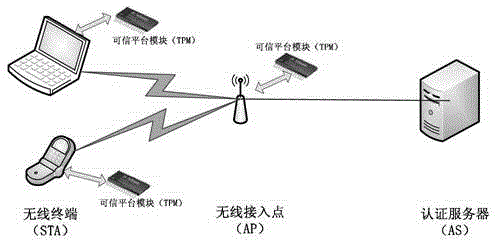
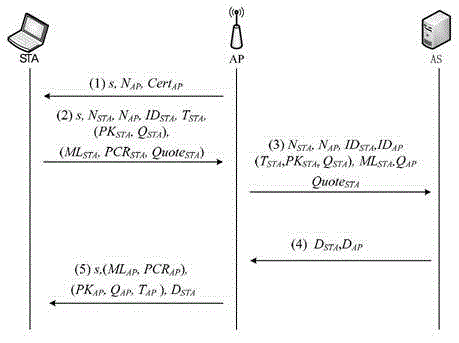
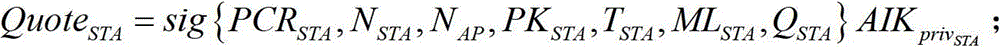A trusted and secure access method for wireless local area network
A wireless local area network and secure access technology, which is applied in the field of wireless local area network security and can solve the problems of inability to measure terminal integrity and reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The implementation manner of the trusted security access method will be described in detail below with reference to the accompanying drawings.
[0043] Description of the main cryptography knowledge, trusted computing technology and security assumptions used in this method:
[0044] 1. Bilinear pairing: let G 1 , G 2 They are respectively the additive cyclic group and the multiplicative cyclic group whose prime number is q in the elliptic curve, and P is the group G 1 the generator of G , and G 1 The discrete logarithm problem on is intractable. Then the bilinear map e:G between two groups 1 ×G 1 →G 2 satisfy the following properties.
[0045] (1) Bilinearity: e(aP,bQ)=e(P,Q) ab , for all P,Q∈G 1 ;a, b∈Z are all established;
[0046] (2) Non-degenerate: there is P, Q∈G 1 , making e(P,Q)≠1;
[0047] (3) Computability: For P, Q∈G 1 , there exist efficient algorithms to compute e(P,Q).
[0048] 2. PCR is the value of some registers in the TPM chip that repres...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com