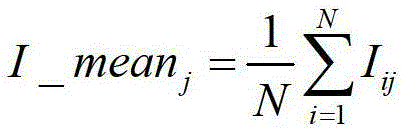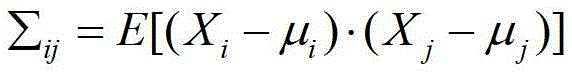Hardware trojan identification method based on single classification supporting vector machine
A technology of support vector machine and hardware Trojan, which is applied in the field of detection and recognition of hardware Trojan chips, can solve the problems of large errors and low efficiency, and achieve the effect of improving recognition efficiency and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
[0016] Specific implementation mode one: the following combination figure 1 Describe this embodiment, the hardware Trojan horse recognition method based on single classification support vector machine described in this embodiment, this method comprises the following steps:
[0017] Step 1. For all the chips to be tested, perform data preprocessing on the side channel information to obtain the preprocessed side channel information matrix of all the chips to be tested;
[0018] Step 2, select a part of the chip to be detected as the anti-section chip, and other remaining chips to be tested are called test chips, and the anti-section chip is reversely analyzed to determine whether each anti-section chip contains a hardware Trojan horse;
[0019] Step 3. For the anti-dissection chip that does not contain a hardware Trojan horse, divide it into two parts, one of which is used as a training sample chip, and the other part is used as a training optimization sample chip;
[0020] Ste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com