DPD method and equipment based on IPsec
A detection method and technology of the detection party, applied in the field of communication, can solve the problems of wasting CPU, losing IP connectivity, etc., and achieve the effect of saving CPU resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
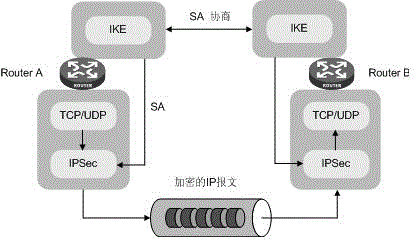
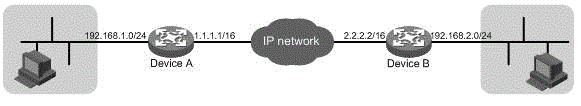
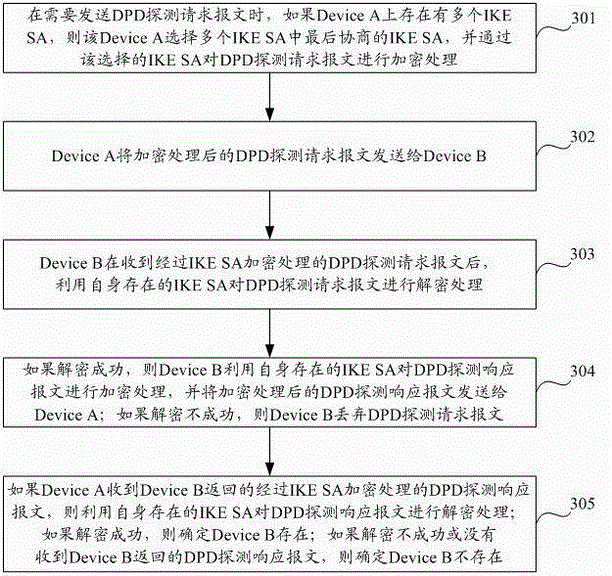
[0040] The embodiment of the present invention proposes an IPsec-based DPD detection method, which is applied to an IPsec network including a detecting device and a detected device, and the detecting device may be an IPsec initiator or an IPsec responder in an IPsec peer , the corresponding detected device is the IPsec responder or IPsec initiator in the IPsec peer; with figure 2 It is a schematic diagram of the application scenario of the embodiment of the present invention. The egress address from Device A to the IP network is 1.1.1.1, and IPsec is deployed on the interface, and the egress address from Device B to the IP network is 2.2.2.2, and IPsec is deployed on the interface. Therefore, Device A and Device B are IPsec peers, and it is assumed that Device A is the detecting device and Device B is the detected device.
[0041] exist figure 2 In the application scenario shown, there is host HOST1 in the private network protected by Device A, and host HOST2 in the private...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com