Key encryption and storage method
A key encryption and key technology, applied in the field of information security, can solve the problems of low key storage complexity and no guarantee of key storage security, and achieve the effect of improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
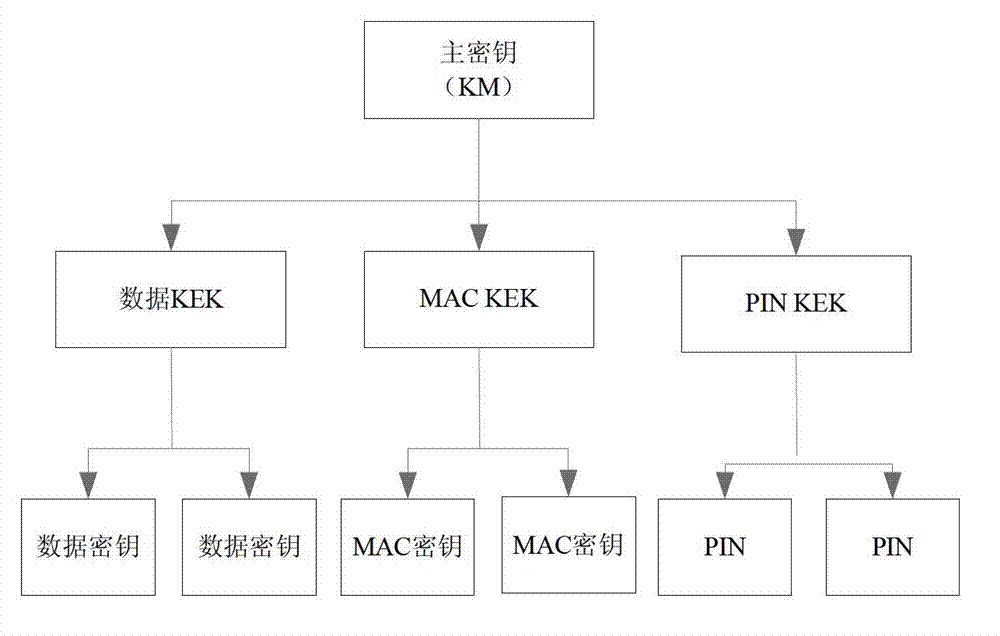
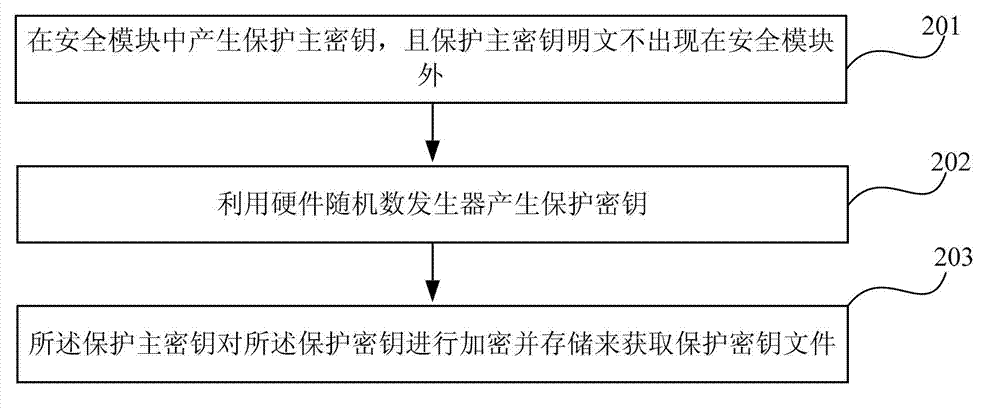
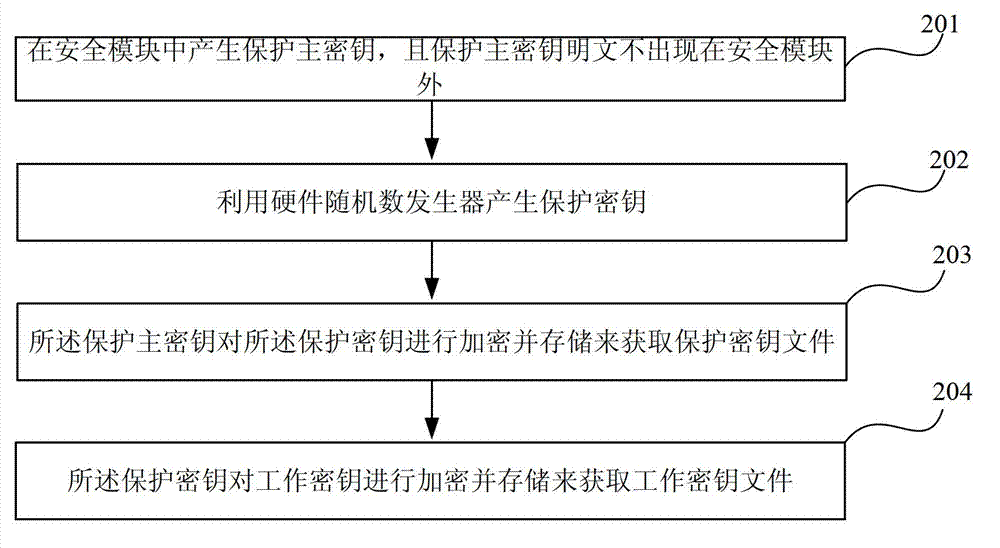
[0059] Such as Figure 4 Shown is a key hierarchical structure diagram in the key encryption storage method proposed by the present invention. Depend on Figure 4 It can be seen that the protection master key is generated inside the security module, and its plain text does not appear outside the security module; the hardware random number generator is used to generate a protection key group, which contains multiple protection keys, and is controlled by the protection master The key is encrypted and stored. Protection Master Key The protection key is encrypted with CTR (Counter) mode. A protection key group encrypts multiple working keys in CTR mode. The working key can be generated by random numbers or according to certain operation rules. The working key includes encryption key, MAC key, asymmetric key, etc.
[0060] The block encryption in the CTR mode and the flow of encrypting the protection key and the working key in the present invention will be introduced below.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com