Method of security service processing and security platform and security gateway
A security gateway, security technology, applied in the direction of network connection, data exchange network, instruments, etc., can solve the problems of poor user-friendliness, high technical threshold, difficult to operate, etc., to reduce criminal cases and various disasters, reduce the use of Cost and loss reduction effect
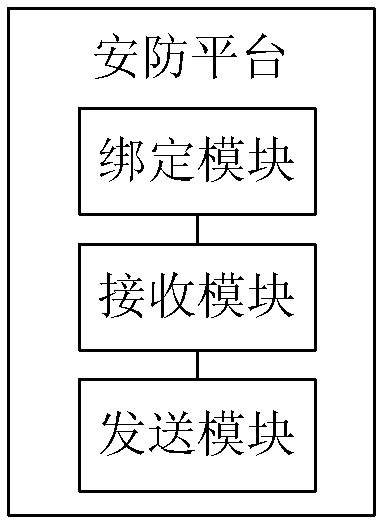
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
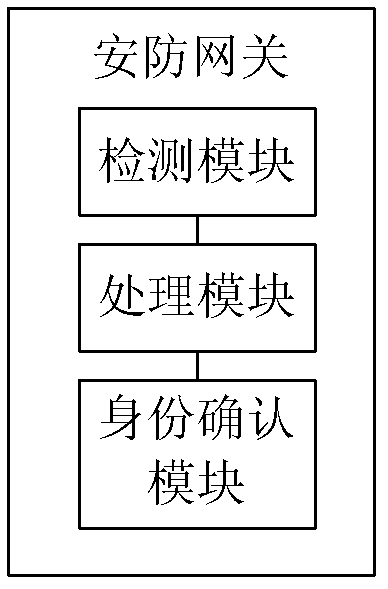
[0059] There are arm and disarm buttons on the hardware of the security gateway. When the user needs to start the security, press the arm button on the security gateway. The specific steps are as follows:
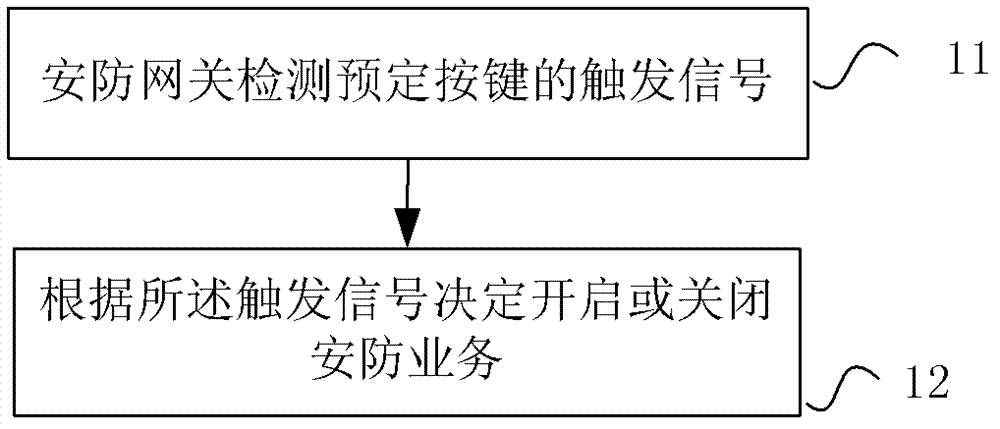
[0060] Step 101, the user presses the arm button on the security gateway;
[0061] Step 102, the security gateway detects the trigger signal of the arm button;
[0062] Step 103, the security gateway reports the arming signal to the security platform;
[0063] Step 104: After receiving the confirmation signal returned by the security platform, the security gateway starts arming, that is, starts the security service.
[0064] When the user wants to cancel the security, press the disarm button on the security gateway, including the following steps:
[0065] Step 111, the user presses the disarm button on the security gateway;
[0066] Step 112, the security gateway detects the trigger signal of the disarm button;
[0067] Step 113, the security gateway reports the disarmi...
Embodiment 2
[0070] The security gateway has a matching remote control on the hardware, and the security function can be turned on and off through the remote control, including the following steps:
[0071] Step 201, the user presses the arm button on the remote controller;
[0072] Step 202, the security gateway detects the trigger signal of the arm button;
[0073] Step 203, the security gateway reports the arming signal to the security platform;
[0074] In step 204, the security gateway starts arming after receiving the confirmation signal from the security platform.
[0075] The disarming process is similar, as follows:
[0076] Step 211, the user presses the disarm button on the remote controller;
[0077] Step 212, the security gateway detects the trigger signal of the disarm button;
[0078] Step 213, the security gateway reports the disarming signal to the security platform;
[0079] Step 214: After receiving the confirmation signal from the security platform, the security gate...
Embodiment 3
[0081] The security gateway is connected to an identification system such as fingerprint recognition or voice recognition. When the user needs to start the security, he must first authenticate his identity through the identification system, and then start the security on the identification system; when disarming, he also needs to perform identity authentication before disarming; including The following steps:
[0082] Step 301, the identity recognition system performs identity authentication, and sends the identity authentication information to the security gateway;
[0083] Step 302, the security gateway confirms that the identity authentication is passed;
[0084] Step 303, the user presses the arm button on the identification system;
[0085] Step 304: After detecting the arming button signal, the security gateway reports the arming signal to the security platform;
[0086] In step 305, the security gateway starts arming after receiving the confirmation signal from the se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com