Virtual machine identification dodging method and device
A virtual machine, non-virtual technology, applied in the field of network security, to achieve the effect of increasing effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
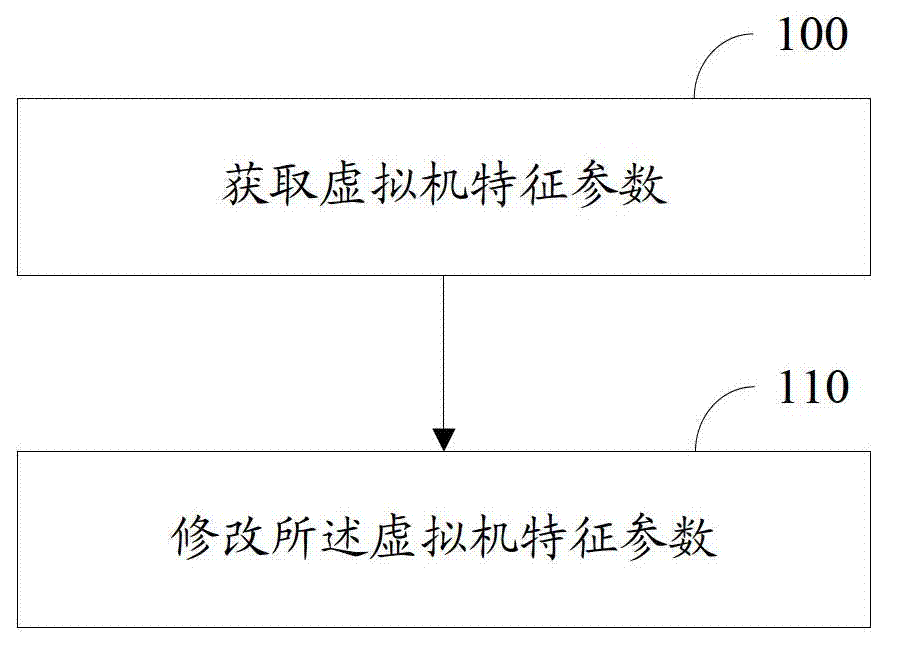
[0016] The present invention provides a method for avoiding recognition of a virtual machine, and its implementation method is as follows: figure 1 As shown, the specific implementation is as follows:
[0017] Step 100, acquiring a virtual machine characteristic parameter, the virtual machine characteristic parameter is a parameter used to identify a virtual machine;
[0018] Step 110, modifying the characteristic parameters of the above-mentioned virtual machine.
[0019] Wherein, modifying the characteristic parameters of the virtual machine may be, but not limited to: deleting the characteristic parameters of the virtual machine, modifying the characteristic parameters of the virtual machine to non-virtual machine characteristic parameters, and so on.
[0020] For the identification of the virtual machine, the feature parameters of the virtual machine are usually identified. The technical solution provided by the present invention, by deleting the characteristic parameter...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com