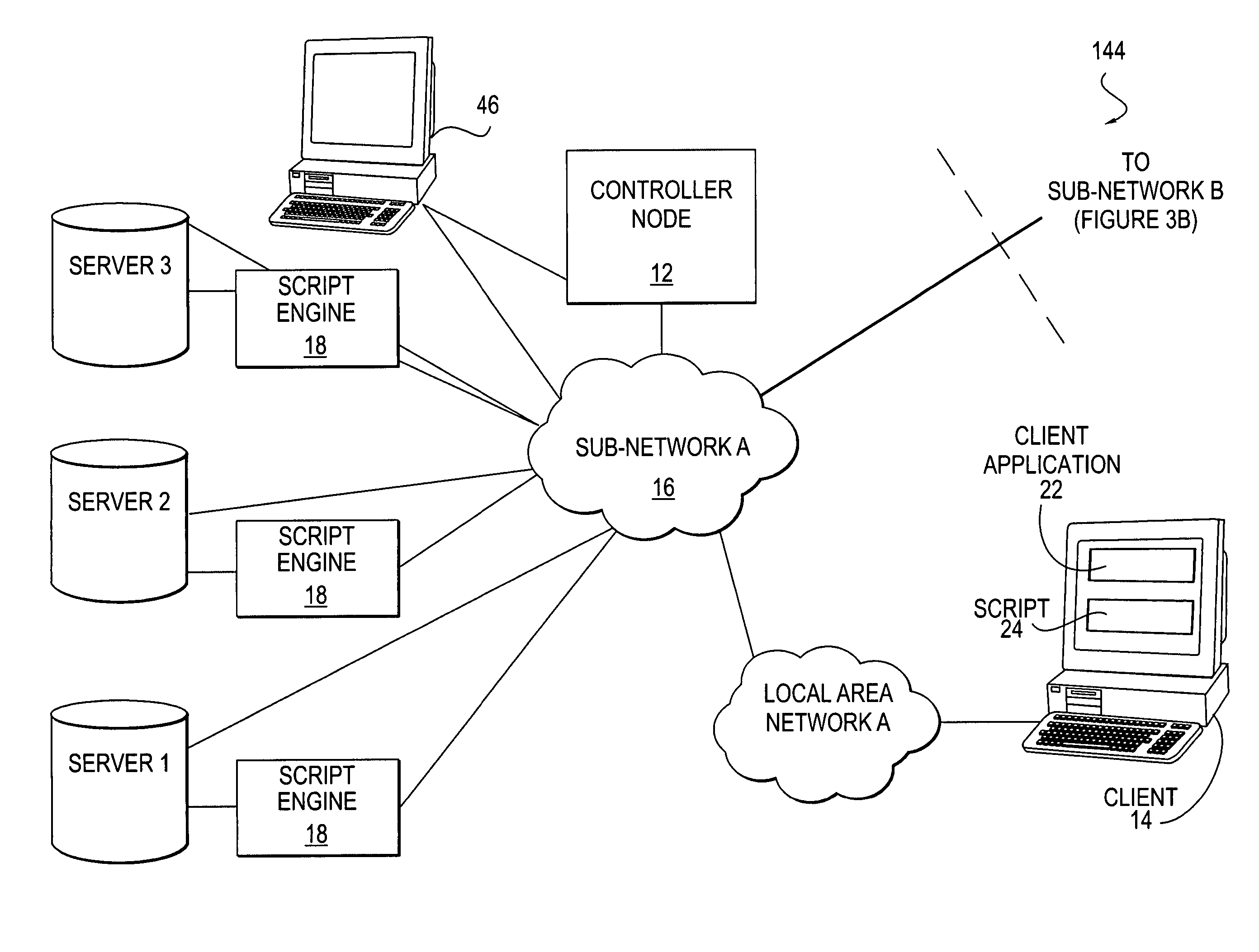
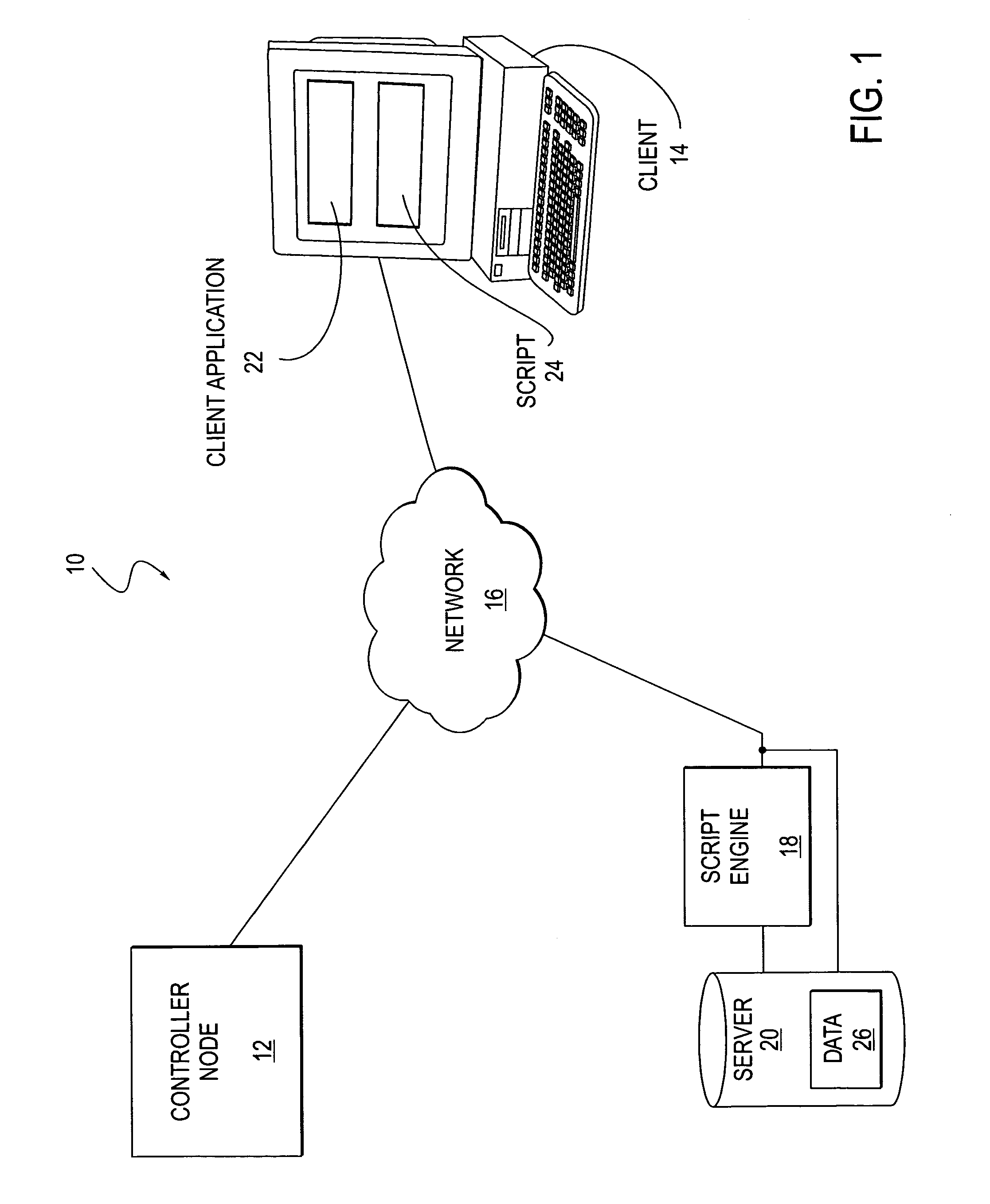
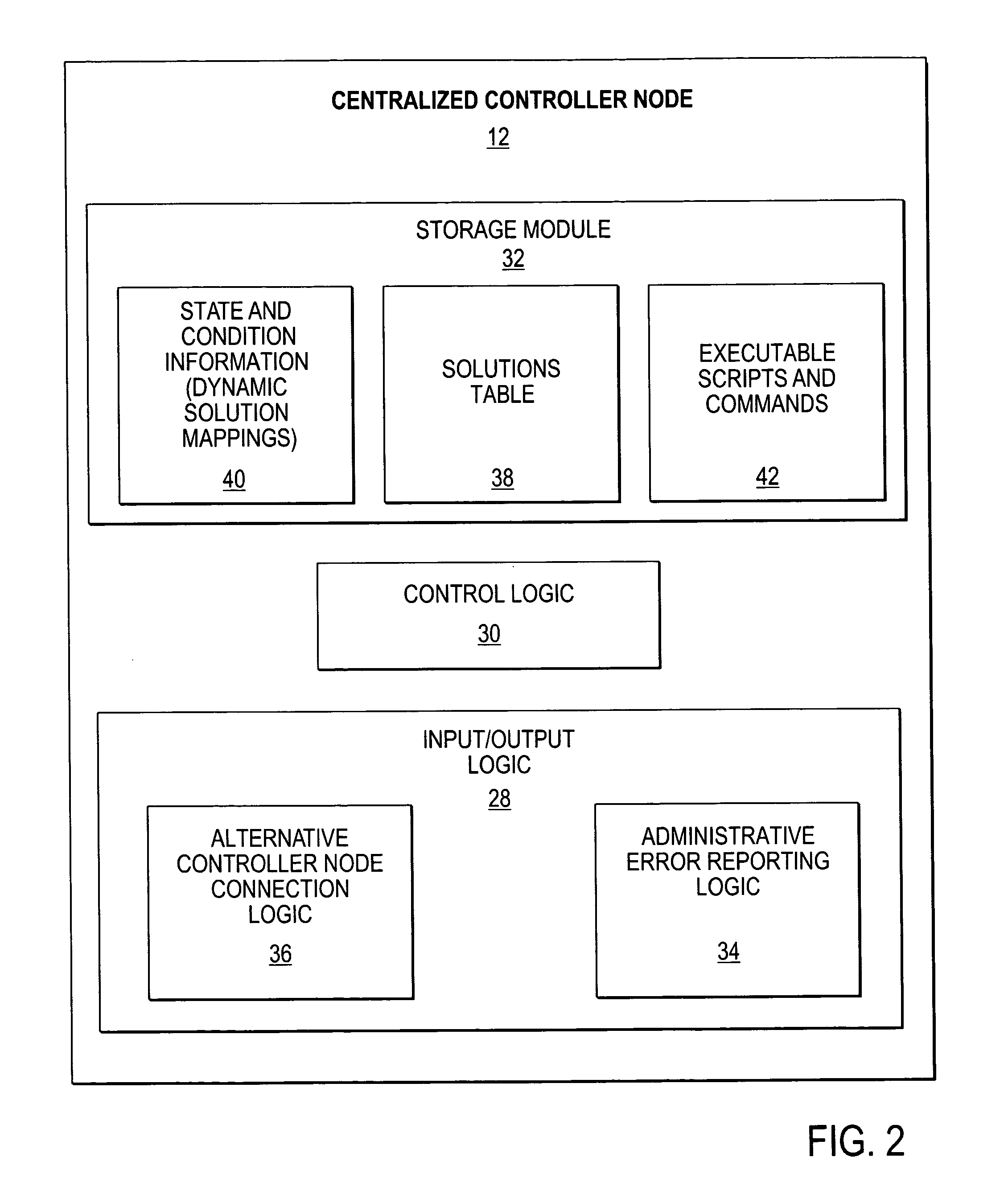
Method and system for intelligent and adaptive exception handling
A method and system for handling errors and exceptions in an ERP environment are disclosed. According to one aspect of the present invention, a condition or event causes a script-engine associated with a particular ERP server to generate an error message. The error message is communicated to a centralized controller-node. The centralized controller-node analyzes the message and determines the best course of action for handling an error or exception related to the error message. Based on the controller node's analysis, the controller node communicates a response message, thereby enabling the process that caused the error to continue without terminating abnormally.
Owner:SAP AG
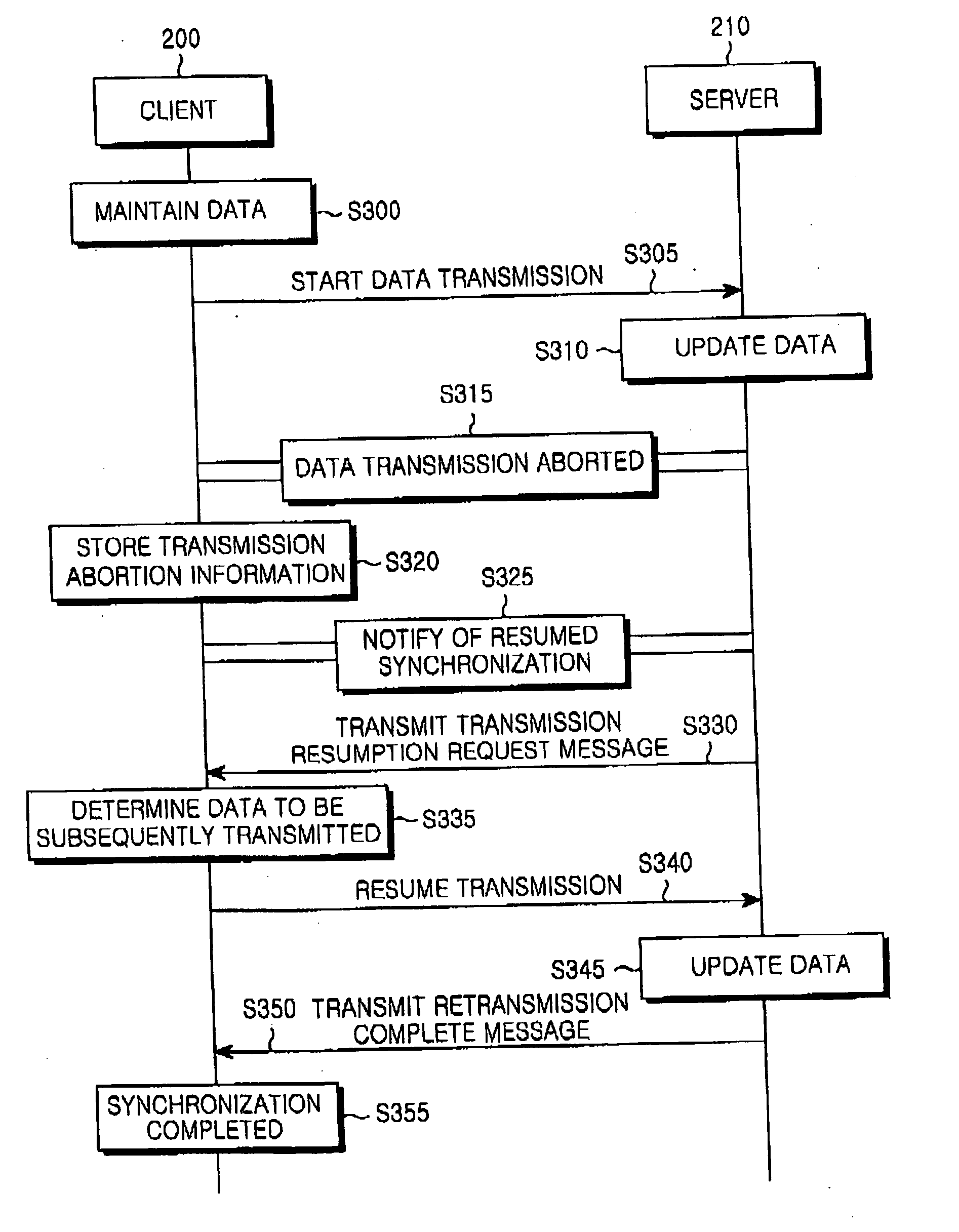
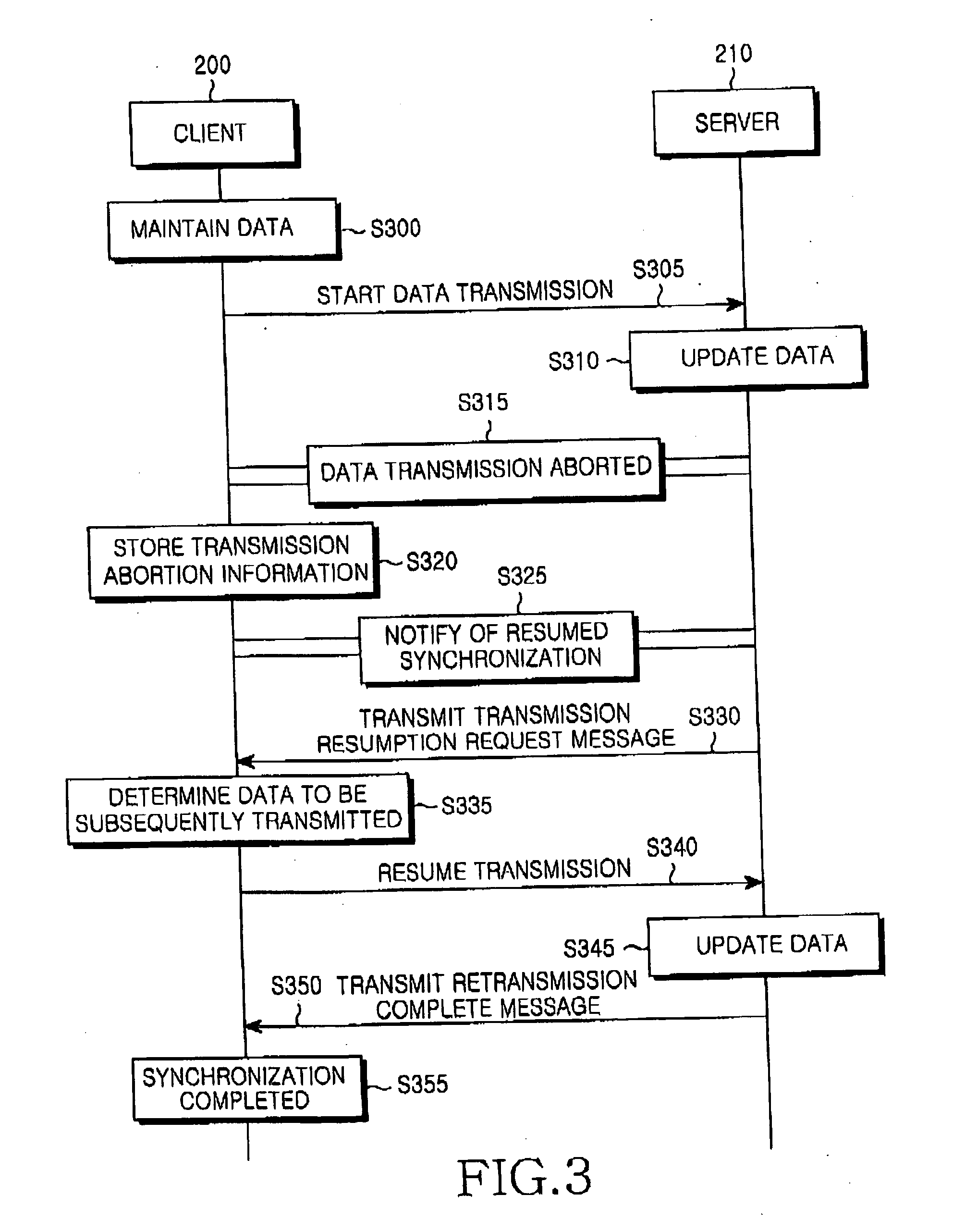
Method and system for transmitting data for data synchronization between server and client when data synchronization session was abnormally terminated
InactiveUS20050235019A1Lighting elementsData switching by path configurationData synchronizationClient-side
Disclosed is a method for transmitting data for data synchronization between a server and a client. If a data synchronization session in a network is abnormally terminated, the client stores state information of data to be transmitted, which indicates states of the data at the time of the abnormal termination. The state information of the data makes it possible to resume the data transmission beginning with data items that were being transmitted at the time of the abnormal termination. Since one of the server and the client transmits only data that has not been received by the other, it is possible to decrease the time necessary to complete the data synchronization and also to reduce a wasteful, unnecessary transaction when synchronization of a large amount of data is performed.
Owner:SAMSUNG ELECTRONICS CO LTD
Nested Recovery Scope Management For Stateless Recovery Agents
InactiveUS20060259526A1Easy to useData processing applicationsDigital data processing detailsInitComputer science
Owner:SERVICENOW INC +1
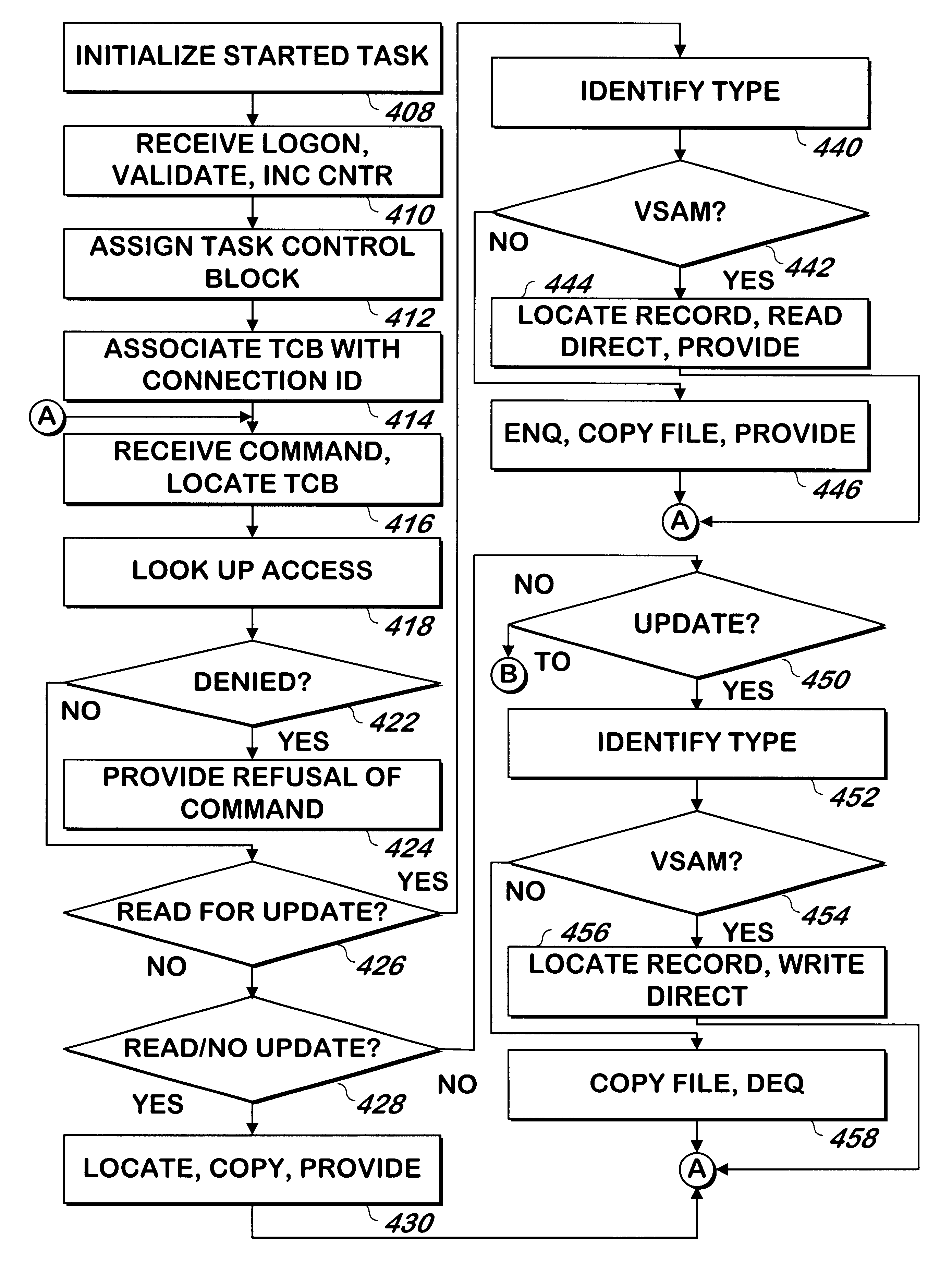
System and method for serving host computer files to one or more client computer systems
InactiveUS6253236B1Unauthorized memory use protectionComputer security arrangementsComputerized systemClient-side
A system and method allows a host computer to operate as a server in a client-server arrangement in response to requests from client computer systems. The system and computer program product performs reads, reads for update, update and deletes on some or all records in a file, depending on the type of file. Record or file locking is provided when applicable. Security is provided at the file level. Abnormal ends of communication with the client computer system are detected to allow resources and record or file locks to be freed in such event. A counter is incremented at the time a client computer system logs into the host computer system to enforce limits on the number of concurrent users, and ordinary log off as well as abnormal ends of communication decrement the counter to maintain its accuracy.
Owner:SERENA SOFTWARE
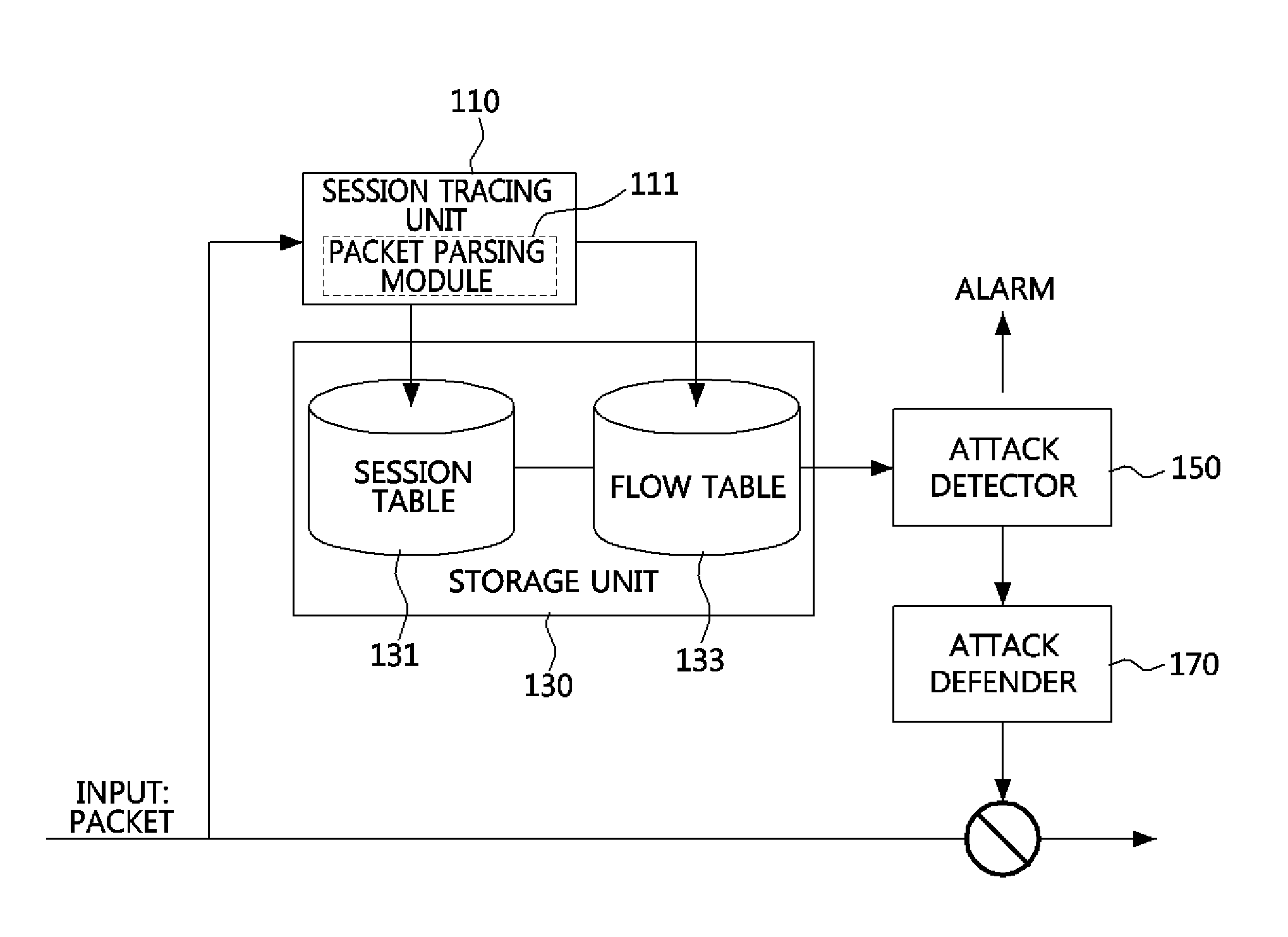
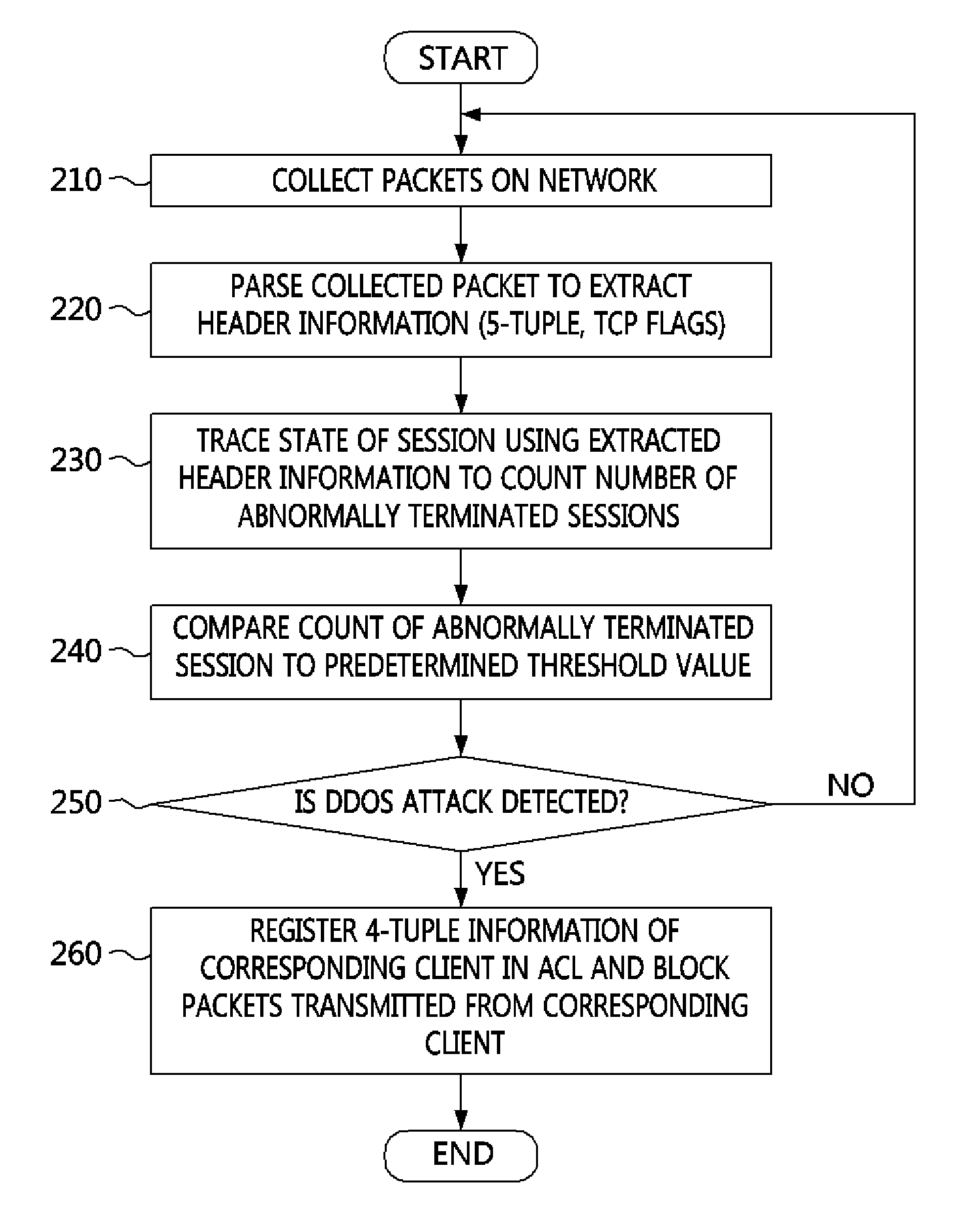
Method and apparatus for defending distributed denial-of-service (DDOS) attack through abnormally terminated session
InactiveUS20130074183A1Reduce the amount requiredReduce rateMemory loss protectionData taking preventionFalse positive rateComputer security
There are provided a method and apparatus for defending a Distributed Denial-of-Service (DDoS) attack through abnormally terminated sessions. The DDoS attack defending apparatus includes: a session tracing unit configured to parse collected packets, to extract header information from the collected packets, to trace one or more abnormally terminated sessions corresponding to one of pre-defined abnormally terminated session cases, based on the header information, and then to count the number of the abnormally terminated sessions; and an attack detector configured to compare the number of the abnormally terminated sessions to a predetermined threshold value, and to determine whether a DDoS attack has occurred, according to the results of the comparison. Therefore, it is possible to significantly reduce a false-positive rate of detection of a DDoS attack and the amount of computation for detection of a DDoS attack.
Owner:ELECTRONICS & TELECOMM RES INST
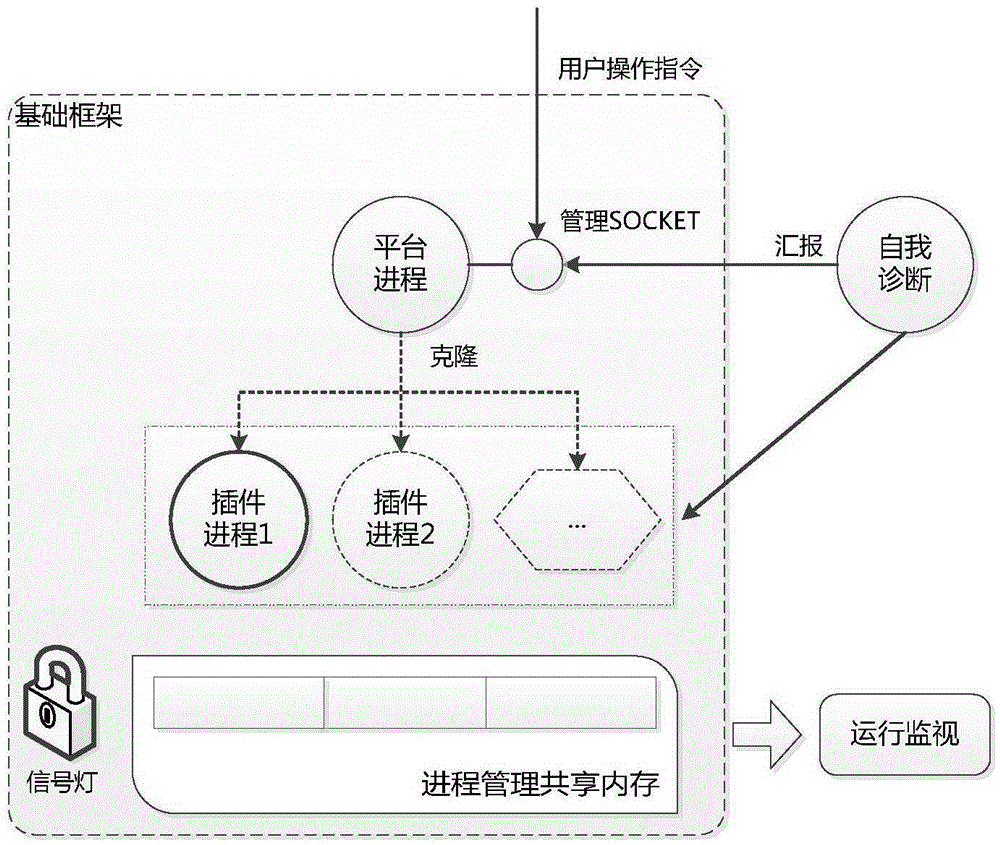
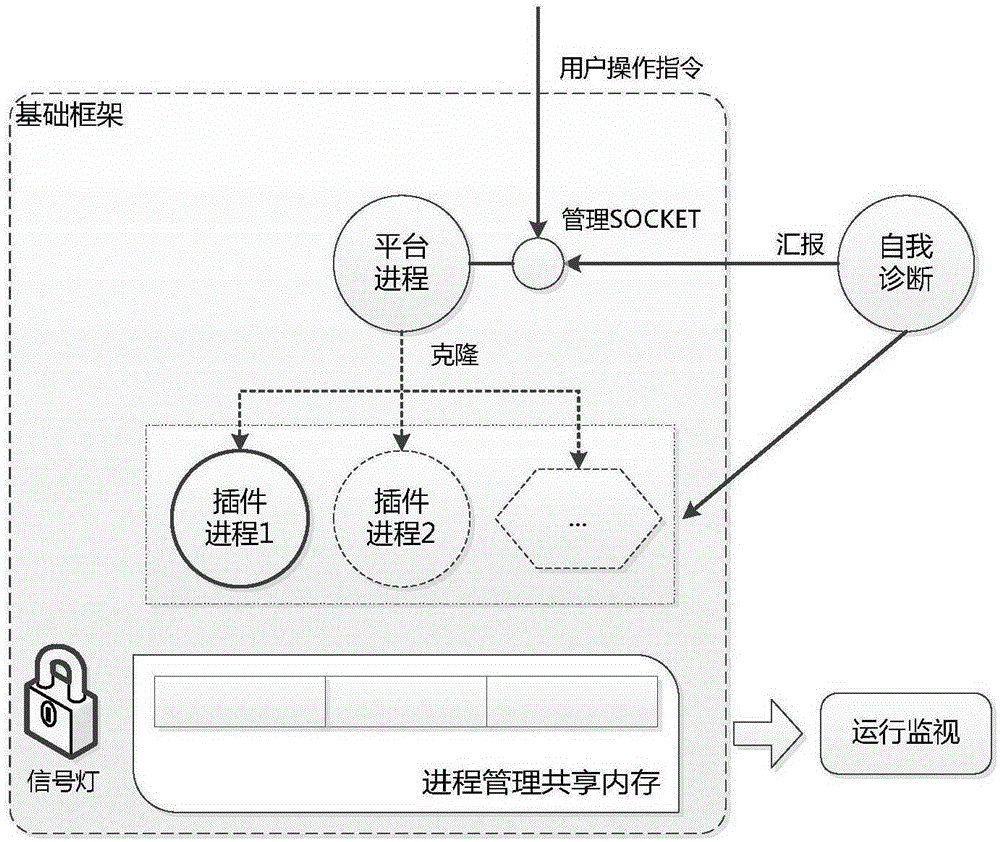
Universal SOCKET communication and process management platform applied to multiple scenes and method
ActiveCN105357266AImprove development efficiencyLower development thresholdData switching networksMessage queueAsynchronous communication
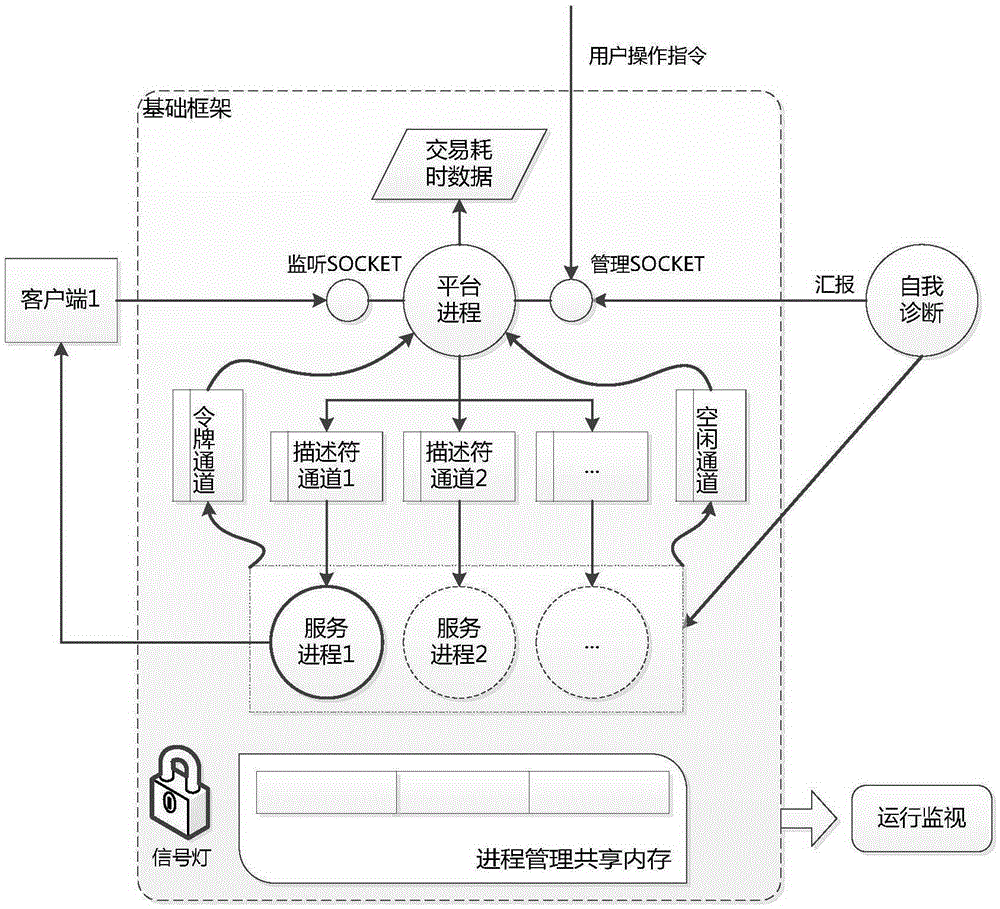
The invention discloses a universal SOCKET communication and process management platform applied to multiple scenes and a method. The universal SOCKET communication and process management platform is applied to a SOCKET service scene and a resident process management scene; a SOCKET service is operated in the SOCKET service scene; and a background application in the form of a plug-in is operated in the resident process management scene. Each scene comprises the following processes: operating a base framework: creating a set of processes for realizing service logic processing and waiting and responding to a user operation instruction and a report of a diagnosis process; and operating the diagnosis process: detecting the operation states of the created processes, and automatically restarting a service process which is abnormally stopped or died, such that continuous and steady operation of the whole platform can be ensured. In combination with the SOCKET service scene and the resident process management scene, the SOCKET service in the asynchronous mode can be realized; due to two platforms including an asynchronous communication platform and a service processing platform, complete functions are realized; the asynchronous communication platform and the service processing platform exchange data with a SOCKET communication mechanism in a UNIX domain through a message queue; therefore, the processing capacity is flexibly expanded; and the transaction throughput is improved.
Owner:MASSCLOUDS
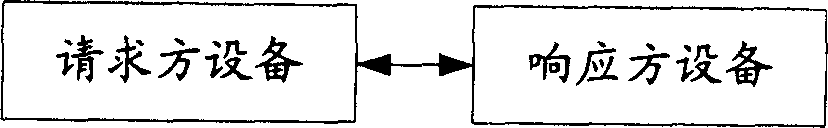
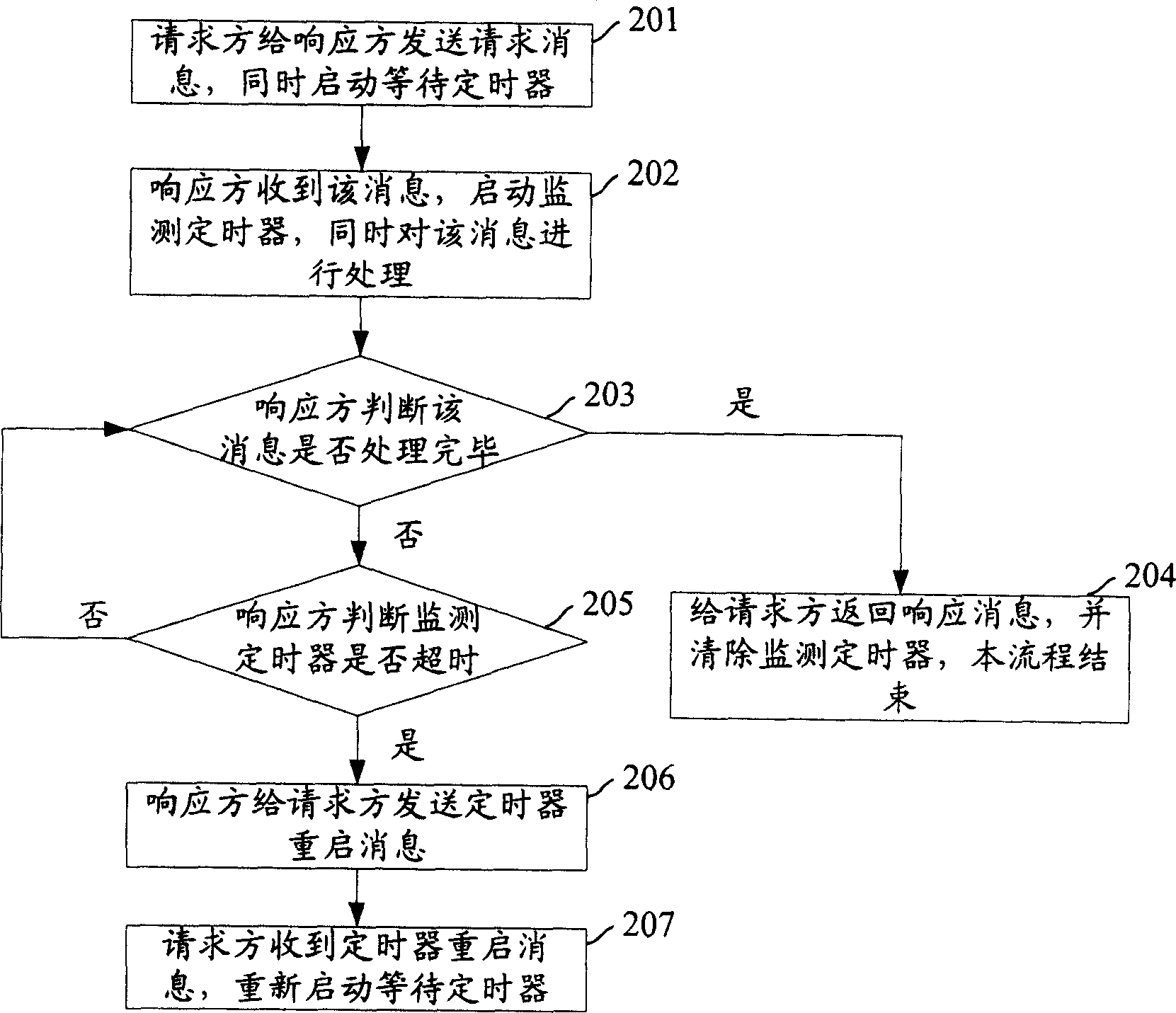
Timer control method and system
InactiveCN1859529AAvoid abnormal terminationSave resourcesTelephonic communicationTelecommunicationsControl system
The present invention discloses timer control method. It contains request side transmitting request message to responding side, starting up waiting timer; responding side receiving said message and starting up monitoring timer, when monitoring timer overtime but said message not having ended process, transmitting restart timer message to request side, request receiving said message and restarting waiting timer. The present invention also discloses a timer control system, which includes transmitting request message, request side equipment, and responding side equipment. The present invention avoids service abnormal end.
Owner:HUAWEI TECH CO LTD
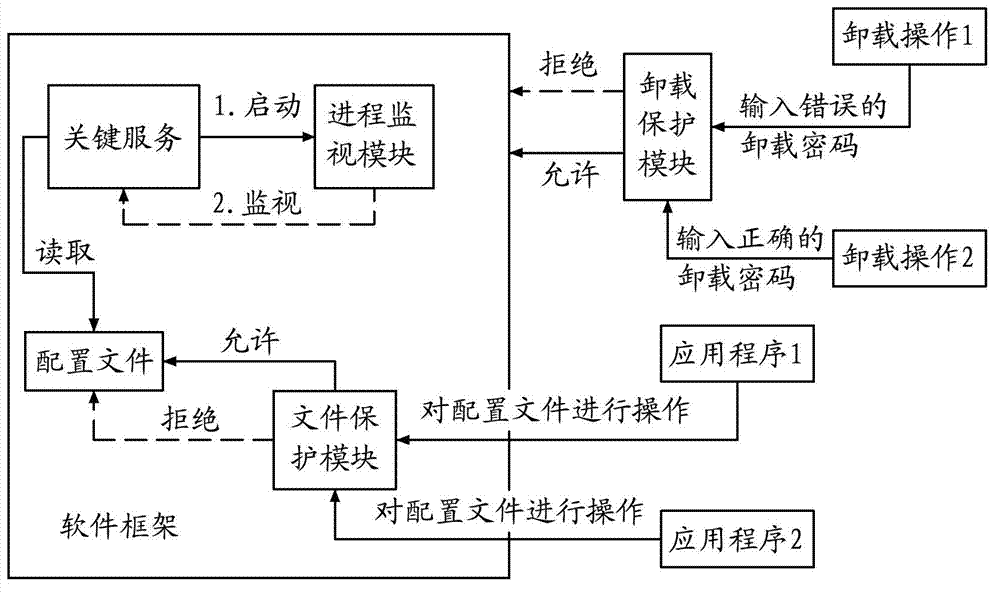
Running protection method for computer software product
InactiveCN102880817ARealize self-starting operationLower the threshold of understandingProgram/content distribution protectionPasswordUser input
The invention discloses a running protection method for a computer software product. The method comprises the following steps of: starting key service, injecting a process monitoring module in a system process when the key service is started for the first time, running the process monitoring module in a system process space, periodically checking whether the key service runs or not by using the process monitoring module, and restarting the key service if the key service is abnormally stopped; filtering file operation in a key directory according to configuration by using a file protection module, and if an application program outside the key directory performs deletion operation on the file in the key directory, stopping the operation; if a file operation process is in the key directory, allowing the file operation of the file operation process; and when a user executes unloading operation, judging whether the actual software unloading operation of the user is allowed or not according to whether an unloading password input by the user is correct or not by using an unloading protection module. According to the running protection method for the computer software product, a full software self-protection function can be realized.
Owner:FUJIAN CENTM INFORMATION
Method and system for intelligent and adaptive exception handling
A method and system for handling errors and exceptions in an ERP environment are disclosed. According to one aspect of the present invention, a condition or event causes a script-engine associated with a particular ERP server to generate an error message. The error message is communicated to a centralized controller-node. The centralized controller-node analyzes the message and determines the best course of action for handling an error or exception related to the error message. Based on the controller node's analysis, the controller node communicates a response message, thereby enabling the process that caused the error to continue without terminating abnormally.
Owner:SAP AG
Adding scalability and fault tolerance to generic finite state machine frameworks for use in automated incident management of cloud computing infrastructures
InactiveUS20120331342A1Program controlRedundant operation error correctionFault toleranceExtensibility
A scalable and fault tolerant finite state machine engine, for example, for use in an automated incident management system, logs or records data in persistent storage at different points or levels during various internal processing of an event associated with an information technology element, and action taken associated with the event, by executing a finite state machine instance that encodes policies for handling incidents on such types of information technology elements. In the event that the finite state machine engine is shutdown during processing, the finite state machine engine is able to pick up from where it left off when it was shutdown, for each abnormally terminated finite state machine instance, by using the data logged in the persistent storage and determining a point of processing from where it should continue its execution.
Owner:GLOBALFOUNDRIES INC
Method and system for intelligent and adaptive exception handling
A method and system for handling errors and exceptions in an ERP environment are disclosed. According to one aspect of the present invention, a condition or event causes a script-engine associated with a particular ERP server to generate an error message. The error message is communicated to a centralized controller-node. The centralized controller-node analyzes the message and determines the best course of action for handling an error or exception related to the error message. Based on the controller node's analysis, the controller node communicates a response message, thereby enabling the process that caused the error to continue without terminating abnormally.
Owner:SAP AG
Rotorcraft early-warning device and method
PendingCN105203999AMonitor trends in real timeAccurate identificationPosition fixationSound sourcesTime delays
A rotorcraft early-warning device comprises a plurality of sound processing modules (1) and a positioning processing module (2); abnormal end point detection modules (5) are used for judging one of a sound short time average amplitude and a sound short time zero-crossing rate which exceed a threshold as abnormal sounds; the positioning processing module (2) comprises a time delay calculating unit (9) used for calculating a time delay difference that signals of the same sound source reach two sound processing modules (1), an angle calculating unit (10) used for determining a sound source directional angle according to the time delay difference and a geometrical relationship among intervals of the sound processing modules and a sound source positioning unit (11) used for positioning a sound source through combination of multiple groups of sound processing modules; the sound source positioning unit (11) is used for clustering according to an azimuth angle theta, selecting a sound source azimuth angle theta judged by two groups of sound processing modules with highest noise power after clustering as a final sound source direction, displaying the sound source position on an electronic map and giving an alarm.
Owner:高域(北京)智能科技研究院有限公司
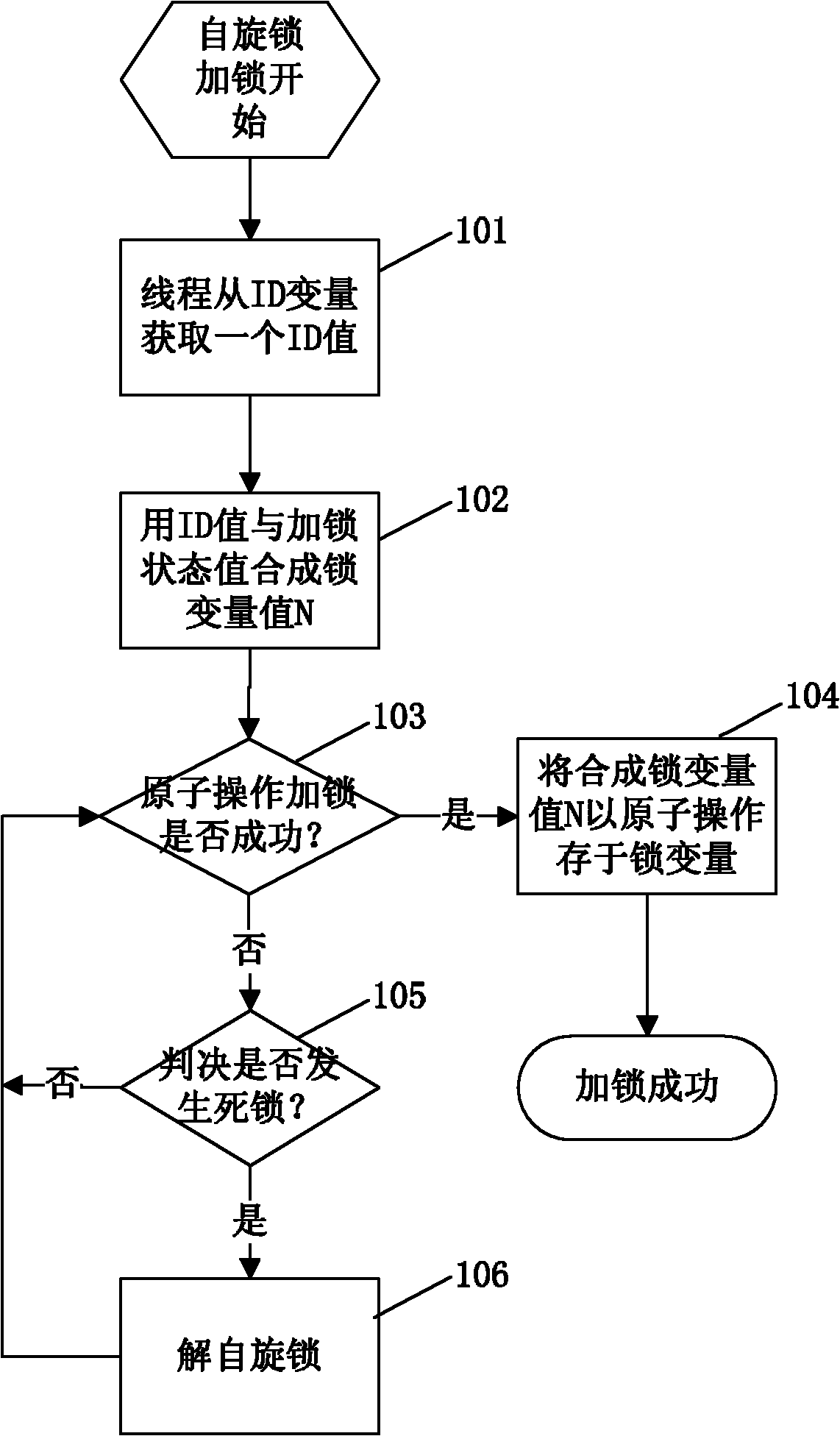
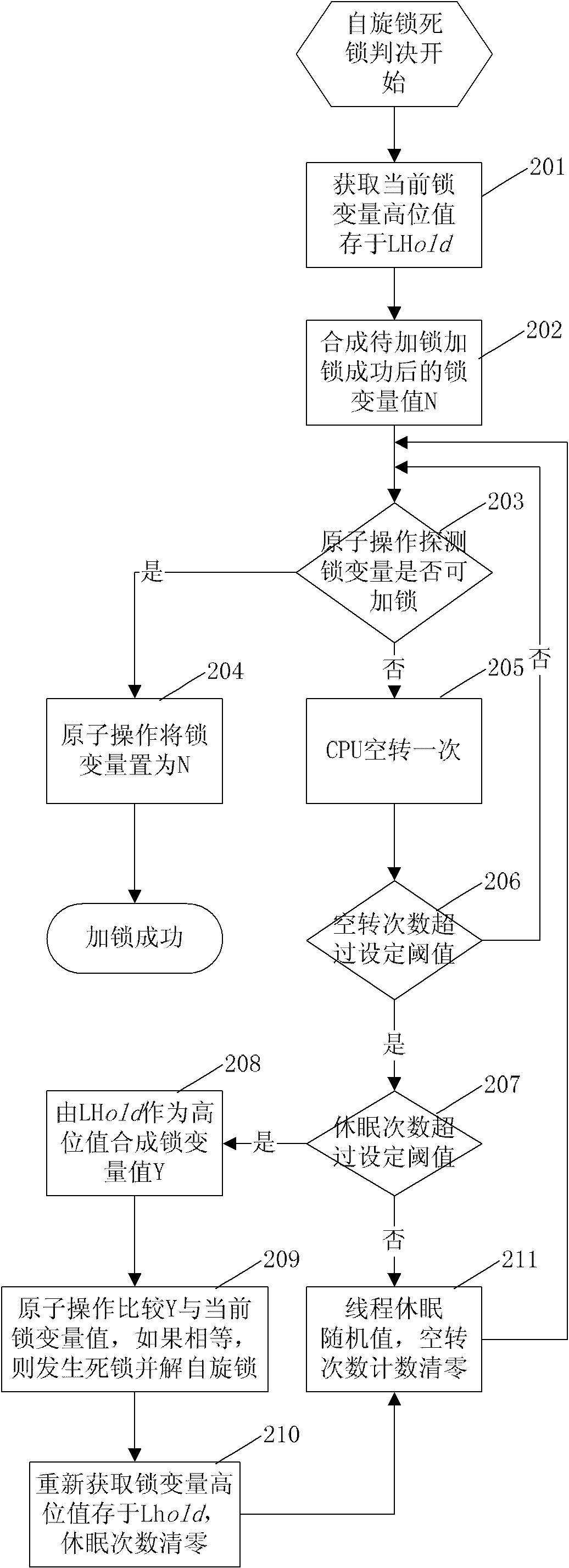
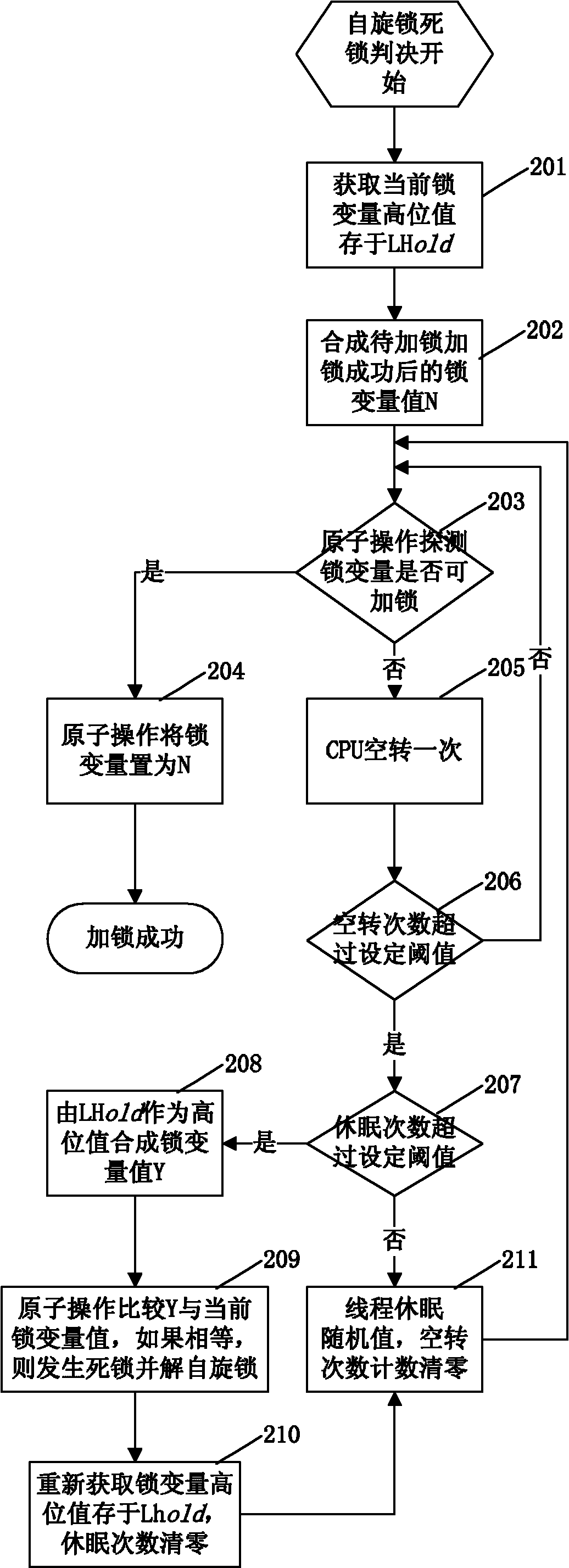
Method for implementing spin lock in database
InactiveCN102129391AAvoid deadlock situationsProtection operationMultiprogramming arrangementsSpinlockComputer science
The invention discloses a method for implementing a spin lock in a database. The method for implementing the spin lock in the database is characterized by comprising the following steps of: storing two global variables, namely a spin lock variable and an ID variable in a shared memory, and initializing the two variables as 0 when a system is initialized; and memorizing a current spin lock holdingthread by using a high storage value of spin lock variables, and implementing automatic unlocking of the spin lock according to the storage value when the lock holding thread is abnormal and exits tocause deadlock. By the method, possible deadlock when multiple tasks compete with the same spin lock is avoided, and the spin lock can protect the operation on a data structure for a long time and can process the deadlock problem caused by the abnormal end of a locking thread in the period by changing a locking flow and a deadlock judgment flow.
Owner:HUAZHONG UNIV OF SCI & TECH
Adding scalability and fault tolerance to generic finite state machine frameworks for use in automated incident management of cloud computing infrastructures
A scalable and fault tolerant finite state machine engine, for example, for use in an automated incident management system, logs or records data in persistent storage at different points or levels during various internal processing of an event associated with an information technology element, and action taken associated with the event, by executing a finite state machine instance that encodes policies for handling incidents on such types of information technology elements. In the event that the finite state machine engine is shutdown during processing, the finite state machine engine is able to pick up from where it left off when it was shutdown, for each abnormally terminated finite state machine instance, by using the data logged in the persistent storage and determining a point of processing from where it should continue its execution.
Owner:GLOBALFOUNDRIES INC
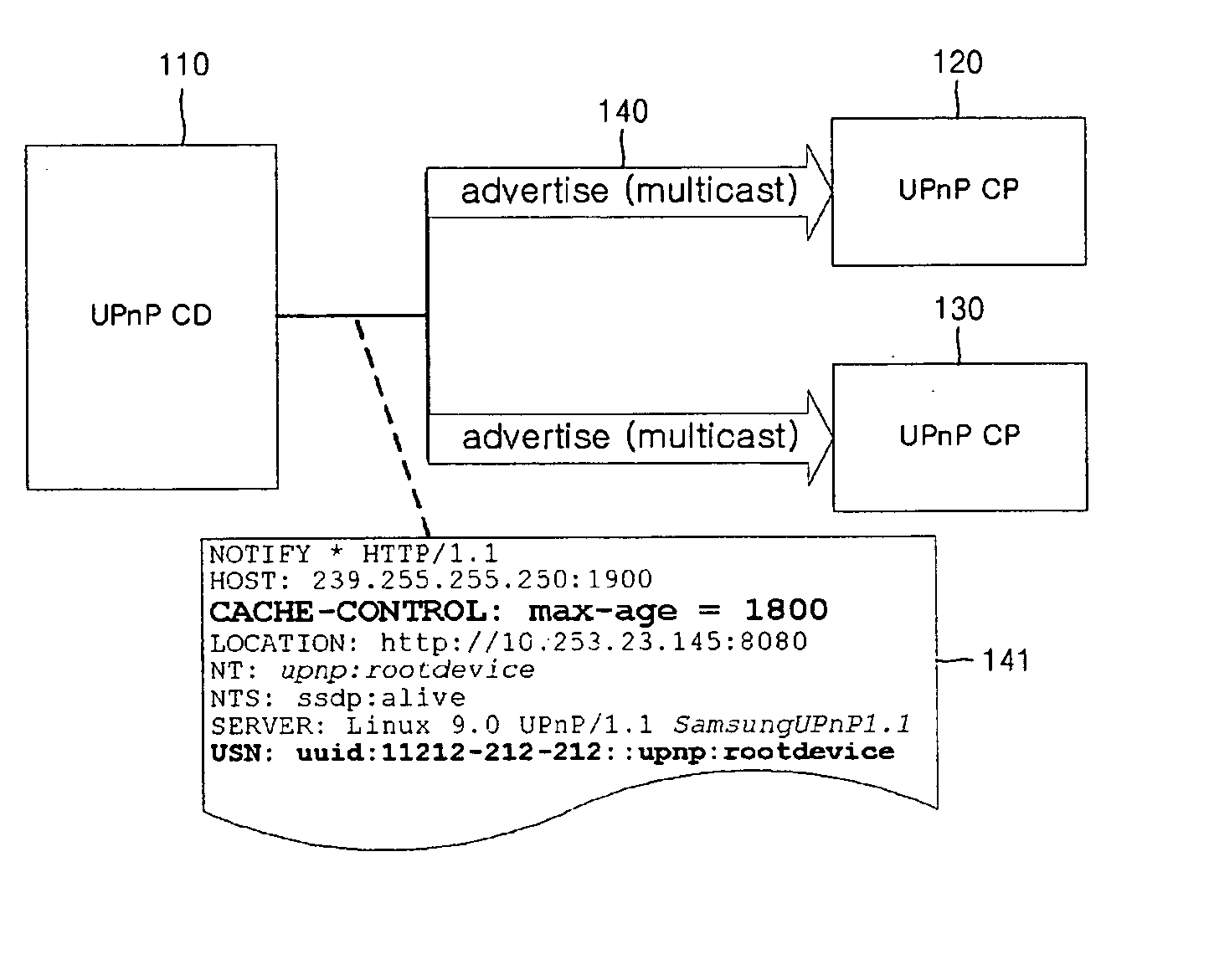
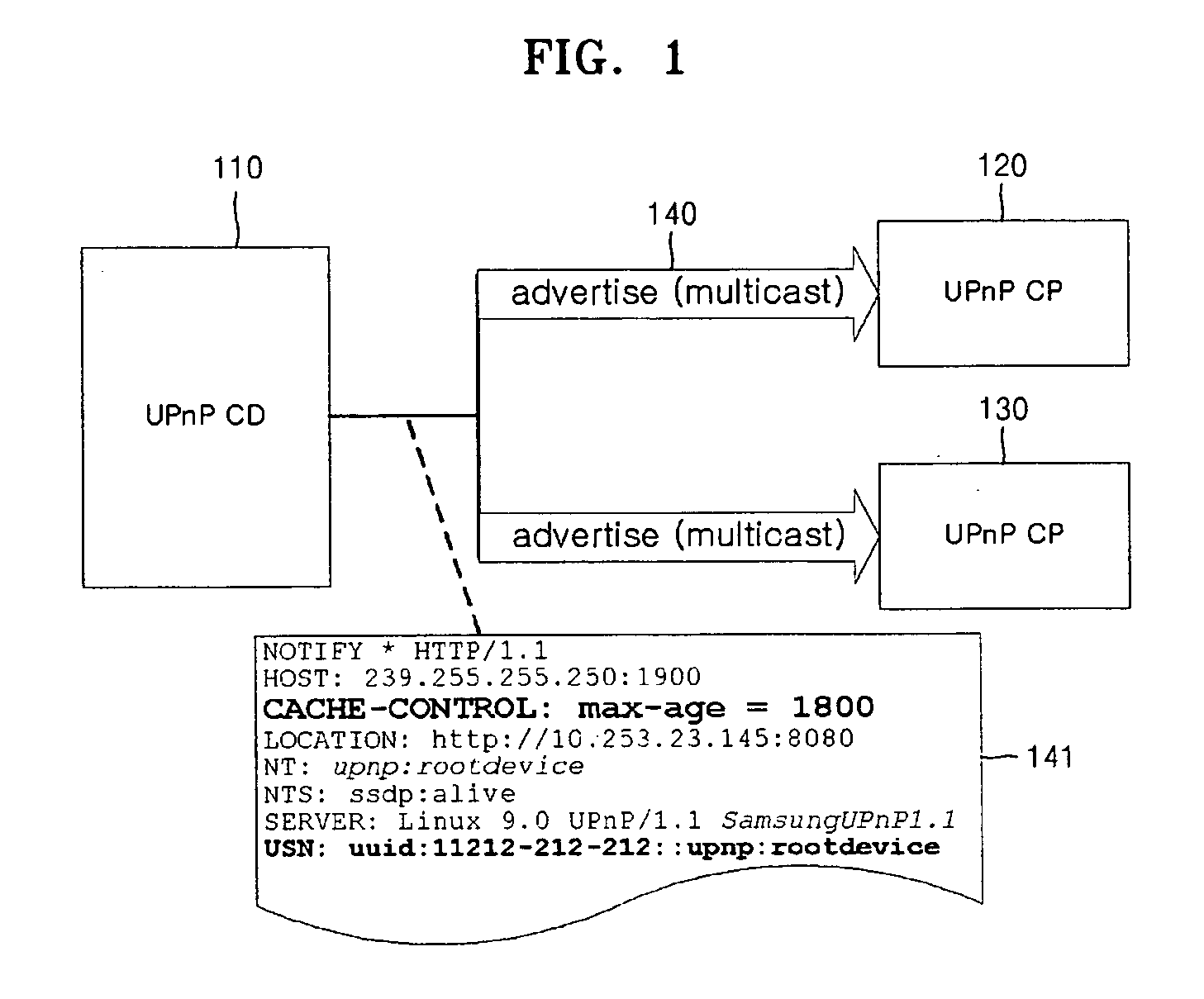
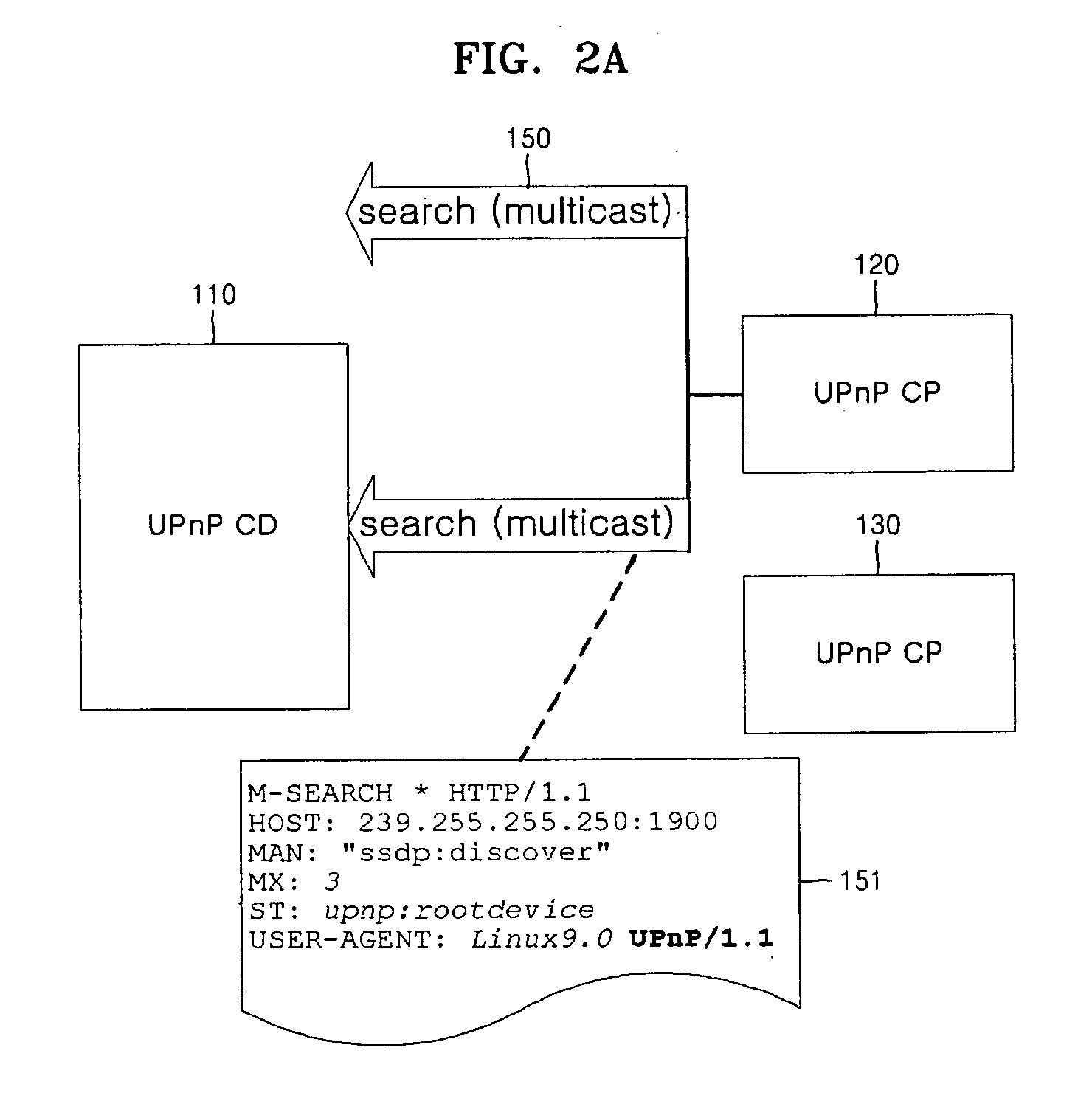
Method and apparatus for transmitting Byebye message when operation of controlled device in UPnP network is abnormally terminated
ActiveUS20070124449A1Special service provision for substationDigital computer detailsComputer compatibilityAbnormal end
A method and apparatus for transmitting a Byebye message when an operation of a controlled device is abnormally terminated are provided. A new field is added to discovery and Event messages defined in the UPnP standard. These messages are exchanged to allow a control point to monitor the controlled device. When the operation of the controlled device is abnormally terminated, the control point monitoring the operation of the controlled device determines whether or not the operation of the controlled device is abnormally terminated according to the presence or absence of a response to a Subscription Renewal message. The control point multicasts the Byebye message over the network instead of the controlled device abnormally terminated. It is possible to notify all control points in a network that the operation of the controlled device is abnormally terminated without increasing the load on the network and compatibility problems with existing UPnP devices.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and apparatus for defending distributed denial-of-service (DDoS) attack through abnormally terminated session
InactiveUS8966627B2Reduce the amount requiredReduce rateMemory loss protectionData taking preventionFalse positive rateComputer security
There are provided a method and apparatus for defending a Distributed Denial-of-Service (DDoS) attack through abnormally terminated sessions. The DDoS attack defending apparatus includes: a session tracing unit configured to parse collected packets, to extract header information from the collected packets, to trace one or more abnormally terminated sessions corresponding to one of pre-defined abnormally terminated session cases, based on the header information, and then to count the number of the abnormally terminated sessions; and an attack detector configured to compare the number of the abnormally terminated sessions to a predetermined threshold value, and to determine whether a DDoS attack has occurred, according to the results of the comparison. Therefore, it is possible to significantly reduce a false-positive rate of detection of a DDoS attack and the amount of computation for detection of a DDoS attack.
Owner:ELECTRONICS & TELECOMM RES INST
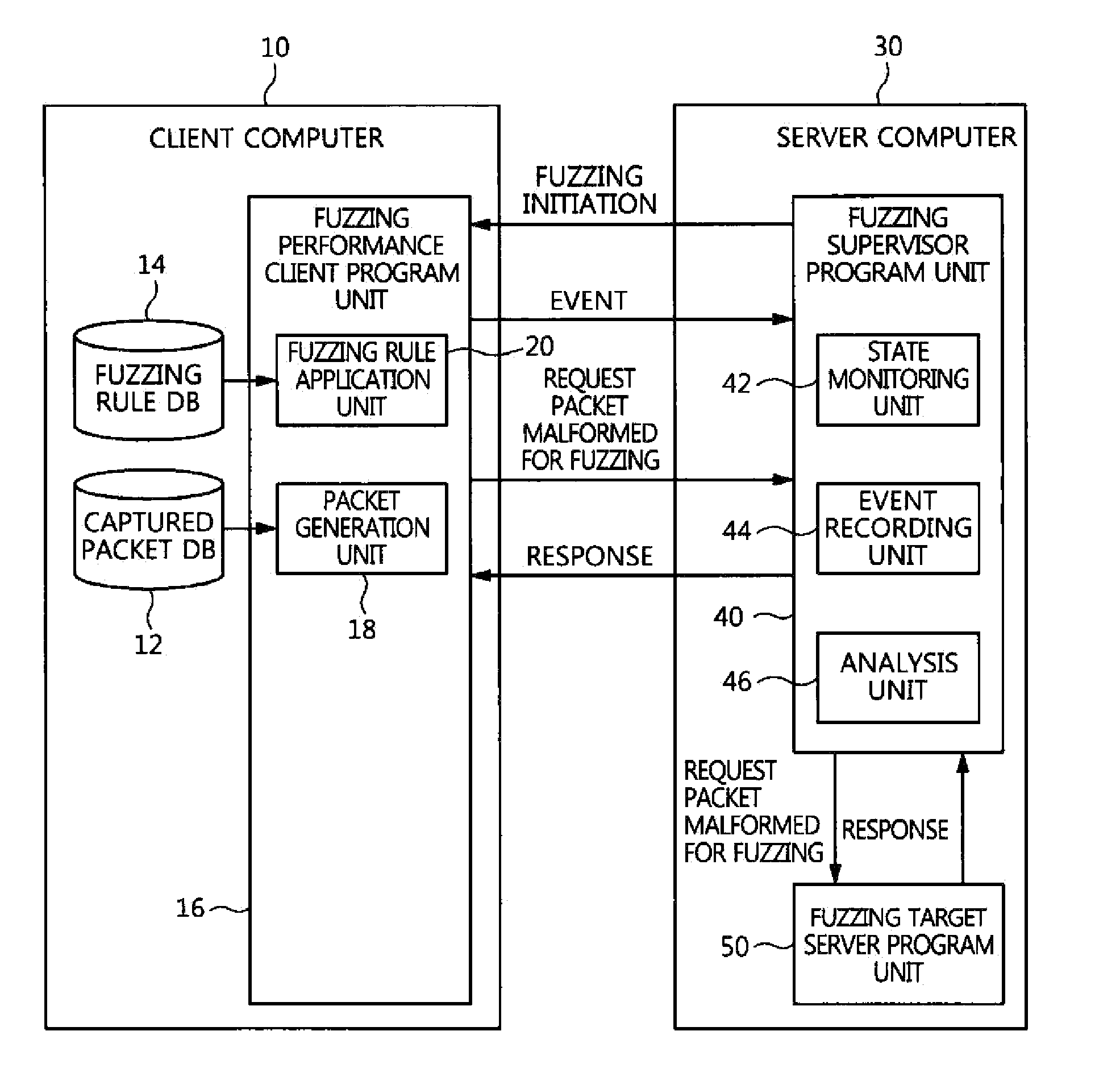
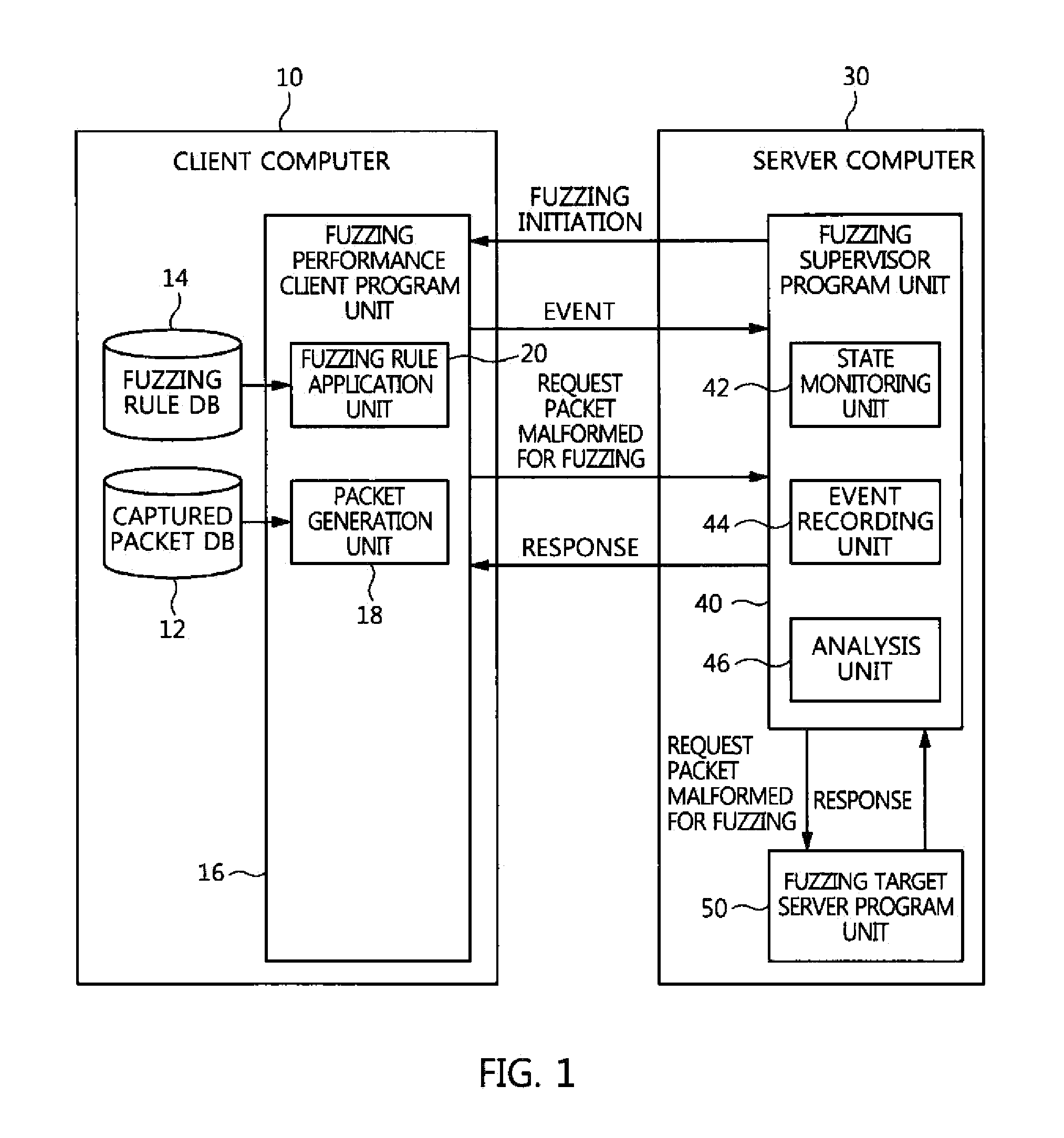
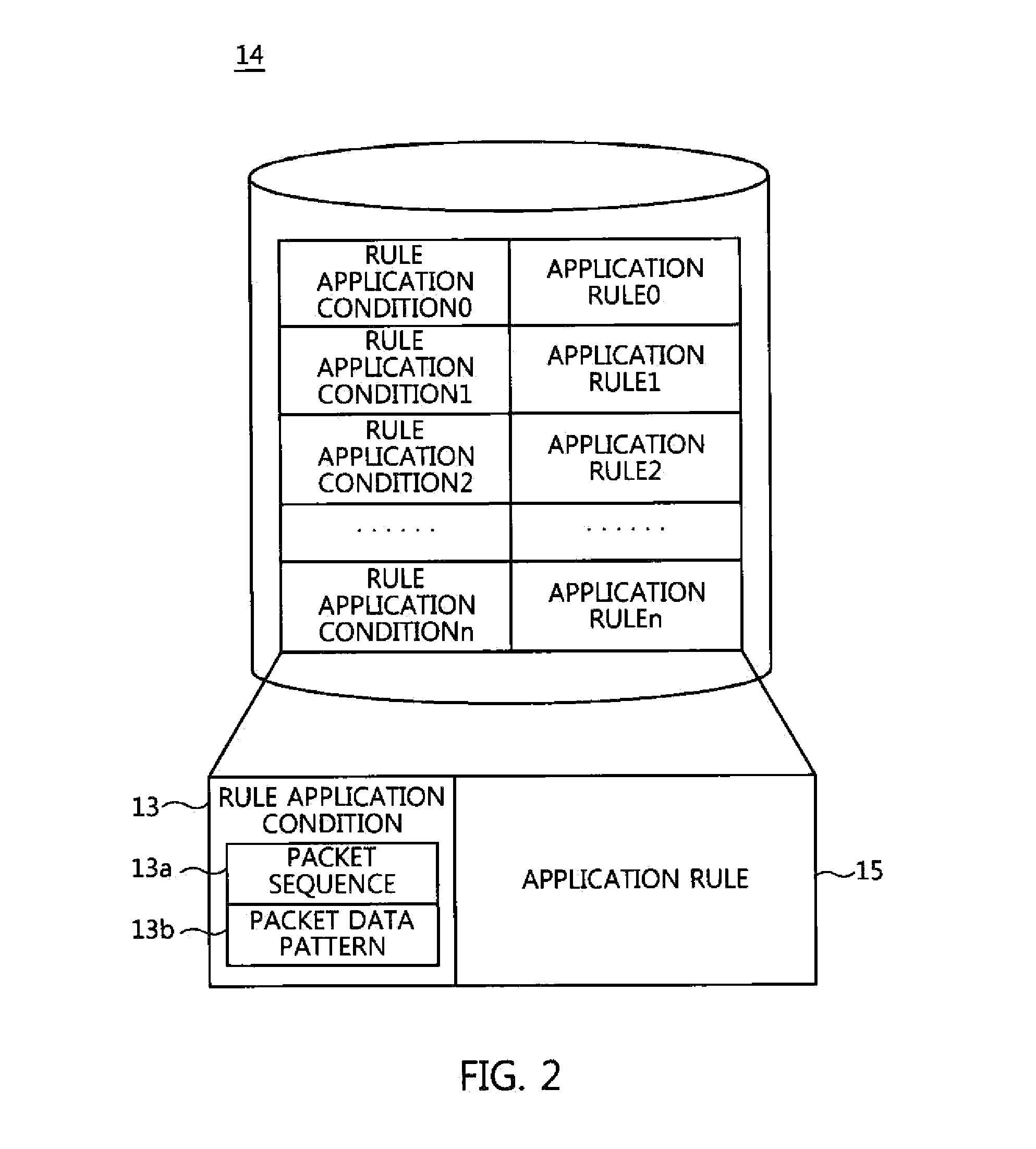
System and method for fuzzing network application program
A system and method for fuzzing a network application program, which use a captured packet upon fuzzing a network application program, and thus neither a protocol analysis procedure nor the production of a fuzzer program is required. The system for fuzzing a network application program includes a fuzzing performance client program unit for generating a packet to be transmitted from a captured packet, applying a fuzzing rule to the packet to be transmitted, and outputting a resulting packet. A fuzzing supervisor program unit provides the packet from the fuzzing performance client program unit to a target program to be fuzzed, monitors an event and abnormal termination of the target program to be fuzzed, and analyzes a situation of termination to verify security vulnerabilities if abnormal termination has occurred.
Owner:ELECTRONICS & TELECOMM RES INST
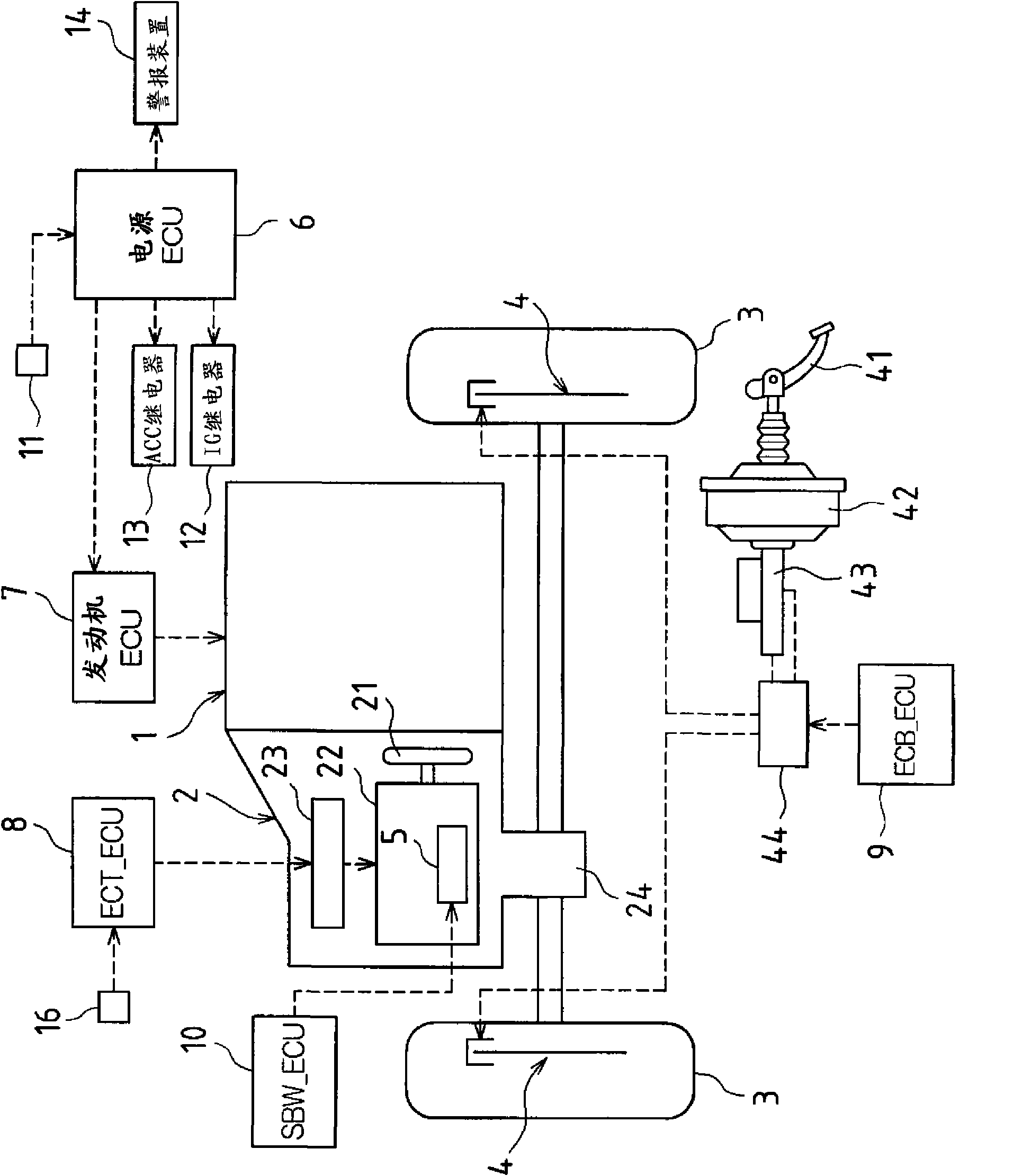
Vehicle control device
InactiveCN101568455AEnsure routine end-of-processing statusImprove reliabilityBraking element arrangementsAutomatic initiationsEngineeringVehicle control
The invention provides a vehicle control device. Control devices (6, 10) include an end process element and a support process element. The end process element performs a normal end process which stops a vehicle drive source (1) and switches it to an ignition off position if lock is established within a reference time after operation of a parking mechanism (5). On the other hand, if the lock is not established, the end process element performs an abnormal end process which stops the vehicle drive source (1) and switches it to an accessory position. When vehicle speed increase is detected upon operation of the parking mechanism (5), the support process element inhibits operation of the parking mechanism (5) and extends the reference time.
Owner:TOYOTA JIDOSHA KK
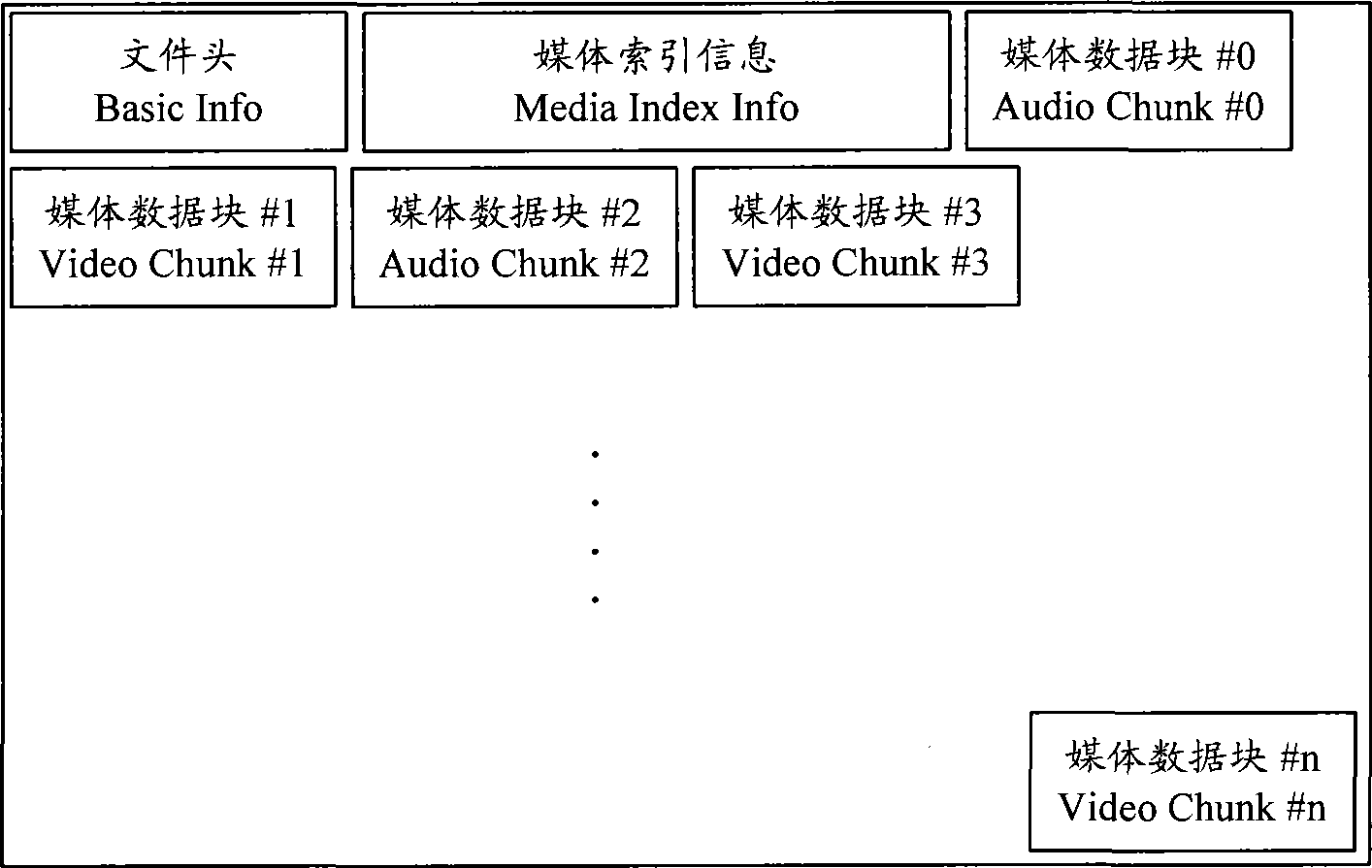
Media recording method and device thereof
ActiveCN101447207AGuaranteed robustnessRecord information storageCarrier indexing/addressing/timing/synchronisingComputer terminalSpatial change
Owner:HUAWEI DEVICE CO LTD
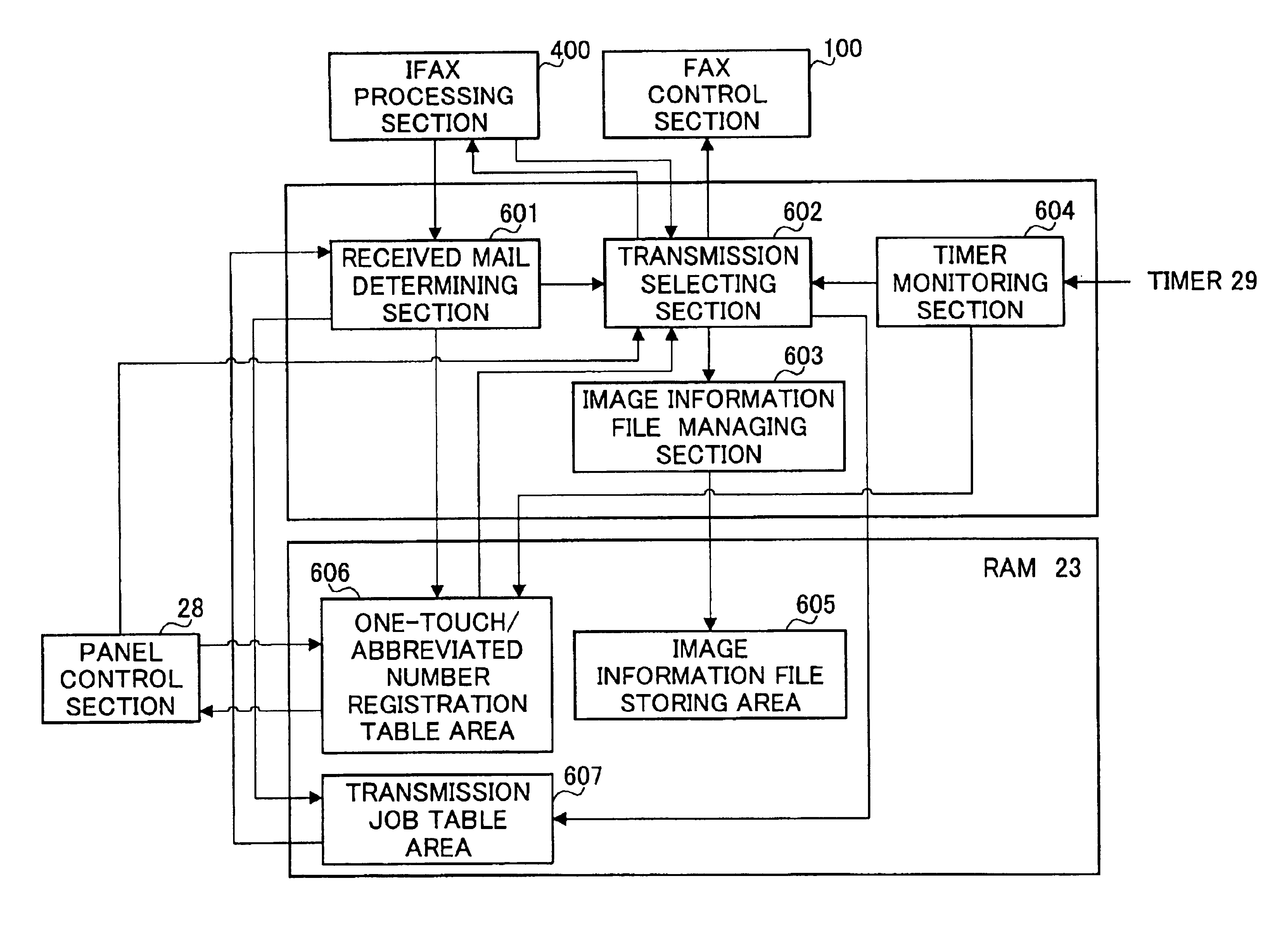
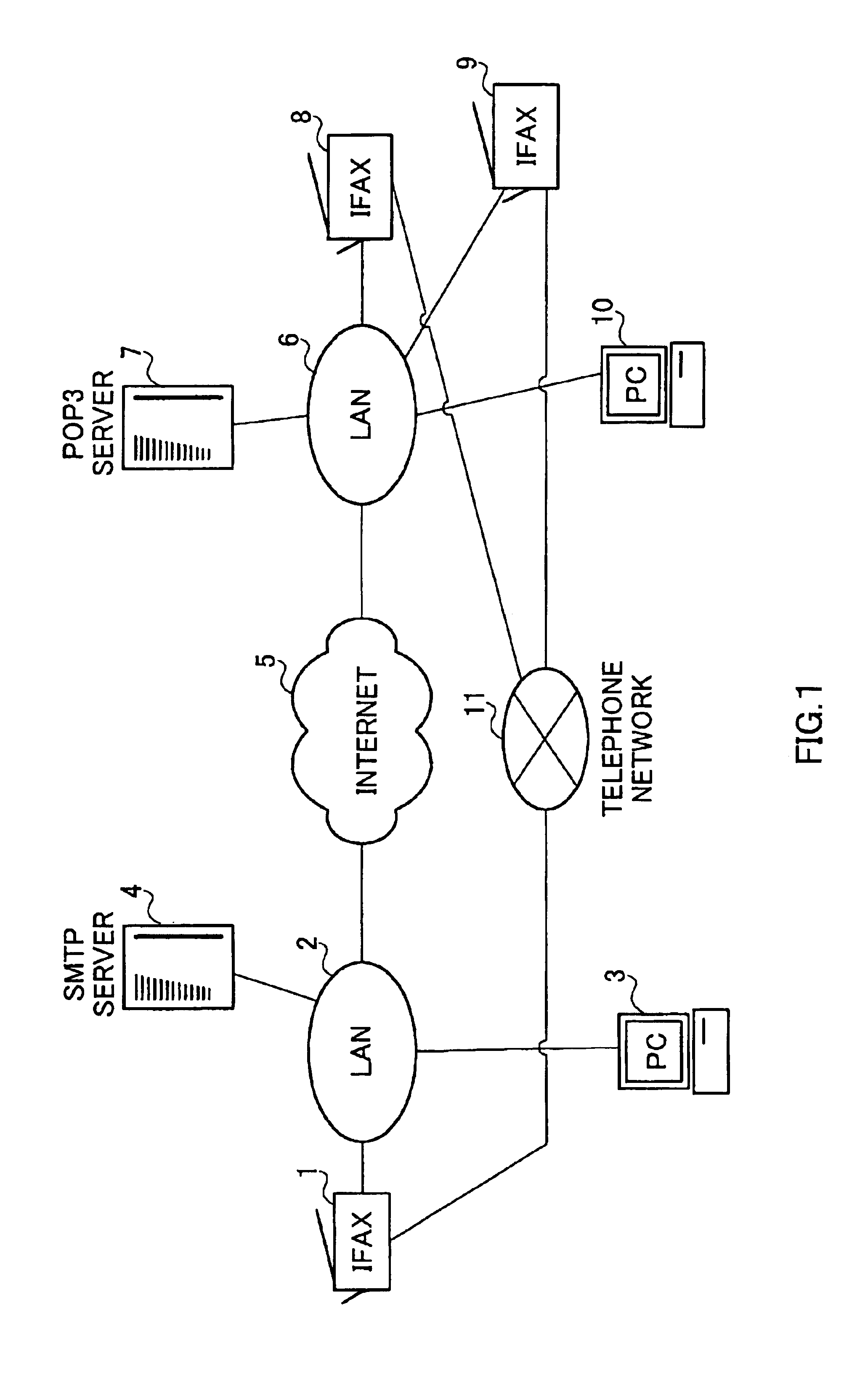
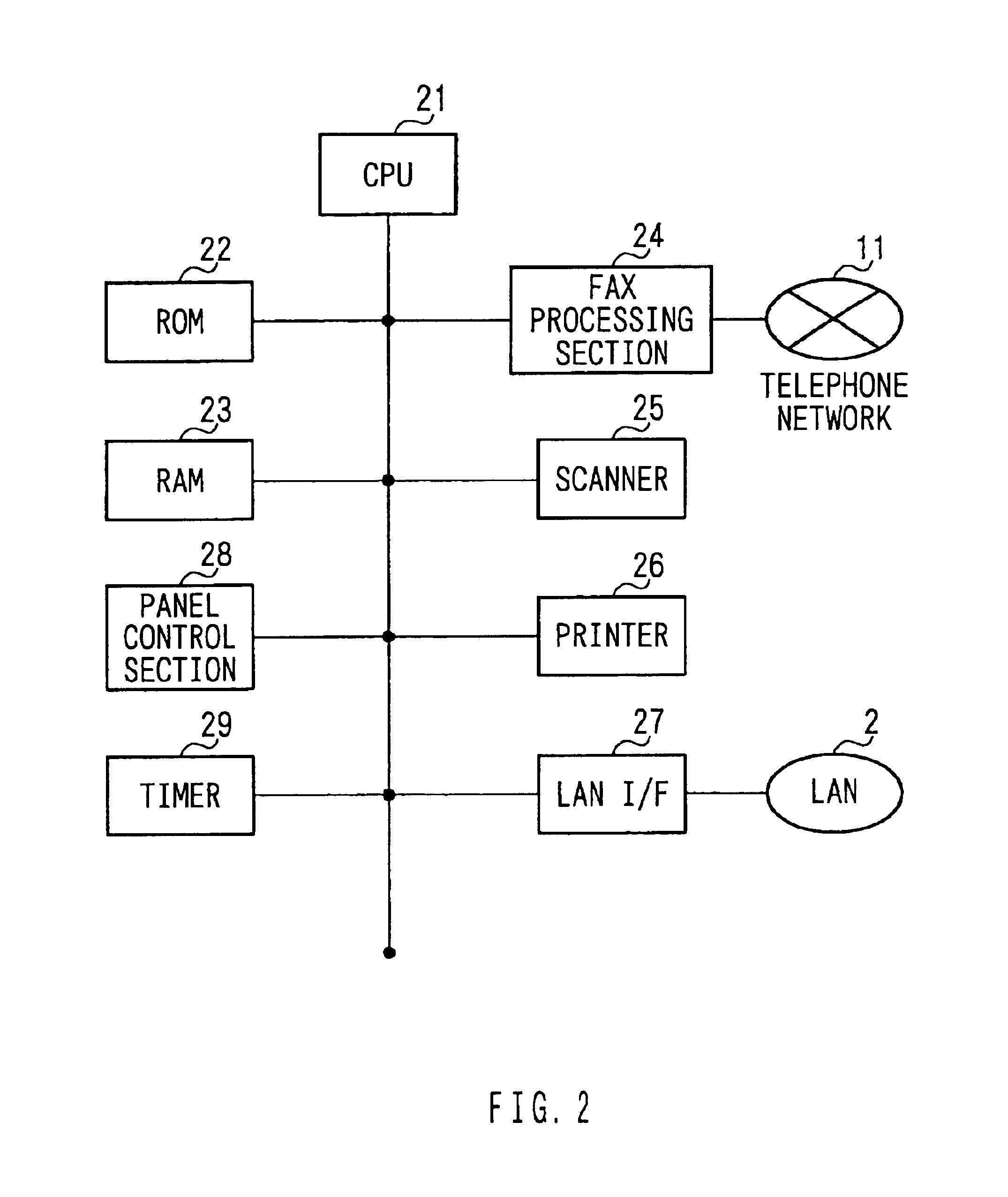
Internet facsimile apparatus and internet facsimile communication method
InactiveUS6965446B2Suppression delayDigital computer detailsTelephonic communicationThe InternetFacsimile
When an IFAX processing section transmits image information using e-mail, a timer monitoring section starts the count of a timer. After starting the count, a received mail determining section determines whether or not a timeout occurs. Also, the received mail determining section determined whether an error mail of a current job or a DSN of the current job is received. In the case of the timeout, when the notification content of the error mail or the DSN is an abnormal end, a transmission selecting section instructs a FAX control section to transmit an image information file of the current job to a telephone number. Thereafter, the transmission selecting section instructs an image information managing section to erase an image information file corresponding to a file name of the current job. This makes it possible to insure a real-time property as making use of advantages of e-mail.
Owner:MATSUSHITA GRAPHIC COMM SYST INC
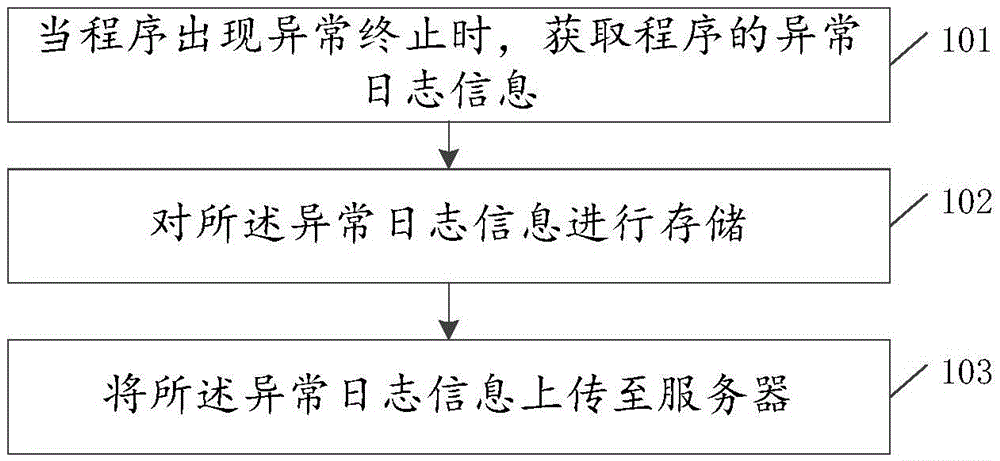
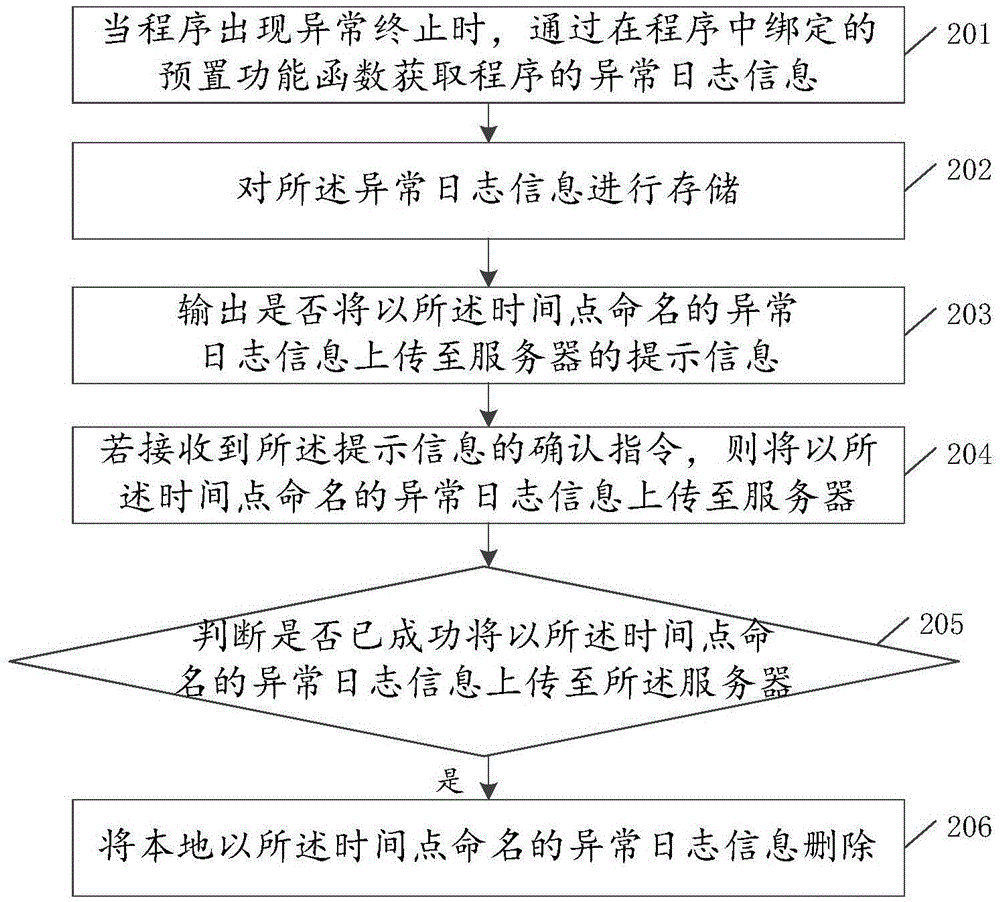
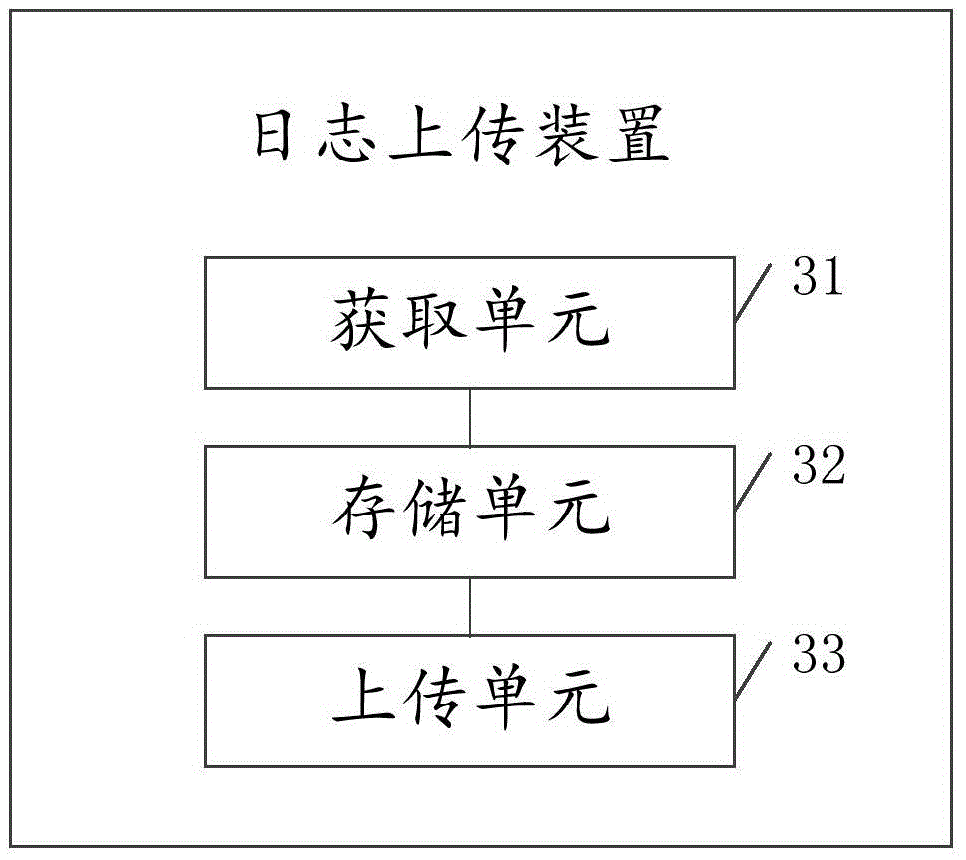
Log uploading method and device
The embodiment of the invention provides a log uploading method and device, relates to the technical field of information and mainly aims at solving the problem that abnormity log information cannot be automatically uploaded to a server when a program produces abnormity. The technical scheme used by the embodiment of the invention comprises following steps of obtaining the abnormity log information of the program when the program produces abnormal termination; storing the abnormity log information; and uploading the abnormity log information to the server. The method and the device are mainly used for uploading the abnormity log information to the server.
Owner:LE SHI ZHI ZIN ELECTRONIC TECHNOLOGY (TIANJIN) LTD
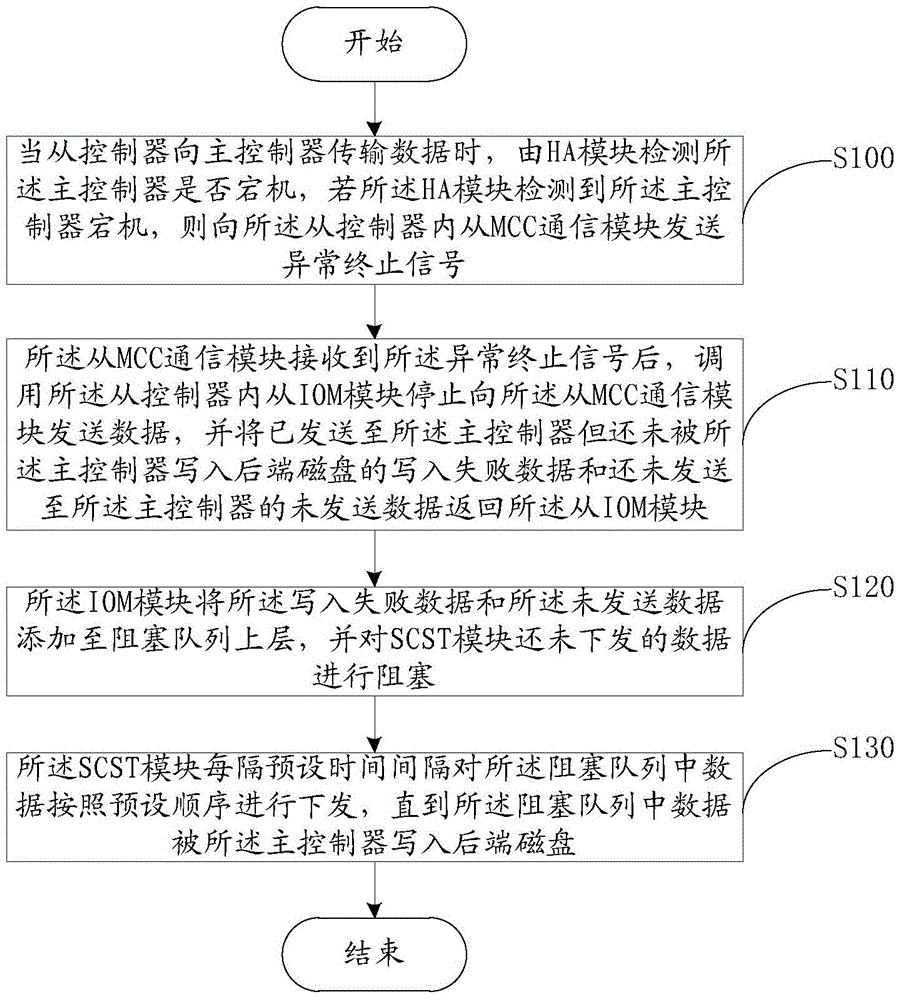
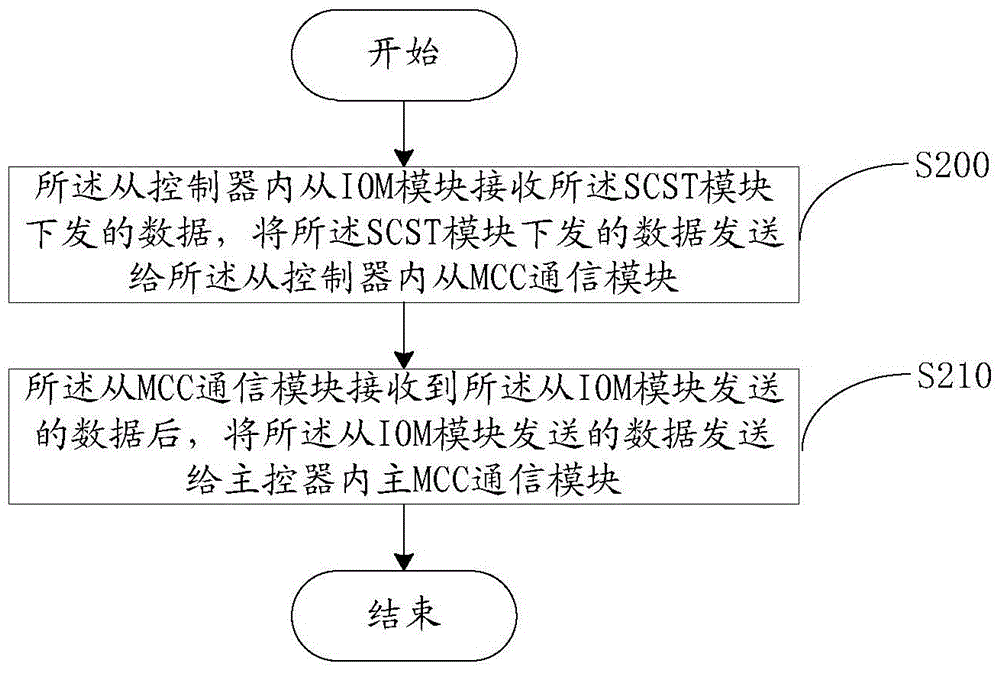
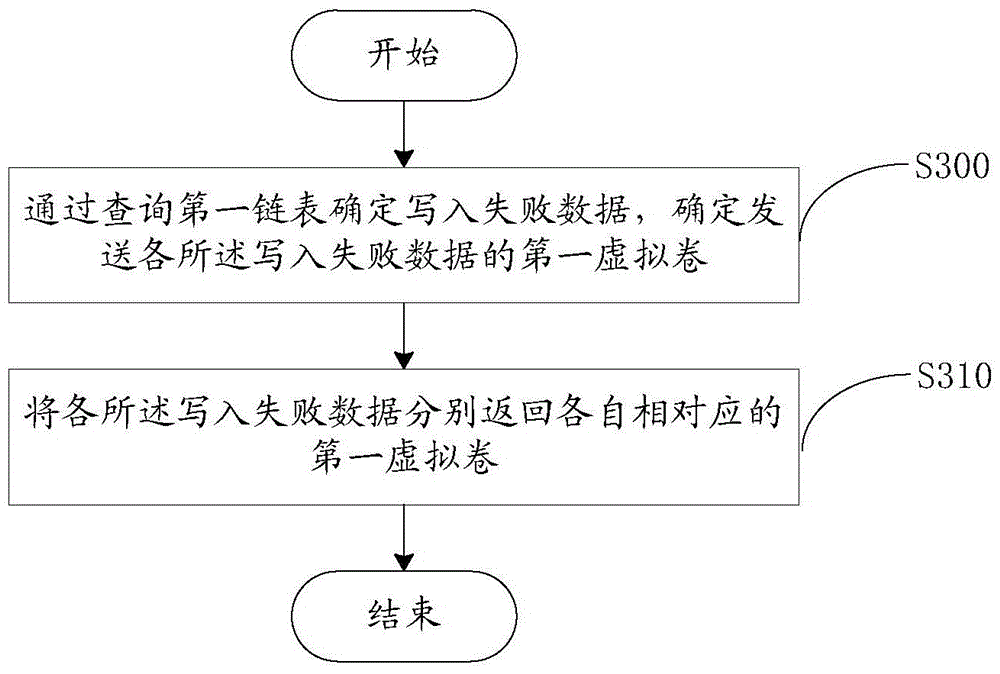
Failure processing method and system for multi-controller storage system
ActiveCN105786666AImprove writing efficiencyIntegrity guaranteedFaulty hardware testing methodsDowntimeMaster controller
The embodiment of the invention provides a failure processing method and system for a multi-controller storage system, wherein the method comprises following steps of sending an abnormal termination signal to the slave MCC (multi-controller communication) module in a slave controller when the slave controller transmits data to a master controller, and if an HA module detects that the master controller is in downtime; invoking the slave IOM module in the slave controller to stop transmitting the data after the MCC module receives the abnormal termination information; returning data failed to be written and transmitted to the slave IOM module; adding the data failed to be written and transmitted in the upper layer of a blocking queue by the slave IOM module; and blocking data which is not sent by an SCST module, wherein the SCST module sends the data in the blocking queue according to a preset sequence at intervals of preset time until the data in the blocking queue is written in a rear end disk by the master controller. According to the method and the system, the integrity of the written data and the stability of the multi-controller storage system are ensured, and relatively high data writing efficiency is realized.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
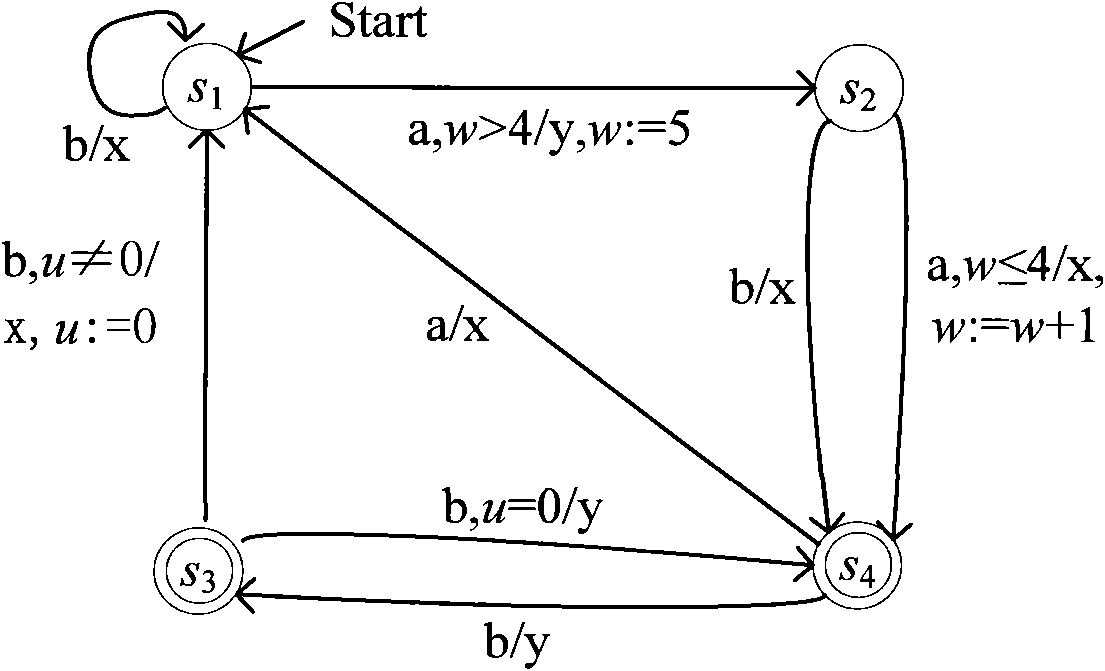
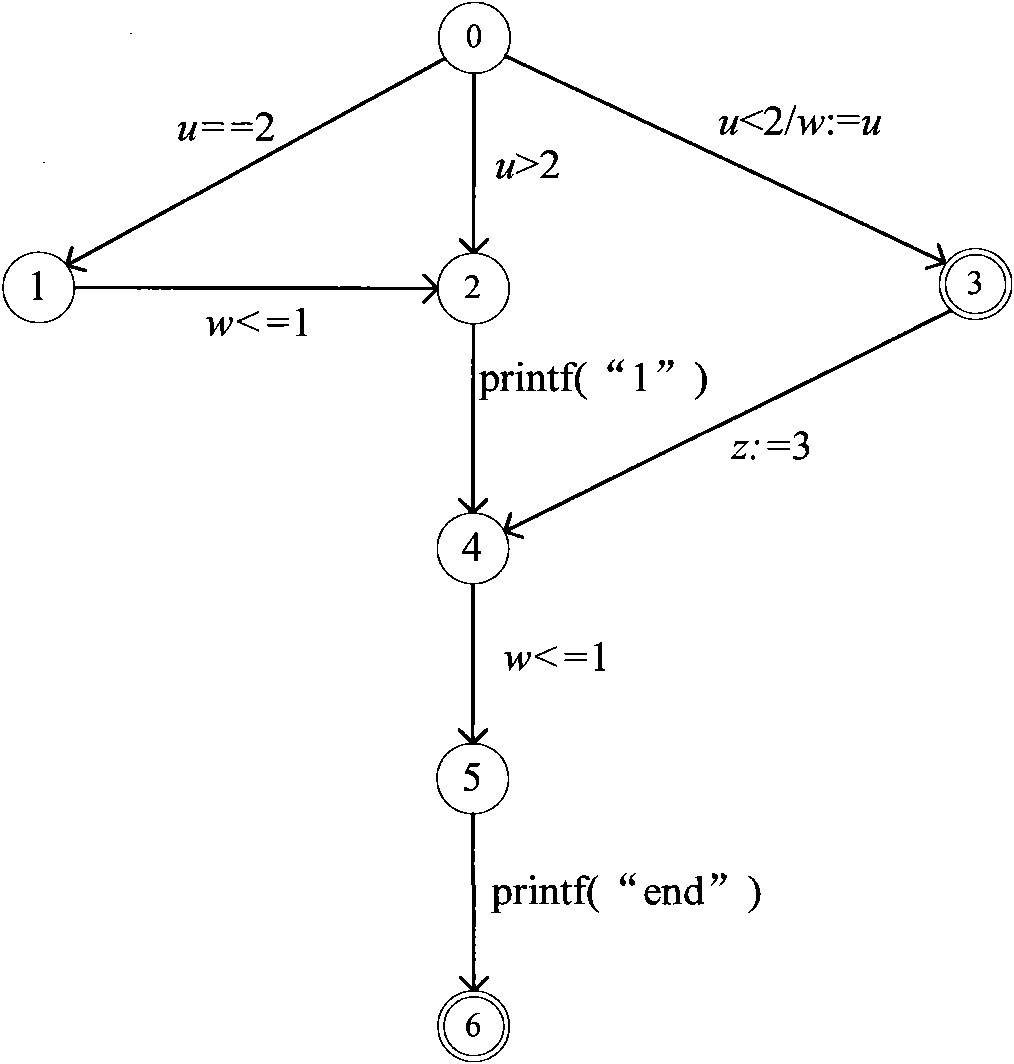
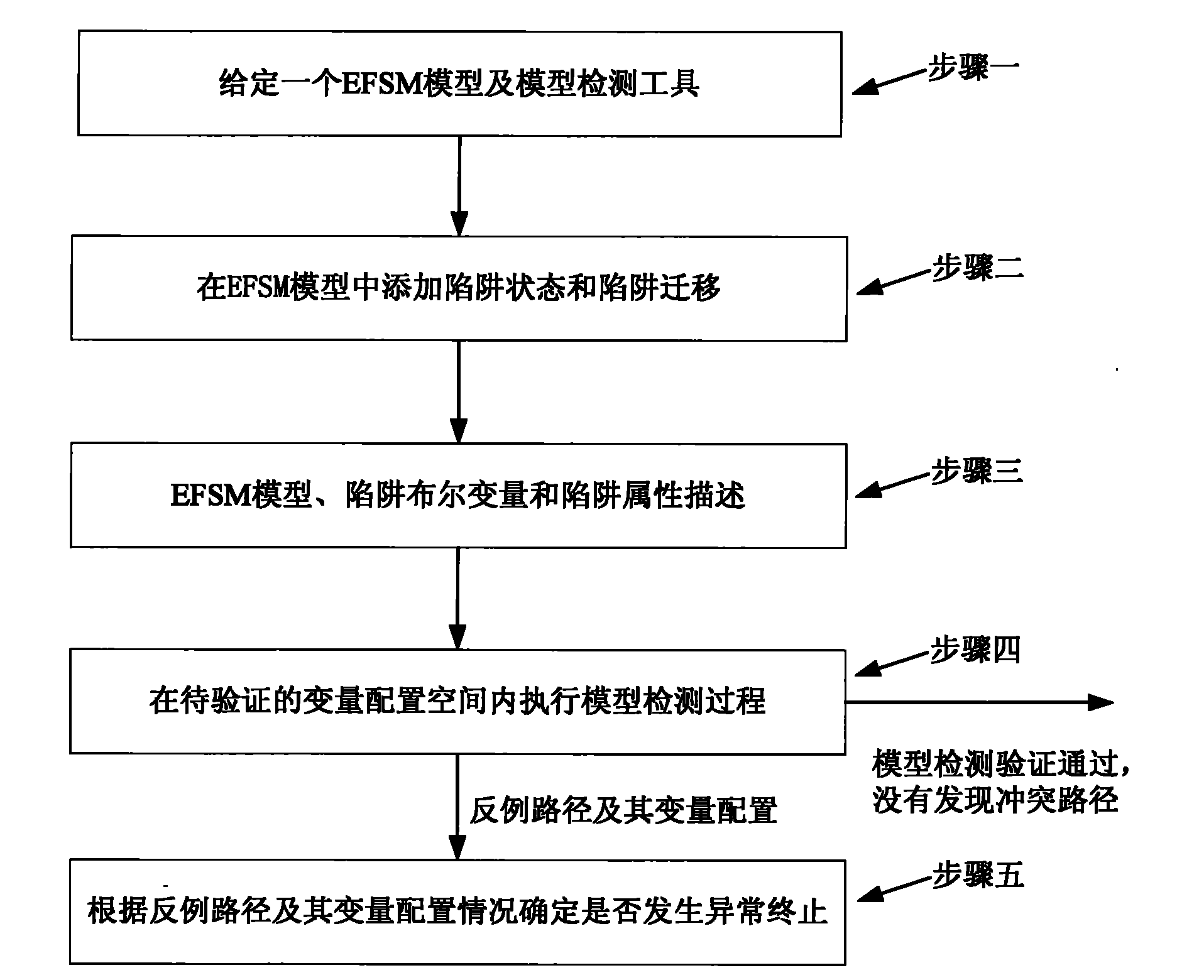
Method for detecting abnormal termination during model detection
The invention discloses a method for detecting abnormal termination during model detection. In the method, a counter example path is generated and recorded by constructing E', describing the E' and performing a model detection process. The counter example path provides detail execution steps for an extended finite state machine (EFSM) model under a variable configuration corresponding to the EFSM model, and the latest part of the counter example path provides information of a terminable state in a trap state. According to logic expressed by the EFSM model, whether a termination state under the variable configuration is the terminable state can be easily determined. If the termination state under the variable configuration is not the terminable state, an abnormal termination phenomenon in the terminable state is detected under the corresponding variable configuration; and if the termination state under the variable configuration is the terminable state, the abnormal termination phenomenon in the terminable state is not detected. Therefore, the detection method provided by the invention realizes the detection of the abnormal termination phenomenon.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
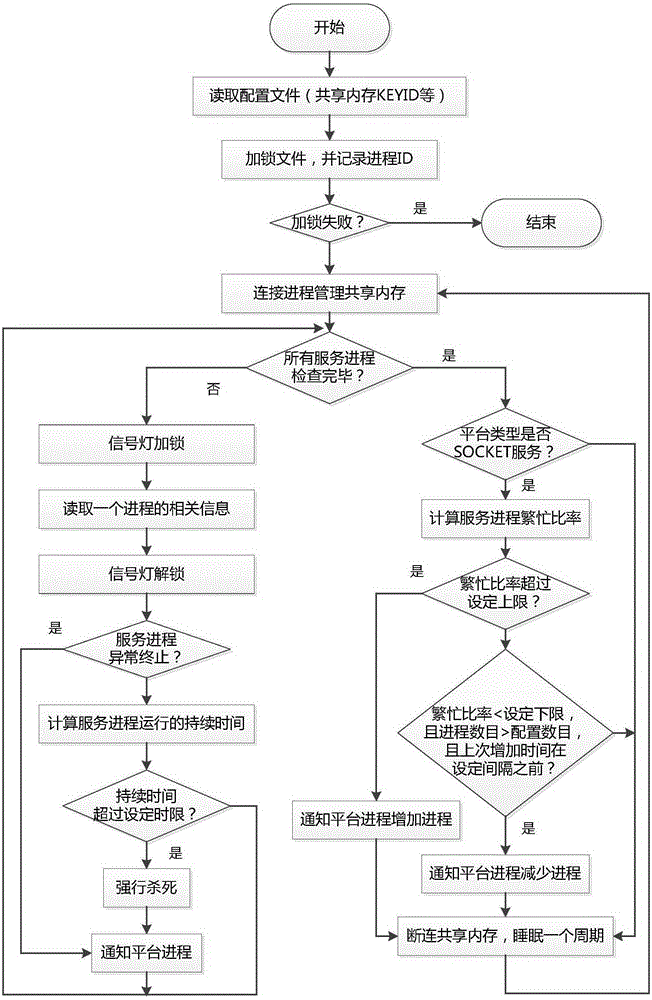
Universal resident process management platform and method
The invention discloses a universal resident process management platform and method. A platform process and a diagnosis process are created, and the platform process creates a process management shared memory and a signal lamp according to platform keywords in a configuration file, creates SOCKET management descriptors and waits for operation instructions of users or reports of the diagnosis process; the process management shared memory includes whole platform information and a group of management slot positions, and each insert process occupies one slot position and stores private information of the insert process; the diagnosis process is matched with the platform process, and abnormally terminated or zombie processes are automatically restarted to ensure continuous and stable running of the whole platform. A developer encapsulates service logics into the independent insert processes, the insert processes can be different from each other, can be executed by the different users and can be separately started or stopped, scattered tasks on the backgrounds of multiple users are managed in the single platform in a centralized mode, and the platform has self-diagnosis and real-time running monitoring functions as well.
Owner:MASSCLOUDS
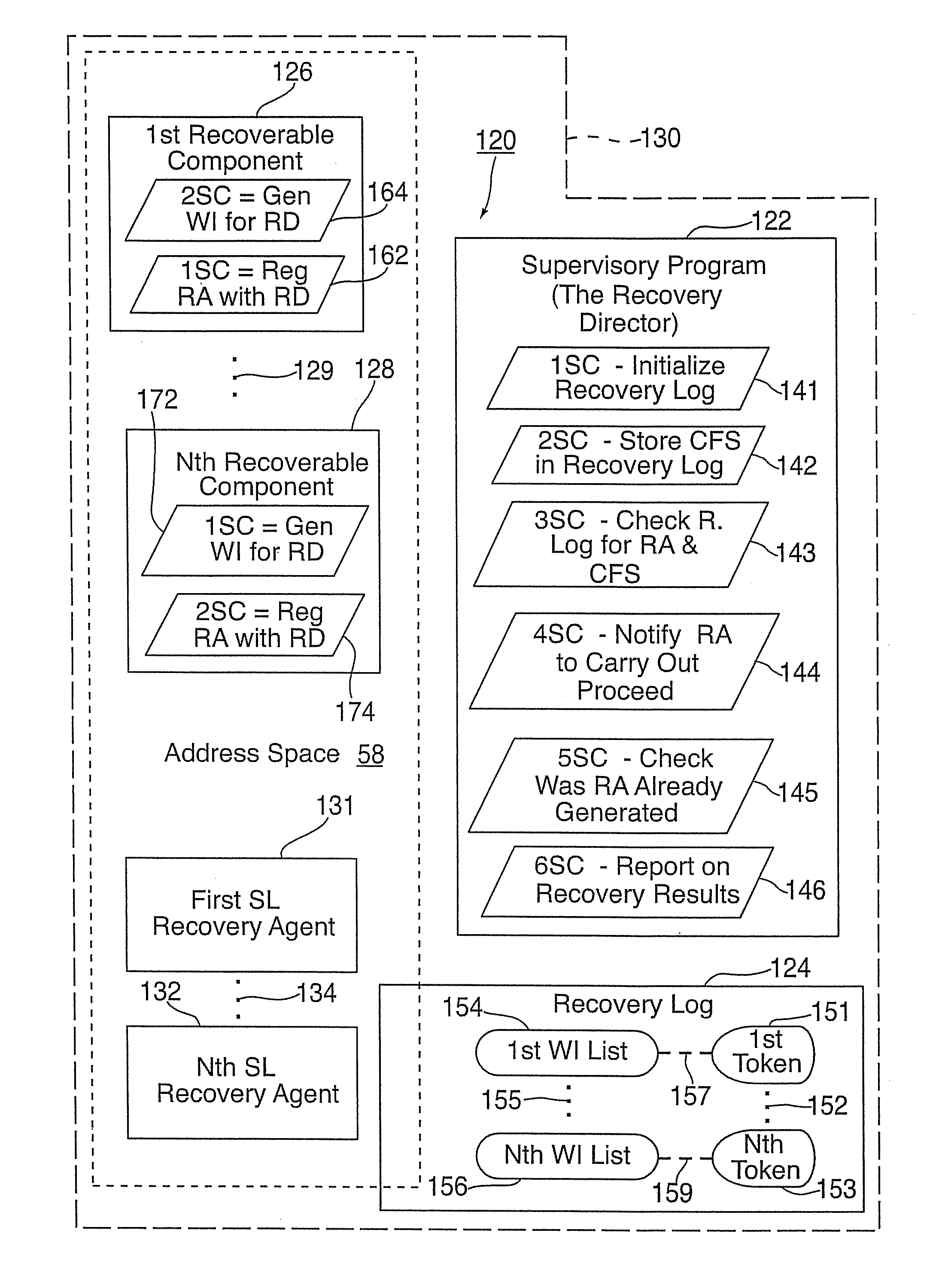
Nested recovery scope management for stateless recovery agents
InactiveUS8572044B2Easy to useData processing applicationsDigital data processing detailsRecovery functionEmbedded system
Nested recovery scope management systems and methods for a multiple process computer system having a dynamic multiple address space server are disclosed. Stateless recovery agents are employed, under the control of a supervisory program called Recovery Director, during initialization or restart of servers to restore recoverable data in response to identified failures or other abnormal termination. The Director controls the recovery of protected resources in a systematic manner. The Director is initialized when a first address space of a first server is started. Then, as each instance of a recoverable component is initialized, the component registers with the Director by providing a reference to a stateless recovery agent that can later perform recovery functions for it if needed. As part of the registration, a token representing the current failure scope of the registration is generated and provided to the recoverable component by the Director.
Owner:SERVICENOW INC +1
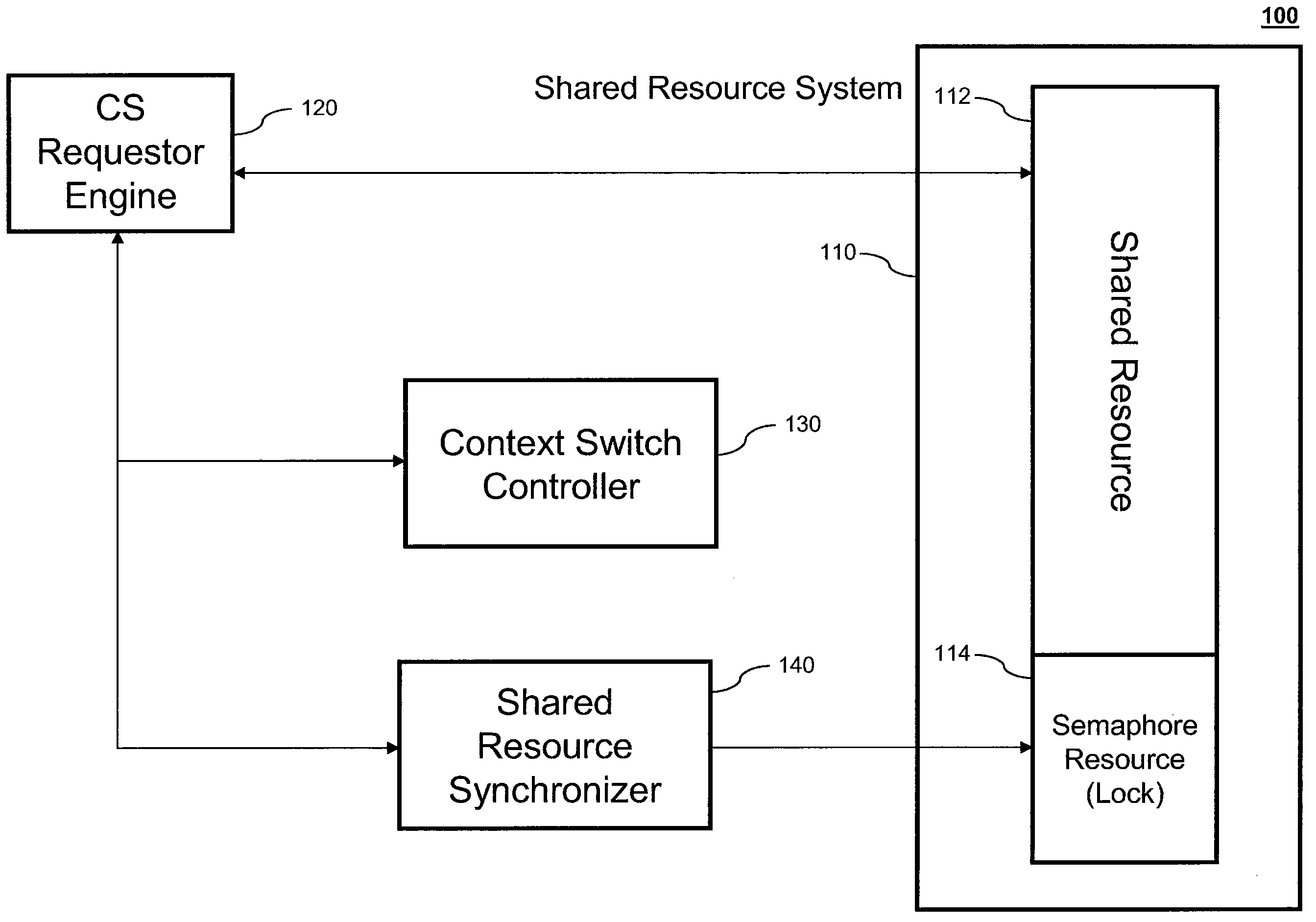
Re-Entrant Atomic Signaling
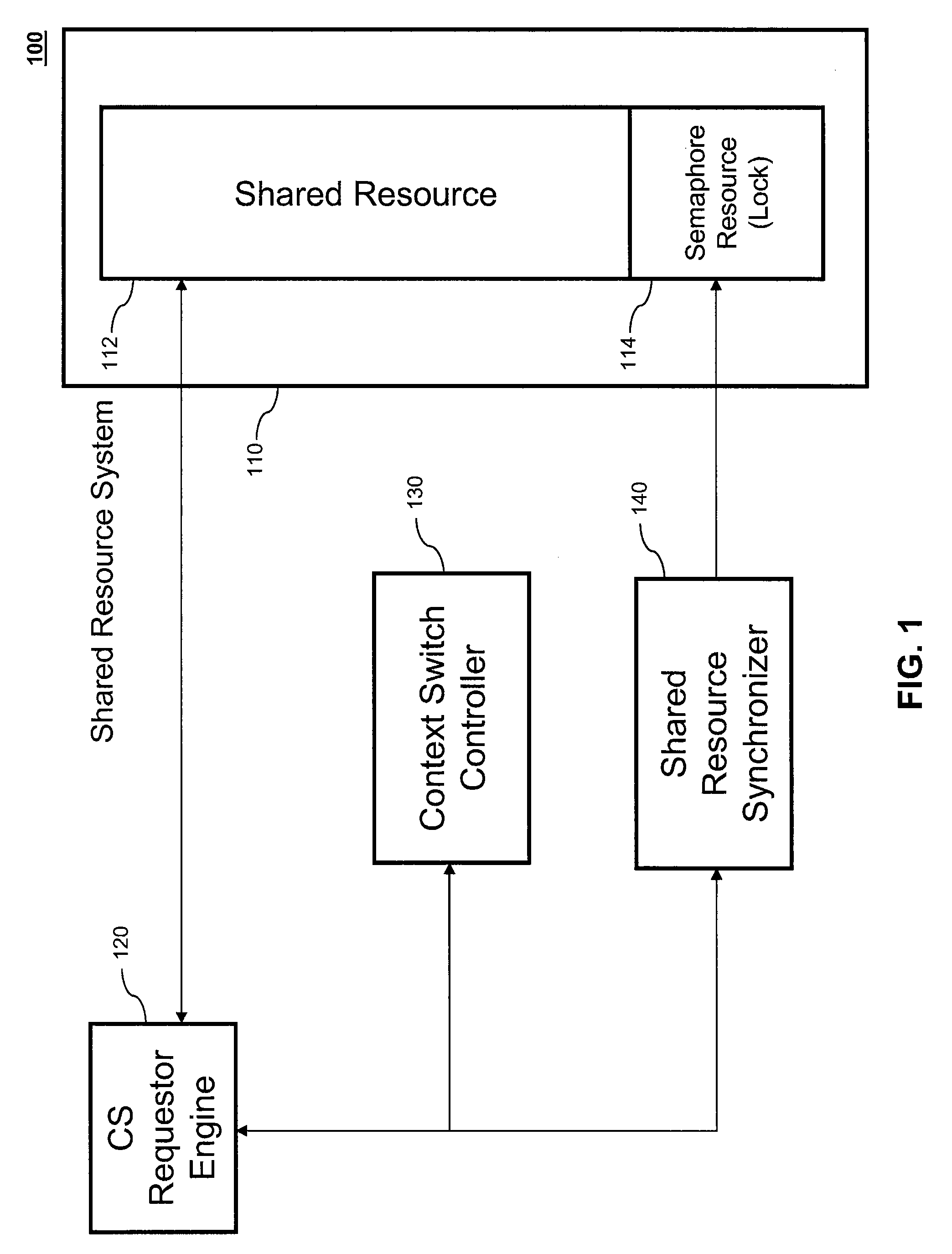
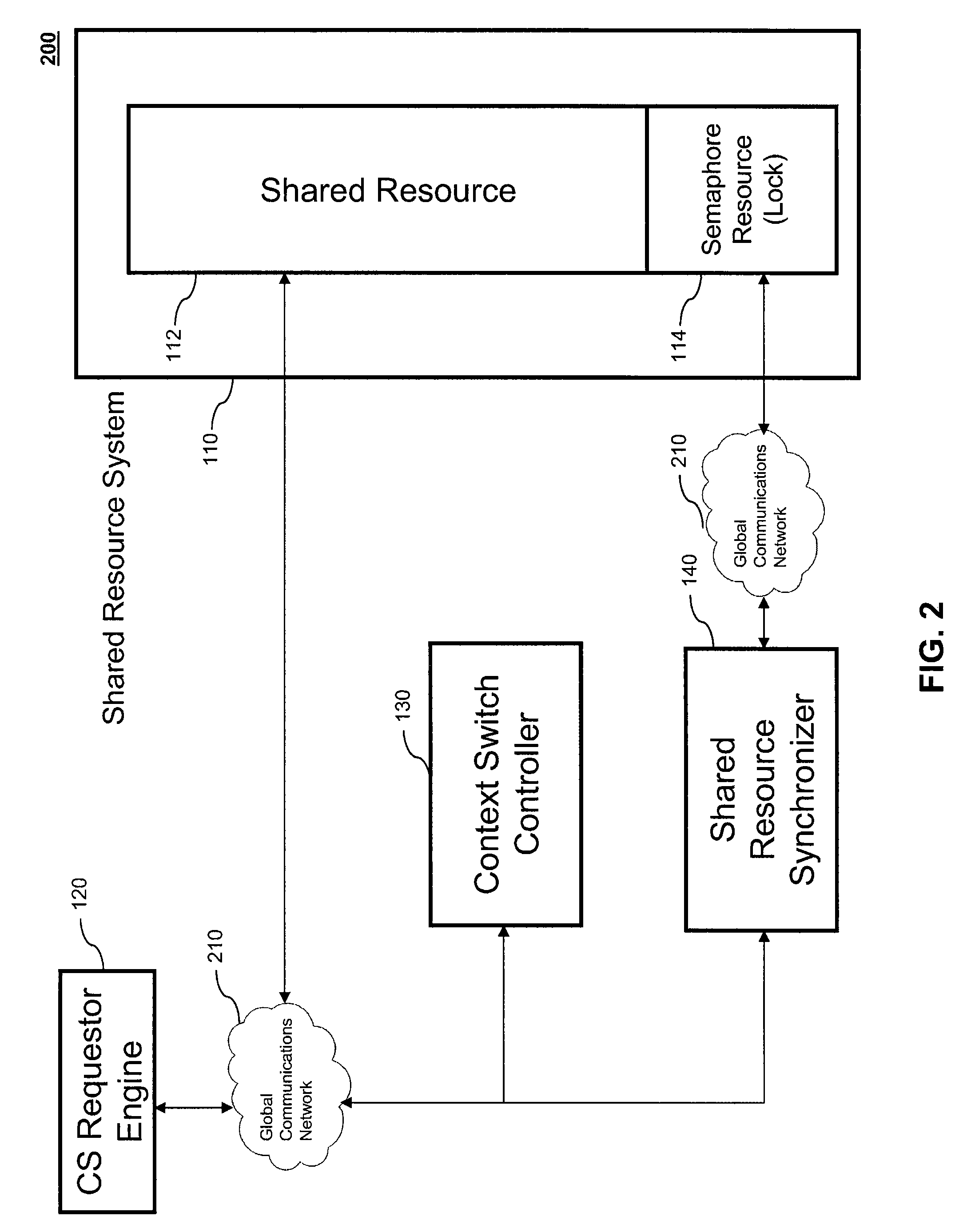
InactiveUS20090172675A1High levelImprove throughputProgram synchronisationMemory systemsSignaling systemShared resource
Systems for context switching a requestor engine during an atomic process without corrupting the atomic process. Typically an atomic process cannot be interrupted prior to completion and if it is interrupted, the process will terminated abnormally resulting in a corrupted transaction. Systems that allow for a controlled interruption of an atomic process without corruption with subsequent context switching are presented. The system consists of a context-switchable requester engine, a context switch controller, shared resource synchronizer, and a shared resource system. The system may also containing multiple local and remote context-switchable requestor engines as well as multiple local and remote shared resource systems. A method for context switching a requestor engine during an atomic process without corrupting the atomic process is also presented.
Owner:ADVANCED MICRO DEVICES INC
Recording apparatus and method, program, and storage medium
InactiveUS20070286050A1Easy and proper storageAchieve recordCombination recordingTelevision system detailsFile systemAbnormal end
Disclosed herein is a recording apparatus for recording a file stream which may be composed of a header, a body, and a footer onto a storage medium. The apparatus may includes header area securing means for, before recording of the body, securing in a recording area of the storage medium a header area in which the header is to be recorded; recording means for recording the body and the footer in the recording area of the storage medium, re-securing the header area secured by the header area securing means based on areas in which the body and the footer have been recorded, and recording the header in the re-secured header area; and reflecting means for allowing information concerning the header area secured when a recording process performed by the recording means is terminated normally or abnormally to be reflected in a file system of the storage medium.
Owner:SONY CORP
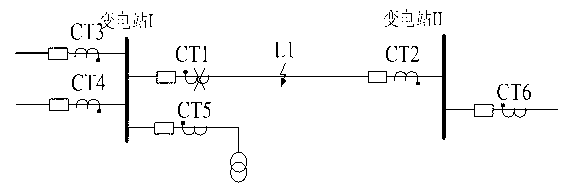
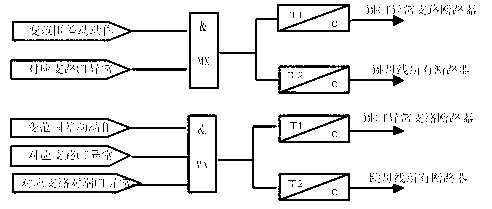
Differential protection method of regional power grid network change range
The invention relates to a differential protection method of a regional power grid network change range, wherein bus differential protection with expanded range in the invention is used as bus, circuit and standby protection of the high voltage side of a transformer, when a current transformer of one element abnormally samples, and a related current transformer on the opposite side of the element is used for replacing the current transformer of the element participate in the bus differential protection; if the current transformers on the sides of a protected object are abnormal, for example, the current transformers on the two sides of the circuit are abnormal, the bus differential protection on the two sides of the circuit directly eliminates the related ports of the protected object to perform differential protection calculation. After the variable-range differential protection, a circuit breaker at the abnormal end of the current transformer is turned off at a first time limit, and the circuit breakers at all ports are turned off at a second time limit. The differential protection method provided by the invention is used for guaranteeing the main protection can normally work when the current transformer of the protected target in the regional power grid is abnormal.
Owner:XJ ELECTRIC +2
FPC line detection method based on feature tracking and skeleton feature matching
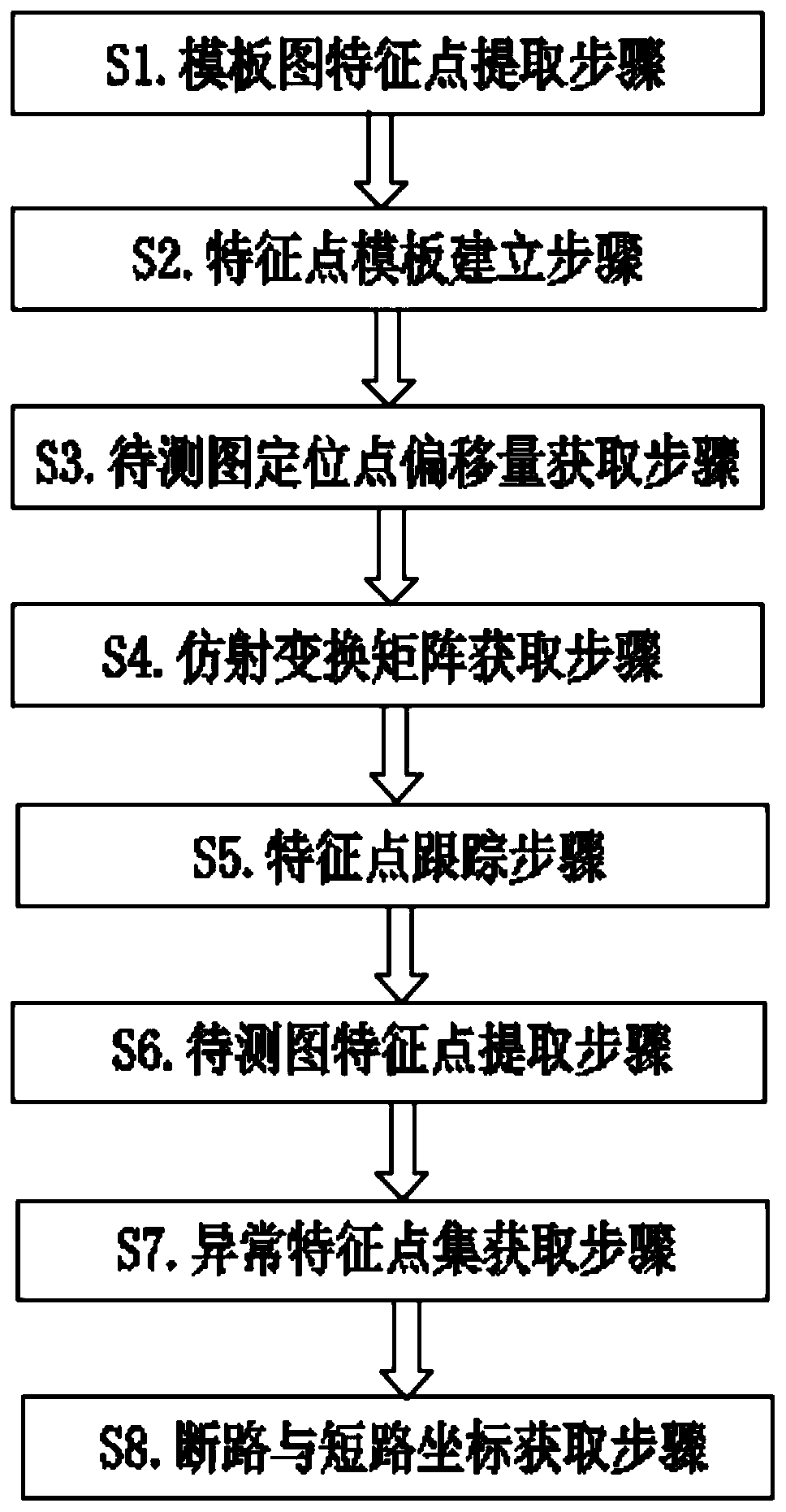
PendingCN110910359AGood circuit breakerEasy to detectImage enhancementImage analysisFeature trackingPoint tracking
The invention provides an FPC line detection method based on feature tracking and skeleton feature matching. The method comprises a template graph feature point extraction step, a feature point template establishment step, a to-be-measured graph positioning point offset acquisition step, an affine transformation matrix acquisition step, a feature point tracking step, a to-be-measured graph featurepoint extraction step, an abnormal feature point set acquisition step and an open circuit and short circuit coordinate acquisition step. According to the invention, the problems of accumulative errors and the like caused by FPC deformation are solved; based on the principle that an abnormal end point is generated during open circuit and an abnormal branch point is generated during short circuit,the tracking range of feature points is flexibly set according to the actual deformation degree, then the tracked feature points are compared with feature points extracted from an actual to-be-measured graph, and finally accurate defect information of short circuit and open circuit of a circuit is obtained. According to the open circuit and short circuit detection method, the open circuit and short circuit detection effect on the FPC with reasonable deformation is good, the accuracy and efficiency of open circuit and short circuit detection are improved, the detection precision is improved, and the robustness is improved.
Owner:GUANGDONG UNIV OF TECH +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com