Zombie network detection method and device
A technology of botnets and detection methods, applied in electrical components, transmission systems, etc., can solve the problem that botnets cannot respond in real time to human participation and analysis workload, and achieve the effect of efficient and safe network communication and reduce workload.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] In order to make the objectives, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below with reference to specific embodiments and accompanying drawings.
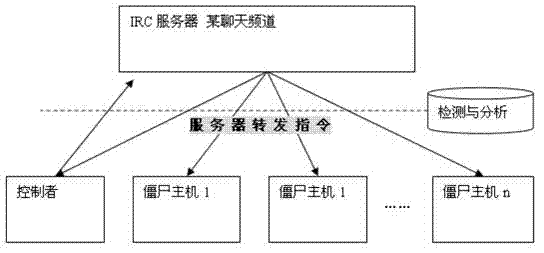
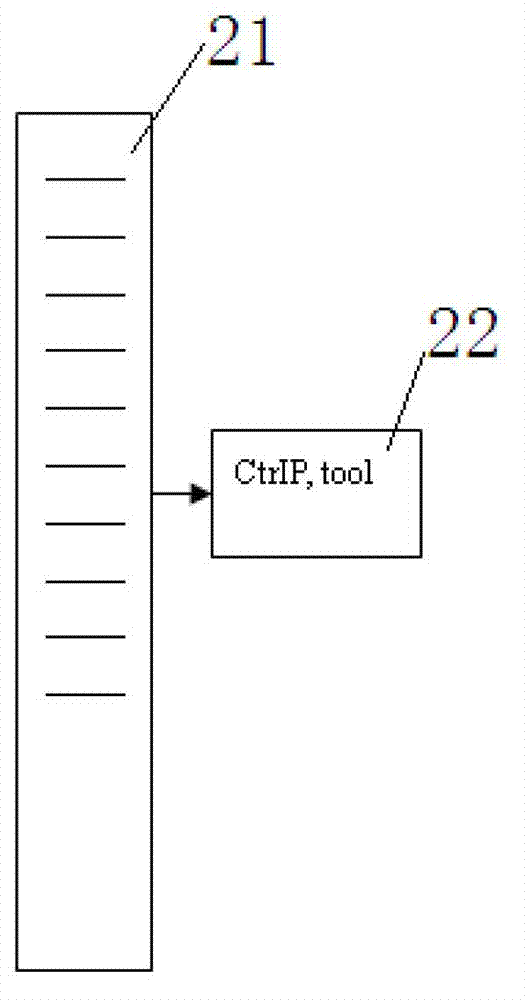
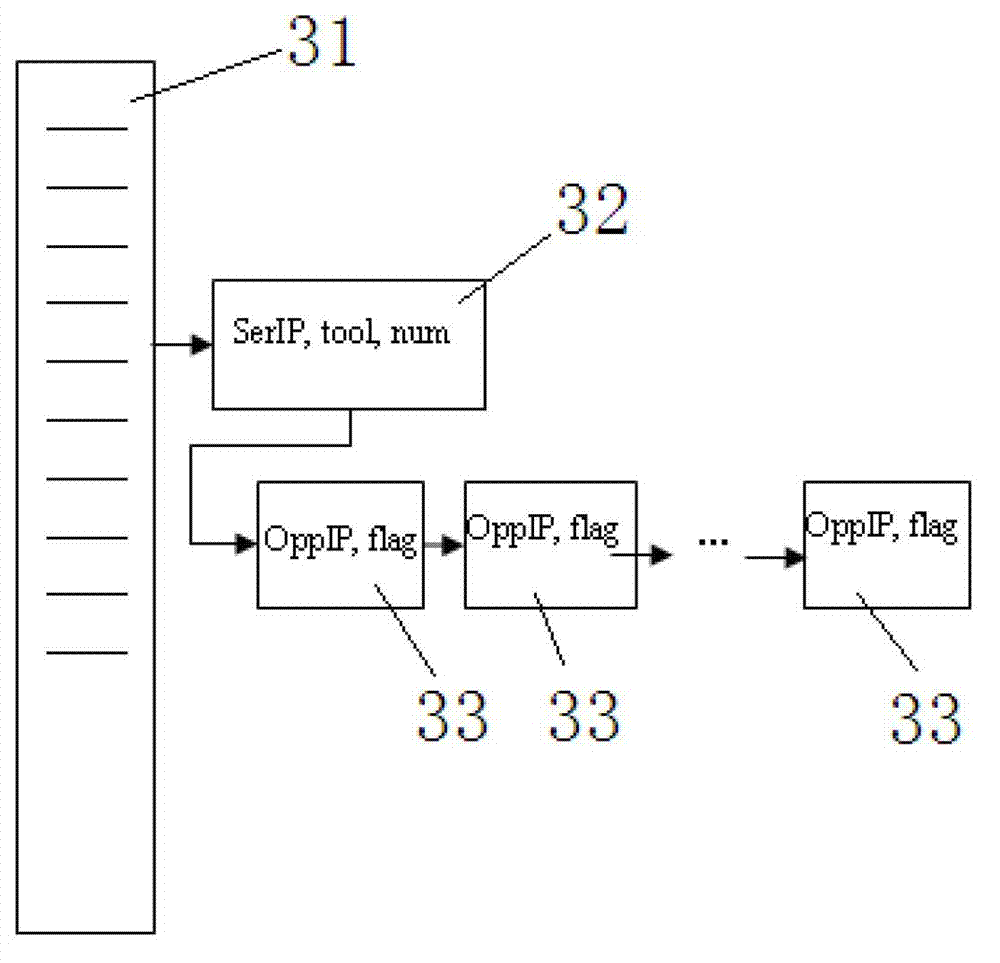
[0031] In the botnet monitoring method in this embodiment, by deploying network detection equipment, firstly, packet feature detection is performed according to the rule base, and the communication packets between the controller and the IRC server, the IRC server and the zombie host are monitored, and the packets are discarded. , thereby blocking the communication of the botnet. Then, the monitoring table of controller bot and IRC server is established by the detection device, and subsequent behavior analysis and monitoring of the IRC botnet are performed to clearly detect the various roles of the IRC botnet such as the IRC server, the controller, and the botnet.
[0032] figure 1 Schematic diagram of issuing and forwarding botnet attack i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com