Character terminal feature data extraction method based on behavioral analysis
A technology of characteristic data and behavior analysis, applied in the field of information security, can solve the problems of reducing accuracy and applicability, achieving the effect of broad application space and reducing redundant workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
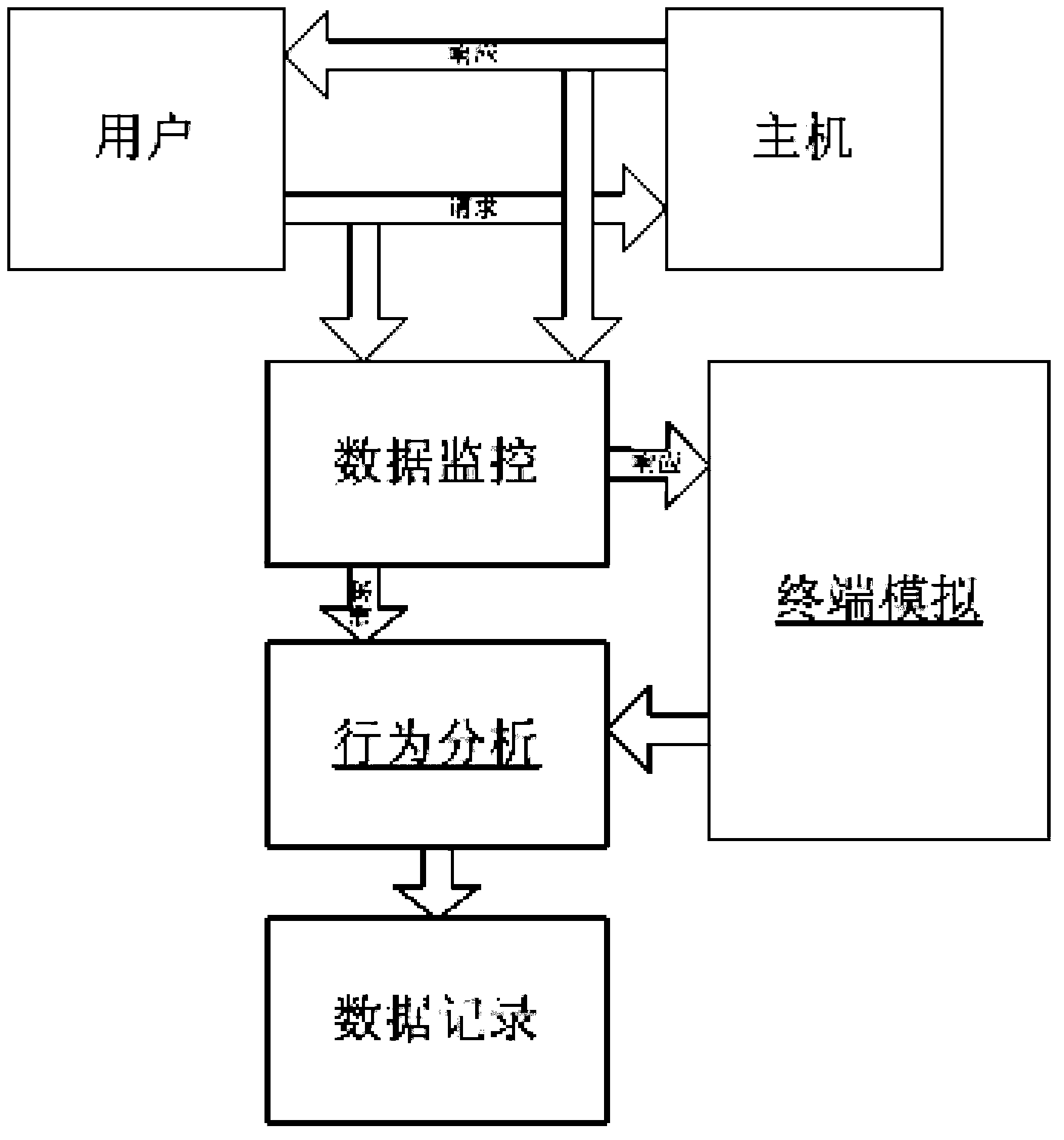
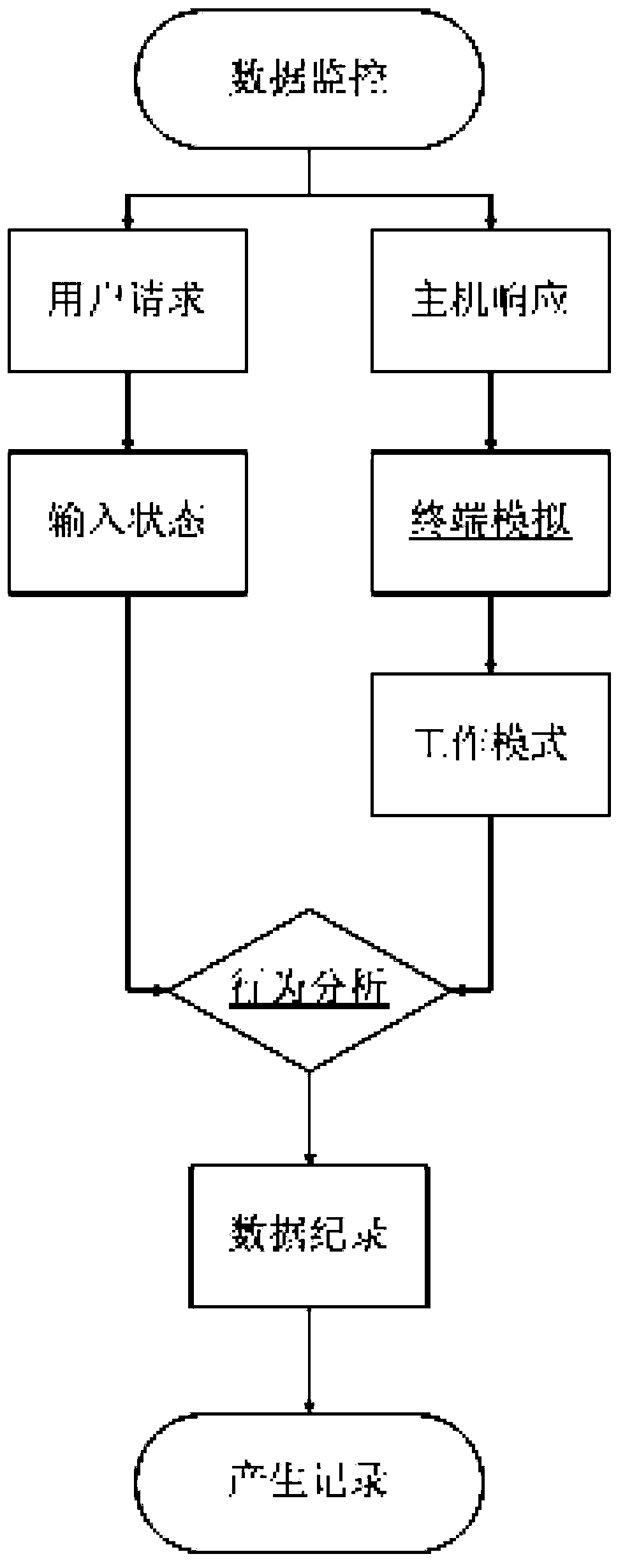
Image
Examples
Embodiment example
[0067] Suppose a user logs in to a typical Linux system through a network character terminal.
[0068] Assume that the user performs several operations on the terminal.
[0069] Suppose we need to extract which commands the user typed.
[0070] Specific steps:
[0071] (1) When the user logs in to the host system, the host will reply to the user with a large amount of information, such as the system logo, current time, basic user information, etc., as shown in the following characters:
[0072] Last login: Sat Mar 16 12:05:02 2013 from 192.168.50.139
[0073] [usercentos139~]$
[0074] (2) After behavior analysis, it is found that the command line prompt string of interest is located in the last line, so the content before the last will be ignored, and then the string is finally obtained through terminal simulation:
[0075] [usercentos139~]$
[0076] (3) The user starts to type in a command, for example, the user types in the command "ls", that is, two characters "l"...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com